How to secure the holidays & prep your 2026 IAM strategy
The holiday season is an intense time for retail, travel, hospitality, and other industries—intense good, and intense bad. While seasonal demand drives sharp increase in business activity, organizations must also onboard temporary employees, contractors, and third parties at speed, dramatically expanding who needs access to internal systems.
The risk of suffering an outage or data breach due to phishing, social engineering, and other cyberattack tactics invariably go up, along with a new growing area of concern: external users, including season staff, contractors, vendors, and partners often require fast access to internal systems and fall outside standard employee identity controls.
Experts predict a rise in third-party risk
Along with heightened exposure to the usual suspects—fraud, ransomware, and remote attacks on IT workers—a new report predicts a rise in third-party risk this shopping season. According to the 2025 Holiday Season Cyber Threat Trends Report, members of the Retail & Hospitality Information Sharing and Analysis Center (RH-ISAC) saw notable spikes in third-party data extortion and anticipate a continued trend of account takeover and business email compromise attempts.

Read the full blog: Avoiding third-party risk with Duo for identity management
So, what should you get your security & IT teams this year?
With more threats sprouting up across your vendor, partner and customer ecosystems, adding third-party defense strategies to your shopping list makes sense this year. Read on for a few powerful “Pro Tips” that might help do the trick—we’re sharing them early, before the “holi-daze” hits full stride.
Pro Tip 1: Give the gift of strong IAM, beyond basic MFA
In addition to fraud, last year’s most common threats included phishing, ransomware, and credential harvesting—all techniques that can be countered by strengthening identity security.
Since about 80% of breaches still involve humans and often credentials, the first step in avoiding risk should be making sure anyone trying to connect and access your company resources is who they say they are. Apply strong IAM consistently to both internal and external users, since both introduce identity risk during the holiday period.
Avoid growing threats by extending your strong access controls to validate more third-parties as thoroughly, and as easily as you do your internal workforce. Multi-factor authentication (MFA) is a crucial component of identity and access management (IAM). Strong MFA helps manage the risk that comes with allowing suppliers, contractors, consultants, and customers to access your company’s systems and data.
