Thwarting adversary-in-the-middle attacks with Proximity Verification
Approximately 4 years ago we introduced Verified Duo Push—an evolution of Duo Push. Verified Duo Push improves security by requiring users to input a numeric code displayed in the Duo Prompt when approving the Duo Push request.
Requiring a numeric code at authentication time prevents 2 types of push phishing:
Push Harassment — An attacker sending multiple successive push notifications to bother a user into approving a push for a fraudulent login attempt
Push Fatigue — Constant multi-factor authentication means users pay less attention to the details of each login, causing a user to mindlessly accept a push login
Verified Duo Push, while more secure than Duo Push alone, is still susceptible to certain attacks.
Let’s examine a real-world Verified Duo Push attack vector:
Case study: Verified Duo Push attack (email phishing + proxied phishing site)
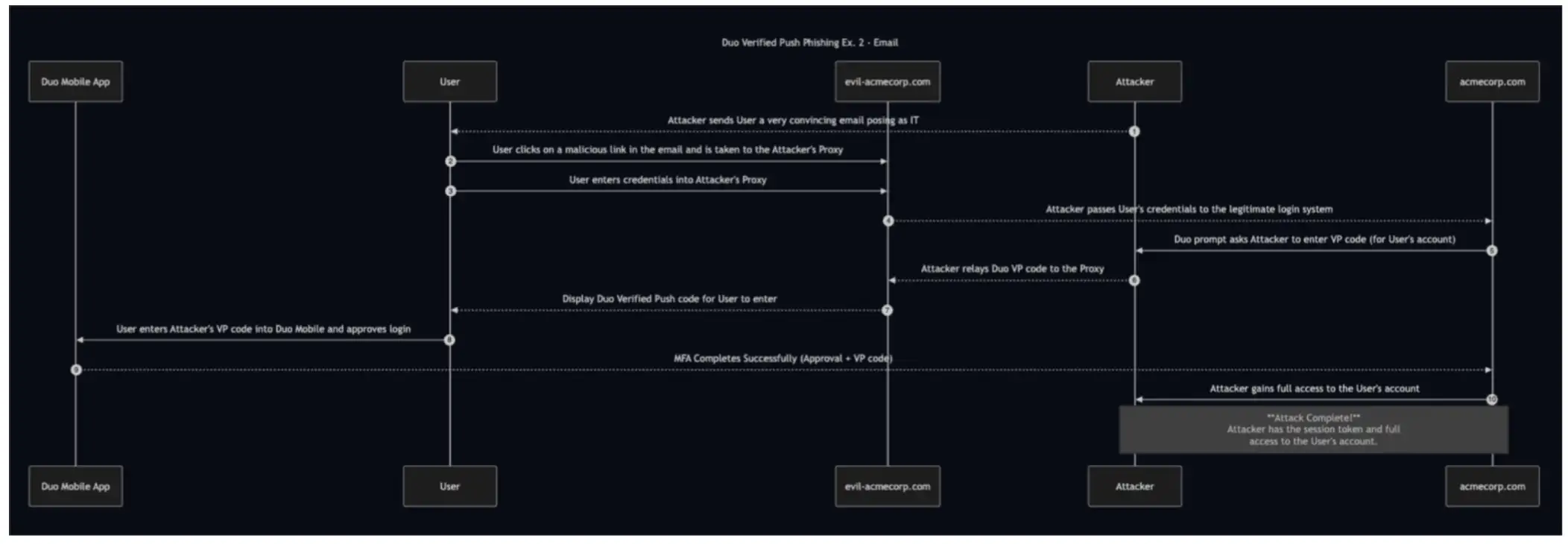
This Verifier Impersonation attack involves a convincing phishing email and a reverse-proxied phishing site:
The Attacker sends the User a phishing email posing as IT support. The User clicks a malicious link and is taken to a proxied login page. The user, thinking the malicious login prompt is the real login prompt, enters their primary credentials. The attacker, in turn, receives those credentials and enters them into the legitimate login page, which proceeds to send a Verified Duo Push to the user’s phone. When the Duo Prompt requests the Verified Push code be entered into Duo Mobile, the Attacker's proxy relays the code back from the real site to the fake site, tricking the User into entering it and granting full access.
Step-by-step breakdown of the attack
Attacker sends a phishing email posing as IT support
User clicks the malicious link and visits a proxied login page
User enters their first factor credentials into the proxy
Attacker forwards the credentials to the legitimate login page and begins authentication
Attacker (via their legitimate Duo Prompt) sends a push to the User's phone requesting VP code
Attacker's legitimate Duo Prompt displays VP code, which is forwarded to and displayed on the attacker's proxy site
User enters the Attacker's VP code into their Duo Mobile, granting the attacker full access to their account
At Duo, we constantly are innovating and adapting to the ever-changing threat landscape. Next let's take a look at the steps we've taken to make Push-based authentication even more secure.
