Duo Administration - Device Insight
Last updated:
Track the mobile 2FA devices and computer endpoints used through your organization to access Duo-protected applications and approve two-factor authentication requests by navigating to Devices → Device Insight → Device Insight in the Duo Admin Panel.
In the Duo Admin Panel, the "Endpoints" and "Laptops & Desktops" pages list the systems used to access resources using the web-based Duo Universal Prompt or traditional Duo Prompt. The "Phones" page shows the phones and other authenticators used to approve 2FA requests from Duo.
Authentications from applications that do not show a web-based Duo prompt, like Duo Authentication for Windows Logon, do not populate the list of endpoints or show up on the "Laptops & Desktops" page.
Device Insight Overview
Duo tracks versions of operating systems, browsers, and plugins like Flash and Java on the devices accessing your protected resources and provides a summary view on the Device Insight overview page. You can easily see how many access devices are out of date throughout your organization.
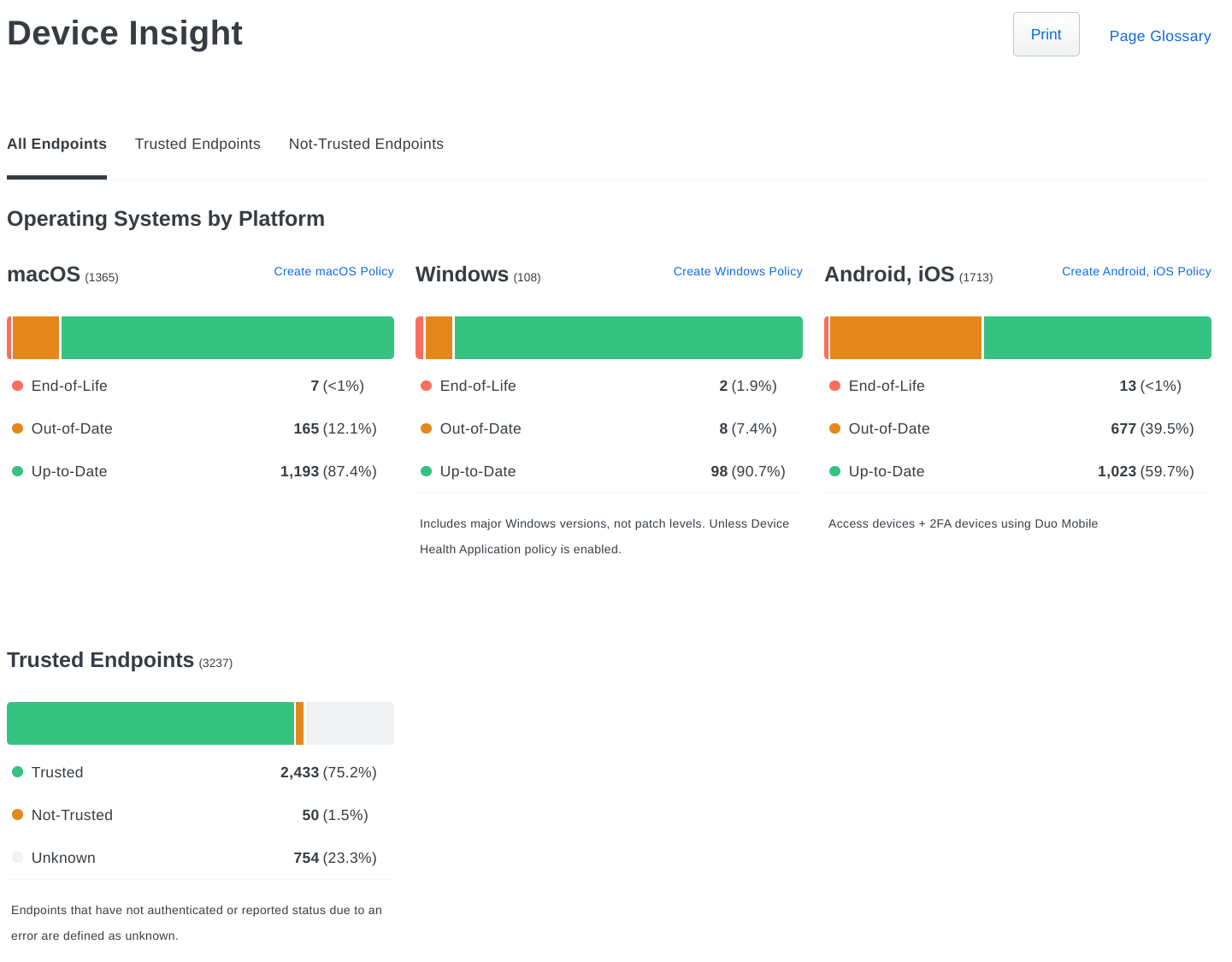
Duo Premier, Advantage, and Essentials plan customers can see summary information for trusted endpoints and can filter the view by "Trusted" and "Not-Trusted" endpoints. Details for access endpoints can also be viewed in the Authentication Log report. Duo Premier and Advantage customers can click through to access the Endpoints page for more granular filtering.
We provide visualizations of authentications from devices with out-of-date operating systems and browsers over time. Move your cursor over any time period in the graph to see the number of authentications from out-of-date devices as of that day. You can change the graph's scale from 7 to 30 or 90 days.
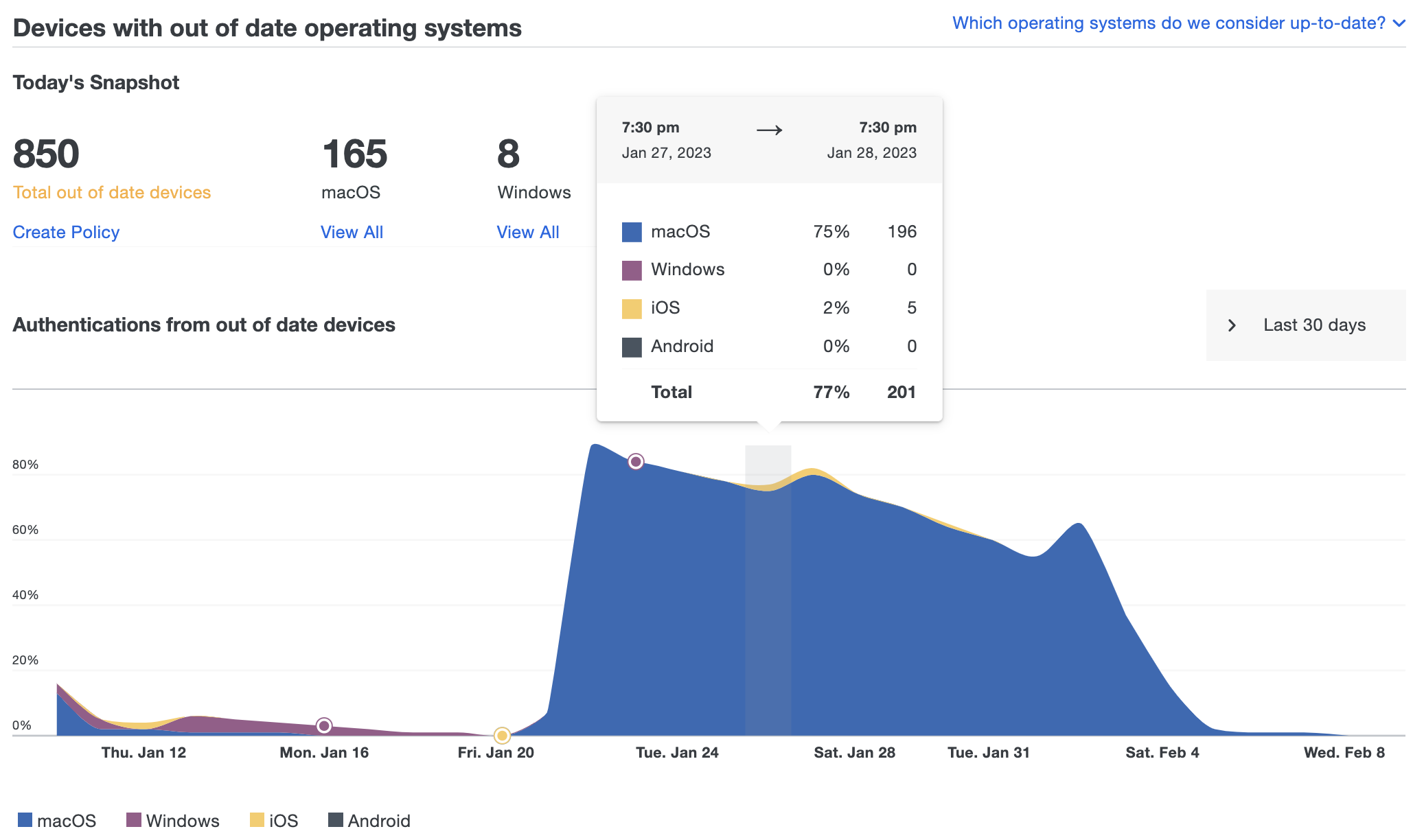
Clicking the Create Policy link under any of the outdated device counts takes you to the Policies page, where you can choose a policy to edit and warn users about outdated software and prevent access to your applications from devices with older software. See our Policy documentation for more information about implementing device access policies.
Mobile Devices
Duo plan required: Duo Advantage or Duo Premier
The Mobile Devices page breaks out smartphone and tablet 2FA devices by operating system and version and shows the status of various security features on iOS and Android platforms.
