Why IAM should put security first
Several vendors talk about “identity-first security,” which is another way of saying, “identity is the new perimeter,” or that zero trust security starts with confirming someone’s identity before giving them access to your company’s resources. Spot-on advice.
But making identity a priority for security is only half the story. To propel a business forward, companies also must make security a priority for identity and access management. IAM emerged to do just what the name says: manage users’ access and privileges to make their lives easier and more productive. With most solutions, strong security controls get added later with a hefty upcharge. Security is literally an “afterthought.”
Only 33% of IT and security leaders are confident in their identity provider’s ability to prevent identity-based attacks, and 94% believe complexity in identity infrastructure decreases overall security.
2025 State of Identity Security Report
Duo turns this equation inside-out by making built-in security foundational to IAM, or “security-first IAM”—all with unmatched ease-of-use, proven speed to security, and at no added cost to properly protect the identity perimeter. Let’s break down what this means.
What makes IAM "security-first"?
We’ve seen time and time again that, despite checking the box for “has MFA,” a majority of successful cyberattacks still involve valid credentials identities. Organizations and compliance firms alike play Wack-a-Mole, solving for unique use cases and crafty attack methods with an increasing list of disparate and expensive identity tools. On average, it takes IT teams five different tools to solve any given identity-related issues. A modern IAM solution is secure by default with top-notch security controls built into the architecture and base pricing.
An IAM solution should not only store identities, but it must also protect them. In addition to being a flexible user directory, the three foundational capabilities of security-first IAM are:
"MFA Everywhere" by default — World-class security starts with making sure you have MFA available and enabled everywhere, not just for some users or use cases but for every user and every use—cloud and SaaS services, legacy systems on-prem, remote or hybrid work, first responders, and third-party contractors connecting to your company’s resources.
Device trust out of the box — Most IAM solutions charge extra to add and manage device trust. In zero trust environments, we avoid risk by verifying every endpoint before granting access. Additional adaptive security policies block threats before they reach the network, stopping risky devices in their tracks to keep businesses safe. These policies should be easy to set up, manage, and adjust.
Building for phishing resistance — To address the weakest links in the identity lifecycle, IAM-driven phishing resistance begins from the minute you start onboarding users through their initial enrollment in MFA, fallback, and account recovery. Protect against remote phishing with a proximity-based authentication. Additionally, the ability to start passwordless without added costs also promotes compliance with evolving mandates for phishing resistance and zero trust strategies.
Bad things happen when security takes a backseat
Treating security like a “nice to have” leads to some obvious bad outcomes starting with greater odds of encountering a data breach. Compromised credentials and unauthorized or undetected access allow attackers to gain access to systems and escalate privileges or take over accounts. Well-known breaches like the attacks on Target, SolarWinds, and Colonial Pipeline all involved identity compromise as an initial access vector.
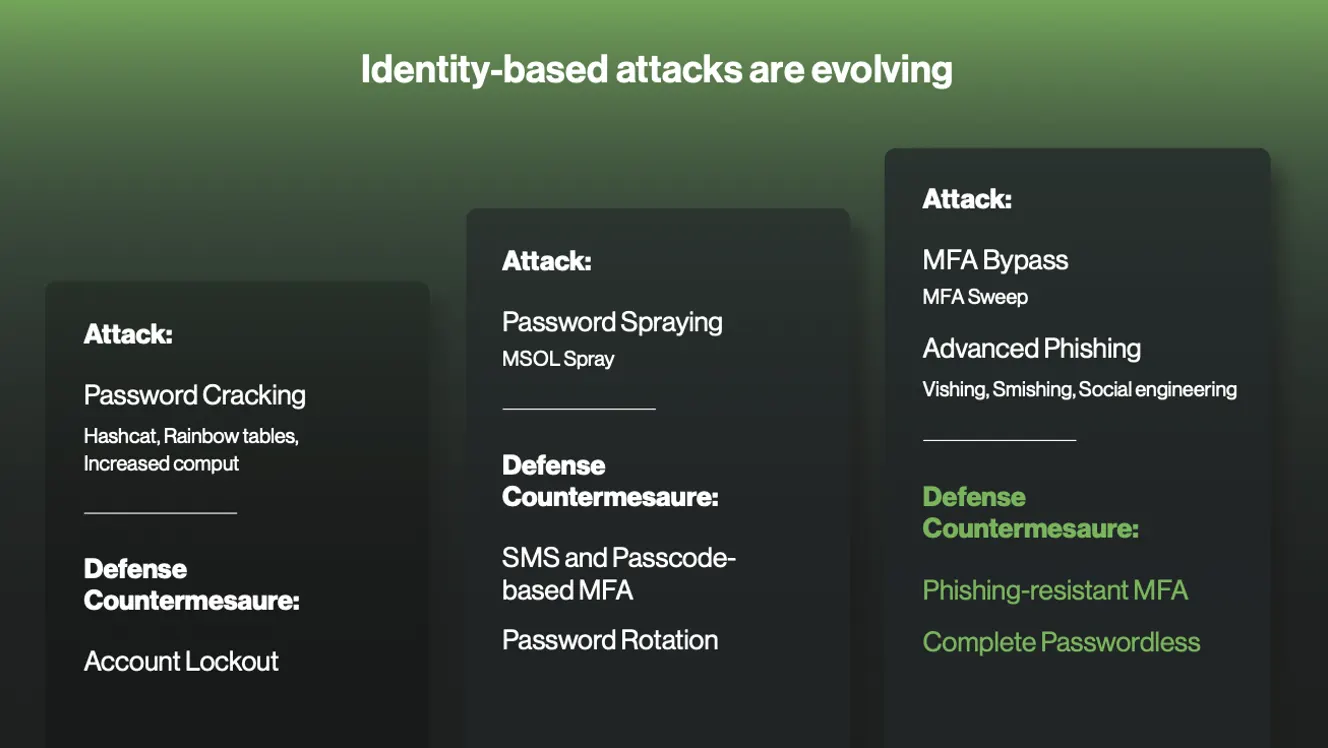