Duo Proximity Verification
We recently released Duo Proximity Verification to Duo Essentials and above, at no additional cost! Proximity Verification helps prevent verifier impersonation attacks and active phishing campaigns.
This new authentication method requires Duo Mobile to perform a BLE communication handshake with the laptop or desktop that the end user is authenticating from in order to successfully approve the login request. The computer must be running a companion application, Duo Desktop, that communicates both with Duo Mobile and with the Duo Prompt.
Proximity Verification stops such attacks with a two-pronged approach:
Origin (Verifier Name) Binding — Duo Desktop must be able to verify that the request for authentication came from a legitimate instance of the Duo Prompt
BLE Proximity Verification — Duo Desktop (via Bluetooth Low Energy) must be able to verify that the Duo Mobile application associated with the user who initiated the authentication request is within physical proximity
These requirements stop verifier impersonation attacks and offer security comparable to FIDO2/WebAuthn without requiring expensive and difficult-to-provision hardware.
Let's take an in-depth look at how Duo Proximity Verification blocks the earlier attack.
Duo Proximity Verification thwarts verified push attack (email phishing + verified impersonation)
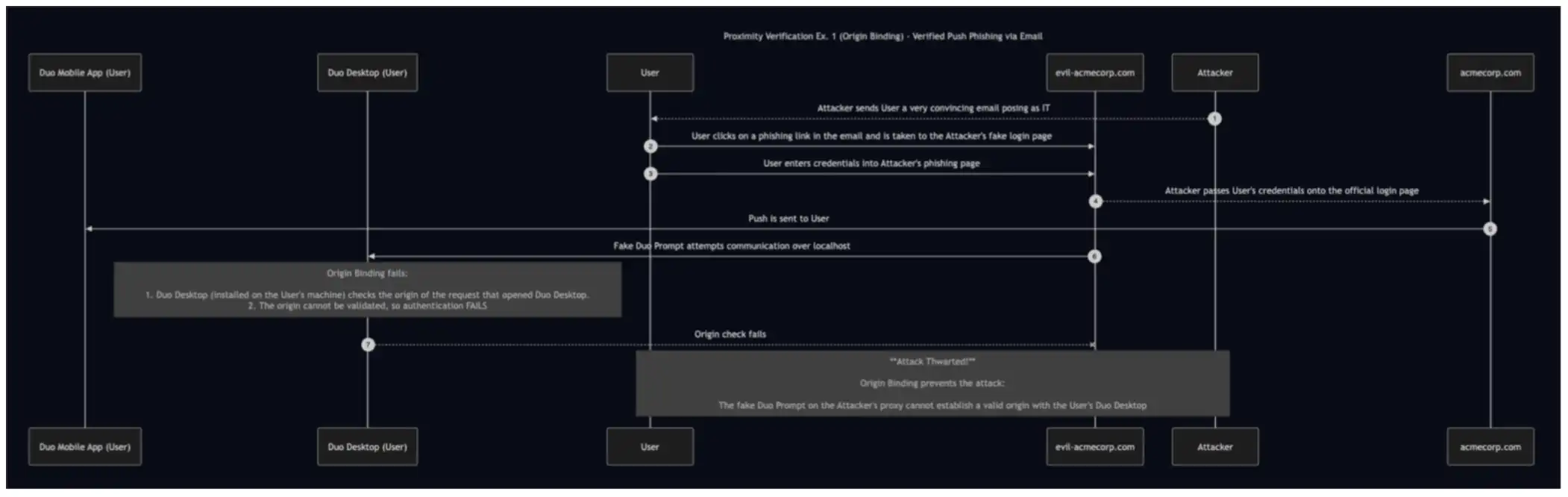
Let's first examine a common attack scenario where the Attacker attempts to leverage the user's Duo Desktop for proximity verification:
Since it’s the User’s Duo Desktop that needs to be within physical proximity of the User’s Duo Mobile, the Attacker allows their proxied site to communicate over localhost with the User’s Duo Desktop.
Step-by-step breakdown
Attacker sends a phishing email
User clicks the link and visits a proxied login page
User enters credentials
Attacker forwards the credentials to a legitimate login
Attacker sends a push to the end user
Fake Duo Prompt attempts to communicate with Duo Desktop over localhost
Origin check fails
Attack is thwarted
Here, Origin Binding is the mechanism that saves the day. Even with the Attacker’s approach of communicating with Duo Desktop (located on the User’s machine), the origin validation request will always fail, as the request originated from evil-acmecorp.com.