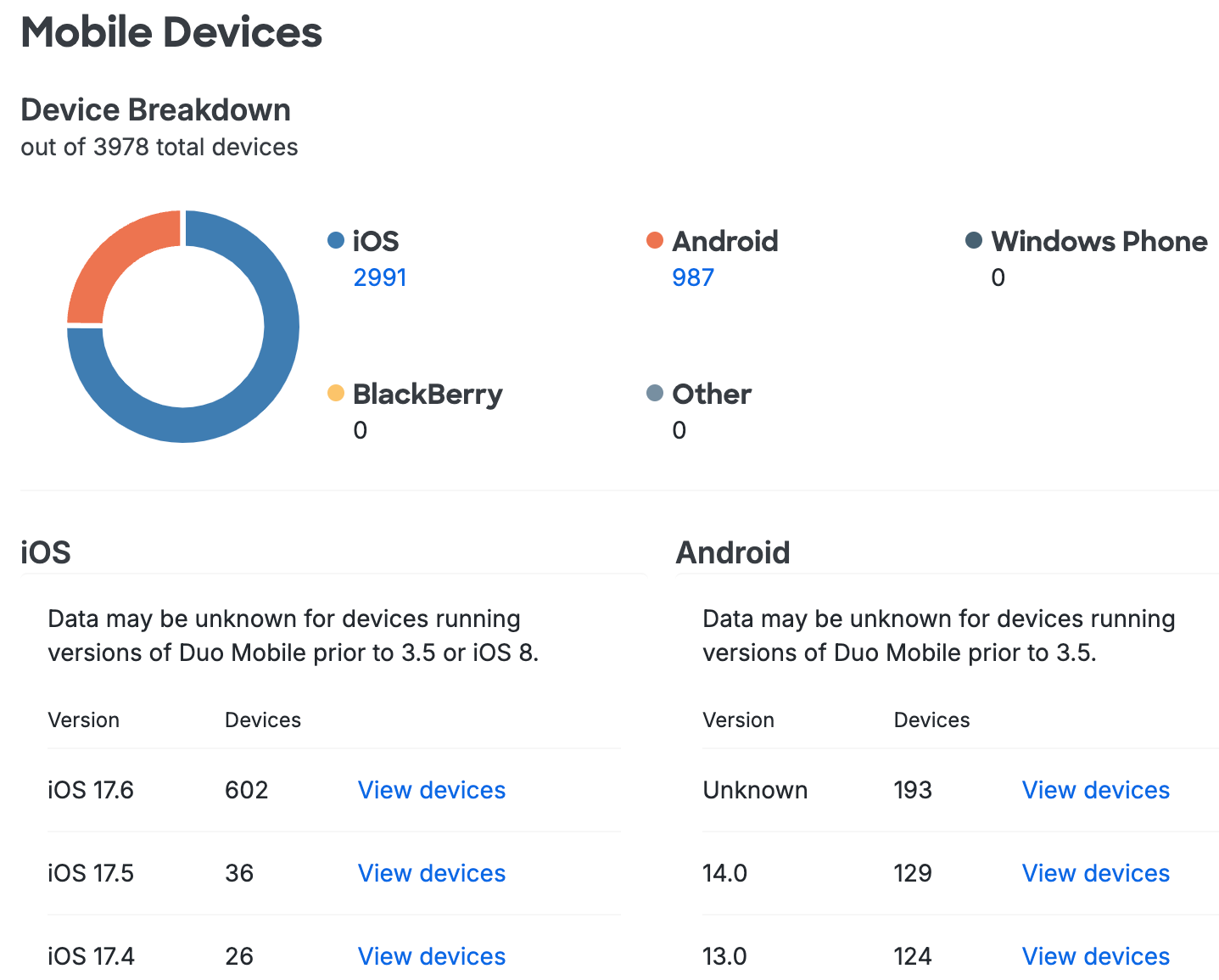
The Device Breakdown summarizes the various mobile device types your users have enrolled in Duo, while the rest of the page displays more information about Apple and Android devices in two columns: iOS and Android.
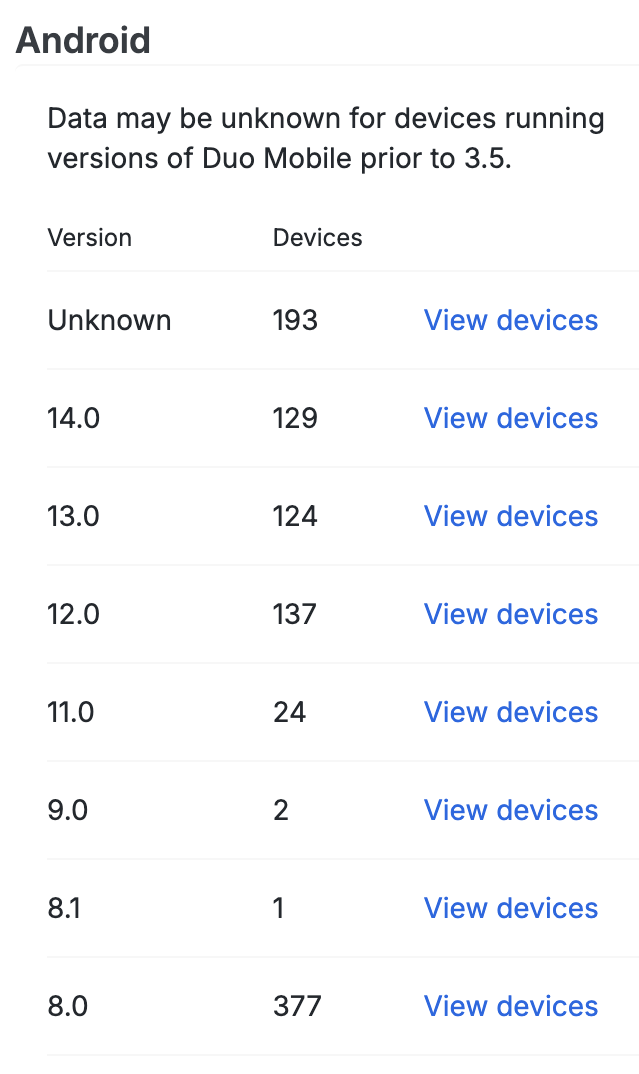
OS Version
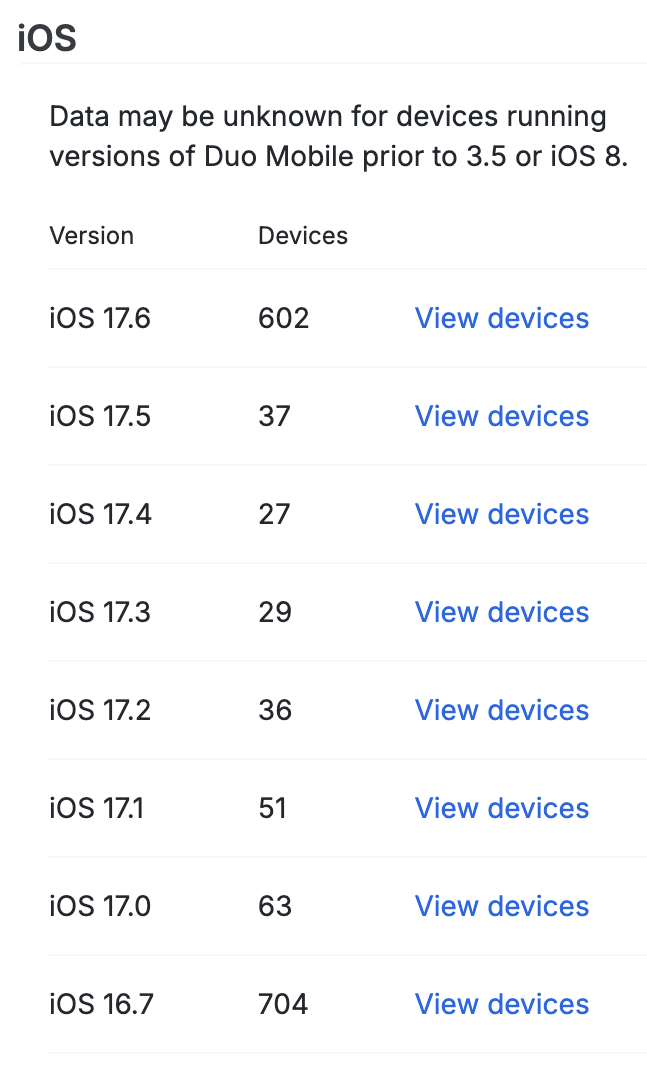
The first table in each column shows the Android and iOS device operating system versions in use across your organization.
