Introducing User Trust Levels: Calculating identity risk to improve security outcomes
Users are weird. That’s not a value judgement—it's just true that end users in an organization do all sorts of things. The job of IT and Security professionals is often to label this weirdness with value. Are these actions “good weird” (ex: taking a trip to a new location to close business)? Are they “bad weird” (ex: a user’s account has been dormant but now tries to sign in without MFA)?
The faster teams can make these judgements the better. Duo’s Identity Intelligence feature offers a powerful tool in this domain: the User Trust Level. This innovative approach helps organizations manage user-related risks more efficiently by assigning trust levels based on a comprehensive evaluation of user behavior and context.
What is a User Trust Level?
The User Trust Level is a dynamic assessment of risk associated with each user in your organization. Cisco Identity Intelligence calculates this level by analyzing various factors such as user behavior, context, and historical data from multiple identity sources.
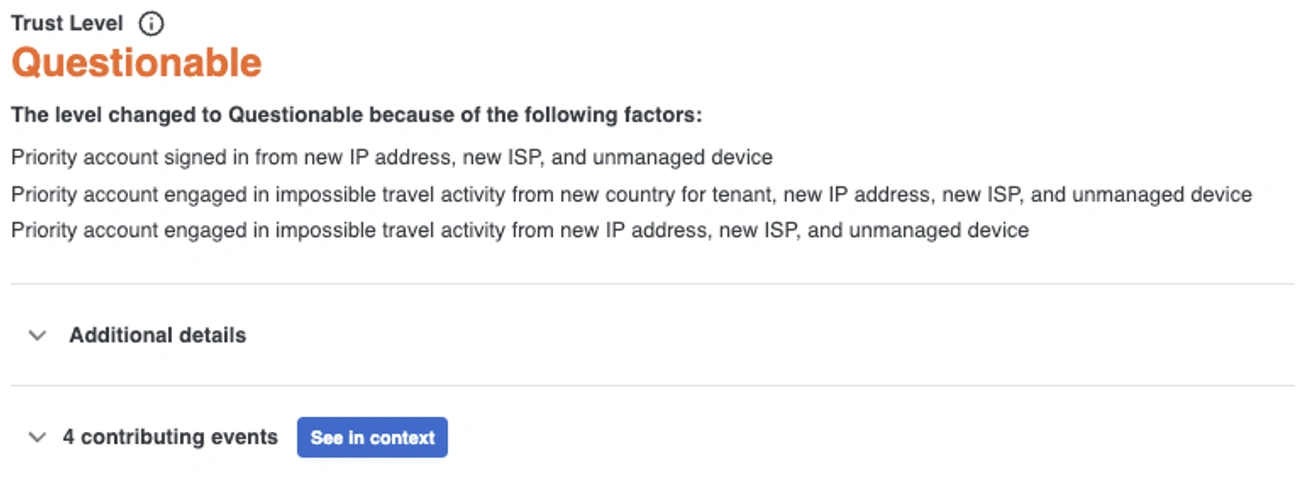
The algorithm first sets out a framework of risk types. For example, there is “inherent risk” or the elevated risk of a powerful user like an administrator or executive. There is also “posture risk” or the risk of account takeover given the current security controls assigned to and used by the user. The algorithm maps risk to each of the various components using the data available (the more data available, the better) and then distills those components into an overarching User Trust Level. User Trust Levels range from "Trusted" to "Untrusted" and serve as indicators of how safe or risky a user is at any given time.
