Legacy authentication protocols: Why RADIUS is (still) important
When reading the title of this blog, you might be wondering to yourself why RADIUS is being highlighted as a subject—especially amidst all of the advancements of modern authentication we see taking place recently. The truth is, for as old as RADIUS is, it is still (to this day) a vital protocol used in virtually every network infrastructure. Although it has many functions within the network itself, the purpose of this article is to show how RADIUS can be used when protecting applications with Duo, the benefits/drawbacks of the protocol, and why it deserves our attention.
Also, customers who subscribe to Duo Care have access to a Customer Success Manager (CSM) and a Customer Solutions Engineer (CSE). This dynamic duo provides solution architecture consulting, best practices, and overall security strategy when it comes to using RADIUS in conjunction with Duo’s services—and can help you navigate the pros and cons of the protocol relative to your organization’s specific environment and end-user needs.
What is RADIUS?
First, let's level-set on what we are talking about. RADIUS (Remote Authentication Dial-In User Service) is a networking protocol that provides centralized authentication, authorization, and accounting (AAA) management for users who connect and use a network service. It is commonly used for network access into VPNs, wireless access points, and other devices (more on this later).
RADIUS itself is a protocol that defines a method for passing authentication information between the network service and the AAA server, but it doesn't define the actual authentication methods. Instead, it supports a variety of authentication protocols, including EAP, PAP, CHAP, and others. Here are the differences between some of these protocols:
1. Extensible Authentication Protocol (EAP)
EAP is a framework that supports multiple authentication methods.
It’s very flexible and can work with a range of authentication mechanisms, including certificates and public key infrastructure (PKI).
EAP itself isn’t a specific authentication mechanism, but a way to encapsulate the authentication process.
EAP can be used in conjunction with RADIUS to authenticate users in more secure and complex scenarios.
It’s commonly used with wireless networks and Point-to-Point connections, but it’s also used for a specific VPN integration with Duo.
The only officially supported Duo integration that makes use of EAP is NetMotion Mobility.
Protected EAP (PEAP) allows for TLS inside of RADIUS. Note that this is different from RadSec, which is TLS encryption of RADIUS over TCP.
2. Password Authentication Protocol (PAP)
PAP is a simple authentication protocol where usernames and passwords are sent to the server as plain text.
Credentials are not encrypted using this protocol, but they can be obfuscated by the use of a shared secret, which is required when using the Duo Authentication Proxy.
Learn more about how Duo protects PAP authentication.
3. Challenge-Handshake Authentication Protocol (CHAP)
CHAP is more secure than PAP as it uses a challenge-response mechanism where the server sends a challenge to the client, the client responds with a value obtained by using a one-way hash function and the server checks this value.
The password itself is never actually sent over the network.
Periodic challenges can be sent to ensure that the password hasn’t been compromised and that the connection is still being managed by the same client.
The Duo Authentication Proxy does not support CHAP.
4. Microsoft Challenge-Handshake Authentication Protocol (MS-CHAP)
MS-CHAP is a Microsoft version of CHAP that includes additional features, such as a different method for hashing and an additional authentication response designed to support Microsoft clients and servers.
MS-CHAP v2 is an improvement over the original MS-CHAP and provides better security by using stronger cryptographic keys and a two-way authentication (mutual authentication).
Does the Duo Authentication Proxy support MS-CHAPv2 or EAP-MSCHAPv2?
In practice, the choice of which authentication protocol to use with RADIUS depends on the required level of security, the capabilities of the client and server equipment, and the specific use case.
