Five ways to defend against AI-powered-identity threats with Duo
What you'll learn
How AI poses new threats to identity
How you can detect and respond to attacks on identity faster
How Duo helps defenders use AI to fight AI
Successful cybersecurity always comes down to time: Can your tools and defenders find and respond to threats before they impact your business? With more threat actors using artificial intelligence (AI) to amplify attacks, CISOs and identity and access management (IAM) leaders need multi-layered, AI-led strategies to stop AI-led threats.
A new ebook from the Cisco Duo team, Identity Security in the Age of AI, looks at the impact of AI on the identity threat landscape and outlines a 5-step plan for defending against modern risks.
We share some highlights from that discussion here, starting with an update on risk.

AI's evolving threat to identity
AI equips adversaries to launch high-scale phishing campaigns and other identity-based attacks faster than ever. It introduces new attack techniques as well as modern twists on the classics:

LLMs make the phish even smarter
Powered by AI, phishing attacks have morphed from simple email scams to sophisticated multi-stage campaigns. AI equips threat actors to:
Automate and orchestrate rapid or multi-stage phishing campaigns
Create more convincing phishing campaigns
Target a broader audience
Increase the scale and sophistication of attacks
Resend exploits quickly and more frequently
Large language model (LLM) tools like ChatGPT and Microsoft Copilot help take phishing and social engineering to new heights. With a few simple prompts, AI tools like ChatGPT do the legwork of gathering information that can be used to impersonate or trick someone into revealing sensitive information, write convincing phishing emails with better spelling and grammar, and include deepfake videos impersonating trusted entities like CEOs, IT technicians, and vendors.

Modern campaigns combine email, social media, and mobile platforms to fool users and evade detection. LLMs help threat actors automate and scale campaigns making it harder for defenders to detect threats before they progress to lateral movement, account takeover (ATO), or outbound attacks against your supply chain.
Computer-Using Agents reimagine credential stuffing
Emerging agentic AI tools like Computer-Using Agents (CUAs) interact with technology just like humans do—which spells the start of a whole new ballgame. AI agents might be used to take over the grunt work from human hackers and perpetrate attacks faster by:
Scanning systems for vulnerabilities
Deploying malware
Impersonating humans in chatbots
Harvesting credentials by logging keystrokes or scraping auto-filled passwords from browsers
Copying and sneaking sensitive data out through email
Security experts predict CUAs can accelerate and scale tried-and-true credential-stuffing attacks by entering massive volumes of username/password combinations instantaneously. Widespread adoption of CUAs will necessitate new defensive strategies like developing and investing in more discerning ways of authenticating and authorizing AI agents themselves.
The news is not all bad
While the potential for threat actors to wield AI against enterprises seems limitless, the same holds true for cyber defenses. The new ebook from Duo AI experts goes on to outline a plan for swinging the AI pendulum back onto defenders’ side.
5 steps to defend agains AI-driven threats (with AI)
The pre-requisite: 100% visibility
As a foundational step, your IAM and security experts need 100% visibility into your identity security and attack surface so they can keep track of AI in your environment. Like the unauthorized use of cloud, using AI tools without going through the proper channels creates ‘shadow AI.’ Part of Cisco’s comprehensive AI Defense portfolio, the Cisco AI Access solution reduces risk from shadow AI by inspecting traffic to discover and manage applications, tools, and functionality with clear context around risk.