Clicking the View devices link in any row of the table takes you to a filtered list of devices running that OS version.
| iOS Versions | Android Versions |
 |
 |
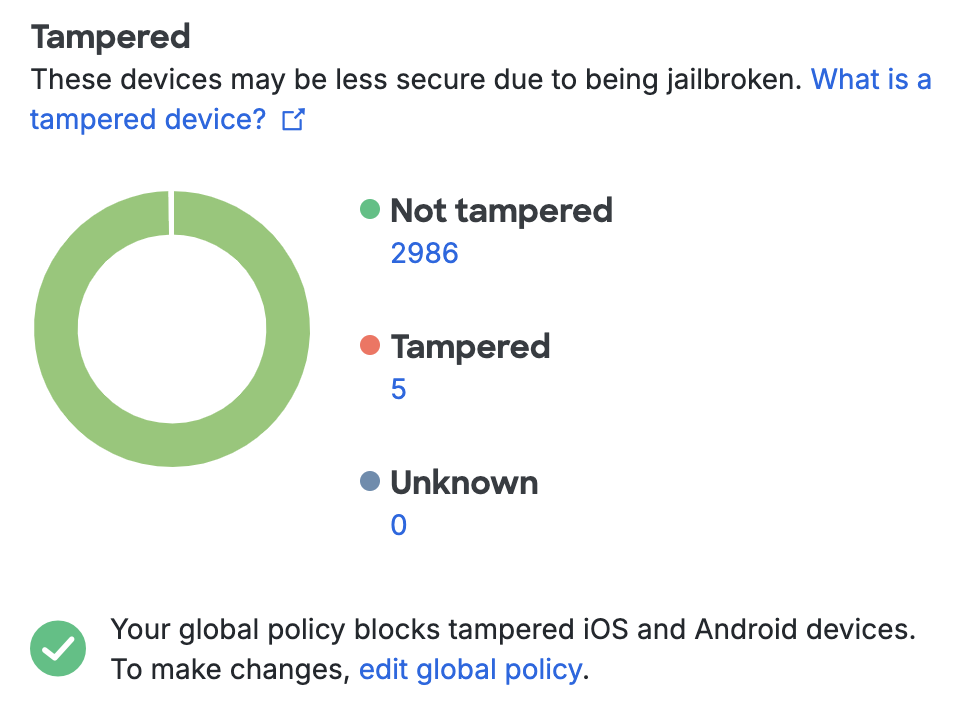
Tampered Devices
The iOS and Android Tampered Devices counts show how many devices have elevated privileges enabled on the operating system or fail other safety checks. Tampered-with devices may be considered a security risk because they are more vulnerable to exploit by malware and malicious apps. You can use the Tampered Devices Policy Setting to restrict authentication from tampered-with devices.
| iOS Tampered Devices Summary | Android Tampered Devices Summary |
 |
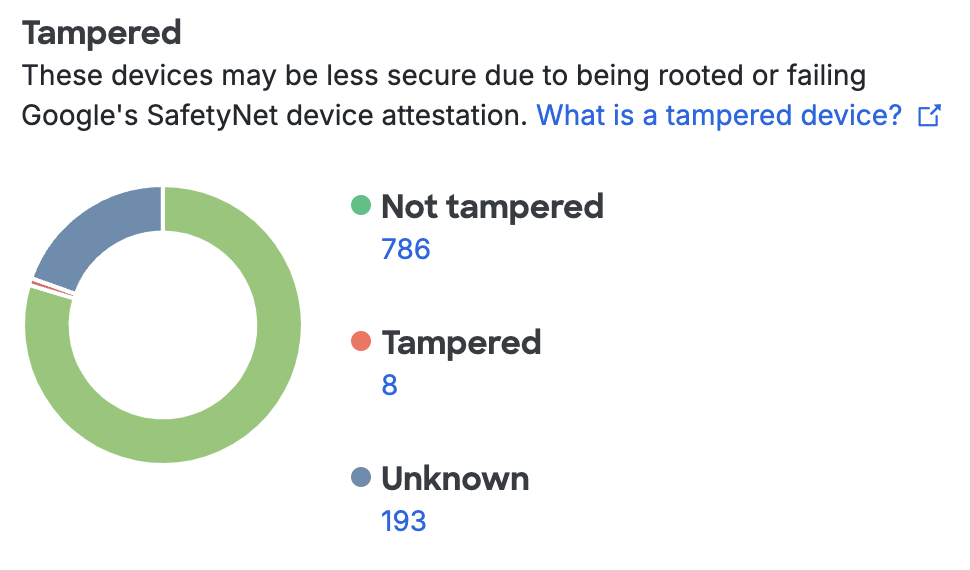 |
Clicking any of the device counts takes you to a filtered list of tampered devices.
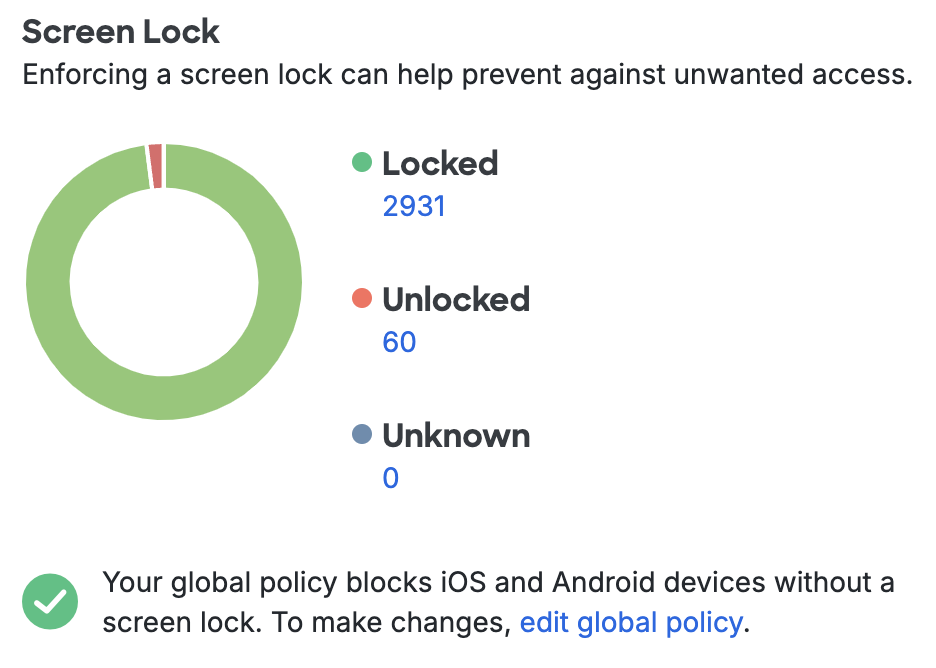
Screen Lock
Enabling a lock screen that requires a PIN or password elevates the security of a mobile device. The Screen Lock items for iOS and Android show counts of devices with and without lock screen protection. Change the Screen Lock Policy Setting to require lock protection from devices used for Duo authentication.
| iOS Screen Lock Summary | Android Screen Lock Summary |
 |
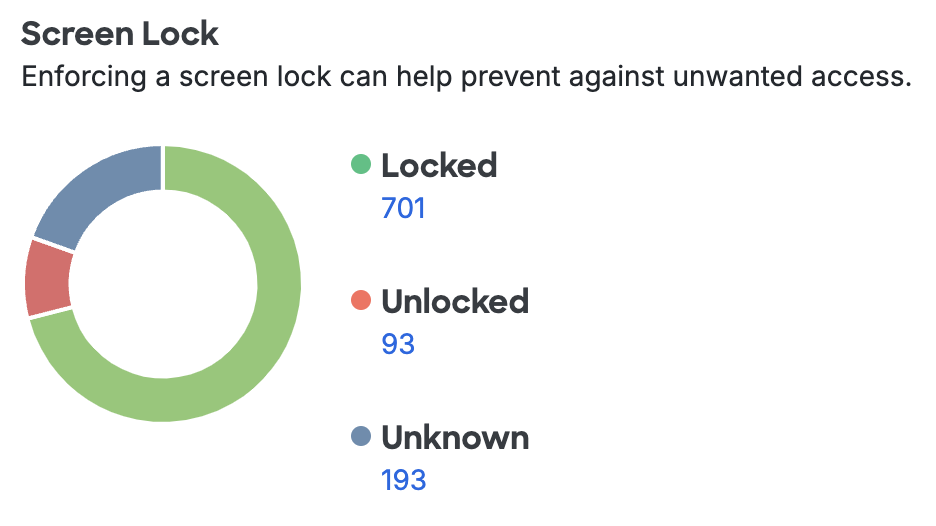 |
Clicking any of the device counts takes you to a filtered list of devices with or without screen lock enabled.
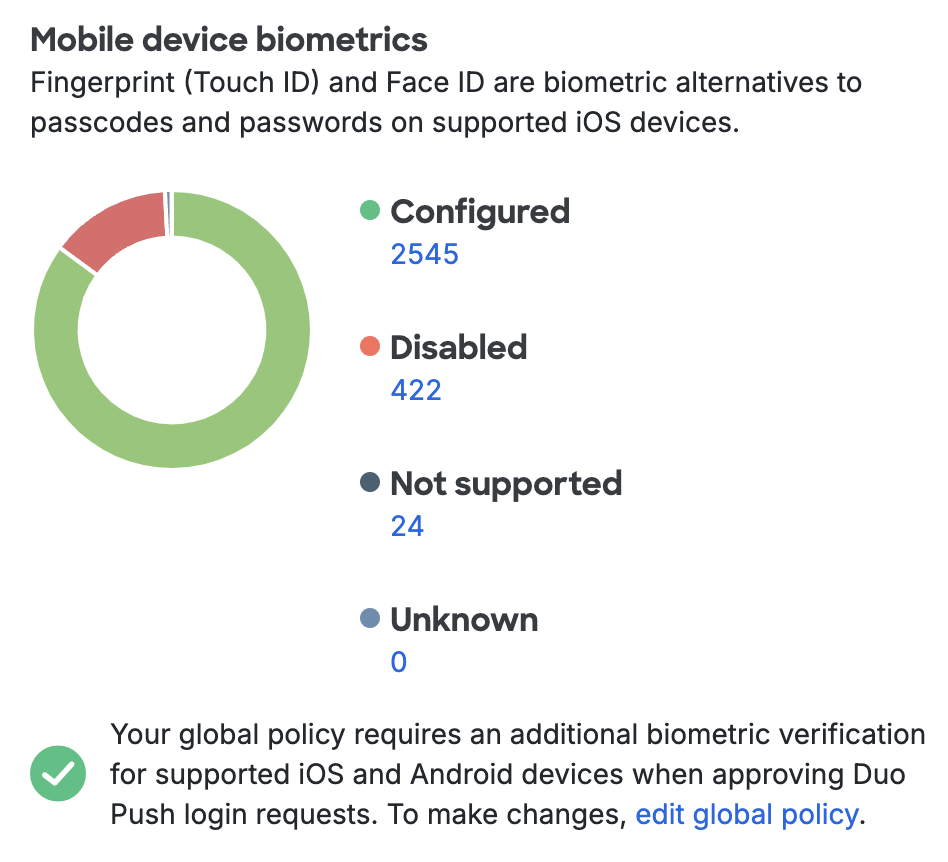
Mobile Device Biometrics
Apple's devices with Touch ID and Face ID and newer Android devices with fingerprint scanners can be used to unlock the device. See how many devices in your organization have Touch ID, Face ID, or fingerprint authentication enabled in the Mobile Device Biometrics count. You can require biometric verification for Duo Mobile login approvals with the Mobile Device Biometrics Setting.