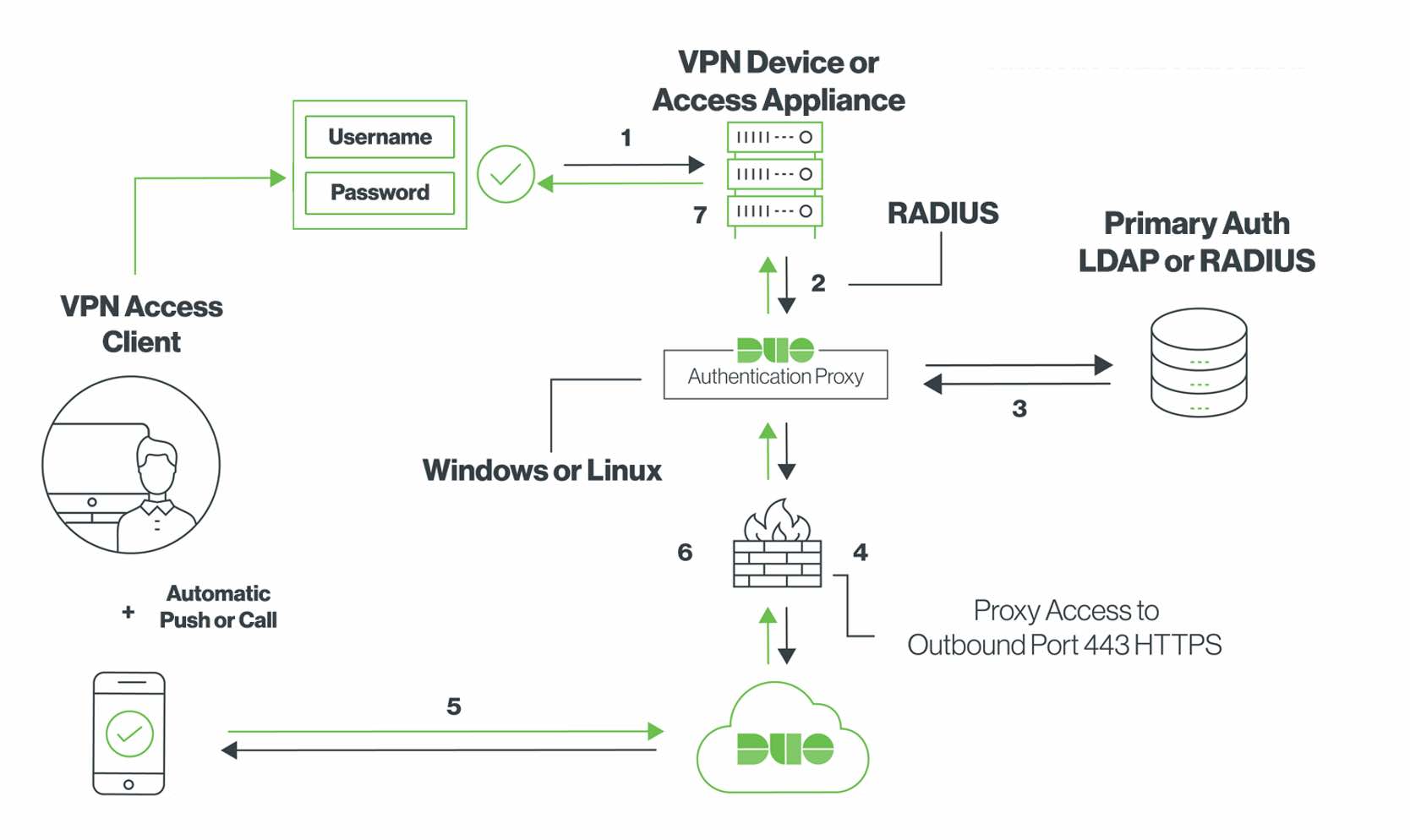
Anatomy of a RADIUS packet (with Duo MFA)
The flow of a RADIUS packet through the RADIUS protocol involves several steps and typically follows this sequence:
Access Request — The flow begins when a client device (known as a RADIUS client, usually a network access server or NAS) sends an Access-Request packet to a RADIUS server. This request includes credentials provided by the user, such as a username and password, along with other attributes like the IP address and port number. The application that Duo is protecting is acting as the RADIUS client device.
Processing the Request — Upon receiving the Access-Request, the RADIUS server processes the request by verifying the user's credentials against a user database, typically by way of the Duo Authentication Proxy. This might involve checking Active Directory (via LDAP) or another downstream RADIUS server, such as Microsoft NPS.
Challenges (Optional) — If additional information is required from the user (in the case of challenge-response authentication), the RADIUS server sends back an Access-Challenge packet to the RADIUS client. The client then prompts the user for additional information, which is sent back to the RADIUS server in another Access-Request packet. A typical example of this is when using the radius_server_challenege configuration of the Authentication Proxy.
Duo Multi-Factor Authentication — Once the Authentication Proxy receives a successful message from the user database (AD, NPS, etc.), it will send an HTTPS request to Duo’s cloud service to perform MFA. The results of that authentication will determine which RADIUS message is sent next.
Access-Accept or Access Reject — After processing the request, the RADIUS server will respond to the NAS with one of the following:
If Access-Accept — The user's credentials are valid, and the server provides authorization attributes that inform the NAS of any specific conditions for access. The user is permitted to access the application.
If Access-Reject — The user's credentials are not valid or the user is not authorized for access. No further attributes are needed or sent. The user is not permitted to access the application.
We won’t delve into Accounting workflows since Duo does not support this part of the RADIUS protocol. When Duo MFA is invoked, record-keeping data is tracked in the Authentication Log.
Throughout the entire process, RADIUS communication uses UDP as the transport protocol, with port 1812 being used by default. The RADIUS packets are also usually encrypted between the client and server to maintain security of sensitive information, such as passwords. It's important to note that RADIUS itself does not define encryption methods for the data payload; instead, it relies on a shared secret between the RADIUS client and server for obfuscating passwords and certain attributes. Learn how to protect the shared RADIUS secret and other passwords that reside on the Duo Authentication Proxy.
