How much does multi-factor authentication cost? A breakdown of true costs
Not all multi-factor authentication (MFA) solutions are created equal. There are some extra features on some and hidden costs in others. The real cost of multi-factor authentication includes all direct and indirect costs of owning a product. For a two-factor authentication (2FA) solution, that may include hidden costs, like upfront, capital, licensing, support, maintenance, and operating costs. There are also unforeseen expenses like professional services, ongoing operation, and administration costs that accumulate over time. Before you know it, the cost of multi-factor authentication can rack up.
How can you be sure you’re getting the best security return on your investment?
What are the main costs of multi-factor authentication?
Upfront costs
Do you pay per device, user, or integration? If your company plans to scale and add new applications or services in the future, you'll need to consider these upfront costs. Many hosted services provide a per-user license model, with a flat monthly or annual cost for each enrolled user.
When investigating licensing costs, make sure to confirm whether licenses are named (locked to a single user ID) or transferable, whether there are add-on charges for additional devices or integrations configured, or delivery charges for different factor methods. Estimate and plan for how much it will cost to deploy multi-factor authentication to all of your apps and users.
Administrative software requirements
Are these included in the software license? Additional management software is often required for some companies—without this, customers can’t deploy MFA. Does the service require the purchase and configuration of hardware within your environment?
Check the equipment costs, setup needs, and essential features for administrative access, including tired permissions based on license version while noting any additional charges.
Authenticators
Physical tokens add inventory, management, and shipping costs to consider. For mobile authenticators, confirm if there is any per-device cost for soft tokens, or if an unlimited number of enrolled devices is permitted for each user license to avoid surprises.
Additional costs of implementing multi-factor authentication
Deployment & configuration
Find out if you can deploy the solution using your in-house resources or if it will require professional services support and time to install, test and troubleshoot all necessary integrations.
End-user enrollment
Estimate user enrollment time and administrative training needs. Discuss deployment timelines with your vendor and seek peer feedback. Prioritize intuitive end-user experiences with simple enrollment to minimize training requirements. Keep in mind: token-based solutions are often more expensive to distribute and manage than they are to buy.
Administrator support
To make it easy on your administrators, look for seamless integrations for major apps, reducing implementation time. Confirm the availability of general-purpose integrations for common authentication protocols and APIs for web applications. Consider a pilot program for testing and feedback—simple integrations should take no longer than 15 minutes.
Patches, maintenance & upgrades
Look for a vendor that automatically installs software and updates the software for security and other critical updates, saving the cost of hiring a team. One of the perpetual benefits of SaaS and cloud-hosted services is that servers, maintenance, and monitoring are covered by the provider’s network and security engineers, lightening the load for your team. Depending on your solution, you may have to manually upgrade to the latest version.
Also consider the frequency of updates, since some vendors may only update a few times a year, which can leave you susceptible to new vulnerabilities and exploits. Choose a vendor that updates often and automatically, without any assistance from your team.
Administrative maintenance
Does your provider maintain the solution in-house, or is it up to you to hire experts to manage it? Employing full-time personnel can get expensive. Is it easy to add new users, revoke credentials or replace tokens? Routine tasks, like managing users, should be simple. Be sure to sign up for a trial and do a test run before deploying it to all of your users.
Support & helpdesk
Live support via email, chat and/or phone should also be included in your vendor’s service – but sometimes support costs extra.
Gartner estimates that password reset inquiries comprise anywhere between 30% to 50% of all helpdesk calls. And according to Forrester, 25% to 40% of all helpdesk calls are due to password problems or resets. Forrester Research determined that large organizations spend up to $1 million per year on staffing and infrastructure to handle password resets alone, with labor cost for a single password reset averaging $70.
If a solution requires extensive support from your teams, estimate the cost of any time spent on support and factor it into your budget.