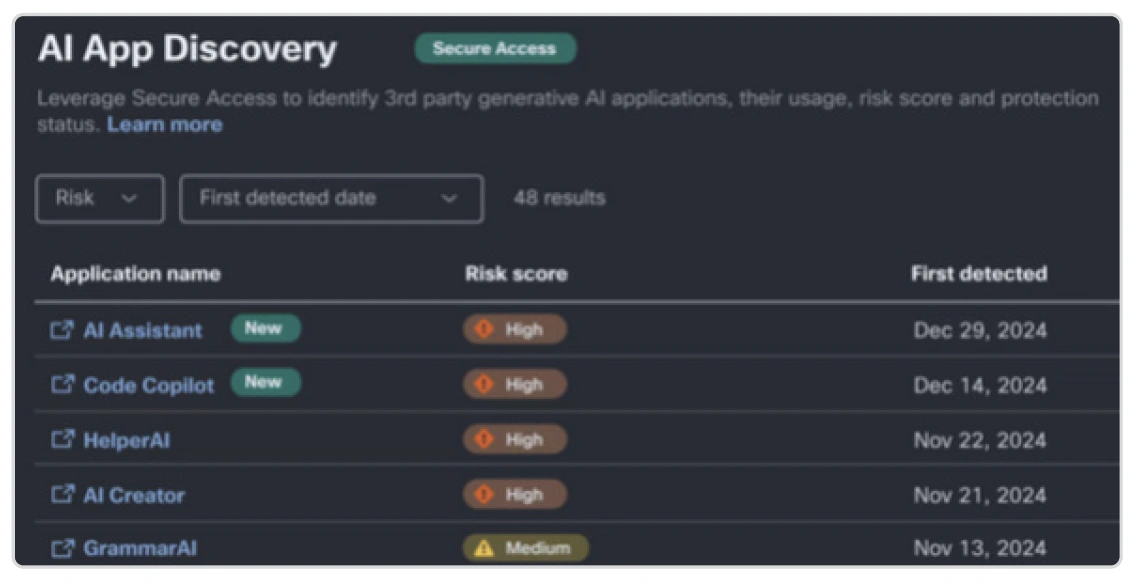
Once you establish visibility and define policies to regulate employees’ use of AI, start building up security at every critical attack vector, beginning with a proactive 5-step plan to bolster security for the age of AI:
Step 1: Secure the new perimeter
Zero trust security journeys start with safeguarding identity, now seen as the modern perimeter of security. IAM effectively becomes the foundation, the new front line of defense.
Build a strong identity security posture management (ISPM) practice
ISPM takes a proactive approach to validating your company’s identity security—versus identity itself (that job belongs to MFA)—to find vulnerabilities and enhance defenses against identity-based attacks. ISPM tools proactively analyze data and ensure organizations have proper authentication and security policies in place. ISPM improves identity data hygiene to ensure authentication strategies like MFA and authorization policies like least-privilege access do not get bypassed.

What's in a number?
Cisco Identity Intelligence assesses and generates an identity security score that reflects the maturity and strength of your organization’s identity security posture. Identity Intelligence also proposes ways to strengthen your defenses based on impact, priority, and risk. Learn more about ISPM.
Step 2: Build end-to-end phishing resistance
Regulators, cyber insurance providers, would-be partners and customers increasingly make decisions about compliance, premium increases, and whether to work with your company based on your security posture. Recognizing the importance of identity, many industry, federal, and state data privacy regulations now specify phishing-resistant MFA.
What they don’t specify is how to go about it. But thanks in part to AI, end-to-end phishing prevention is now well within reach. Cisco Duo adds powerful capabilities like:
Proximity verification that uses Bluetooth Low Energy (BLE) to confirm the authentication device and system being accessed are in the same place—great added protection against remote and third-party attacks.
Complete passwordless that takes away the bait phishing attacks try to capture. Passwordless MFA replaces vulnerable credentials using a flexible mix of tokens, push notifications and biometrics to validate identity, even during MFA enrollment, Help Desk calls, and fallback
Secure transfer of trust through Duo Passport with Session Theft Protection. Passport seamlessly completes multiple authentication sessions without asking users to log in repeatedly.

