OAuth 2.0's next chapter: Enabling the AI security revolution
It seems like on a near monthly basis, a protocol is “dead” or “dying.” Some have been close to true, but when we dig into the likes of OAuth, the reality couldn’t be further from the truth: OAuth continues to expand its role. With OAuth 2.1 approaching ratification and enterprises exploring agent-driven frameworks like the Model Context Protocol (MCP), OAuth is moving from a behind-the-scenes standard to a frontline security guardrail.
It’s not flashy, but without OAuth, interoperability quickly turns into uncontrolled risk. A risk that Duo’s here to help you solve!

The framework enterprises rely on
At its core, OAuth is a delegation protocol. It was designed to let applications grant access without sharing usernames and passwords, relying instead on scoped tokens. That simple idea has become the connective tissue of enterprise IT. It allows SaaS platforms to integrate cleanly, internal APIs to share data securely, and, increasingly, AI agents to take on tasks with just the right level of permission.
The principle is always the same: Access should be temporary, identity-bound, and accountable. OAuth enforces that principle at scale.
Why AI agents raise the stakes
The emergence of MCP highlights why OAuth still matters. MCP promises a world where apps and AI agents can coordinate across organizational boundaries. But that flexibility also increases the number of access decisions enterprises must manage.
OAuth provides the discipline MCP requires. Tokens limit what agents can do and how long they can do it. Permissions are no longer vague, permanent grants but scoped, time-limited credentials. Every interaction is governed by least-privilege. In short, OAuth makes MCP practical for enterprises that can’t afford to trade innovation for uncontrolled risk.
OAuth 2.1 sharpens the tools enterprises already depend on. By removing insecure pieces such as the implicit flow, it closes off a common path to token leakage. By requiring PKCE in every application—even server-side ones—it reduces the risk of code interception. And by consolidating best practices into a single recommended baseline, it simplifies life for developers who no longer need to guess which flow to use.
The result isn’t a reinvention, but a protocol that is easier to implement securely and better suited for distributed, agent-rich ecosystems.