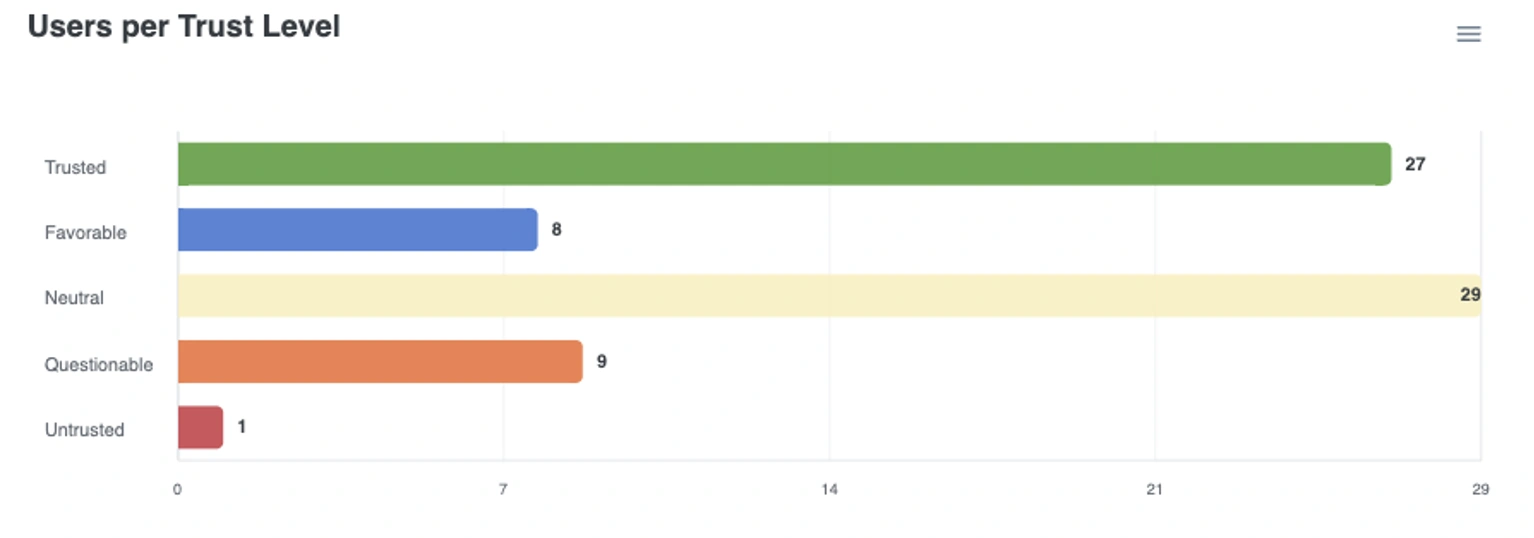
The value of User Trust Levels
In an ideal scenario, User Trust Levels would be shared in real-time across all systems, seamlessly enhancing security workflows and policy decisions. Imagine a world where the slightest change in user risk is effectively accounted for and shared instantly with relevant access points like Secure Service Edge (SSE) or Firewall tools. These tools could always make the most informed decision possible about access. And, to be clear, Cisco is building this vision by integrating the User Trust Level into its broader portfolio. The philosophy of this effort is critical – because sharing enriched user context across the broader networking and security ecosystem is fundamental to an “identity-first” approach to Zero Trust.
How to leverage User Trust Levels in your organization today
While the theoretical benefits of User Trust Levels are significant, practical implementation requires some consideration. One key aspect to understand is that today’s User Trust Levels, though informed by a multitude of data points, should often incorporated into decisions as a directional variable, but not the only variable. They provide a holistic view of a user's risk profile over time and therefore should be used like IP reputation to inform actions and decisions.
User Trust Levels are best utilized in workflows where they can be assessed as part of a broader context. For example, in threat detection and response workflows, the trust level can help prioritize which users require immediate attention and remediation. An "Untrusted" user signals high priority and should prompt further investigation, especially when correlated with alerts from other security tools.
Another practical use case involves access policy decisions. As a concrete example, Cisco Secure Access can ingest the User Trust Level—and in the future, will be able to designate which resources a user can access or authentication requirements for users with a specific trust level. However, while it seems fine to use User Trust Levels for dynamic access control, the implications of doing so are important to consider.
“What happens when a user is blocked?” is a key question to answer. If access is denied based on a low trust level, there must be a clear process for users to regain access, preventing unnecessary disruptions. There are other ways to approach the problem as well. Perhaps risky users are not blocked outright—but they must perform a form of phishing-resistant MFA to gain access after being labeled “untrusted.”
On the flip side, when trust levels are "Trusted," there must also be stop gaps in case that User Trust Level calculation was missing a critical piece of information. Therefore, policy should never be so lenient such that the User Trust Level assessment is the only thing standing between an attacker and a valuable resource.
However, all this being said, User Trust Levels are still a great way to enrich all of these workflows and decisions! A User Trust Level is not a silver bullet, but it is a fantastic way to improve defenses.
Taking concrete steps towards an ideal future
The User Trust Level is a transformative tool in the realm of identity security, offering a nuanced approach to managing user risk. By understanding its theoretical value and practical implications, organizations can better integrate it into their security strategies, leveraging it to enhance detection, response, and access decisions. As Cisco continues to innovate in identity intelligence, User Trust Levels will undoubtedly play a pivotal role in shaping the future of cybersecurity.
To understand more about how to use User Trust Levels to secure your organization—contact a Duo expert.