Step 3: Build and maintain device trust
With AI finding new ways to confuse recognition scanners, companies need policies and tools to establish trust in the devices being used to interact with resources. That means extending trust to devices as well as people, including personal and third-party endpoints your IT department doesn’t control.
Duo’s Device Trust capabilities assess and validate the health of any device to make sure it has the right security controls in place and working, up to date and configured correctly. Learn more about Device Trust.
Step 4: Update your Help Desk skills to spot AI scams
CISA recently highlighted the rise of attacks in which attackers contact an organization’s Help Desk requesting or demanding help to reset a password or MFA workflow. AI helps power these attacks with social engineering campaigns that enable threat actors to impersonate employees.
Companies can take several steps to prevent dedicated, responsive Help Desk technicians from complying with urgent requests to reset logins for adversaries impersonating executives and remote workers:
Monitor and update policies for resetting credentials
Train technicians to recognize Help Desk scams
Create contingency plans for verifying identity when users can't produce valid credentials or devices used to receive push notifications or complete MFA
Cisco Identity Intelligence helps IT build on-the-fly contingency plans by generating reliable data that can be used to verify identity—for example, which applications users accessed the day before and from where. Read more about preventing Help Desk attacks.
In addition to Identity Intelligence, the introduction of Duo Identity Verification powered by Persona helps organizations avoid social engineering threats and eliminate trade-offs between strong security and responsive service. A verifying user gets redirected to Persona and asked to provide a snapshot of their government-issued ID along with a selfie photograph. Persona conducts a variety of verification checks such as matching the selfie to the photo in the government-issued ID and performing liveness detection on the selfie to detect AI-powered deepfakes.
Step 5: detect and respond to AI-driven threats faster
Identity Threat Detection & Response (ITDR) systems protect your identity management infrastructure by verifying admin credentials and detecting and blocking identity-based threats like phishing and account takeover. Cisco Identity Intelligence supports ITDR by correlating identity data from various sources and calculating trust level scores—complete with explanations—for individual users based on their activity. Identity Intelligence even recommends response actions that can be implemented manually or automated within existing workflows, like configuring a system to send an alert to SOC analysts upon detecting anomalies.
Use AI to resolve identity issues faster
There’s no such thing as a “simple” login. Incorporating AI into your IAM practices can help security teams get to the bottom of login issues quickly and accurately. Cisco’s AI Assistant lets admins see the full trail of events in context. The tool facilitates investigation by bringing together logs, knowledge base articles and product documentation resources in one place, and one single conversation. Learn more about AI Assistant.
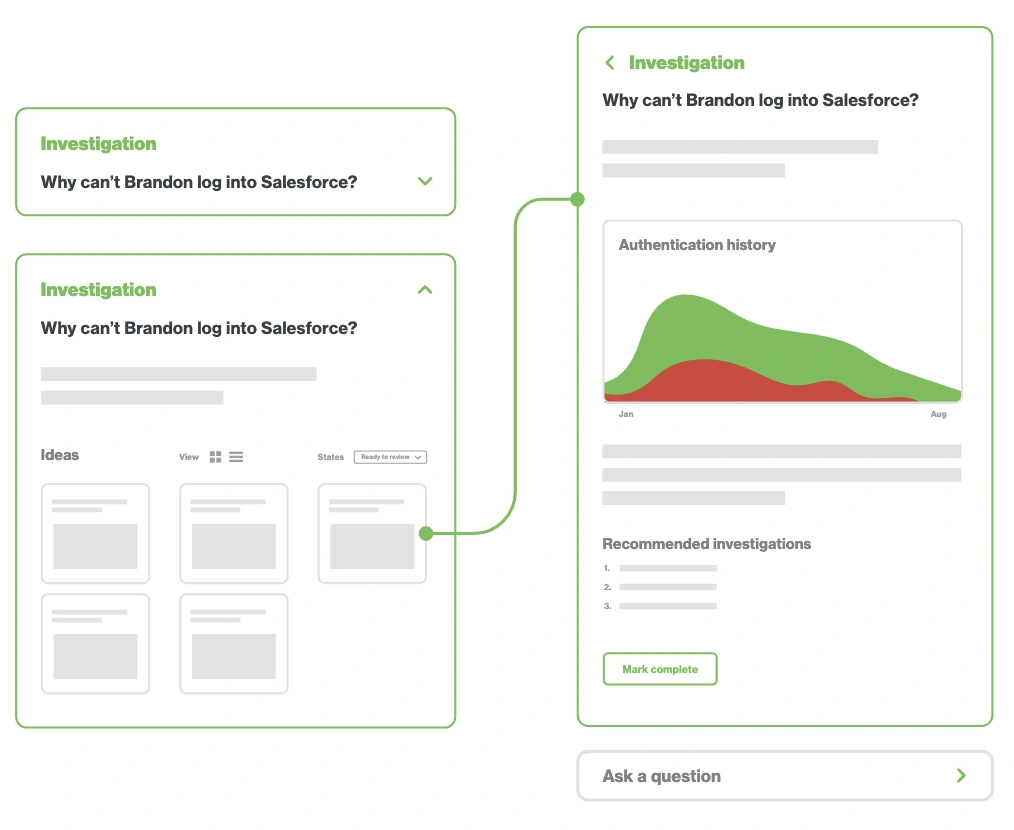
Cisco's proprietary machine learning models (ML) provide superior threat detection, safeguarding against data exposure and protecting against novel attack vectors. With full visibility and control over the traffic on your network, Duo helps identity security leaders uncover and block malicious use of AI without impeding productivity.
Duo secures identity with—and against—innovations in AI
Flexible strategies, and the right solutions, equip organizations to fight AI with AI by:
Adapting continuously as AI tools evolve and pose new threats
Keeping security and user experience (UX) in balance with security-first IAM
Enabling end-to-end phishing resistance and identity threat detection and automated response at machine speed and scale
Read the ebook now
Download the full ebook to learn more about securing and fully leveraging your investments in AI.
If you’d like to go further, get in touch with a Duo identity security expert for a targeted assessment of your organization’s potential risk from AI and strategies tailored to keep time on your side.