Now, let's consider a more sophisticated attack where the attacker attempts to bypass the origin check by installing Duo Desktop on their own machine:
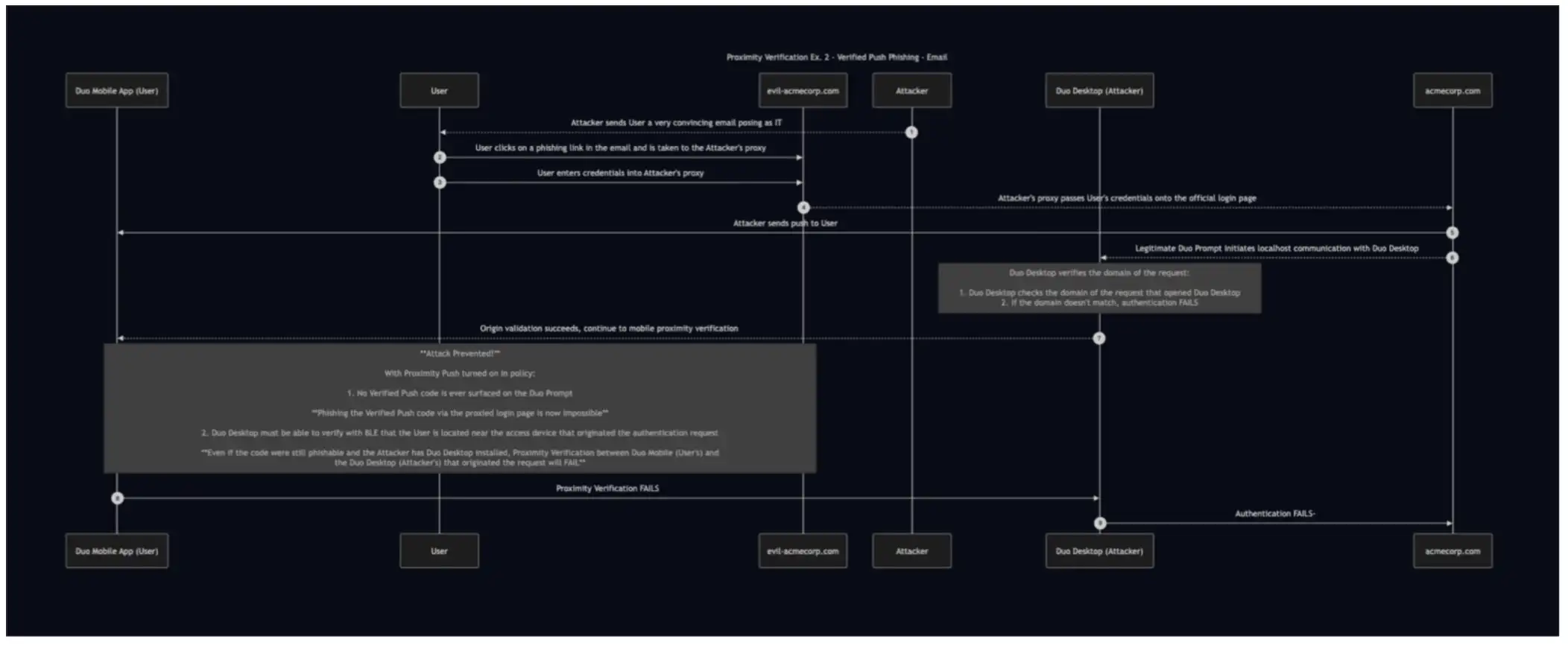
When Duo Proximity Verification is required
No Verified Push code is shown in the login flow. Instead, an encrypted single-use payload not visible to the user is exchanged between Duo Mobile and Duo desktop using BLE.
Duo Desktop verifies the origin of the authentication request ensuring that it came from a legitimate Duo Prompt.
BLE communication is used to prove that the user approving the Duo Push request in Duo Mobile is in close proximity to the computer they are logging in from.
The attacker cannot satisfy these conditions, so the attack fails.
Step-by-step breakdown
Attacker sends a phishing email
User clicks the link and visits a proxied login page
User enters their credentials
Attacker forwards the credentials to a legitimate login
Attacker sends a push to the end user
Duo Prompt (on the Attacker's machine) pings Duo desktop (also on the Attacker's machine) over localhost to provide encrypted payload
Duo Prompt validates the origin of the request from Duo Prompt. All is well!
Duo Desktop attempts BLE communication with Duo Mobile, but since Duo Mobile isn't in proximity, this check fails
Attack is thwarted!
Duo’s Proximity Verification provides a new layer of security beyond what Verified Push offers, neutralizing sophisticated verifier impersonation attacks without requiring additional hardware.
Where to learn more about Proximity Verification
If you’d like to explore Proximity Verification in more detail, check out the documentation, a demonstration, or start testing in your environment today!
If you aren’t a Duo customer but are interested in trying out this feature, you can start a trial of Duo.