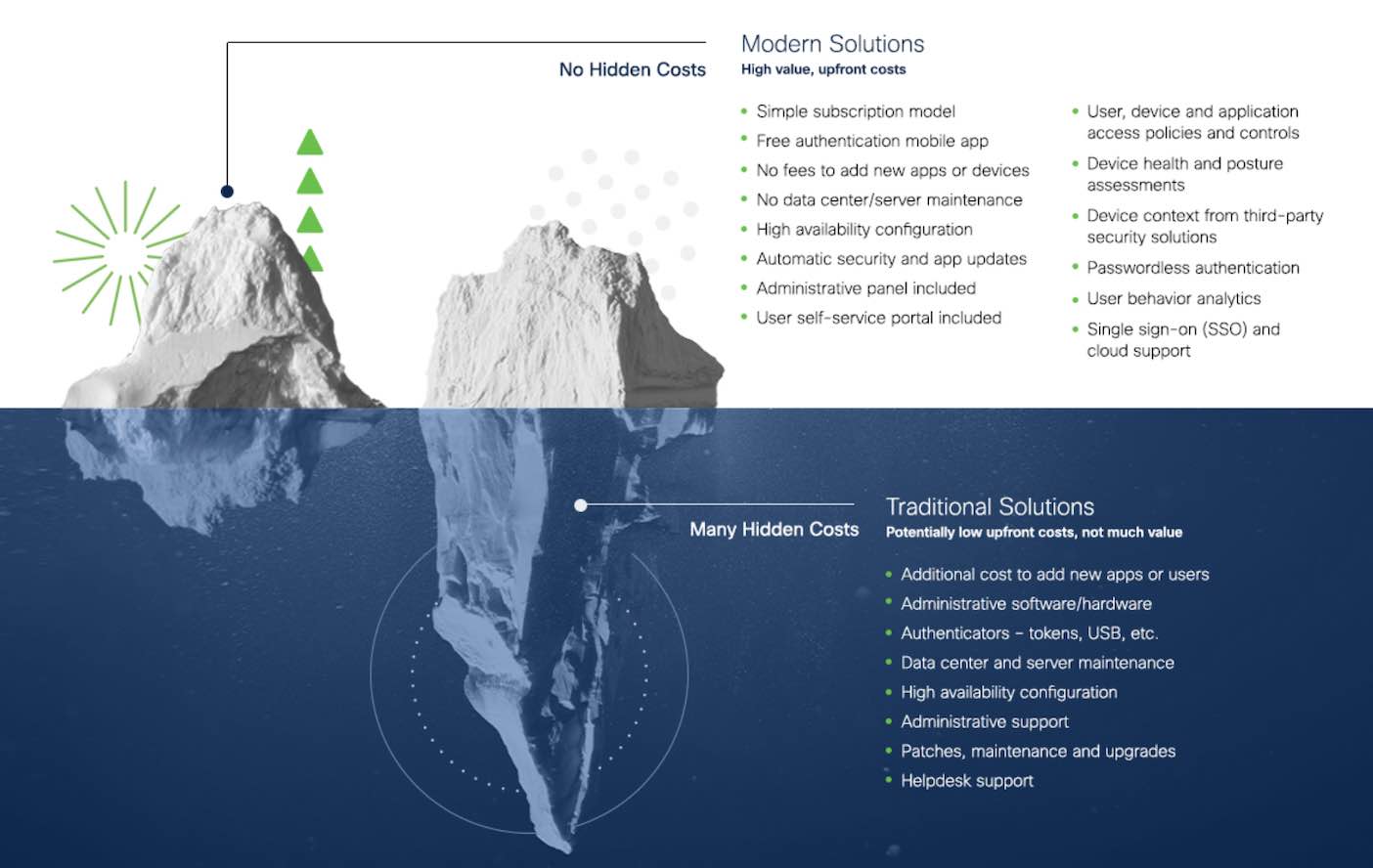
How to reduce costs of multi-factor authentication
Traditional solutions potentially have low upfront costs, but not much value. For instance, they may lack seamless integration with your existing environment without an upgrade. There are a lot of hidden costs that can add up to one costly MFA solution. Here are some tips to minimize your total cost of MFA:
1. Consolidate tools and services
Traditional perimeter defenses focus on a few key services to maintain visibility and enforce security standards, but the growth of SaaS adoption has led to patchwork solutions for securing cloud-based data. Be mindful of the hidden costs of complex integrations and consider using a comprehensive platform like Duo Security by Cisco to avoid these costs.