Last year, we explored security tips to combat holiday phishing. Traditional forms of MFA like SMS, callback, and hardware tokens are not only clunky to use and disruptive to users, but also no longer sufficient in defending against evolving phishing attacks. Duo balances security with user experience, covering the widest range of MFA options to fit organization needs. To defend against MFA-targeting attacks, deploy modern risk-based authentication (RBA) and token-free, phishing-resistant Proximity Verification—a reliable method of authenticating independent contractors, service technicians, and other third parties accessing sensitive systems onsite.
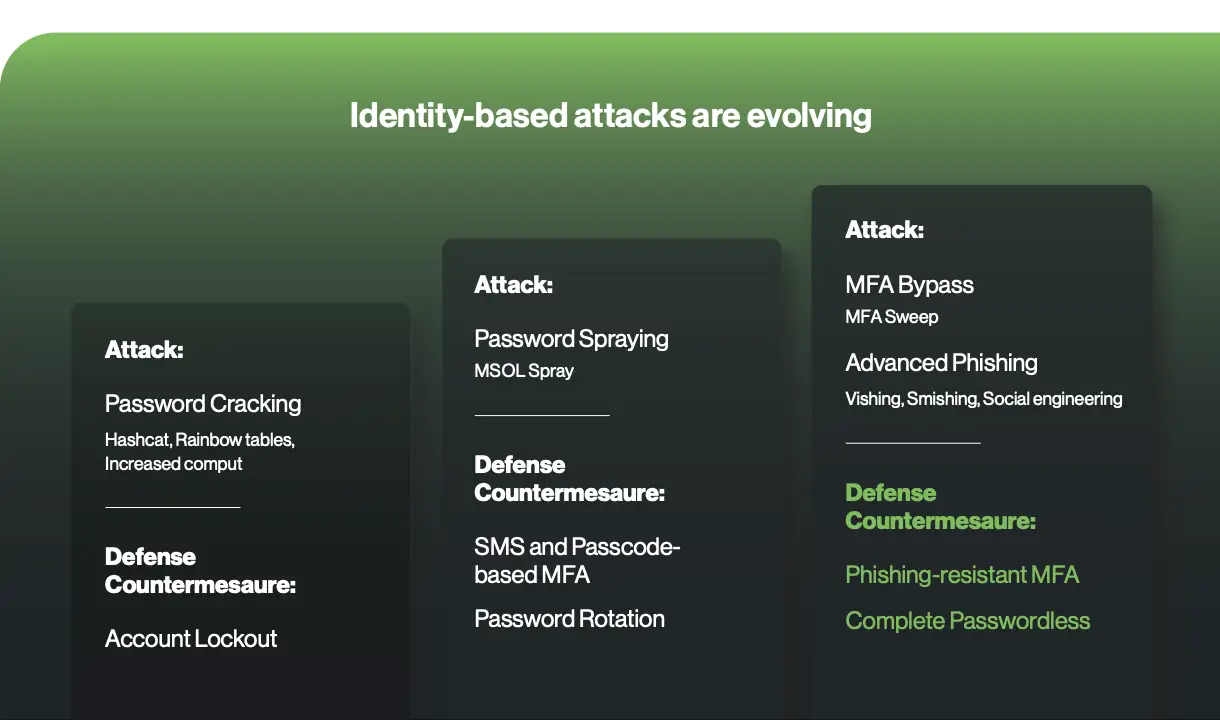
Evolution of identity-based attacks, from Restoring Trust in Identity: Duo’s Guide to Security-First IAM
One size definitely won’t fit all
Secure-by-default, Duo makes it super easy to verify external identities and block unauthorized access. Flexible user directory capabilities help IT streamline access by both internal and external identities and manage them separately or together.
The recent addition of Duo Directory lets admins set up, segment, and manage third parties in alternate directories in the same way—but not the same place—that they do employee data. A safe and simple place to store third-party identities, Duo’s cloud-based directory can broker authentication across multiple Identity Providers. After all, protecting your company against external risk protects your entire supply chain; it’s the gift that keeps on giving!
Pro Tip 2: Verify trust in devices
There’s no getting around it: everyone multi-tasks around the holidays. That means employees and external users may be doing their holiday shopping—creating accounts, resetting credentials, sharing links, and entering payment data—all from some of the same devices they use to access your network. While shopping itself doesn’t change the need for device trust, it does increase the chances that those devices are exposed to risky links or downloads, raising the likelihood of compromise and directly impacting the security of your environment.
Strong identity security validates trust in devices as well as users themselves. This includes workforce and third-party devices; both must meet your security bar before accessing internal systems. MFA alone won’t keep everybody safe, particularly when your IT team can't see or control their devices. That’s why Duo’s strong identity security solution validates trust in devices themselves as well as users.
Duo Device Trust delivers strong security for third-party access without requiring people to add new hardware or mobile device management (MDM). Duo automatically runs health checks on external endpoints—managed or unmanaged BYOD devices—and spots red flags like outdated software that could easily be exploited. With Duo’s Trusted Endpoints, easily stand up a policy that denies access from any unknown device.
