Duo 2FA for F5 BIG-IP APM - FAQs
Last updated:
Do any of Duo's configurations for F5 BIG-IP support the Duo Universal Prompt?
The F5 BIG-IP APM OIDC configuration provides Universal Prompt support for F5 BIG-IP logins. Another alternative with Universal Prompt is to configure Duo Single Sign-on with a generic SAML application.
RADIUS configurations for F5 BIG-IP that feature the traditional Duo Prompt with radius_server_iframe reached its end of support on March 30, 2024. Customers must migrate F5 BIG-IP deployments to BIG-IP OIDC, Duo Single Sign-On, or a RADIUS configuration that does not use the iframe, such as BIG-IP RADIUS with Auto Push Instructions, for continued support from Duo.
Learn more about options for out-of-scope applications in the Universal Prompt update guide, and review the Duo End of Sale, Last Date of Support, and End of Life Policy.
My WebTop users are not being prompted to reauthenticate if they close the F5 session browser tab. How can I force them to reauthenticate?
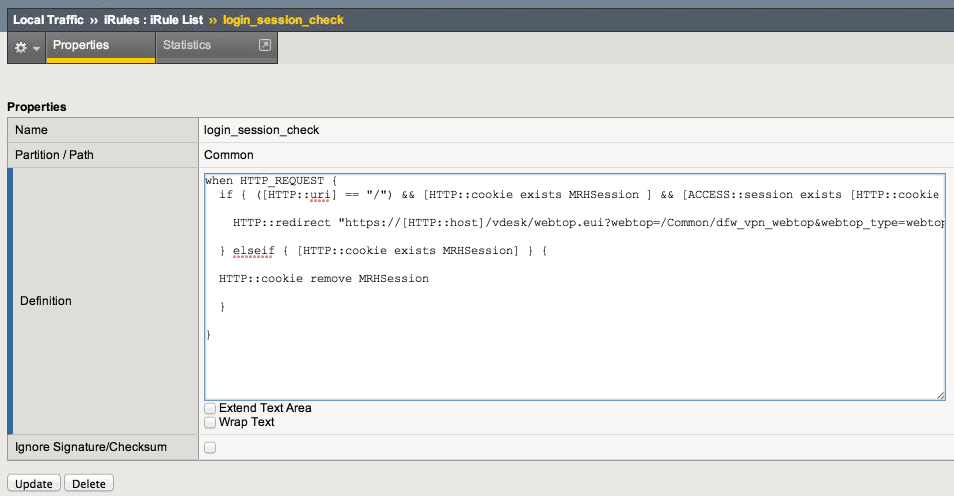
The F5 APM 11.4 may not be clearing out the WebTop session cookies correctly. Try creating an iRule to remove the cookie on the Local Traffic branch of your defined WebTop Access Policy with the following definition (in this example the name of the Access Policy is dfw_vpn):
when HTTP_REQUEST {
if { ([HTTP::uri] == "/") && [HTTP::cookie exists MRHSession ] && [ACCESS::session exists [HTTP::cookie value MRHSession]] }{
HTTP::redirect "https://[HTTP::host]/vdesk/webtop.eui?webtop=/Common/dfw_vpn_webtop&webtop_type=webtop_full"
} elseif { [HTTP::cookie exists MRHSession] } {
HTTP::cookie remove MRHSession
}
}
Consult the BIG-IP Access Policy Manager Configuration Guide for more information about iRule creation and syntax or contact F5 support.
Additional Troubleshooting
Need more help? Try searching our F5 BIG-IP Knowledge Base articles or Community discussions. For further assistance, contact Support.
