Duo Identity Security with Cisco Identity Intelligence
Last updated:
Overview
Duo Identity Security combines Duo’s strong attack mitigation and remediation capabilities with cross-vendor identity insights powered by Cisco Identity Intelligence.
Cisco Identity Intelligence
Cisco Identity Intelligence (CII) is a multi-sourced, vendor-agnostic solution that works across your existing identity stack and brings together authentication and access insights, enabling you to proactively address vulnerabilities and risks in your multi-vendor identity environment.
All Cisco Identity Intelligence features and capabilities are included in Duo Identity Security for Duo Premier and Duo Advantage customers.
Learn more about Cisco Identity Intelligence.
Requirements
The requirements for provisioning Cisco Identity Intelligence are:
- A Duo Premier or Duo Advantage plan.
- A Duo administrator with the Owner or Administrator role.
- Everyone in your organization whom you want to be able to access the Cisco Identity Intelligence dashboard via Duo Single Sign-On should exist as an end-user in your Duo account your SAML or Active Directory external authentication source if you use them.
If you are using Active Directory Sync or Microsoft Entra ID Sync, Cisco Identity Intelligence will use the source directory's unique identifiers to associate Duo identities with matching identities in other vendors.
If you are not using Active Directory Sync or Microsoft Entra ID Sync, an email address will be required for the username or email field for your Duo users in order for Cisco Identity Intelligence to map Duo user identities to corresponding identities in other data integrations. The email address used in Duo must match an email address in another integrated platform (e.g., Okta, Google Workspace, AWS).
Provision Your Cisco Identity Intelligence Tenant
-
Log on to the Duo Admin Panel as an administrator with the Owner or Administrator admin role.
-
Navigate to Monitoring → Cisco Identity Intelligence.
-
Review the information on the "Cisco Identity Intelligence" page. Click the Connect to Cisco Identity Intelligence button to continue.
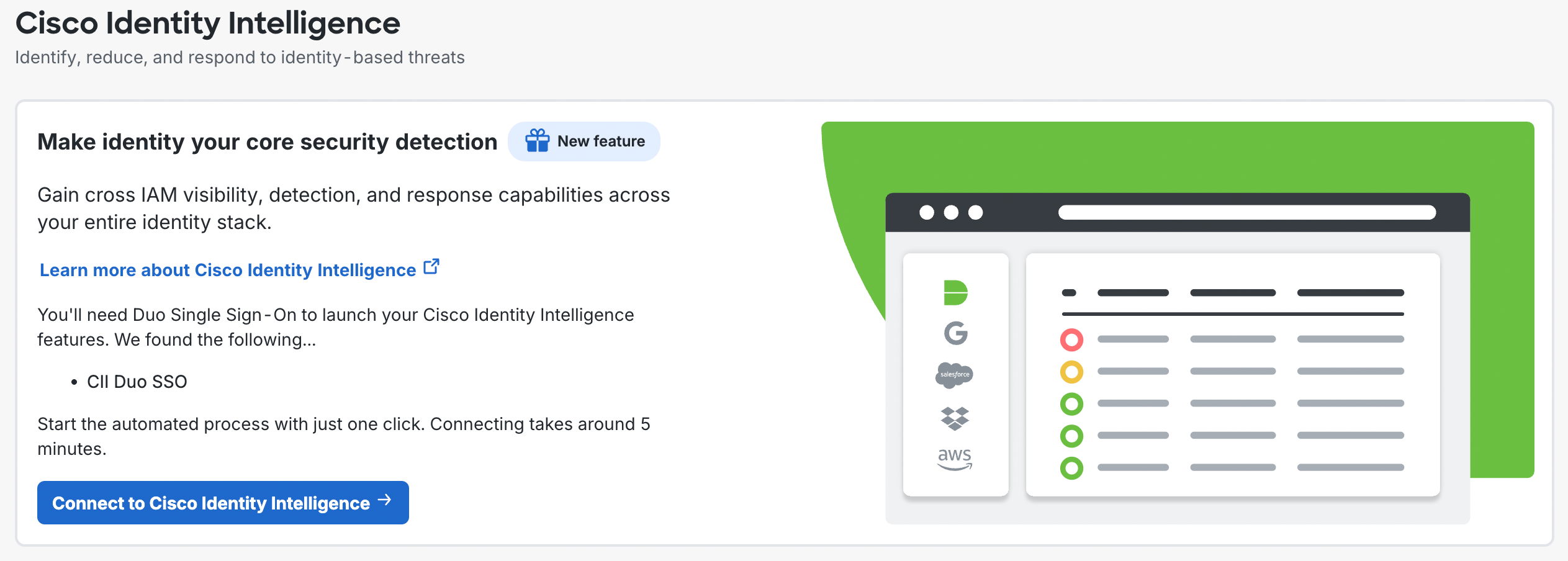
-
Duo will automatically provision your Duo integration with Identity Intelligence to enable your new Identity Intelligence tools to consume and analyze Duo user and authentication data.
