MSP Delegated Access
Last updated:
Overview
Delegated Access allows users placed into a group on the main (parent) account to authenticate into customer applications on subaccounts.
This feature is not available in Duo Federal editions.
Prerequisites
-
An MSP account is required to use this feature.
-
Ensure MSP users are users with a 2FA device on the main account. MSP users that need to access subaccount applications must be enrolled in the parent (main) account. This user should not be added to the Duo subaccount. The username for this user should be the same as the username that the application uses to login to.
- The main account user must have an active 2FA device. Inline device enrollment is not permitted with Delegated Access.
-
The username (or user alias) cannot exist in the customer’s subaccount. If the username exists in the subaccount, the authentication will not be delegated to the user on the main (parent) account.
Known Limitations
Application Feature Limitations
-
Delegated Access does not work with Passwordless OS Logon for Windows, Offline Access for Windows, or Offline Access for macOS. The MSP main account user will not be able to use any of these login features when logging into the subaccount application via Delegated Access.
-
Delegated Access overrides any user access restrictions specified on the subaccount application. A Delegated Access user may log in to a subaccount application regardless of any user access restriction in place.
-
Delegated Access does not work with SSO applications. You cannot delegate access from SSO applications.
Policy Limitations
Please note the following restrictions when editing a policy with delegated access:
-
Remembered devices is disabled for Delegated Access to ensure a higher level of security. Even if you apply a remembered devices policy to the Delegated Access, it will not take effect.
-
Users in bypass status will be unable to use Delegated Access.
-
Any policy that could bypass authentication will be ignored and all users will be required to authenticate (or blocked if specified in policy). These include:
- Authentication policy - when "Bypass 2FA" is enabled.
- Authorized networks
- User Location - you can use this policy to block use of Delegated Access, but not to bypass it.
Setup Delegated Access
Role required: Owner
To setup Delegated Access, you will need to add your users to a group, and then enable those groups to use Delegated Access. Once setup, MSP users can authenticate into their subaccount applications.
Add User to a Group
To add your user to a group or confirm groups you choose to permit to use Delegated Access:
-
Log into the Duo Admin Panel.
-
On the main (parent) account, navigate to Users → Groups.
-
Click on the group that you want to permit to use Delegated Access.
-
Click +Add users to group. Select from the drop-down list the users you want to add to a group for use with Delegated Access.
-
Click Add User to Group.
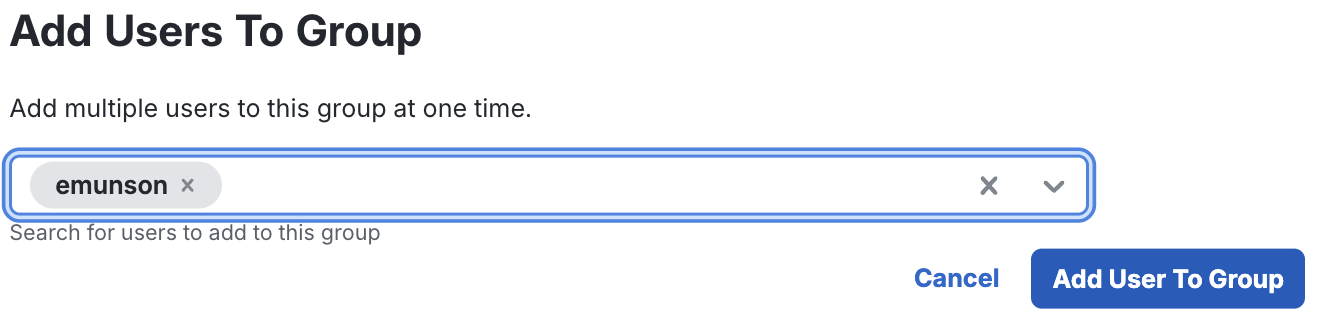
-
Confirm which groups you intend to permit to authenticate into subaccount applications.
In the next step, you will enable these groups to use Delegated Access to access customer applications.
Enable Groups to use Delegated Access
To enable groups to use Delegated Access:
-
While still in the main (parent) account, navigate to Accounts → Delegated Access.
-
From the "Delegated Access" page, in the "Subaccount application access" section, select Enable for selected groups.
-
Choose your designated group(s) from the drop-down list.
-
Click Save access.
