Duo for Oracle Access Manager
Last updated:
Support for the traditional Duo Prompt experience and Duo Prompt delivery via iframe ended on March 30, 2024.
See the update instructions for Oracle Access Manager to update an existing deployment of the iframe-based Oracle Access Manager software to the latest release. Authenticating once with the updated Duo software is a required step before you can enable the Duo Universal Prompt for your existing Oracle Access Manager application.
Please visit the Duo Universal Prompt Update Guide for more information about the traditional Duo Prompt end of support.
Duo's plug-in for Oracle Access Manager supports Oracle Access Manager 11g and later. The plugin supports FORM and COOKIE RequestCacheType configurations.
Before you install Duo for OAM, determine a Redirect URL to which the Duo plugin should redirect back to after successful two-factor authentication, which usually is the embedded credential endpoint for your OAM instance. An example URL example for ECC basic authentication flow would be https://<<oam-server-host>>:<<port>>/oam/server/auth_cred_submit. The redirect URL must be a valid HTTPS URL and port, using an RFC-1034-compliant hostname (not an IP address), with a maximum length of 1024 characters.
This application communicates with Duo's service on SSL TCP port 443.
Firewall configurations that restrict outbound access to Duo's service with rules using destination IP addresses or IP address ranges aren't recommended, since these may change over time to maintain our service's high availability. If your organization requires IP-based rules, please review Duo Knowledge Base article 1337.
Effective June 30, 2023, Duo no longer supports TLS 1.0 or 1.1 connections or insecure TLS/SSL cipher suites. See Duo Knowledge Base article 7546 for additional guidance.
First Steps
If you already have a previous version of the Duo OAM plugin installed, you must remove it before installing the v2 Universal plugin. See the steps in the Update the Duo Plugin section for more information..
- Sign up for a Duo account.
- Log in to the Duo Admin Panel and navigate to Applications → Application Catalog.
-
Locate the entry for Oracle Access Manager with the "2FA" label in the catalog. Click the + Add button to create the application and get your Client ID, Client secret, and API hostname. You'll need this information to complete your setup. See Protecting Applications for more information about protecting applications with Duo and additional application options.
Previously, the Client ID was called the "Integration key" and the Client secret was called the "Secret key".
- No active Duo users can log in to new applications until you grant access. Update the User access setting to grant access to this application to users in selected Duo groups, or to all users. Learn more about user access to applications. If you do not change this setting now, be sure to update it so that your test user has access before you test your setup.
This setting only applies to users who exist in Duo with "Active" status. This does not affect application access for existing users with "Bypass" status, existing users for whom the effective Authentication Policy for the application specifies "Bypass 2FA" or "Skip MFA", or users who do not exist in Duo when the effective New User Policy for the application allows access to users unknown to Duo without MFA.
- Download the latest DuoUniversalPlugin.jar 2.x.x plugin file from GitHub.
The security of your Duo application is tied to the security of your client secret. Secure it as you would any sensitive credential. Don't share it with unauthorized individuals or email it to anyone under any circumstances!
Duo Universal Prompt
The Duo Universal Prompt provides a simplified and accessible Duo login experience for web-based applications, offering a redesigned visual interface with security and usability enhancements.