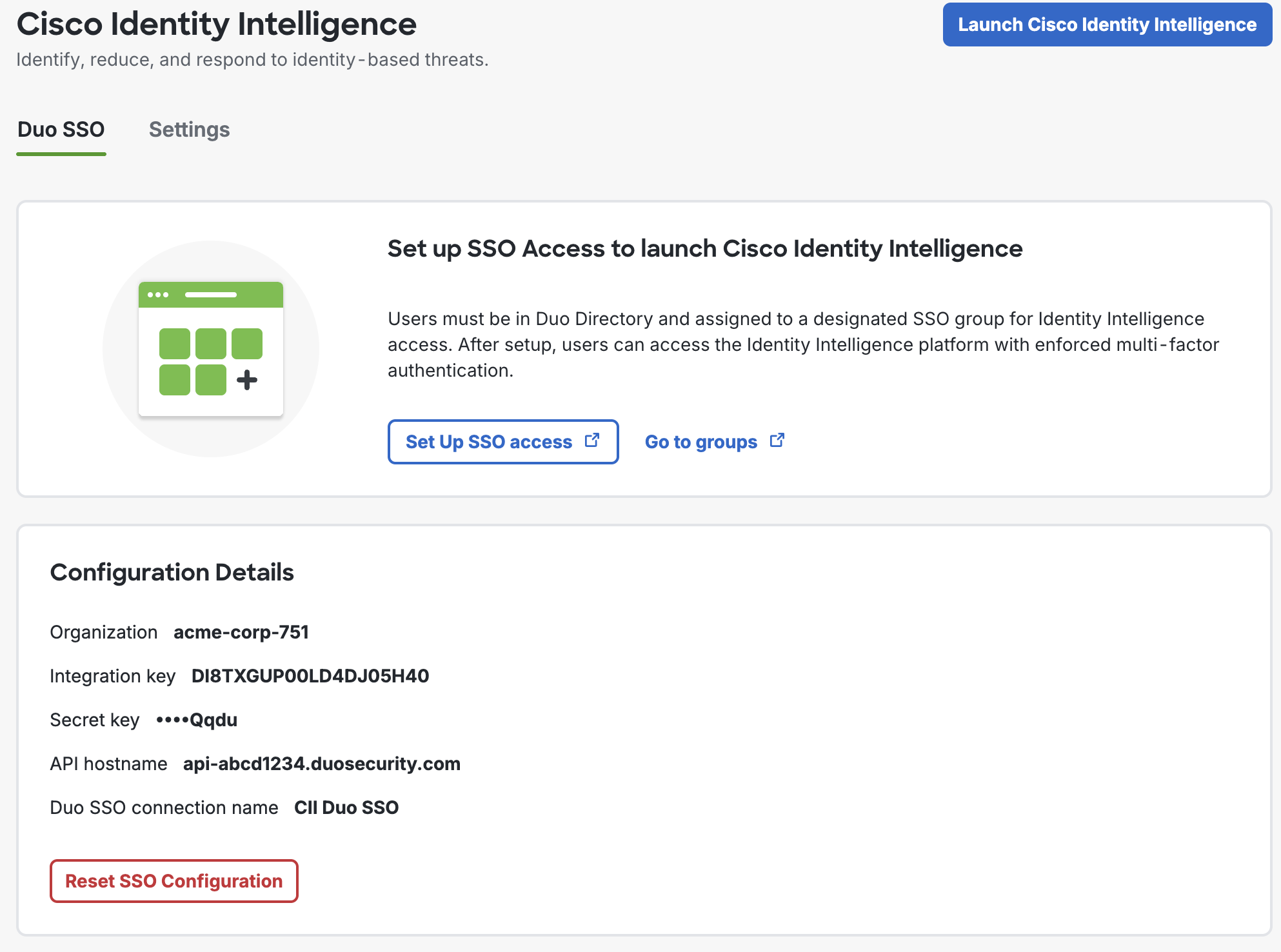
-
You should verify the user access and group mappings for the new CII SSO application. Click the Setup SSO Access button on the Cisco Identity Intelligence "Duo SSO" tab to view the SSO application.