| iOS Device Biometrics Summary | Android Device Biometrics Summary |
 |
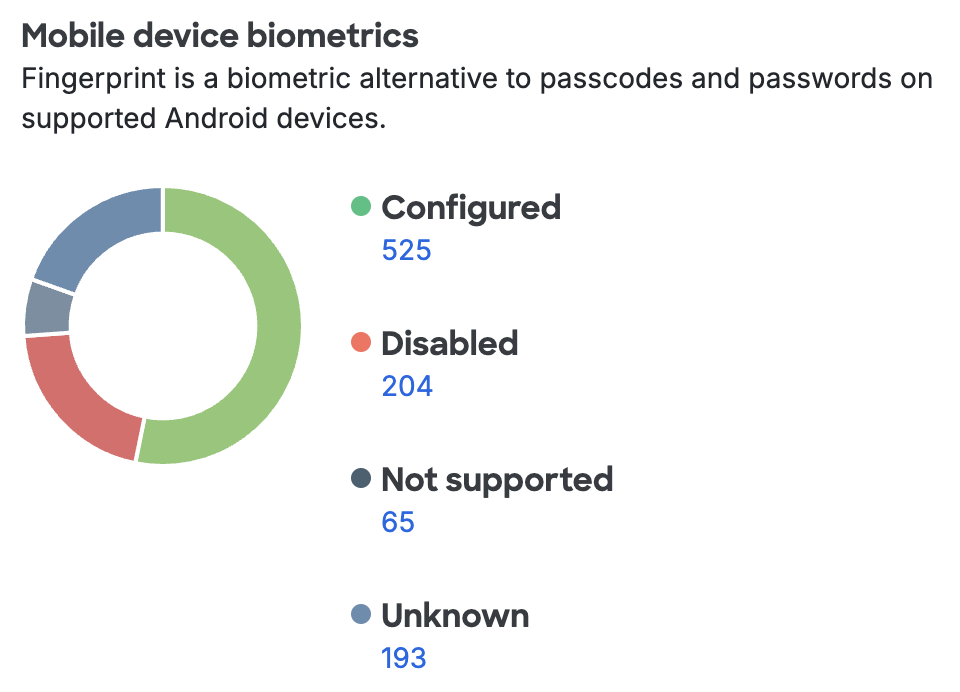 |
Clicking any of the device counts takes you to a filtered list of devices with and without biometric verification enabled.
Disk Encryption
Android devices typically do not ship with full-disk encryption. A password or PIN must be entered at boot to decrypt and access the data when a device’s disk is encrypted. The Disk Encryption count shows how many Android devices have full-disk encryption. Restrict Duo authentication to only devices with encryption enabled with the Disk Encryption Policy Setting.
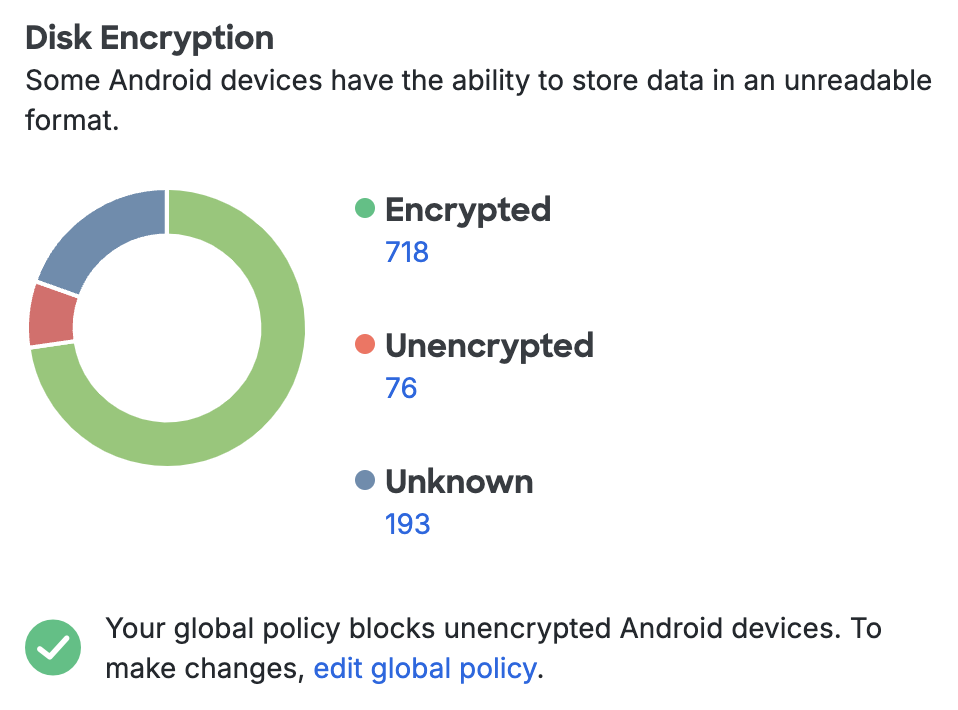
Clicking any of the device counts takes you to a filtered list of Android devices with or without encryption. In order for a device's status to show as encrypted the device must require PIN entry at startup.
Disk encryption status does not apply to iOS devices. Apple phones and tablets ship with an encrypted file-system.
2FA Device Details
The Devices → Phones list in the Admin Panel flags less optimal security properties ("Screen unlocked", "Tampered", etc.) in addition to displaying summary information like platform, Duo Mobile app version, and attached user or users. Click any of the column headers to sort on that property.
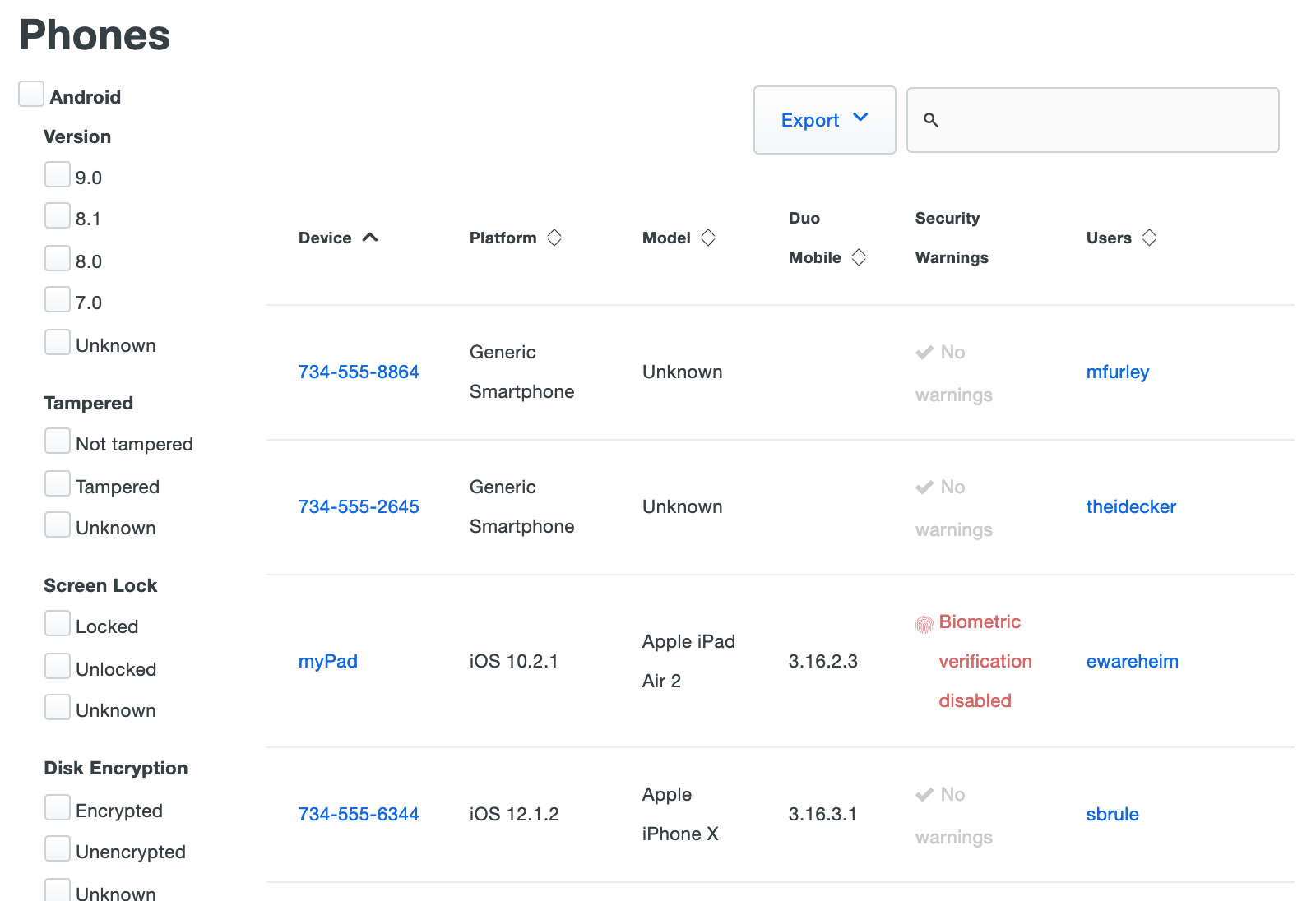
You can filter the Phones list by Android or iOS operating system version, as well as by security property status. For example, checking the boxes next to "iOS", "8", and "Locked" on the left side of the 2FA Devices > Phones page then displays all Apple phones and tablets running iOS version 8.x with Screen Lock enabled.
