Expanding visibility for the rise of AI agents
Imagine a world where your most tedious tasks are no longer “your” tasks. They vanish from your day-to-day life. No more manually copying data from a spreadsheet, pasting it into your CRM, and then toggling to another app to create a support ticket.
This is the promise of AI agents: a seamless, intelligent workforce that handles tedious tasks automatically, freeing up your team for more meaningful work. This future is arriving faster than we think, powered by technologies like Model Context Protocol (MCP) servers that act as bridges, allowing AI to securely interact with your company’s applications and data. The potential is immense.
The excitement around AI agents can obscure a simple truth. While we dream of revolutionary gains, the most immediate risks aren’t a rogue Skynet, but something far more mundane: lack of visibility and unmanaged permissions. This is where, as your friendly security advisor, I’d suggest we pause and take our vitamins. The agentic future will be incredible, but only if we build it on a foundation of trust and visibility.
Meet your new workforce
While your security team diligently manages human identities, a new workforce is quietly materializing in the shadows. A marketer streamlining a campaign or a developer experimenting with a new tool can now spin up a powerful AI agent in minutes.
The problem? These agents are often built for speed, not security, creating a chaotic and unsupervised digital workforce. At Cisco Security, we’re seeing a pattern of significant risks emerge:
A New Identity Blind Spot: Every one of these agents is a Non-Human Identity (NHI) that needs a “registered home.” It’s impossible to protect or secure what you can’t see, which is why without a proper inventory of agents – security teams are left in the dark.
Too Many Permissions: In the rush to innovate, many agents are built with hard-coded admin credentials, giving them—and by extension, their users—far more access than they need. It's the digital equivalent of giving a new intern a master key to every room in the building.
Uncontrolled Activity: An AI agent has no hesitation. It will execute its programming at a machine-driven pace, potentially racking up enormous API costs from services like Salesforce or Snowflake before anyone even notices.
From inventory to governance with Cisco Identity Intelligence
We wouldn't hire a human employee without an identity, a defined role, and clear access rules. The principles that govern human identity and access management (IAM) must be adapted for this new, non-human workforce. The first and most critical step is visibility.
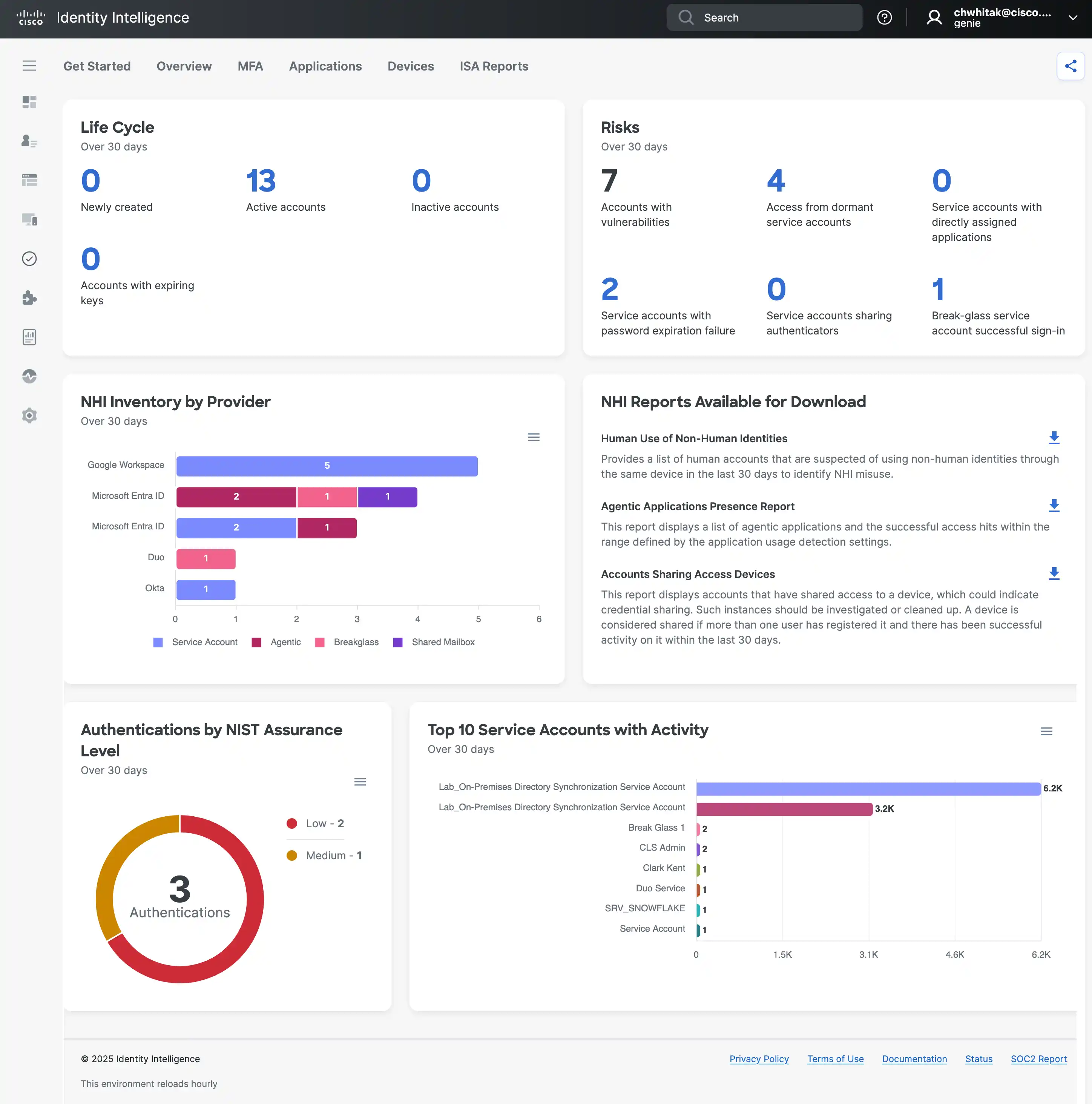
This is why we’re enhancing Cisco Identity Intelligence to shine a light on this new shadow workforce. Our goal is to provide the foundational visibility needed to securely enable AI innovation. We help you:
Discover Agents: We actively identify AI agents and MCP servers across your environment, turning unknown entities into a known inventory.
Map Their Activities: We connect the dots between agents, the credentials they use, and the applications they access, creating a clear picture of your NHI landscape.
Bridge the Gap to Governance: Once discovered, these NHIs can be brought into your identity governance and administration (IGA) program. This allows you to treat an agent like any other privileged identity—subject to access reviews and fine-grained controls.
The age of AI agents is here, and it will transform your business for the better. By prioritizing visibility, you can ensure this transformation is not only powerful but also secure. To learn more about our approach to agent visibility, check out Cisco Identity Intelligence or reach out to an identity expert.