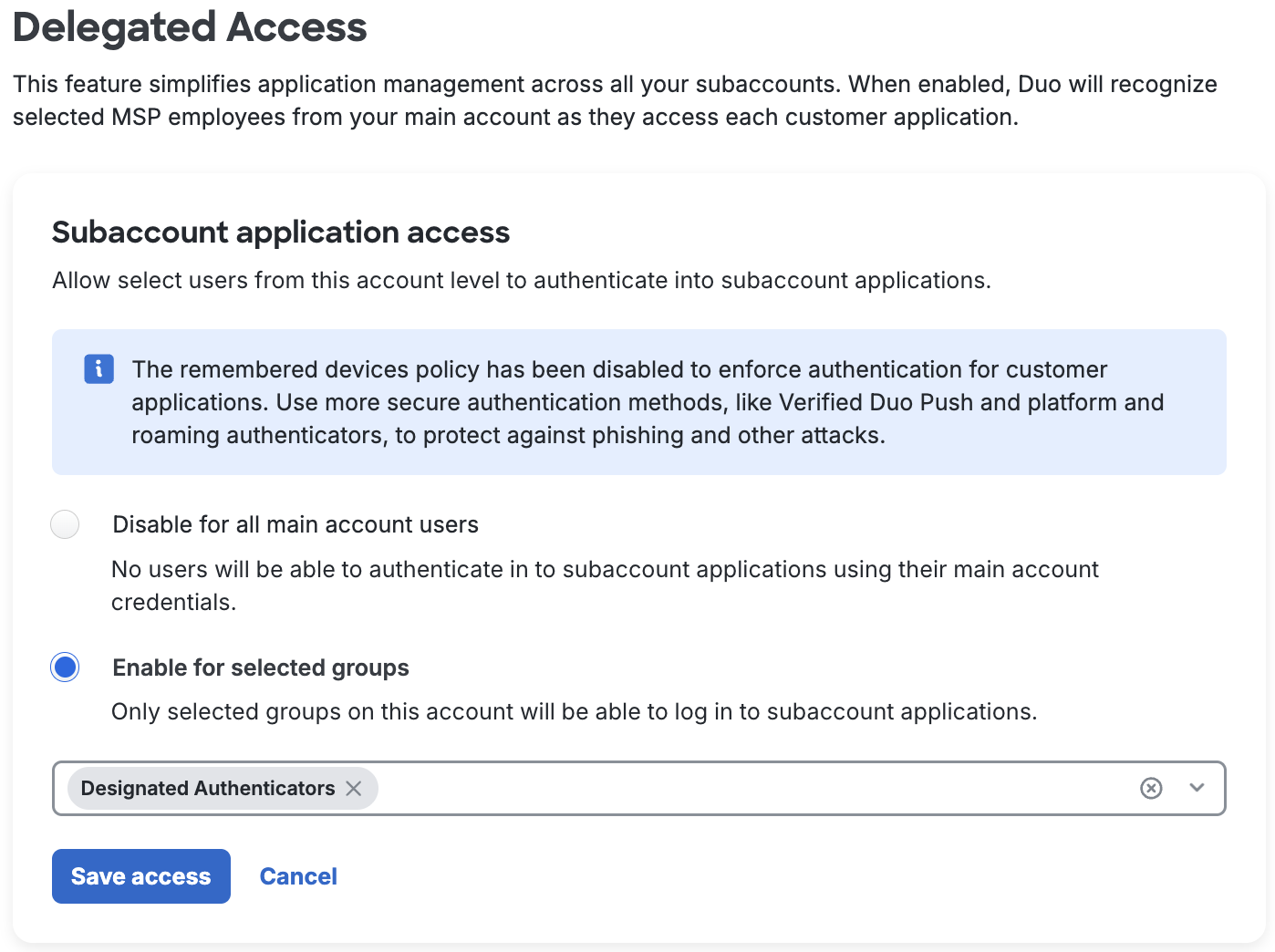
- This setting allows only users in selected groups to log into subaccount applications, and only if their username exists in the application.
Edit Subaccount Policies
The "Policies" section on the "Delegated Access" page shows when and how users will authenticate when accessing subaccount applications via Delegated Access. Your global policy always applies, but you can override it with custom policies with custom group or application policies.
Policies will be evaluated at the main (parent) account and not at the subaccount when authenticating via Delegated Access, except for username normalization if set up in the application on the subaccount. For more information, refer to the Policy documentation.
For increased security, we do not allow policies that bypass MFA when using Delegated Access, including Remembered Devices and Authentication policy.