| Universal Prompt | Traditional Prompt |
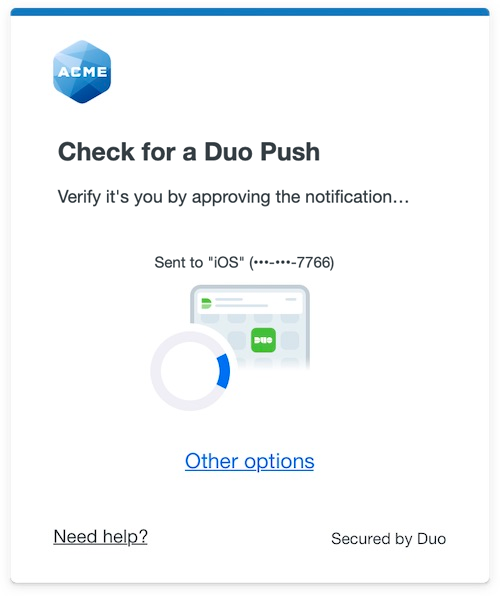 |
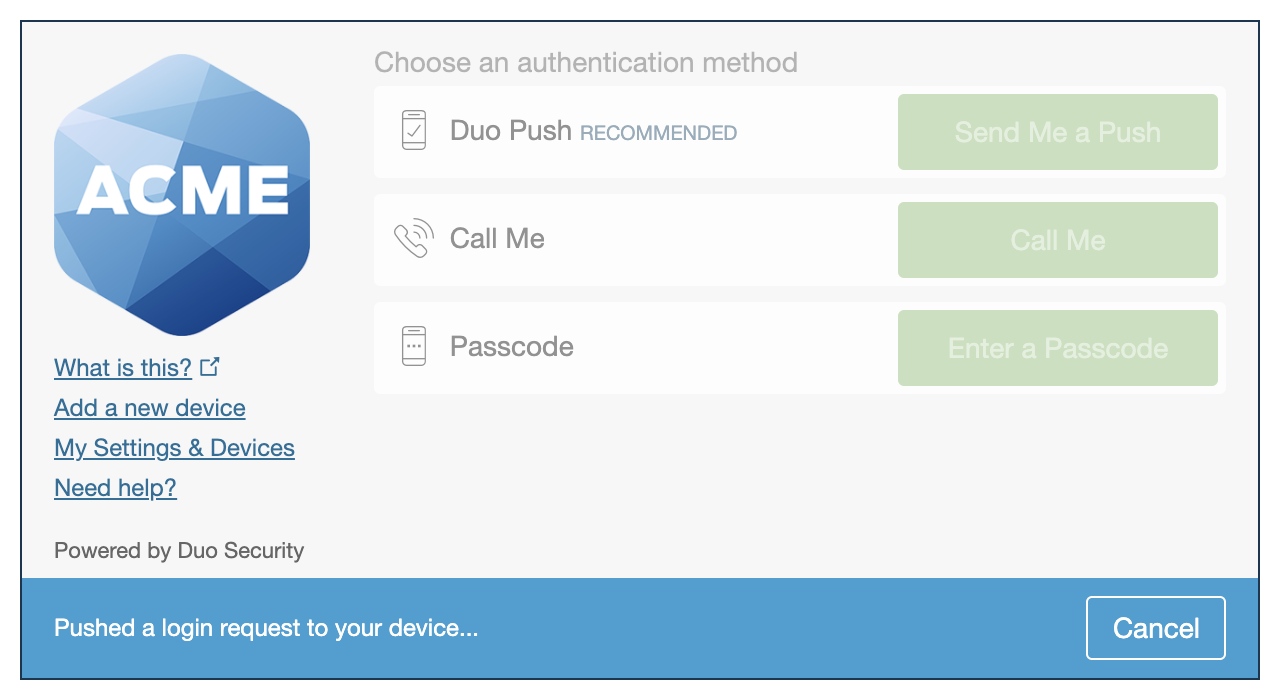 |
For Oracle Access Manager applications created before March 2024, migration to Universal Prompt is a three-step process:
- Install an update for the Oracle Access Manager application, which implements a redirect to Duo during authentication to support the Universal Prompt.
- Authenticate with Duo 2FA using the updated application so that Duo makes the Universal Prompt activation setting available in the Admin Panel. This first authentication after updating shows the traditional Duo prompt in a redirect instead of an iframe.
- From the Duo Admin Panel, activate the Universal Prompt experience for users of that Duo Oracle Access Manager application if the traditional prompt is still selected. Once activated, all users of the application see the Duo Universal Prompt in a redirect.