Secure access includes strong authentication through MFA to validate users, and may also include:
Endpoint management or mobile device management tools for defending against threats
Single sign-on (SSO) portals to simplify login workflows for users
Log analysis tools to identify and escalate potential security threats
Multiple dashboards to manage disparate services and unsupported applications
Consolidating tools for secure access not only minimizes redundant costs, but also can lower initial and ongoing management labor expenses.
2. Get on the cloud
Server hosting costs can add up: power, HVAC (heating, cooling, and air conditioning), physical security, and personnel, but a cloud-based solution will typically build these costs in.
3. Look for simple subscription models
When it comes to High Availability Configuration, duplicating your software and linking them with a load balancer can triple the cost of MFA. Some vendors may even charge added licensing fees for business continuity. Look for vendors with simple subscription models, priced per user, with flexible contract times.
How to choose the best MFA solution for your business
Time to value
Time to value, or speed to security, refers to the time spent implementing, deploying, and adapting to the solution. You'll want to get an idea of how long it may take for your company to benefit from MFA to get the best value out of your time, especially if you've experienced a breach or security incident recently.
Proof of concept
Setting up a two-factor authentication pilot program lets you test your solution across a small group of users, giving you the ability to gather valuable feedback on what works and what doesn’t before deploying it to your entire organization.
Deployment
Implementation Scenarios: Walk through likely deployment scenarios so you can estimate the time and costs. Cloud-based services provide the fastest deployment times since they don’t require hardware or software installation, while on-premises solutions tend to take more time and resources to get up and running.
Drop-in Integration: Most security professionals don’t have time to write their own integration code. Choose a vendor that supplies drop-in integrations for all major cloud apps, VPNs, Unix, and MS remote access points. You’ll also want a vendor that enables you to automate functionality and export logs in real time. To save on SSO integration time, check that your multi-factor solution supports the Security Assertion Markup Language (SAML) authentication standard that delegates authentication from a service provider or application to an identity provider.
Onboarding & training users
Optimize Efficiencies: Walk through the enrollment process to identify any issues that may cause a major time sink for IT administrators. For enterprises, bulk enrollment may be a more time-efficient way to sign up a large number of users. To support your cloud apps, ensuring your two-factor solution lets you quickly provision new users for cloud apps by using existing on-premises credentials.
Empower Users: See if the solution requires hardware or software for each user, or time-consuming user training. Token deployment can require a dedicated resource, but easy self-enrollment eliminates the need to manually provision tokens. A cloud-based solution that allows your users to download, enroll and manage their own authentication devices using only a web browser or mobile device can save your deployment team’s time.
Required Resources
Consider the time, personnel and other resources required to integrate your applications, manage users and devices, and maintain your solution. Ask your provider what they cover and where you need to fill in the gaps.
Application support
Some multi-factor authentication solutions require more time and personnel to integrate with your applications, whether on-premises or cloud-based. Check that they provide extensive documentation, as well as APIs and SDKs so you can easily implement the solution into every application that your organization relies on.
User & device management
Like any good security tool, your multi-factor authentication solution should give administrators the power they need to support users and devices with minimal hassle. Look for a solution with a centralized administrative dashboard for a consolidated view of your multi-factor deployments.
Your solution should also enable admins to:
Easily generate bypass codes for users that forget or lose their phones
Add and revoke credentials as needed, without the need of physical tokens
Ask your provider if they offer a self-service portal that allows users to manage their own accounts, add or delete devices, and perform other simple tasks.
Maintenance
Make sure that your solution requires minimal ongoing maintenance and management for lower operating costs. Cloud-hosted solutions are ideal since the vendor handles infrastructure, upgrades and maintenance. Ask your vendor if monitoring or logging is included in the solution. Otherwise, you'll need to factor in who on your team can do the job.