-
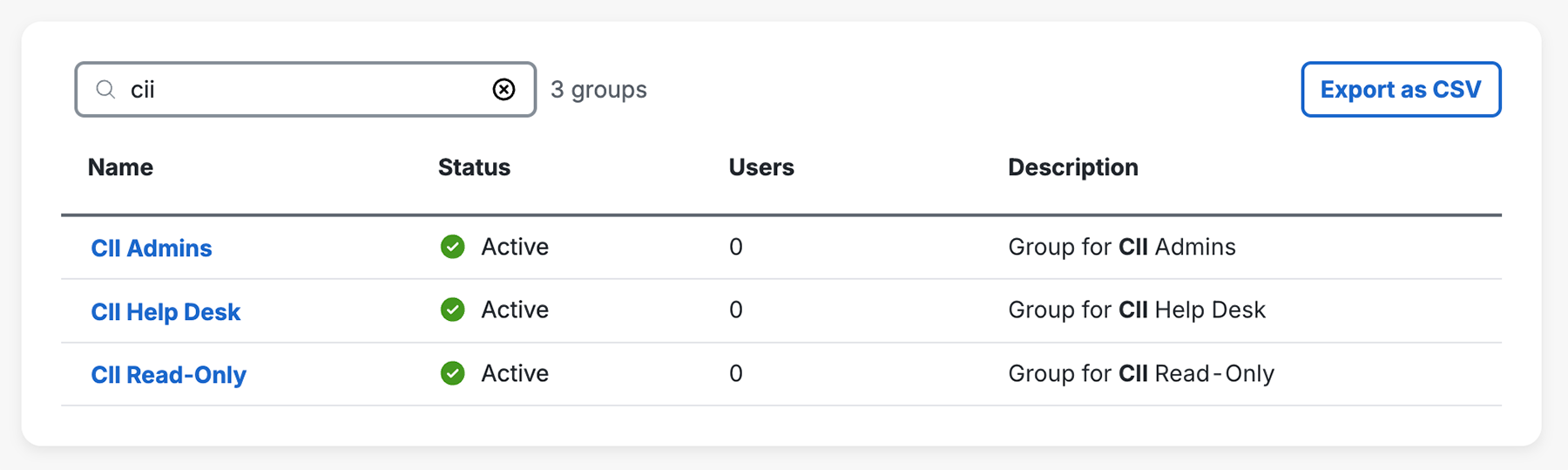
The CII provisioning process creates three groups in Duo for mapping CII role access: CII Admins, CII Help Desk, and CII Read-Only. You should see that the "User access" setting for your autogenerated Cisco Identity Intelligence SSO application defaults to Enable only for permitted groups with the three CII role groups automatically selected. If these groups do not exist, you may create them manually. You may also add any Duo groups you already created that contain your CII administrators.