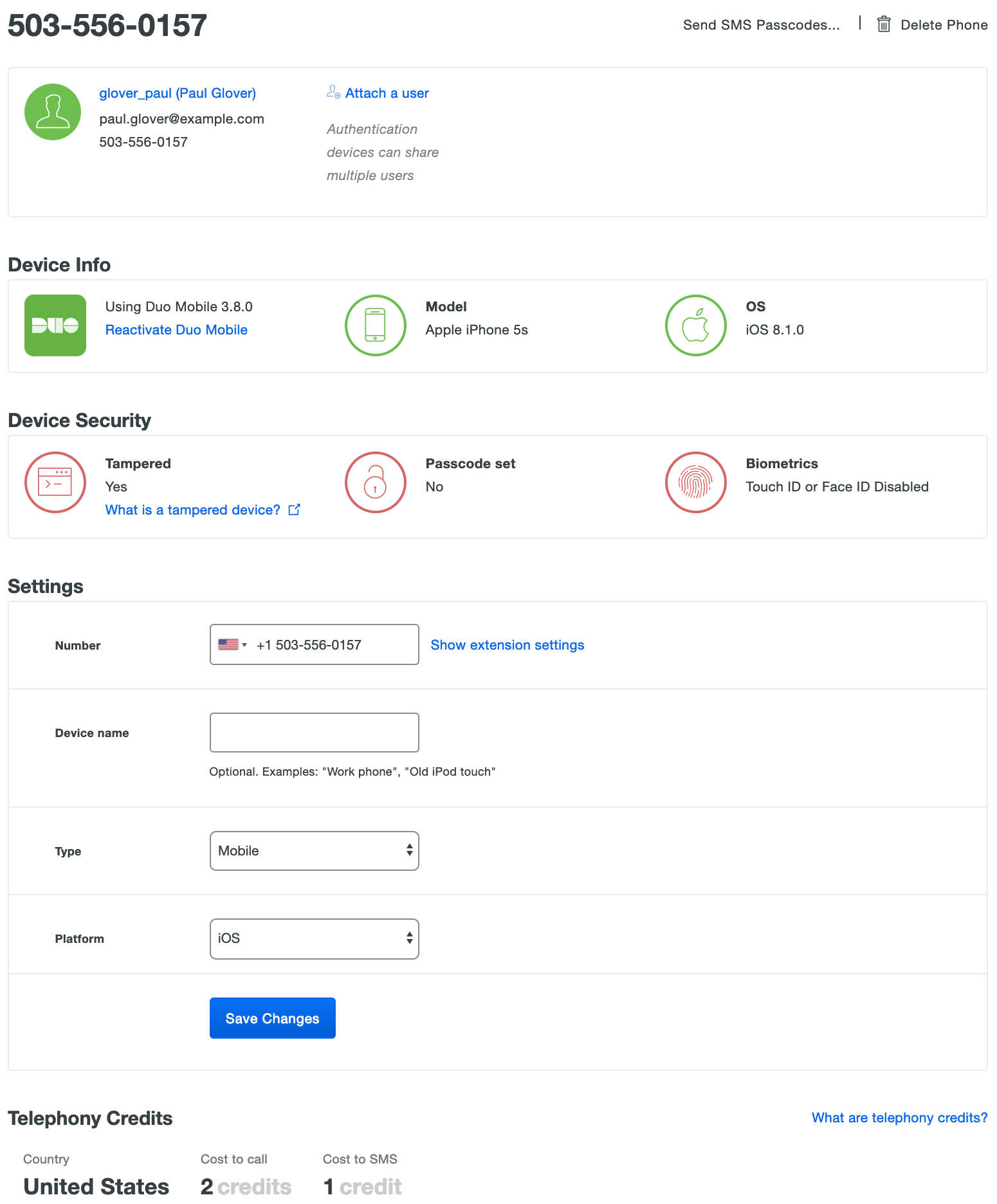
Viewing the details of a phone or tablet device shows the status of various security properties e.g. Screen Lock, TouchID, etc.
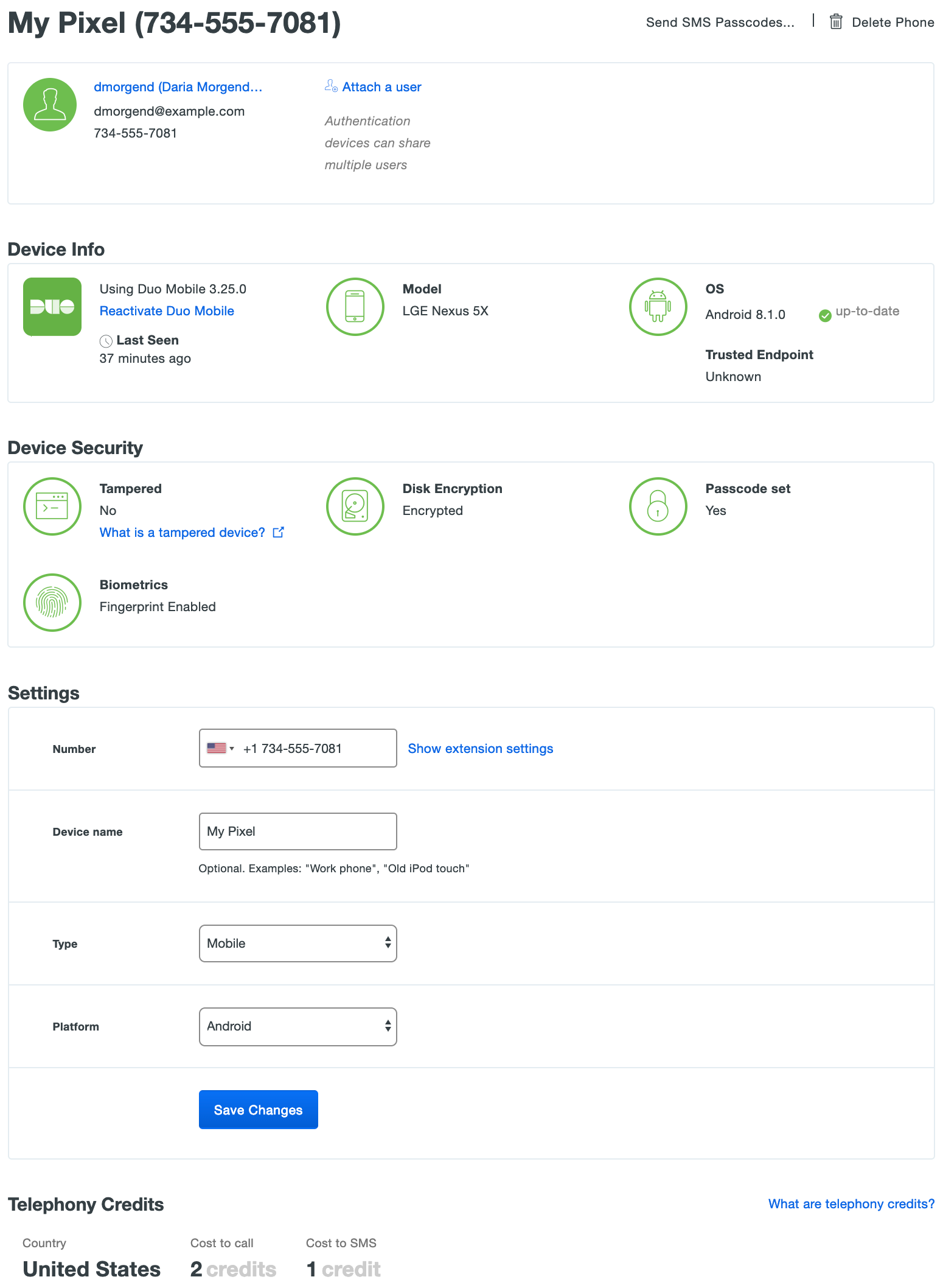
When a device is secure, the various details are green. A setting shown in red indicates a less secure status.
