Defending against help desk attacks
The dissolution of the traditional security perimeter and the increase in identity-based attacks has come with its fair share of new risks for security practitioners to consider. From MFA bombing to adversary-in-the-middle (AITM) tactics, there are a variety of ways attackers are targeting weak spots in identity and access management (IAM) infrastructure and processes.
One that has been highlighted by CISA in many of its recent briefs is the Help Desk Attack. This technique involves an attacker contacting the help desk, often with relevant context regarding a high-profile employee, and then demanding a password and MFA factor reset. Typically, the attackers will use urgency and feigned authority to put fictional pressure on the help desk worker (ex: “I am boarding a flight with the CEO, and I need this now”). However, in some cases, attackers will pretend to be a naive worker who does not know how to use technology (ex: “I never understand this MFA stuff”).
The fundamental problem the attacker is exploiting in either case is identity verification. It is difficult to virtually verify a caller is who they say they are in a timely manner.
If the help desk worker complies, the attacker will have gained initial access and will typically reset the account credentials, both password and MFA devices, to be under their control. This first foothold is a dangerous step towards attackers gaining more malignant access and control of internal systems.
So, how should we think about preventing, detecting, and responding to help desk attacks?
Preventing help desk attacks
There are two key components to prevention:
Reduce the number of tickets associated with authentication and MFA addressed by the help desk.
Equip help desk workers with the proper training and tools to identify and prevent active attacks.
Reducing help desk tickets
Let’s begin with the first component: reducing the number of help desk tickets associated with authentication. This may seem like a round-about way to solve the problem of help desk attacks, but if there are fewer overall tickets associated with the authentication and MFA then help desk professionals have more time to consider each request. There is less urgency for any given ticket, and if an MFA-related request is rare then it will fall under something that should be given more scrutiny. In the end, we’re hoping for this type of reaction from the help desk: “Hey, this type of request isn’t common—perhaps I should double-check it.”
So, how do we reduce help desk tickets associated with MFA? At Duo, we have been working on this problem from three angles:
Invest in simple, intuitive design
Securely reduce the number of times users are asked to authenticate
Empower users to remediate security and IT issues themselves
There are many ways that Duo emphasizes these three pillars in our product, but there are a few examples that should be highlighted. Duo’s Universal Prompt provides a sleek UI that makes it easy for a user to understand their options and how to engage. The Universal Prompt also has customization functionality so organizations can implement their own branding and coloring to make it even easier for users to understand that they’re in the right place.
To securely reduce the number of times users are asked to authenticate, we introduced Duo Passport. Duo Passport securely passes trust between authentication scenarios so that if a user remains in a trusted state, they will not have to authenticate repeatedly.
Finally, to empower users, Duo has features like self-service password reset—instant restore—to get Duo running on new devices, and the device management portal so that users can attempt to solve problems on their own first before reaching out to the help desk.
Equipping the help desk with training & tools
To start, help desk workers should be trained on this type of attack. They should understand that even though asking for a password reset or MFA reset might be a common ask—it is always a big ask. They should also be trained to understand certain signals (e.g., like urgency, fear, and anger) that might indicate a user is trying to pressure them into resetting credentials.
“Even though asking for a password reset or MFA reset might be a common ask — it is always a big ask”
However, even if a help desk worker is trained perfectly, there may be an attacker that sounds legitimate! They may have done research on the potential target and know to sound typical. Most employees asking for help desk assistance probably sound confused and slightly annoyed. A clever attacker will probably take on this tone and attitude. An advanced attacker may utilize novel voice-changing technologies in what’s known as vishing.
Therefore, it is also important to equip the help desk with tools and mechanisms to try and verify the identity of the caller. Traditionally, Duo has done this with our help desk push functionality, which sends a Duo Push to a phone a user controls. However, an attacker will almost certainly claim they’ve lost their phone as well.