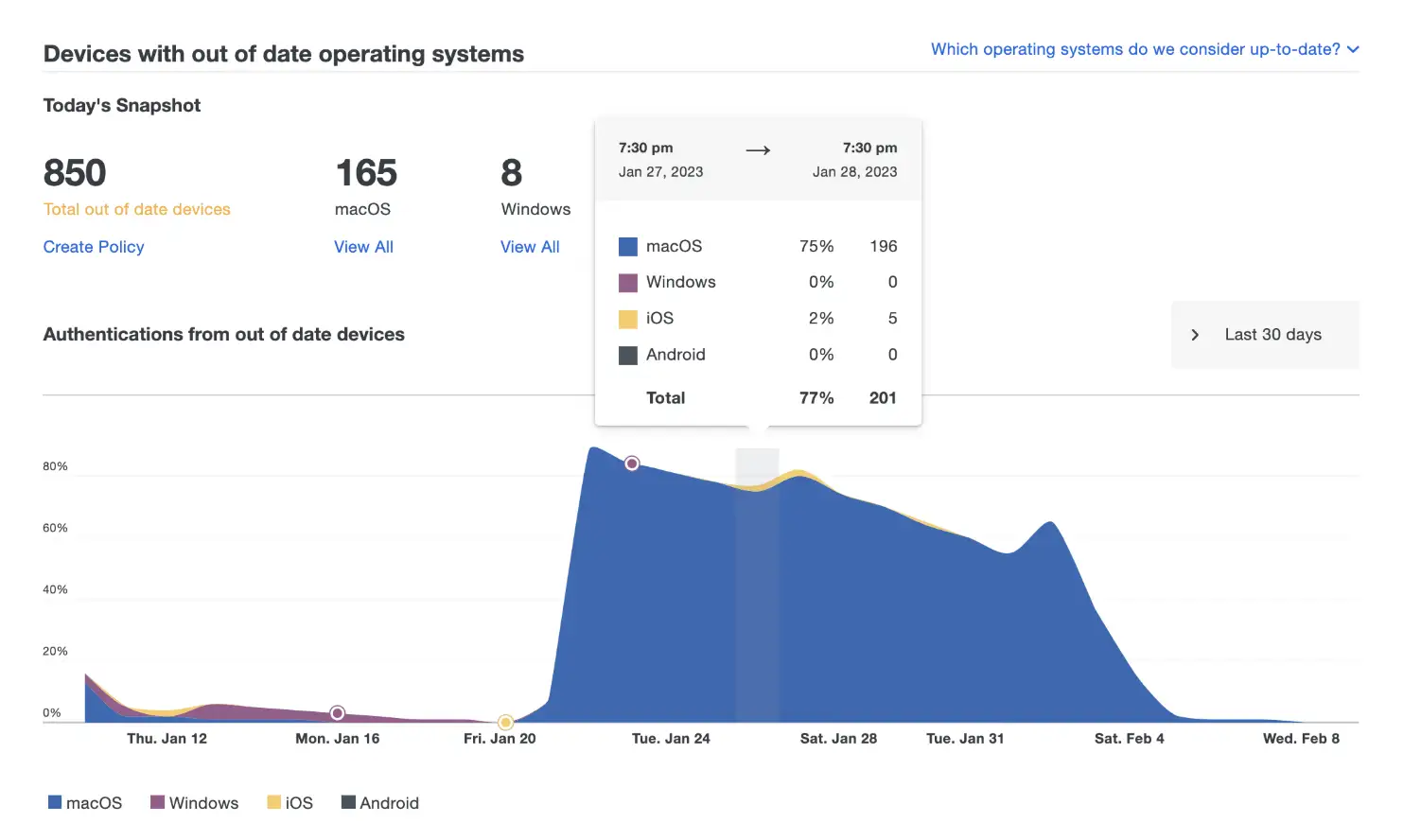
See device health at-a-glance in the Duo Admin panel with Device Insights
Real-time device telemetry gives admins the same visibility they use to manage internal device health, including detection of jailbroken devices and what OS version the endpoint has running. This way, automatically block access until users bring their devices into compliance with company policies.
Pro Tip 3: Turn AI into your security & IT team’s helper
According to RH-ISAC, the 2025 Holiday Period will likely be defined by an unprecedented scale of automation. With generative AI traffic predicted to grow 520% in the 10 days leading up to Thanksgiving, the lines between good bot, bad bot and human will be significantly blurred.
The same AI traffic surge targeting consumers will also overwhelm workforce identity systems. Higher access volumes and increasing number of employees becoming phishing risks, especially as threat actors on Santa’s naughty list use AI to scale their attacks. This is where Duo’s AI Assistant can help by unifying logs, and user context and device posture in one place to accelerate decisions rather than looking through various pages to find an answer. An admin can simply ask the AI Assistant, “Show me all devices this employee used to access corporate resources this week and tell me if it’s safe to grant him access from his Android device.”
As much as we try to separate personal and corporate activities, employees often use the same devices for personal holiday shopping and work. Securing identity at the point of login becomes critical to maintaining resilience during this time.
Holiday Bonus Tip: Give the gift of passwordless
Sometimes less is more. Getting rid of passwords is a gift that makes life easier for users and IT while making everyone, and your organization, safer.
Even at work, we may have a wish list, like just being able to login faster without the headache of typing and remembering all the different passwords. Do your employees and external users a favor this year by reducing this friction and give them the gift of passwordless.
Duo enables end-to-end passwordless identity security, a foundational element of end-to-end phishing resistance and one less thing for everyone to worry about as they flip from app to app. A bonus for sure, but one every Grinch in your ecosystem can appreciate.
Download the free playbook
Get the free guide to modern, security-first identity and access management and get ahead of your identity strategy in the new year. Download the Guide to Restoring Trust in Identity.
With that we’d like to wish everyone a safe and joyous holiday rush and a healthy, prosperous 2026. See you then!