Laptops & Desktops
Duo plan required: Duo Advantage or Duo Premier
Laptops & Desktops shows which operating systems and browsers were used to authenticate to your organization's web-based applications through the Duo Universal Prompt or traditional Duo Prompt over the last seven days. Duo also checks to see if Flash and Java browser plugins are present.
Clicking the View Devices link in any row of the Operating Systems, Browsers, or Plugins tables takes you to the Endpoints page, with the view filtered to show access by the selected OS, browser, or plugin.
Client Platforms
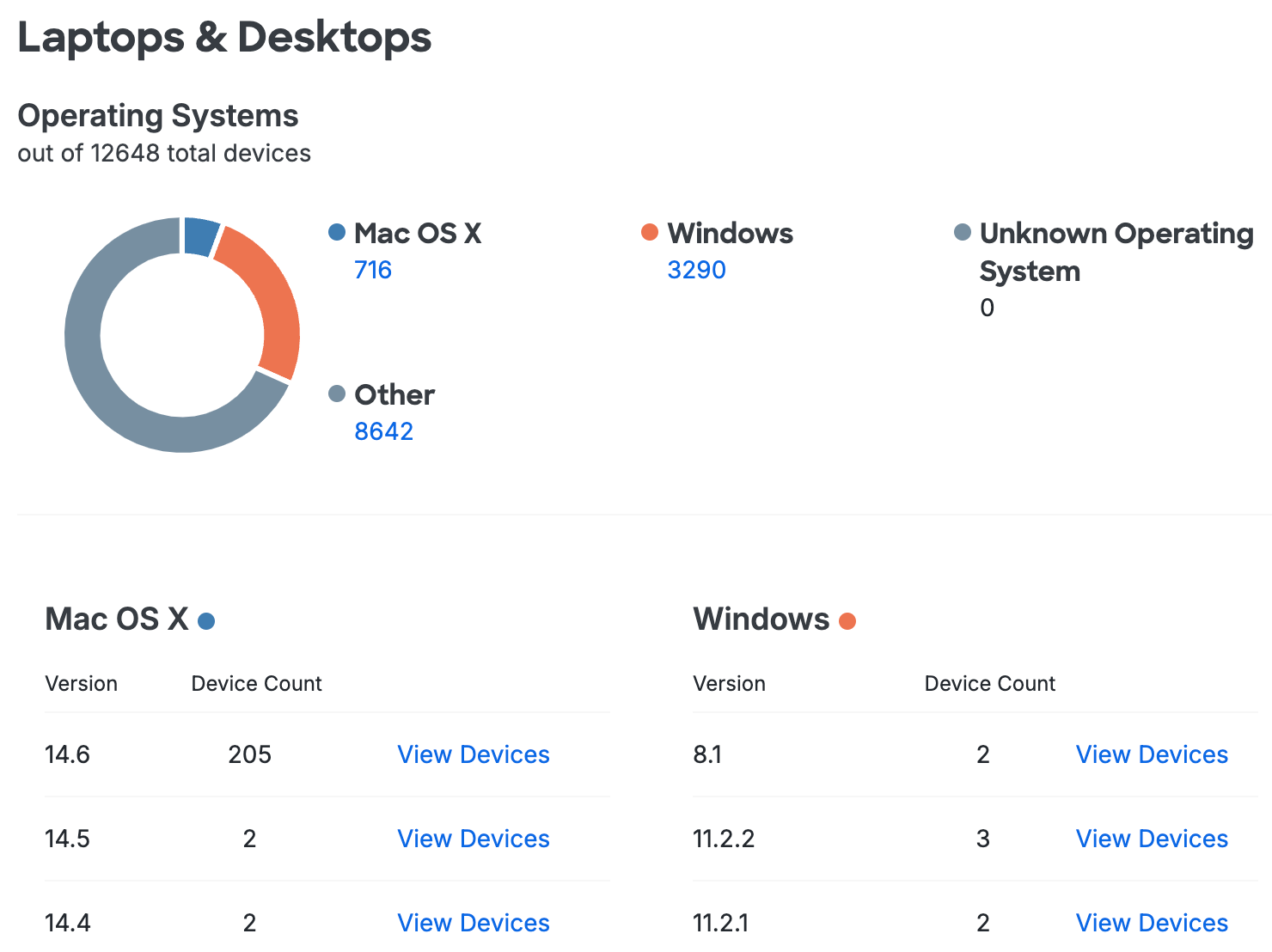
The Operating Systems chart summarizes access by operating system. Totals for the most popular operating systems (Mac OS X and Windows) are shown, while less commonly used endpoint operating systems (like Chrome OS and Linux) roll up to the "Other" category.
The tables under the chart detail Mac OS X and Windows platforms recently used when accessing Duo protected resources, also showing device counts for each OS version.
Client Browsers
The Browsers chart breaks down recent access by browser vendor.
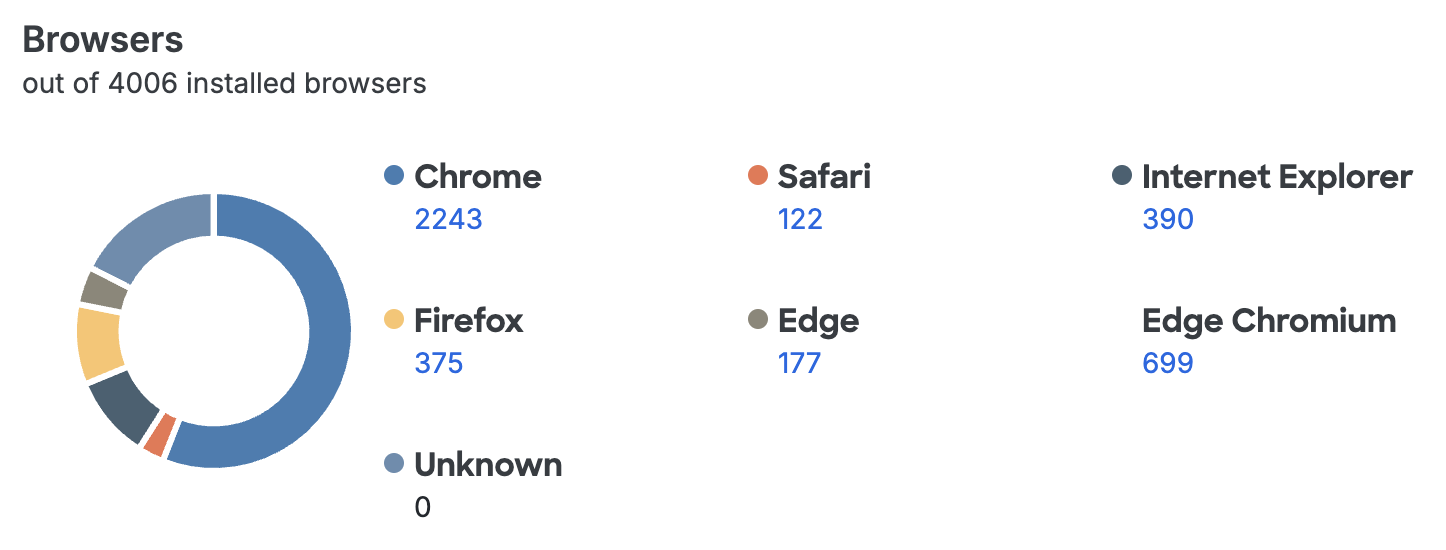
The tables below present statistics for Chrome, Safari, Internet Explorer (IE), Edge, and Firefox versions recently used for Duo authentication. Duo shows you how many of your users initiated access from devices using an out of date version of that browser, and also informs you just how far behind the current browser version those vulnerable endpoints are. Here's example data for the Chrome browser:
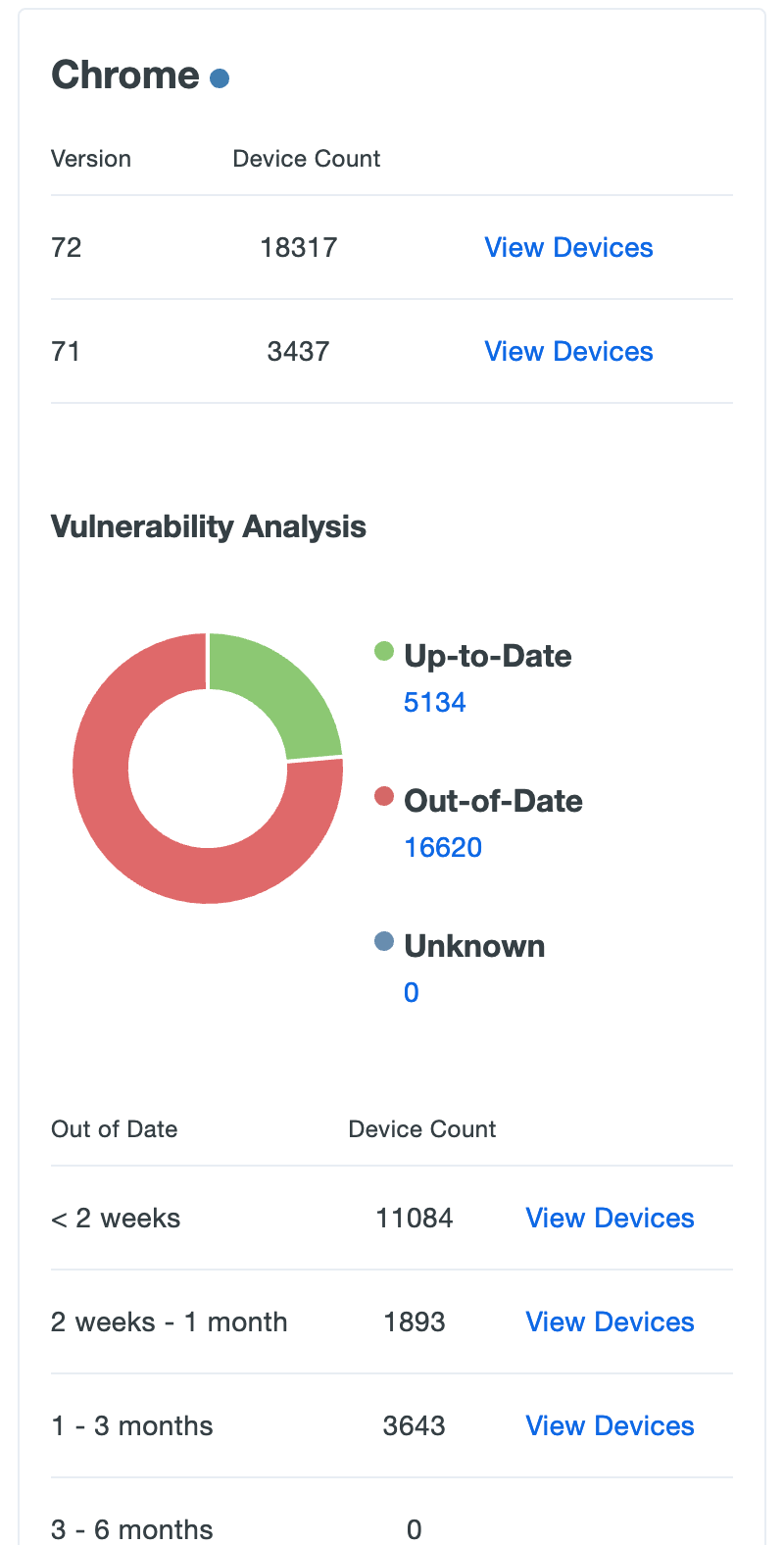
Click the View Devices link on any of the listed plugin versions to go to a filtered view of the Endpoints page showing which endpoints users authenticated from using that browser version.