Edit Settings
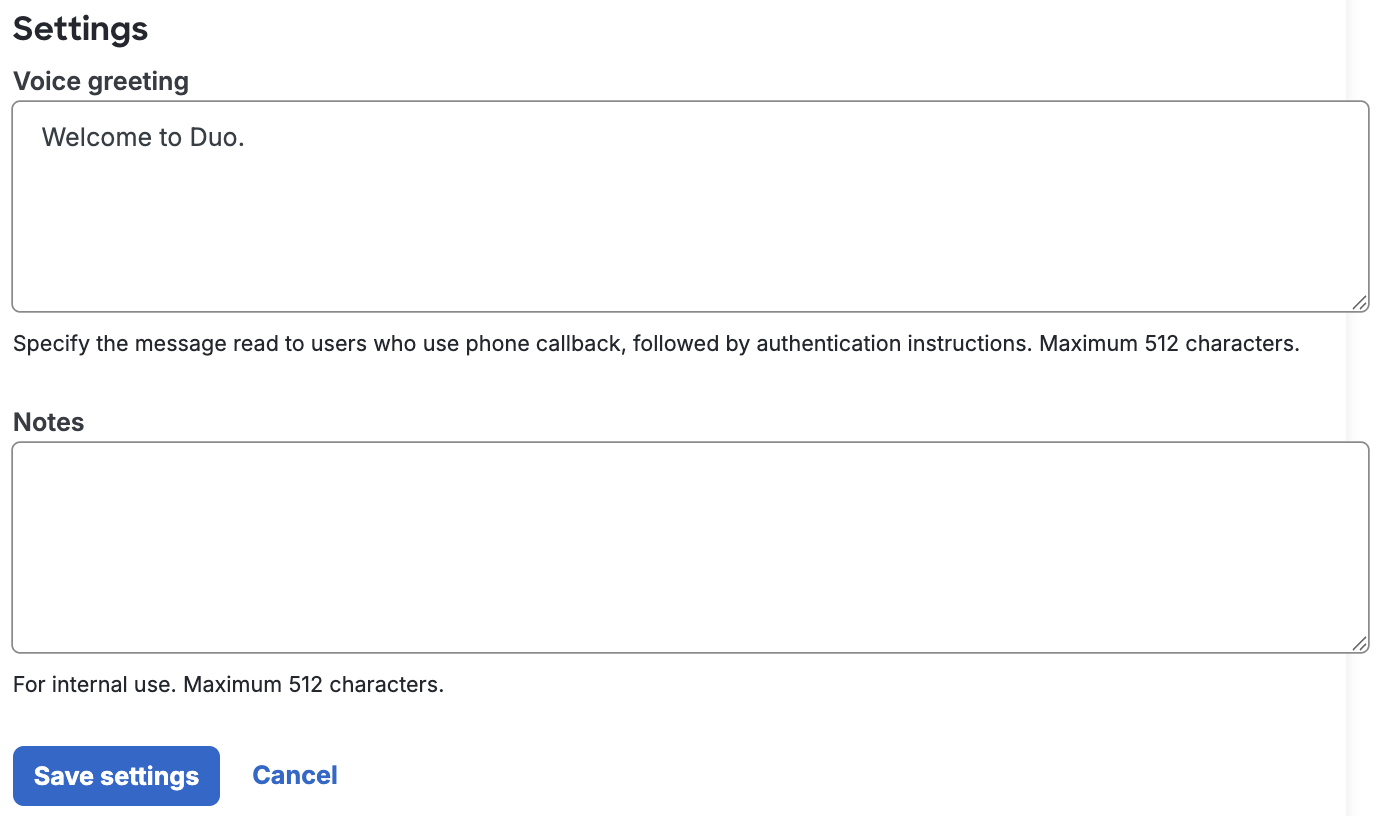
Use the Settings section on the "Delegated Access" page to add:
- Voice greeting or message to users who use phone callback, followed by authentication instructions.
- Notes - for internal notes.
To save your settings, click Save settings.
