Duo Authentication for Microsoft AD FS - FAQ
Last updated:
Does Duo Authentication for AD FS support the Duo Universal Prompt?
Yes, as of version 2.0.0 for AD FS on Windows 2016 and later. Please see the update instructions to install the latest version with Universal Prompt support, and then once you authenticate to Duo using the new plugin you can activate the Universal Prompt experience for your users.
The Duo AD FS application for Windows 2012 and earlier will receive no further updates and will not support Universal Prompt. Migrate to AD FS on a supported version of Windows Server (2012 R2 and later) and install the Duo for AD FS v2.x plugin before March 2024.
Does Duo Authentication for AD FS support AD FS Application Groups?
Yes, as of version 2.2.0. Prior versions did not support adding MFA to AD FS application group OIDC/OAuth client applications.
What Windows versions does Duo Authentication for AD FS support?
The Duo Authentication AD FS multi-factor adapter version 2.0.0 and later supports AD FS on Windows Server 2016, 2019, and 2022. Version 2.3.0 and later supports Windows Server 2025.
The Duo Authentication for AD FS IIS plugin version 1.1.8 supports AD FS 2.1 on Windows Server 2012 only. This plugin will not be updated to support the Duo Universal Prompt.
Microsoft ended support for Windows Server 2012 and 2012 R2 on October 10, 2023, therefore Duo's support for AD FS 2.1 on Windows 2012 and AD FS 3.0 on Windows 2012 R2 also ended on that date.
Microsoft ended support for Windows Server 2008 and 2008 R2 on January 14, 2020, therefore Duo's support for AD FS 2.0 on Windows 2008 R2 also ended on that date.
Duo's last day of support for installation and use of any Duo applications on Windows operating systems or with Microsoft applications corresponds with the Microsoft end of support. View details about Microsoft's product end of support at the Microsoft site.
We strongly urge you to upgrade to current versions of Microsoft operating systems and applications.
Why don't I see the Duo Authentication for AD FS plugin in the AD FS Management console?
If you installed version 1.1.x.x of Duo's MFA adapter for AD FS, make sure that you installed Duo from an administrator command prompt (right-click "Command Prompt" and select "Run as Administrator"). Simply double-clicking the 1.1.x.x MSI installer may not use the correct privilege elevation, even if you are logged in with administrator rights.
This issue was first corrected in version 1.2.0.17. Please install the most recent release of Duo's AD FS adapter.
How Do I uninstall Duo for AD FS?
For AD FS 2.1, simply open the Programs and Features Control Panel applet, select the Duo Security AD FS integration, and uninstall.
To uninstall Duo on an AD FS 3.0 and later server, it is necessary to disable the Duo Security for AD FS authentication method in the AD FS Management console first.
-
Navigate to AD FS → Authentication Policies and click the Edit Global Multi-factor Authentication... action (AD FS 3) or AD FS → Service → Authentication Methods and click the Edit Multi-factor Authentication Methods... action (AD FS 4).
-
Uncheck the box next to the Duo Authentication for AD FS X.X.X.X authentication method to disable Duo protection. Note that in older releases of Duo for AD FS the authentication method is called Duo Security for AD FS 3.0.
-
If you configured multi-factor authentication at the individual Relying Party level, remove the MFA requirements for those Relying Parties as well.
-
Apply the multi-factor authentication policy change, and then proceed to the Programs and Features Control Panel applet, select the Duo Security AD FS integration, and uninstall.
How do I configure the fail mode for AD FS?
If the "Bypass Duo authentication when offline" box is selected during installation, authentication attempts will fail open after primary authentication is successful if the Duo service cannot be contacted. The default for new Duo for AD FS installations is to fail closed (option not checked).This will deny all login attempts to federated resources if there is a problem contacting the Duo service.