Is RADIUS still relevant?
RADIUS is typically viewed as a legacy network protocol since it cannot take advantage of modern security benefits that would normally be available when using WebAuthn, such as phishing-resistant MFA, enhanced device telemetry, biometrics, and Passwordless. We typically see RADIUS deployed (to this day) in a network appliance ecosystem because (along with TACACS+) it is one of the protocols of choice for logging into routers, switches, wireless access points, and VPNs. Robust identity platforms such as Cisco Identity Services Engine (ISE) can enhance the agility, automation, and visibility of the RADIUS protocol. Although it is recommended that end-user facing applications be migrated over to a modern authentication protocol such as browser-based SAML or OIDC (that leverage Single Sign-On), the need for RADIUS-based client/server authentication is still prevalent today. For example, consider the following points:
Widespread Adoption: RADIUS has been implemented in a wide range of network devices and services. Many vendors support RADIUS in their networking equipment, making it a de facto standard for network access control.
Centralized Authentication: RADIUS allows for centralized management of authentication credentials. This means that users can be authenticated across various network services and devices from a single point of control, which simplifies administration.
Support for Multiple Authentication Methods: RADIUS supports a variety of authentication methods, including PAP, CHAP, MS-CHAP, EAP, and more. This flexibility allows it to integrate with various types of user databases and authentication mechanisms, including modern multi-factor authentication (MFA) systems, such as Duo.
Interoperability: RADIUS works across different types of networks, including wired, wireless, and VPN connections. Its ability to function in diverse environments makes it a versatile tool for network administrators.
Scalability: It can handle a large number of authentication requests, making it suitable for organizations of all sizes, from small businesses to large enterprises and ISPs. Compared to LDAP, RADIUS has less overhead when processing requests via the Authentication Proxy.
Security: Although it has some limitations in terms of encryption, RADIUS does offer a level of security that is sufficient for many scenarios. The use of shared secrets and attribute obfuscation helps protect sensitive information as it travels across the network.
Compatibility With Legacy Systems: Many organizations have legacy systems and infrastructure that already integrate with RADIUS. Switching to a new system using SAML or OIDC may not be (yet) feasible for an organization or the application vendor, so RADIUS remains relevant for ensuring compatibility and protecting existing technology investments.
Should I use RADIUS with Duo?
Duo supports many named integrations via RADIUS as well as a generic integration that can be used to protect virtually any RADIUS-based application. When determining when to use RADIUS, you might be at the mercy of the application to only use RADIUS (and perhaps even a specific authentication protocol, such as MSCHAPv2). Or you might have the option to choose between RADIUS and another protocol such as LDAP or SAML when integrating with Duo. For example, Cisco ASA for AnyConnect has multiple integration options as seen in the ‘What are the differences between the various Cisco ASA configurations?’ knowledge base article.
To help you choose the best option for protecting your application with Duo, note some of the key differences between RADIUS and other protocols:
RADIUS can send the IP address of the client (user) by way of an attribute, typically when using calling-station-id or NAS-IP-Address. However, not all RADIUS devices send the IP address by default or may be able to send the address at all. Check your RADIUS application’s documentation for details.
LDAP cannot send the IP address of a client/user to Duo, so this makes RADIUS a better choice if you plan to use the IP address to make contextual decisions regarding your user’s location at the time of logon.
Using web-based applications and authentication methods such as WebAuthn (via SAML or OIDC) are even better because they can obtain the IP address (and other system information) directly from the user’s browser via the User-Agent string.
RADIUS supports Append Mode (concatenation), but only when using non-MS-CHAPv2 authentication protocols.
RADIUS supports inline password reset with the Duo Authentication Proxy but only with MS-CHAPv2.
As mentioned earlier, Cisco ISE can add more functionality to the RADIUS protocol. When ISE is integrated with Duo, you can easily add MFA to all RADIUS (and TACACS+) devices that use ISE as their downstream authentication server. See the solution overviews for Cisco ISE Auth API and Cisco ISE RADIUS.
RADIUS does not support phishing-resistant MFA methods such as Roaming Authenticators, Platform Authenticators, and Duo Passwordless as these all require use of the WebAuthn API. You can learn more about the WebAuthn specification.
Conclusion
No matter what authentication method or protocol you choose to integrate with Duo, there will always be differences in security, usability, and compatibility that should be carefully considered. RADIUS remains an integral part of most network ecosystems and has enough use today to warrant serious consideration. As applications move toward modern protocols such as OIDC and WebAuthn, we should see a reduction in overall RADIUS usage—but there will likely remain critical use cases to support for the foreseeable future.
Access-Accept!