A solution that requires many additional resources to adapt may not be worth the cost and time. Your company will evolve, so your MFA solution should easily allow any changes needed without the need to hire more personnel.
What does the best MFA deal look like?
Token-related helpdesk tickets can account for 25% of the IT support workload. You should look for a provider that offers:
Modern solutions with high value, upfront costs
A simple subscription model
A free authentication mobile app
No fees to add new apps or devices
No data center/server maintenance
High availability configurations
Automatic security and app updates
Administrative panel included
User self-service portal included
User, device and application access policies and controls
Device health and posture assessments
Device context from third-party security solutions
Passwordless authentication
User behavior analytics
Single sign-on and cloud support
What is multi-factor authentication like with Duo?
Duo's high availability architecture has maintained an uptime of greater than 99.99%, with a hard service level guarantee backed by SLA. Duo’s servers are hosted across independent PCI DSS, ISO 27001-certified, and SSAE 16-audited service providers with strong physical security. We provide a high-availability service split across multiple geographic regions, providers and power grids for seamless failover, and our multiple offsite backups of customer data are encrypted.
If an outage occurs on the vendor side, there are business costs assumed with that, such as employees unable to access critical work resources.
For administrators
Deployment costs
Duo is cloud-based and comes with hundreds of out-of-the-box integrations, making deployment quick and easy. Duo supports VPNs, RDP, Microsoft OWA and cloud apps such as Salesforce, Box and Office 365.
Ongoing costs
To keep your security solution free of vulnerabilities, MFA patches need to be installed on a timely basis. Duo doesn’t require any IT support—new updates are pushed every two weeks to ensure your MFA is updated to protect against new threats. Duo also allows your users to self-enroll and manage their own devices, effectively reducing IT helpdesk requests.
For end users
Deployment costs
With Duo, users enroll themselves when they sign into applications. Users can use their smartphone for authentication. IT needs fewer resources to deploy MFA solutions to users.
Ongoing costs
Duo’s mobile app sends push notifications to users’ phones, allowing them to log in quickly by tapping an Approve button—increasing productivity and security
Duo has an upfront value without hidden fees in the future. Duo MFA, Duo Device Trust, Duo Network Gateway (DNG) and Duo Trust Monitor combine into one trusted access solution and can secure remote access to on-premises infrastructure and prevent breaches from getting access in the first place.
Device Trust checks the health of a device, managed or unmanaged, before granting access to the network and can block untrustworthy devices.
The Duo Network Gateway allows your users to access your on-premises websites, web applications, and SSH servers without having to worry about managing VPN credentials, while adding login security with the Duo Prompt and Duo SSO.
Trust Monitor is machine learning software that continuously monitors your authentications looking for anomalies to flag and alert you to.
"Duo provides fast deployment without complicated applications to roll-out or educate end users to use." — Sean McElroy, Chief Technology Officer Alkami Technology, Inc.
Is multi-factor authentication worth it?
Choosing vendors is always a bit of a challenge. But knowing upfront what you're buying can make it easier. Investing in MFA can save your business from unauthorized access, data breaches, and financial loss.
While MFA may seem complex, Duo provides robust security solutions that are easy to use and quick to implement. We understand the value of time and will not make you sacrifice security. Our strong MFA solution comes with added security features that protect and adapt with your business. At Duo, we grow with you.
Get started today with our Access Management Buyer's Guide and find out how to choose the best access management solution for your business.
*Duo Trust Monitor is unavailable to new Duo Advantage and Premier subscriptions and trials as of September 29, 2025. Cisco Identity Intelligence is now the sole option for user threat detection capabilities offered to new customers after this date.
Trust Monitor remains available to Duo customers created before September 29, 2025. Trust Monitor functionality will be removed from the Duo Admin Panel on July 27, 2026, and the Trust Monitor API endpoint will reach end-of-support status on January 31, 2027.
Cisco Identity Intelligence, which is included in Duo Advantage and Premier plans, offers broader protection and more robust capabilities than Trust Monitor, extending beyond Duo and providing a more comprehensive security solution.