This setting is controlled by a Registry DWORD value FailOpen, with 1 allowing fail open and 0 preventing fail open.
| AD FS Version | Registry Path |
|---|---|
| AD FS 2.1 | HKLM\SOFTWARE\Duo Security\DuoIis\FailOpen |
| AD FS 3.0+ | HKLM\Software\Duo Security\DuoAdfs\FailOpen |
You can change the fail mode during installation to "fail open" by selecting the "Bypass Duo authentication when offline" box in the Duo installer, or modify the setting after installation by changing the Duo registry DWORD FailOpen value.
Duo for AD FS v1.x installers enabled fail open by default. Duo for AD FS v2.x installers now default to fail closed, but preserve the selection made by a previously installed version on upgrade.
How do I enable debug logging?
The Duo event log for the AD FS integration is under the "Applications and Services Logs" node in the Windows Event Viewer.
- ADFS 2.1: "Duo IIS Integration"
- ADFS 3 and later: "Duo Authentication for AD FS 3.0" or "Duo Security for AD FS 3.0"
To turn on debug logging, create a registry REG_DWORD value Debug set to 1.
| AD FS Version | Registry Path |
|---|---|
| AD FS 2.1 | HKLM\Software\Duo Security\DuoIis\Debug |
| AD FS 3 & 4 | HKLM\Software\Duo Security\DuoAdfs\Debug |
After creating the debug DWORD value, cycle the appropriate service:
- ADFS 2.1: Restart the IIS service.
- ADFS 3 & 4: Restart the AD FS service.
How do I change the username format sent to Duo?
Duo's AD FS adapter sends a user's sAMAccountName to Duo as the Duo username by default. You can change the username format sent to Duo to userPrincipalName (UPN) starting with version 1.2.0.17.
If you enable this option, you must also change the properties of your AD FS application in the Duo Admin Panel to change the "Username normalization" setting to None, or Duo will drop the domain suffix from the username sent from AD FS to our service, which may cause user mismatches or duplicate enrollment.
Choose to send userPrincipalName usernames to Duo during installation by selecting the "Use UPN username format" box in the Duo installer.
Changing this setting after Duo adapter installation requires creating a new registry value and re-registering the Duo adapter using PowerShell.
-
Follow the instructions for disabling the Duo MFA adapter in the AD FS Management Console. While you are doing this, note the version of the Duo adapter (e.g.
1.2.0.17). -
Launch the PowerShell command line interface with elevated permissions (right-click PowerShell and choose "Run as Administrator").
-
Issue the command
Unregister-AdfsAuthenticationProvider DuoAdfsAdapterat the PowerShell prompt. If asked to confirm the action typeYfor "Yes". -
Cycle the AD FS service by entering the command
Restart-Service adfssrvat the PowerShell prompt. -
Launch the Registry Editor (regedit.exe) from the elevated PowerShell prompt and navigate to
HKLM\Software\Duo Security\DuoAdfs.Create or update the REG_DWORD value
UseUpnUsernameto set it to 1 to enable UPN username format.Alternatively, you can enter the command
reg add "HKLM\Software\Duo Security\DuoAdfs" /v UseUpnUsername /t REG_DWORD /d 1 /fin PowerShell to create or update the registry value. -
Re-register the Duo AD FS adapter from PowerShell with the command
Register-AdfsAuthenticationProvider -TypeName "Duo.DuoAdfsAdapter, DuoAdfsAdapter, Version=X.X.X.X, Culture=neutral, PublicKeyToken=cac53dcfadb30b87" -Name "DuoAdfsAdapter" -Verbose, whereX.X.X.Xis the Duo MFA adapter version you noted in step 1 (e.g.1.2.0.17). -
Cycle the AD FS service again with
Restart-Service adfssrv. -
Re-enable the Duo MFA adapter in the AD FS Management Console.
Example showing all PowerShell steps:
PS C:\Users\administrator> Unregister-AdfsAuthenticationProvider DuoAdfsAdapter
Confirm
Are you sure you want to perform this action?
Performing the operation "PS0061: Remove external authentication provider: 'DuoAdfsAdapter'." on target
"DuoAdfsAdapter".