Browser Plugins
Help your users navigate the web securely by keeping third-party browser add-ons up to date. Duo captures Java and Flash plugin information whenever your users log in to a Duo protected browser-based application using our inline enrollment or activation prompts.
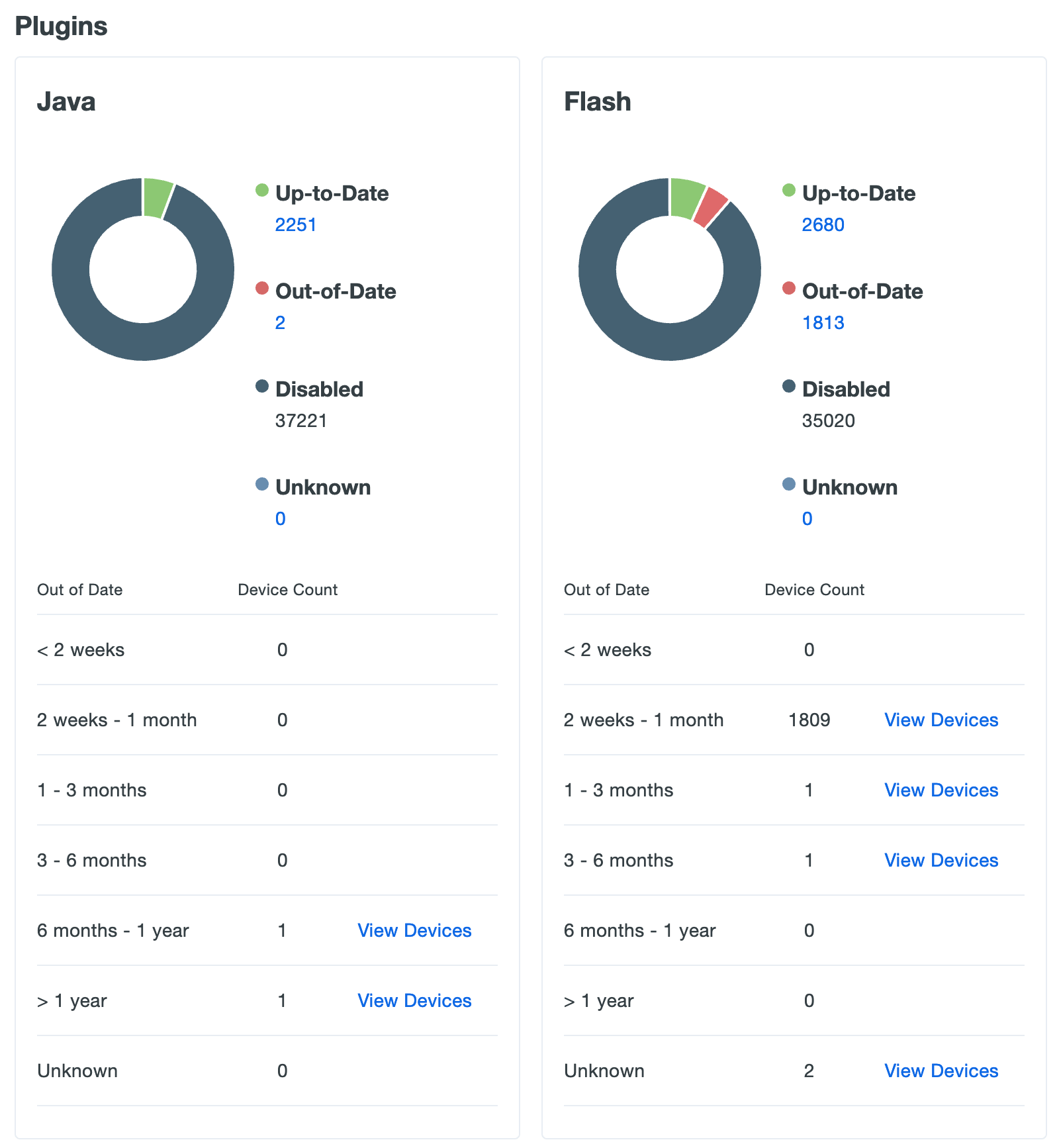
The Java chart and table shows how many of your users have Oracle's Java plugin enabled in the browsers they use to authenticate to Duo, and which versions in use are out of date and vulnerable. The Flash chart and table shows the same information about Adobe's Flash plugin.
Click the View Devices link on any of the listed plugin versions to go to a filtered view of the Endpoints page showing which users authenticated from an endpoint with that specific plugin enabled.
Access Control
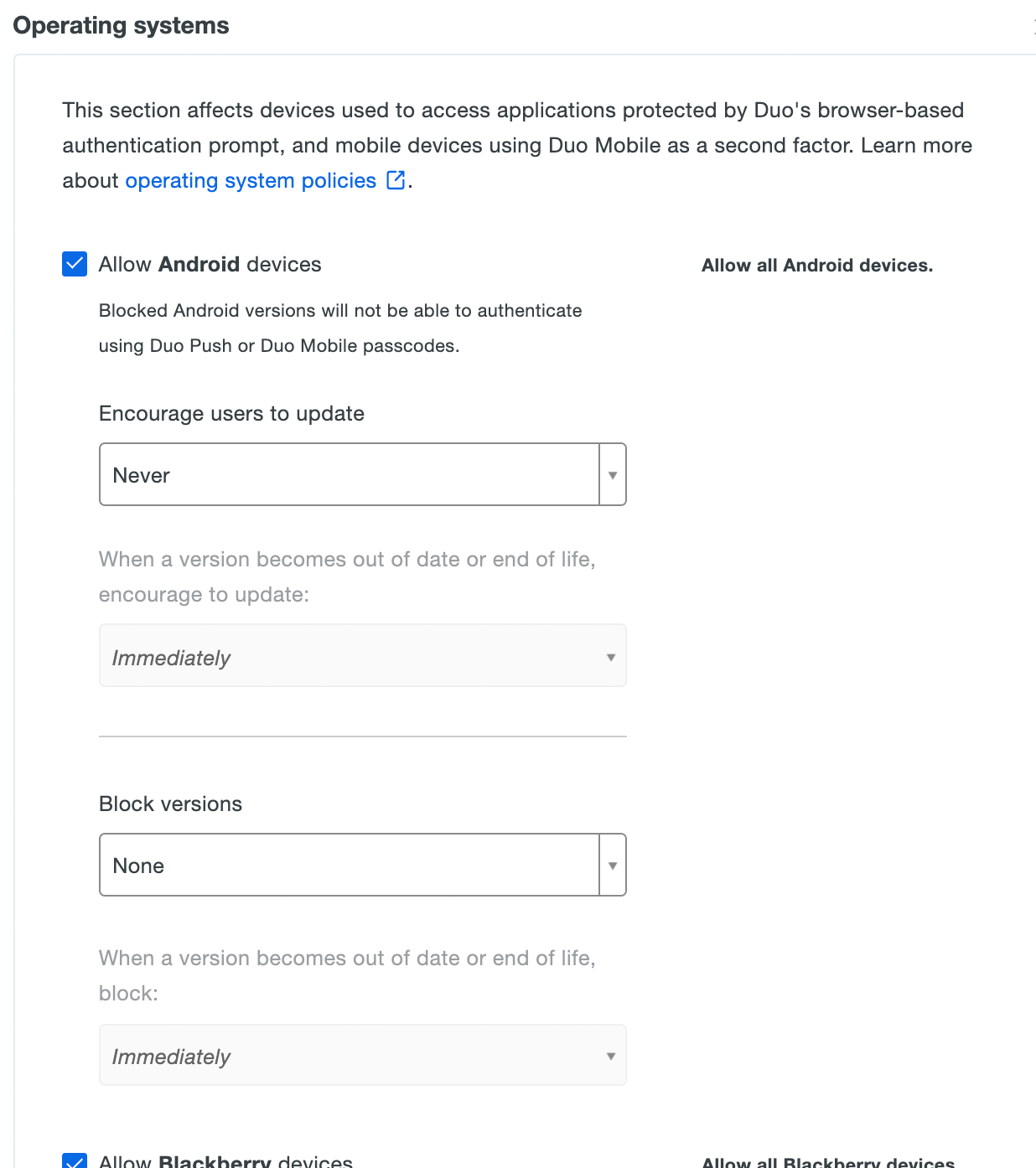
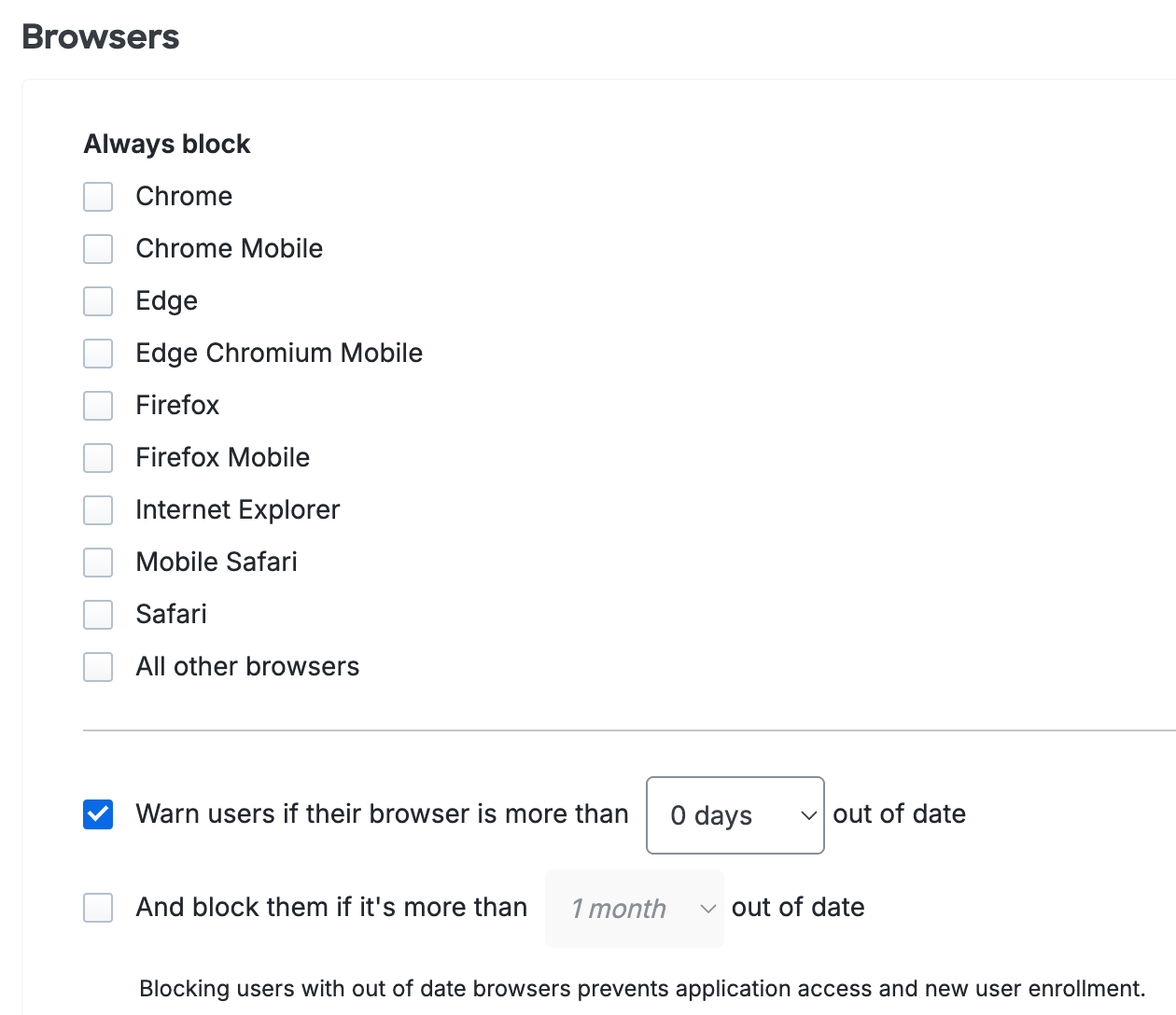
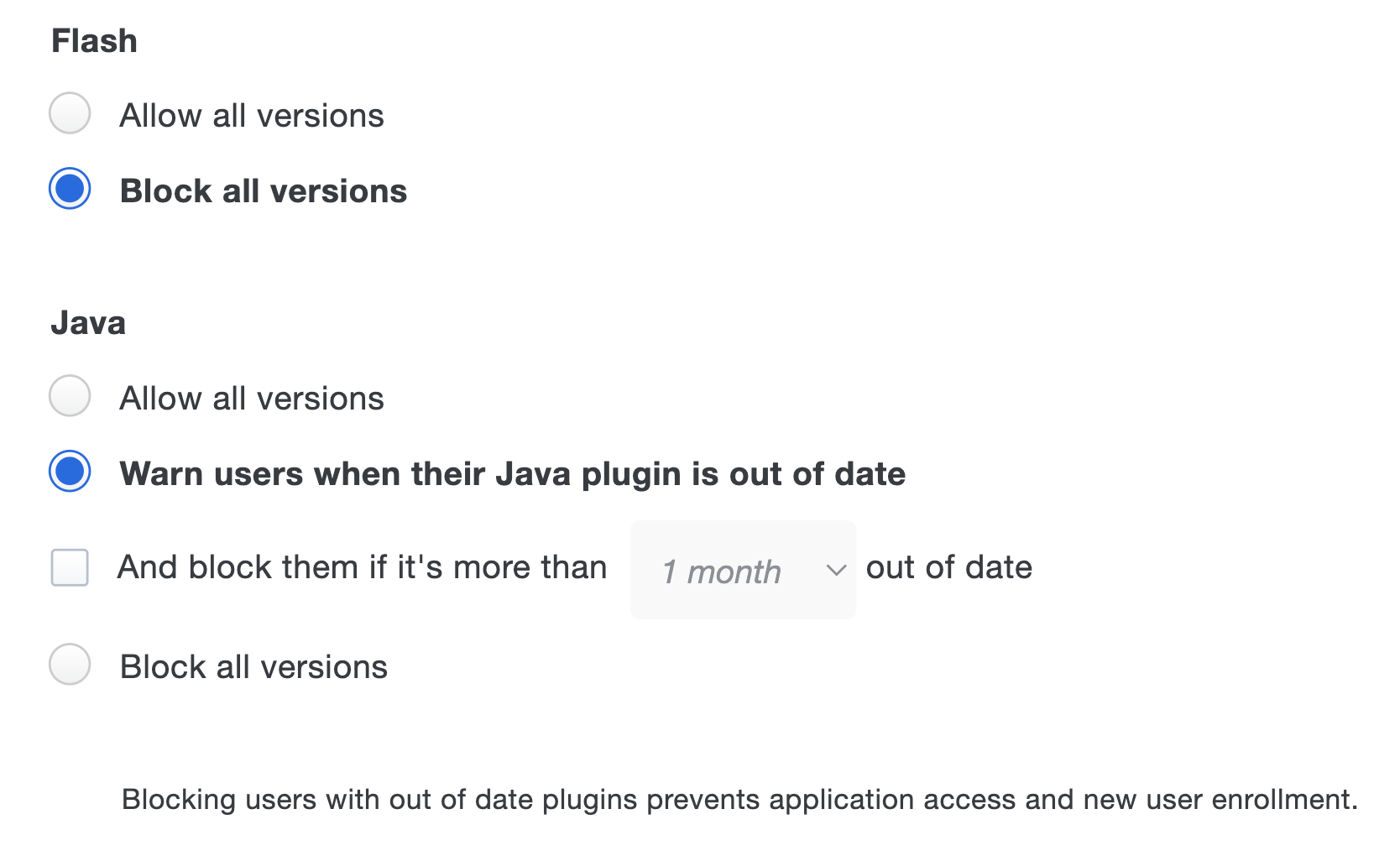
Use the Operating Systems, Browsers, and Plugins policy settings to restrict access and authentication from certain operating systems and versions, inform your users when their web browser or select plugins are out of date, and optionally block access to applications protected with Duo from devices with outdated software. Users authenticating via the Duo Prompt see a notification when the selected software is older than the current release version. If you choose to block access to users with outdated software or to selected operating systems, users are unable to complete authentication to access your applications.
Self-remediation notifications and access controls are available for the following:
- Operating Systems: Computer and mobile device platforms
- Browsers: Chrome, Chrome Mobile, Edge, Firefox, Internet Explorer, Mobile Safari, Safari, and all other browsers (which includes Firefox Mobile).
- Flash
- Java
See the Policy & Control documentation for more information.
Troubleshooting
Need some help? Try searching our Knowledge Base articles or Community discussions. For further assistance, contact Support.