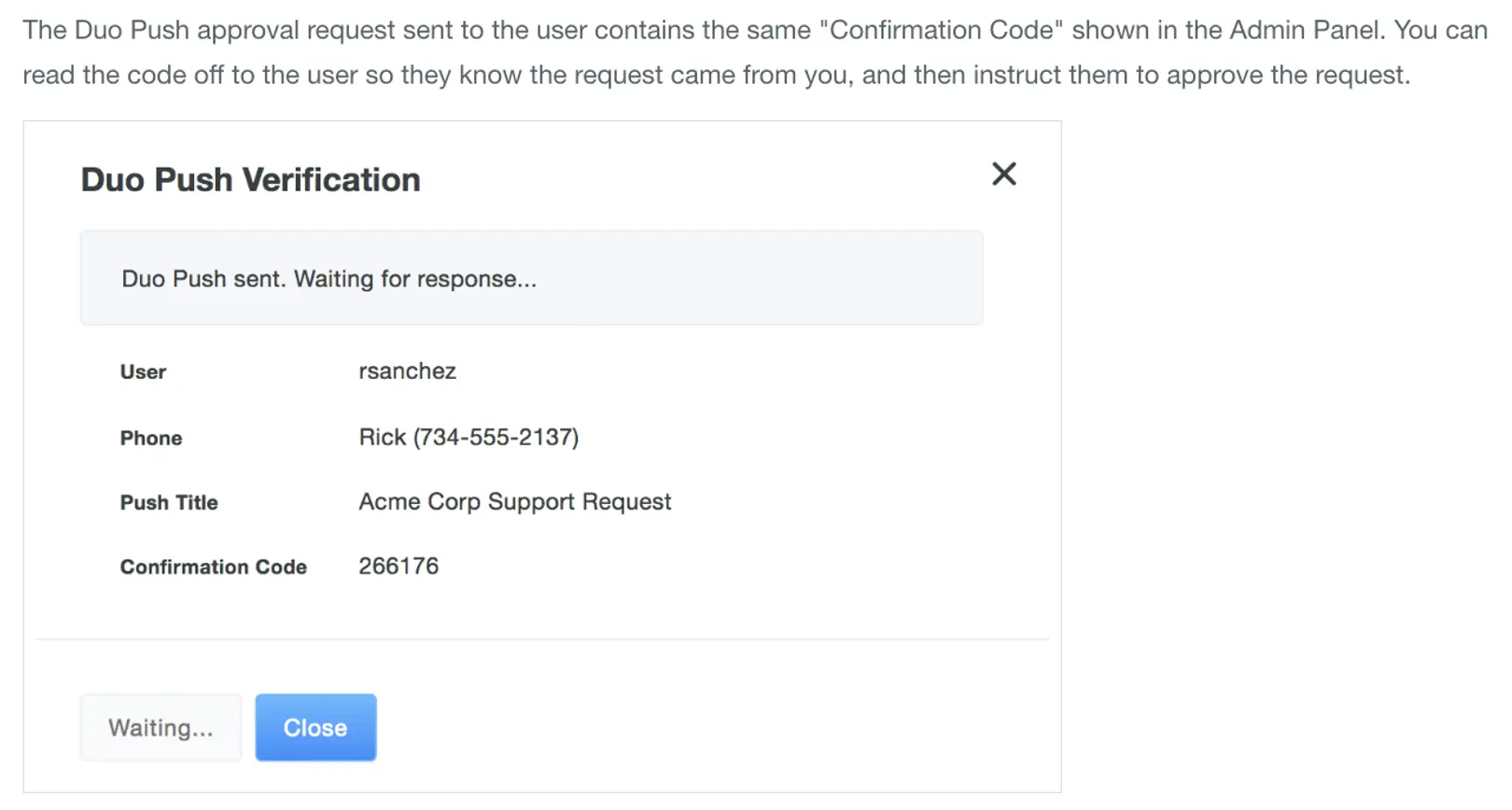
Therefore, we also recommend the help desk have other tools they can use to quickly validate a caller’s identity. One mechanism to do this with Duo is to use our Identity Intelligence functionality. With Identity Intelligence, a help desk employee can quickly see a user’s typical access activity (e.g., which applications they tend to log into, from where, and with which devices). This information can provide some helpful context in a reset credentials conversation—the help desk worker can now say things like:
"I see you have a second device registered for MFA. Can I send a verification there?"
"Name 3 applications you used yesterday."
"I see that you logged in from an unusual location a week ago. Where did you log in from?"
Identity Intelligence is just one way to verify user identity at the help desk. There are also more traditional mechanisms like knowledge-based authentication (KBA) questions that a user may have set. However, given that the attacker may have also stolen the KBA answers if they are easy to research or steal (e.g., mother’s maiden name), we suggest using data that is more dynamic and specific like the examples above.
Detecting & responding to help desk attacks
Now, even if help desk workers are trained well and equipped with proper verification tools, there still may be a case where an attacker slips through. In these instances, it’s important to detect the compromise as quickly as possible.
Detecting help desk attacks
Again, Identity Intelligence has some powerful features to equip security professionals with context regarding help desk attacks. The tool comes with dozens of alerts built to detect identity-based risk. In the case of help desk attacks, there are specific features and checks that may be most beneficial.