Identity-based attacks are evolving, and defensive countermeasures step up accordingly. From Guide to Duo's Security-first IAM.
IAM failures can have a high blast radius that leads to excessive financial and reputational losses from operational downtime and service disruptions. And according to a 2024 Microsoft report, poorly managed identities and access controls still play a role in more than 90% of successful ransomware attacks. Subpar security also damages the bottom line through the high costs of reputational damage, regulatory audits and fines for non-compliance, and increased cyber insurance premiums.
Users will push back: How much security is too much security?
Putting security first doesn’t mean user experience should take a backseat, either. To avoid dangerous workarounds or low enrollment, it’s important not to make accessing resources too complicated or to ask users to authenticate over and over once they’re logged in. Single sign-on (SSO) for as many applications as possible helps minimize logins, especially if the user doesn’t have to re-authenticate for their different browsers, thick clients, desktop apps, and VPN connection.
Historically, increased security often comes at the tradeoff of user friction and frustration. But really, balance is key. Modern IAM intelligently reduces the number and complexity of logins while accommodating users’ individual working styles. For example, once a user on a known, trusted device completes MFA, you can grant them longer session times before prompting the user to authenticate again.
Risk-based authentication dynamically steps-up MFA when risk is detected based on known threat patterns, user and entity behavior analytics (UEBA), and continuous security research that keeps up with evolving attacks. Continuous evaluation of trust is important. It’s a cornerstone of improving security without impeding on productivity. If everything looks good, why should users have to re-authenticate?
How do we get there from here?
We’ve already outlined a few foundational tenets of security-first IAM:
Ensure MFA is truly everywhere and plug the often-overlooked holes in your security perimeter.
Establish and set policies based on device trust. Be able to block or step up MFA controls for unknown and under-secured endpoints.
Enable with proximity-based phishing-resistant authentication and get started with moving toward a fully passwordless future.
How do we get from a vision of stronger security and frictionless productivity from where we are today?
Choose a security-first IAM solution
Does your current provider put identity or security first? If they lead with identity, do they look to “nickel and dime” you just to add basic security capabilities?
Can you trust the provider’s own security posture to protect your identity data? Has the company suffered breaches before? If so (it happens!), how did they handle the aftermath? Did they communicate effectively and take steps to better prevent future disasters?
Move toward the future one step at a time
The road to better security doesn’t have to be a rip-and-replace story. Choose an IAM solution that includes practical, forward-looking innovations like identity provider (IdP) brokering capabilities to streamline directory management and identity intelligence to self-assess your security posture.
Next week, we’ll outline an easy progression to start where you are and phase in security-first IAM without disrupting your current operations:
Find gaps in MFA coverage and enrollment
Identify unmanaged devices
Detect long gaps between user logins and review privileges
In the meantime, check out Duo's learning hub to read more about fundamental (or advanced) identity concepts, and see how Duo is restoring trust in identity with our latest guide to security-first IAM.