[Y] Yes [A] Yes to All [N] No [L] No to All [S] Suspend [?] Help (default is "Y"): y
WARNING: PS0103: The authentication provider was successfully unregistered from the policy store. Restart the AD FS
Windows Service on each server in the farm.
PS C:\Users\administrator> Restart-Service adfssrv
WARNING: Waiting for service 'Active Directory Federation Services (adfssrv)' to start...
WARNING: Waiting for service 'Active Directory Federation Services (adfssrv)' to start...
PS C:\Users\administrator> reg add "HKLM\Software\Duo Security\DuoAdfs" /v UseUpnUsername /t REG_DWORD /d 1 /f
The operation completed successfully.
PS C:\Users\administrator> Register-AdfsAuthenticationProvider -TypeName "Duo.DuoAdfsAdapter, DuoAdfsAdapter,
Version=1.2.0.17, Culture=neutral, PublicKeyToken=cac53dcfadb30b87" -Name "DuoAdfsAdapter" -Verbose
WARNING: PS0114: The authentication provider was successfully registered with the policy store. To enable this
provider, you must restart the AD FS Windows Service on each server in the farm.
PS C:\Users\administrator> Restart-Service adfssrv
WARNING: Waiting for service 'Active Directory Federation Services (adfssrv)' to start...
WARNING: Waiting for service 'Active Directory Federation Services (adfssrv)' to start...
PS C:\Users\administrator>How do I resolve the error "Request to server has been blocked by extension" when logging in to Duo-protected AD FS on Server 2019 with v1.x of the Duo adapter?
The inline Duo Prompt is blocked by the AD FS 2019 default Content Security Policy. Run the following PowerShell command to permit display of the Duo Prompt, replacing api-xxxxxxxx.duosecurity.com with your actual Duo API hostname:
Set-AdfsResponseHeaders -SetHeaderName "Content-Security-Policy" -SetHeaderValue "default-src 'self' 'unsafe-inline' 'unsafe-eval'; img-src 'self'; frame-src api-xxxxxxxx.duosecurity.com"
This is no longer required with the Duo for AD FS v2.0.0 or later adapter.
Is Office rich client login or the Office 365 mobile app supported?
Office desktop applications (including Outlook and Skype for Business) by default can no longer connect to Office 365 after installing the Duo ADFS integration. Office 365 customers must enable Microsoft's Modern Authentication to bring two-factor authentication to Office client applications (or construct MFA rules that exclude Office applications). More information about Modern Authentication, including a list of Office applications that support Modern Authentication, is available at the Office Blog.
- Modern Authentication may already be enabled on your Office 365 tenant. Follow these instructions to verify or enable Modern Authentication on your Exchange Online tenant and these instructions to do the same for your Skype for Business Online tenant.
- Apply registry updates for Office 2013 (Office 2016 natively supports Modern Authentication).
- Your Office applications should now provide you with your federated login page followed by the Duo Authentication prompt. Once you authenticate with Duo the session security token is cached and remains valid for eight hours.
When you log in to Office 365 using an Office 2016 or 2013 application with Modern Authentication, you'll see the AD FS primary login page within the Office application, followed by the Duo authentication prompt.