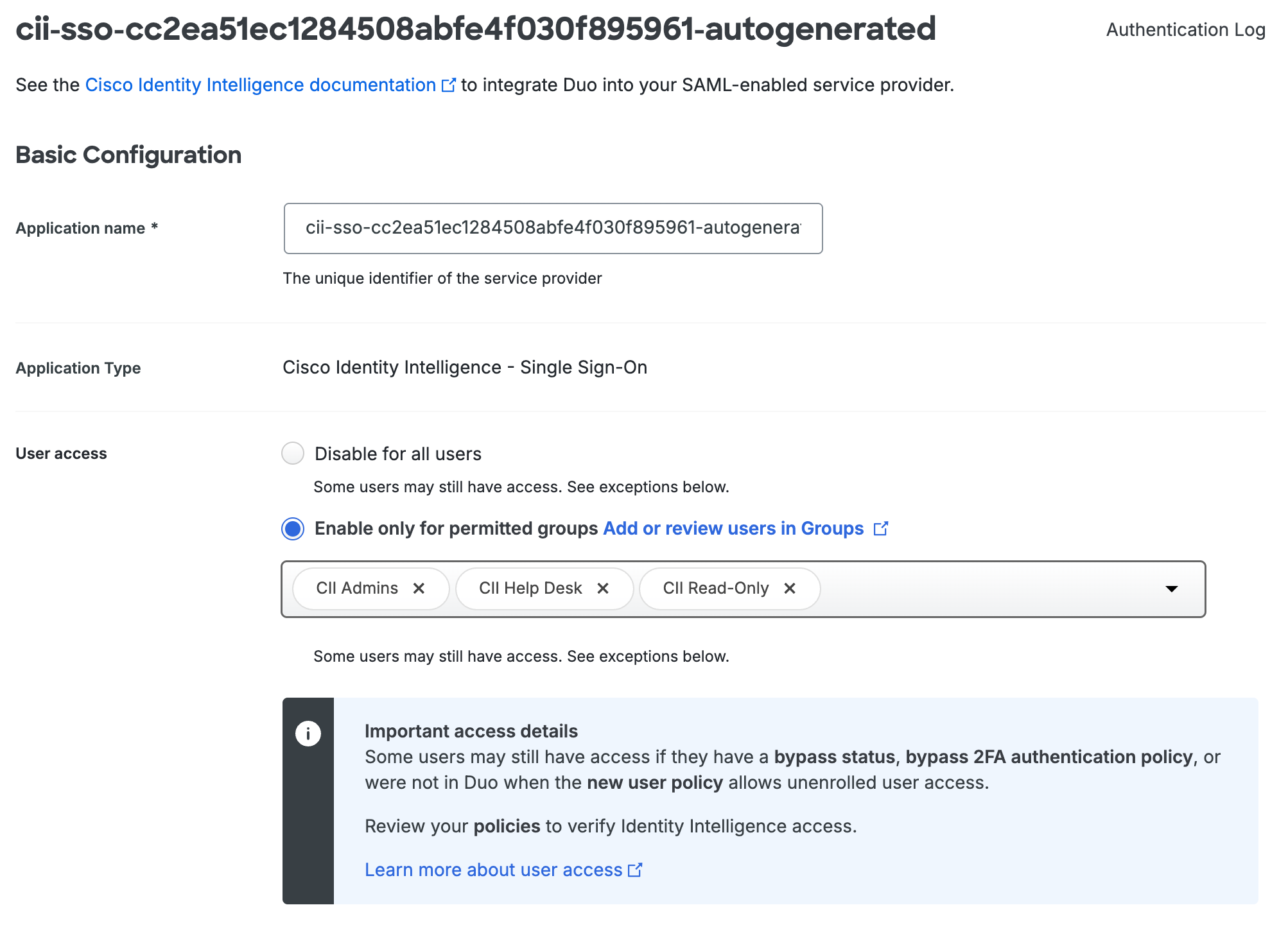
-
Scroll down to the "Role-based Access" section of the CII SSO application page. You should see default mappings in place as follows:
CII role mapping Duo groups CII Admins CII Admins CII Help Desk CII Help Desk CII Read-Only CII Read-Only If you have other Duo groups containing your CII console access users, you can add them to the default CII role mappings with the drop-down selector.