Feature: User Trust Level
Check: Users Sharing Authenticators
Check: Admin Role Assigned to User
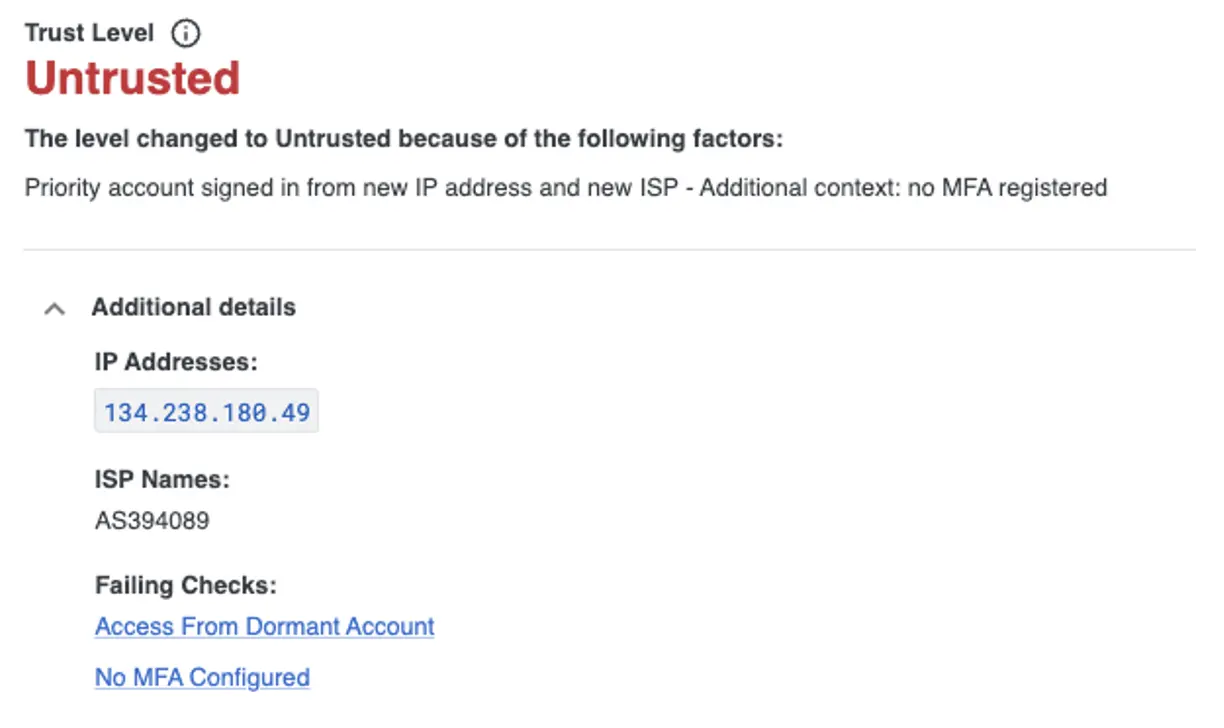
Identity Intelligence recently released a feature called a User Trust Level. This takes data on user role and activity to establish how trusted a user is at any given time. While it won’t explicitly detect a help desk attack, the User Trust Level is a helpful tool to see a subset of riskiest users in an environment at any given time. By reviewing and remediating the list of “Untrusted” users, security professionals will heavily improve their susceptibility to identity threats.
Identity Intelligence also has an alert for sharing authenticators. This is a helpful tool when detecting identity threats because often an attacker will target multiple users in an organization. If the attacker uses the same phone number/mobile device with each compromised user, Identity Intelligence will highlight this trend with the Users Sharing Authenticators check. Then, a security professional can remediate the compromised users.
Finally, attackers will almost always look to elevate the privileges of the accounts they now control. Therefore, the Admin Role Assigned to User is a great check for detecting privileges being added to an account. And, Admin Activity Anomaly checks are great for understanding if administrator accounts are acting unusually.
To be clear, detection is always a tricky game—but, by combining User Trust Level with the power of the checks that Identity Intelligence offers, security teams will have a powerful set of tools to identify a potential Help Desk compromise.
Remediating help desk attacks
Once compromised accounts and users have been detected, it’s important to establish a secure remediation process. To start, the accounts should be constrained or blocked from further access until the compromise is resolved. Identity Intelligence has a variety of response mechanisms available depending on the integrations set up. For example, a user can be locked out or quarantined via an action in Identity Intelligence. If the security team leverages a SIEM or SOAR for their response workflow, Identity Intelligence can seamlessly integrate there.
However, one thing to note here - there are many processes in place today that may give control to accounts right back to an attacker. Resetting passwords and MFA factors are only viable controls once trust has been accurately re-established with the account holders. We highly recommend putting in place a mechanism to re-verify users via a strong form of identity verification (ex: a phishing-resistant form of MFA or biometric authentication).
Hopefully, by combining strong mechanisms for prevention, detection, and remediation, organizations can attain a defense-in-depth against help desk attacks. If you’d like to learn more about establishing a robust identity security program from the ground up, check out our eBook Building an Identity Security Program.