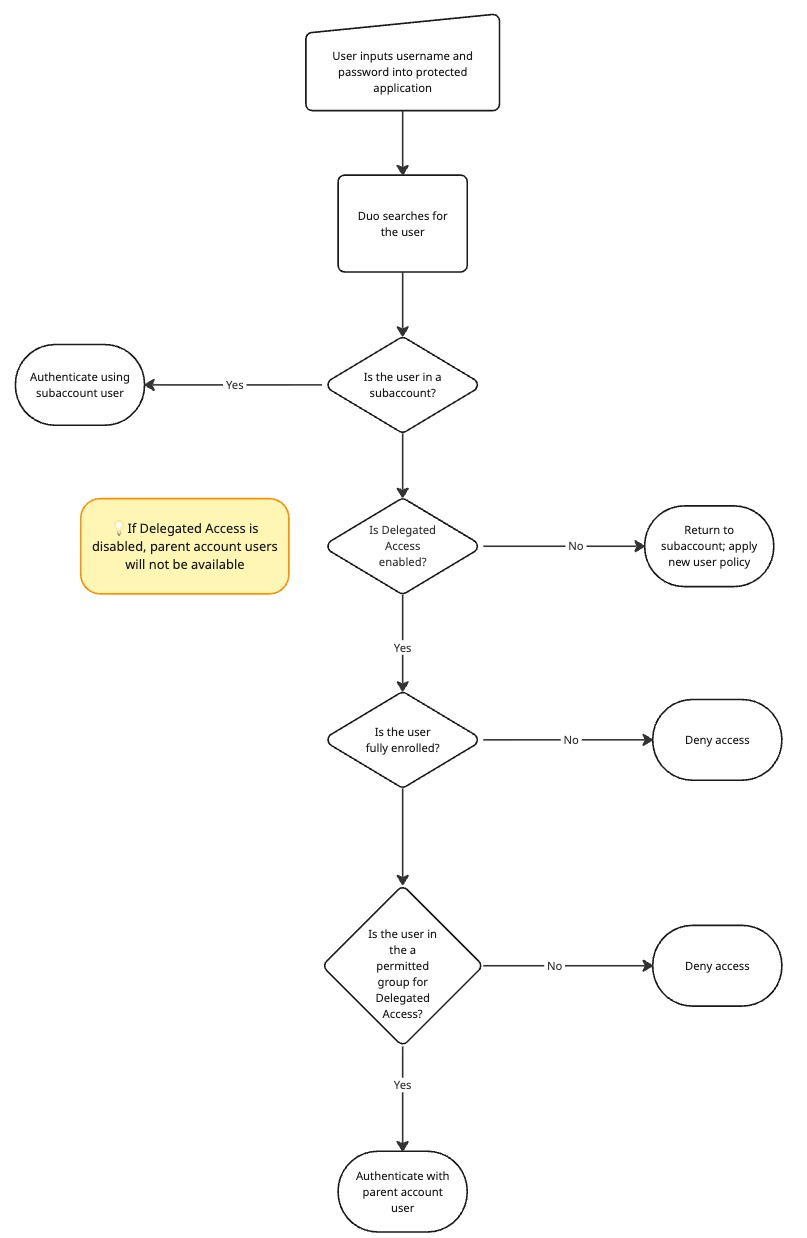
Authenticate Using Delegated Access
If a delegated authentication was successfully completed, the MSP parent user can log in with any of their existing authentication methods. There will be no enrollment prompt. If the user chose Duo Push as the authentication method, then the Duo Push notification will specify "Delegated Access - [Application Name]".
If the user receives an enrollment prompt, completing enrollment will add the user to the subaccount; this will disable Delegated Access for that user until they are deleted from the subaccount.
See the diagram below for more information on how user decisions are made during delegated access.
Validate Authentication
To validate that the authentication performed was delegated to the user on the main (parent) account:
-
Navigate to Reports → Authentication Log from the main (parent) account. If successful, you will see that the user was approved via Delegated Access. The user column will have the following structure: {Subaccount name} - {Subaccount application name}.
-
You may also filter your Authentication Log by the Delegated Access application to see all attempts at delegated authentications.
You can view authentication logs for Delegated Access on the subaccount by navigating to subaccount → Reports → Authentication Log. The user column will have the following structure: Delegated Access:{parent user username}.
Frequently Asked Questions
Does Delegated Access work with all applications?
- No, it does not support SSO applications.
How is policy evaluated?
- Policy is evaluated entirely on the parent account. Regardless of what policy is configured on the subaccount and subaccount application, Duo will only consider policy on the parent account as applied on the "Delegated Access" page.
How are usernames normalized?
- If a subaccount application has username normalization toggled on, usernames will arrive to the main account already normalized. If username normalization is not enabled on the subaccount application, Duo will only match the username with the username on a main account if it is an exact match.
Can the delegated users be on a subaccount?
- No, they must be on the parent (main) account.
Can you restrict which subaccounts an MSP user may use Delegated Access for?
- No, not at present. If your organization needs this, please let us know.
Troubleshooting
Need some help? Take a look at our MSP Knowledge Base articles or Community discussions. For further assistance, contact Support.