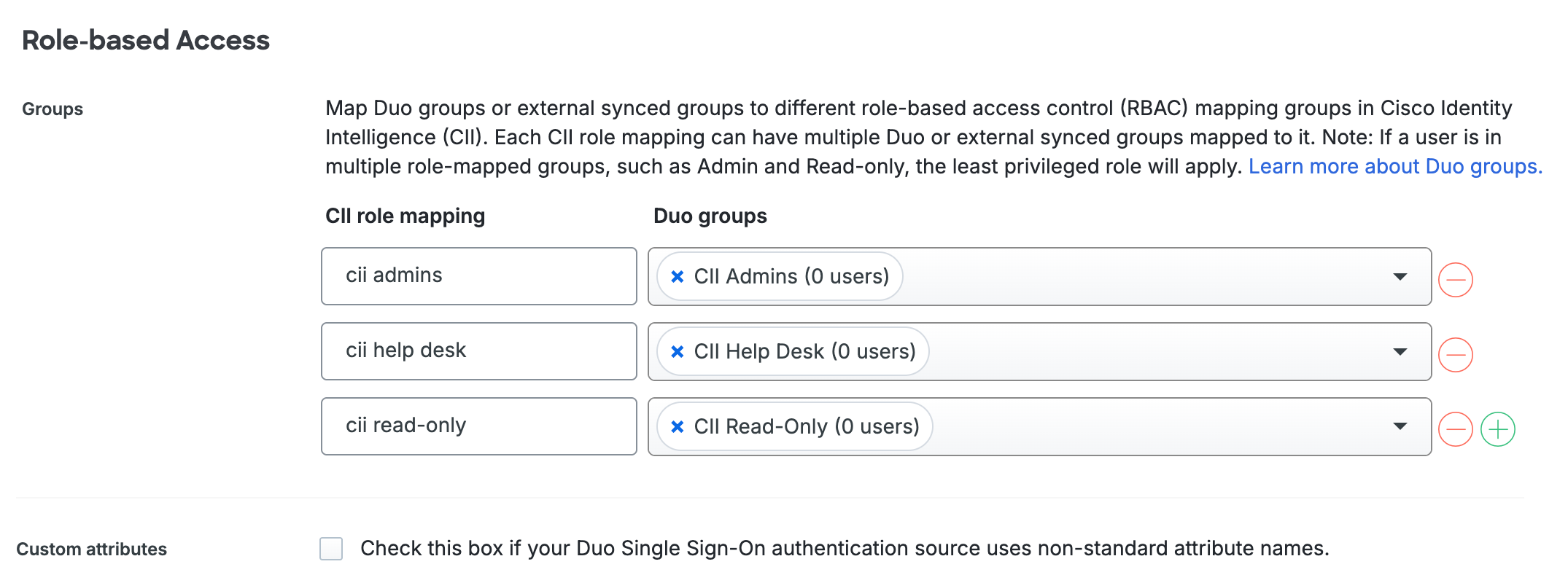
If you do not plan to use one of the CII roles you may remove it. Use the Add button to restore a CII role you've deleted. You may not add additional roles.
-
If you made any changes to user access or to the group mappings, scroll down and click Save.
-
Navigate to Users → Groups and populate the three CII groups with the Duo users who should have access to the CII dashboard by clicking each one's name and then clicking Add users to group.
While you can't add users synced from external directories as members of the CII default groups, you can add groups managed by directory sync to the role mappings as described in the previous steps.
See the Using Groups documentation for more detailed group management instructions.
-
You can now use your Identity Intelligence tenant. Navigate to Monitoring → Cisco Identity Intelligence again and click the Launch Identity Intelligence button. This launches the Identity Intelligence dashboard from the Duo Admin Panel. Duo administrators logged into the Admin Panel with any role assigned can access the Identity Intelligence dashboard from this link to log in via Duo SSO.
Make sure that any Duo admins accessing Identity Intelligence also exist as an end-user in Duo who is a member of the group granted access to the CII SSO application. Active Duo users in the permitted groups whose effective policy requires MFA can sign in to Cisco Identity Intelligence via Duo SSO. Active Duo users whose effective policy requires MFA who are not members of one of the CII permitted groups will receive an access error from Duo SSO. Review the warnings about user access.
If you use an external identity source for SSO also ensure the CII dashboard user exists there for primary authentication.
Next Steps After Provisioning
Data ingestion and analysis of Duo data begins automatically after provisioning. Depending on how many identities exist in your environment, it can take a few days for all the data in your environment to get fully synchronized in the Cisco Identity Intelligence tenant.
Create Additional Integrations
Set up additional available integrations to maximize the cross-vendor visibility that Cisco Identity Intelligence provides and to ensure protection of your full identity ecosystem.
Integrations
Cisco Identity Intelligence can integrate with a number of vendors for data ingestion, ticketing, notifications, and SIEM usage.
You can read more about the integrations and find configuration instructions by following the links below.
Cisco Identity Intelligence can ingest data from the following sources:
- Auth0
- AWS
- GitHub
- Google Workspace
- Microsoft Active Directory (Beta)
- Microsoft Entra ID
- Microsoft Entra ID Event Hub
- Okta
- Salesforce
- Workday
Additionally, integrations are available for notifications, ticketing and SIEMs:
Troubleshooting
Need some help? Take a look at our Identity Security Knowledge Base articles or Community discussions. For further assistance, contact Support.