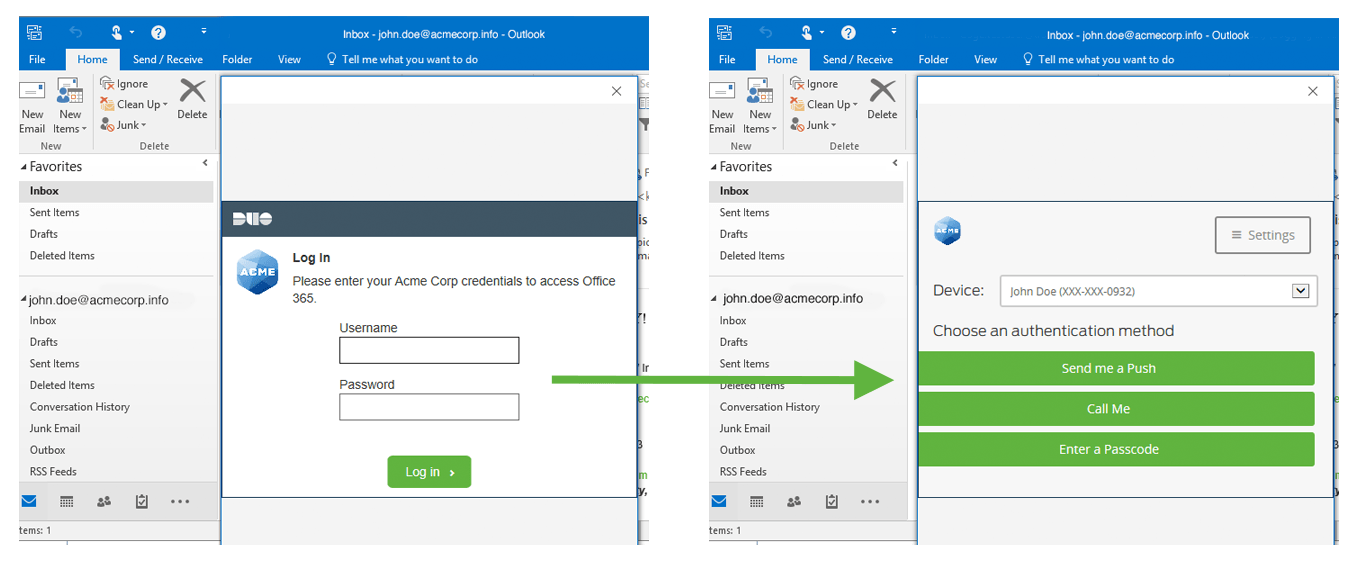
For additional information please see the "Road map for multi-factor authentication in Office desktop applications" section in this blog post from Microsoft: Multi-Factor Authentication for Office 365 and the previous blog entries Office 2013 updated authentication enabling Multi-Factor Authentication and SAML identity providers and Office 2013 modern authentication public preview announced.
Duo does not natively support the creation of application specific passwords for bypassing multi-factor authentication for Office 365 tenants.
If you need to enforce more complex MFA rules for an Office 365 relying party to include or exclude certain clients, groups, or networks, please take a look at our Guide to advanced client configuration for Duo with AD FS 3 and later with Office 365 Modern Authentication.
What claims are supported for Duo two-factor authentication?
When using Duo with AD FS 2.1, the assertion must contain a SAML 2.0 NameId or a WS-Federation (AD FS 1.1 compatible) UserPrincipalName, WindowsAccountName, or EmailAddress. Additionally, the SAML assertion must not be encrypted.
Why do I receive an error trying to install the Duo AD FS application version 1.1.x.x on secondary servers in an AD FS 3 or later SQL server farm after a successful install on the primary server?
You may receive the error "An authentication provider with identifier 'DuoAdfsAdapter' is already present in the policy store. Identifiers must be unique." when attempting to install Duo Authentication for AD FS 3 version 1.1.0 or later on additional SQL farm members.
This issue was corrected in version 1.2.0.17. Please install the most recent release of Duo's AD FS adapter.
Does the AD FS server require internet access?
The AD FS server does not need to be externally accessible from the internet if you are using a AD FS Proxy, but the Duo AD FS integration installed on the server does require access to the Duo cloud service over the internet. Without internet access users may experience delays, timeouts, or failures to authenticate Duo after submitting their primary login credentials.
Do I need to click the "Enable Duo Security Authentication Module" button for the Default Web Site in IIS Manager to complete the installation?
No additional actions are required to enable the Duo Security integration. Do not click the "Enable Duo Security Authentication Module" button.
Additional Troubleshooting
Need more help? Try searching our AD FS Knowledge Base articles or Community discussions. For further assistance, contact Support.
