FAQs
-
What are the three main types of authentication methods?
Combinations of these authentication techniques are often used for MFA and 2FA authentication:
- Something you know: This knowledge-based method relies on something the user knows, such as a password, PIN, or personal security questions.
- Something you have: This method verifies user identity through a physical item the user possesses, such as a mobile phone, a security token, or a smart card. The item either generates or receives an OTP or serves as a physical key.
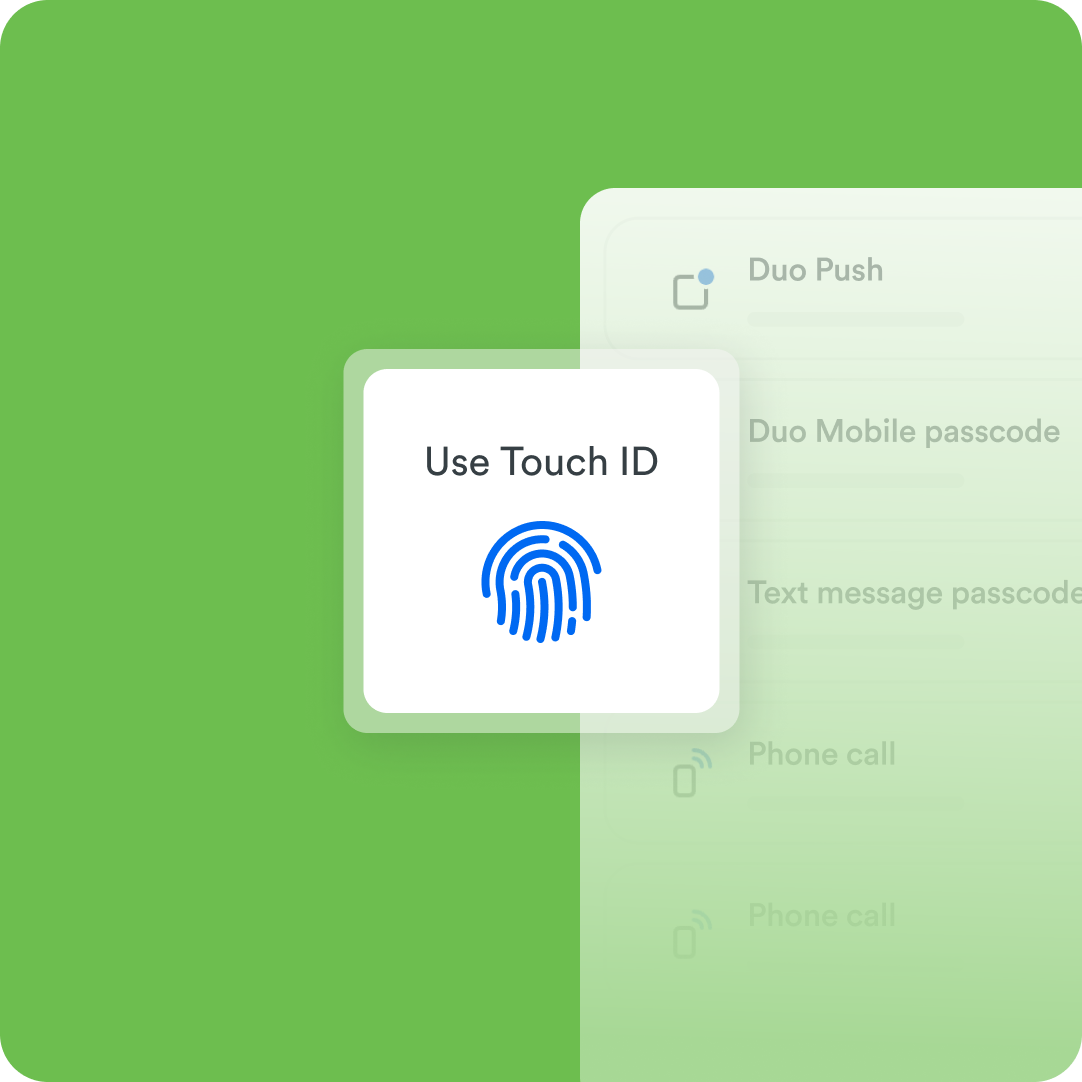
- Something you are: Biometric authentication types, such as fingerprints and facial recognition.
-
What are the 3 A's of authentication?