How Duo extends OAuth
Most identity providers manage OAuth through a single authorization server per tenant. Duo takes a different approach: Each OAuth or OIDC integration is its own server, creating explicitly secure segmentation, seamlessly tying into our security-first IAM strategy. By doing this, we ensure that a potential compromise in one integration cannot cascade laterally across the tenant.
When more flexibility is required, Duo also offers Global Token Introspection, an optional capability that centralizes token validation across selected integrations. Instead of managing multiple introspection endpoints, organizations can route validation through a single global service. That improves consistency, reduces administrative overhead, and makes interoperability between applications and agents more straightforward—all without sacrificing the control to isolate integrations when necessary.
Layered security with Duo stack
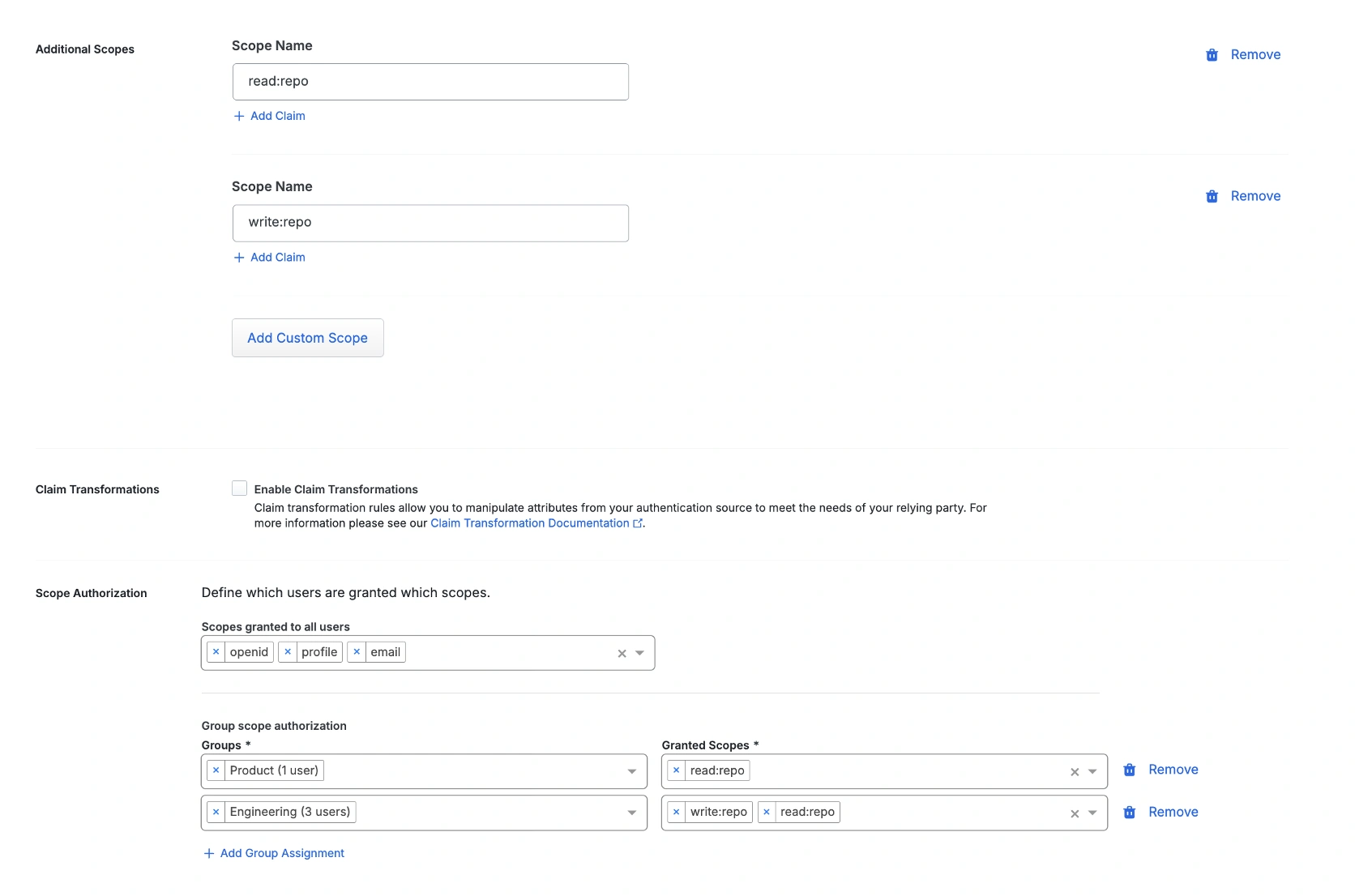
OAuth is only one layer. Duo enriches it with contextual policies that consider device health, location, and risk. Groups can be mapped to scopes through only after meeting the policy criteria that customers can define, ensuring access decisions align tightly to identity. And all of it feeds into a unified visibility layer, giving administrators a single place to monitor logins, API calls, and soon, agent activity.
This layered approach expands OAuth from a protocol that connects apps to and IdP into an access management framework. One that aligns with how enterprises actually manage workforce access today!
What's next
We just launched a beta for a new OIDC/OAuth 2.1 integration. This release combines grant types from OAuth 2.0 and 2.1, enables group-to-scope mapping, and extends Duo’s policy framework directly into authorization decisions. Very shortly, we’ll be further enhancing this integration by adding Dynamic Client Registration (RFC 7591) and Resource Indicators (RFC 8707) for even deeper support, so stay tuned! It’s OAuth built for the agent era - secure, interoperable, and ready for enterprise adoption.
AI agents are already becoming part of daily work. OAuth ensures they operate within safe boundaries. Duo makes that governance secure, scalable, and simple enough for enterprises to adopt with confidence.
Ready to see it in action? We sure are and we want to hear from YOU!