If you created your Oracle Access Manager application before March 2024, it's a good idea to read the Universal Prompt Update Guide for more information, about the update process and the new login experience for users, before you activate the Universal Prompt for your application.
New Oracle Access Manager Applications
When you install the latest version of Duo for OAM you're ready to use the Universal Prompt. Oracle Access Manager applications created after March 2024 have the Universal Prompt activated by default. If you're configuring Oracle Access Manager now, proceed with the installation instructions in this document.
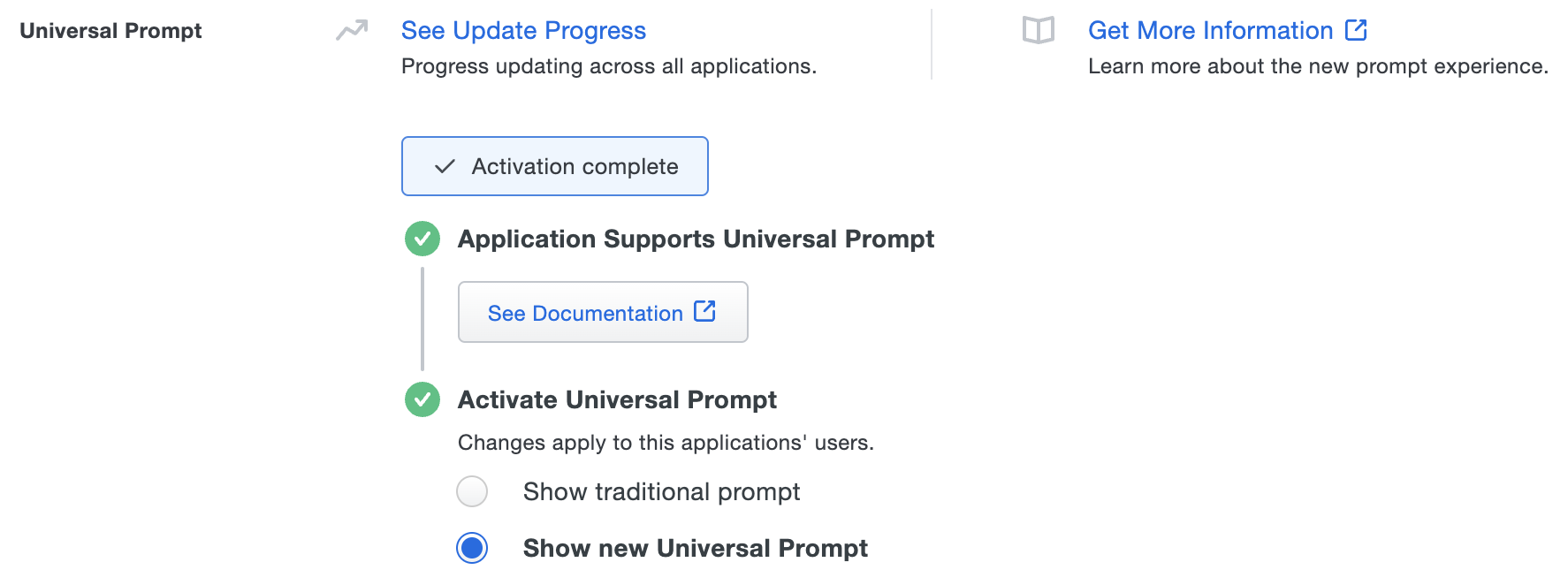
The "Universal Prompt" area of the application details page shows that this application is "Activation complete", with these activation control options:
- Show traditional prompt: Your users experience Duo's traditional prompt via redirect when logging in to this application.
- Show new Universal Prompt: (Default) Your users experience the Universal Prompt via redirect when logging in to this application.
Existing Oracle Access Manager Applications
Duo for OAM needs a software update installed to support the Universal Prompt. The "Universal Prompt" section of your existing Oracle Access Manager application reflects this status as "Update required". To update Duo for OAM application to a newer version, follow the update directions below.
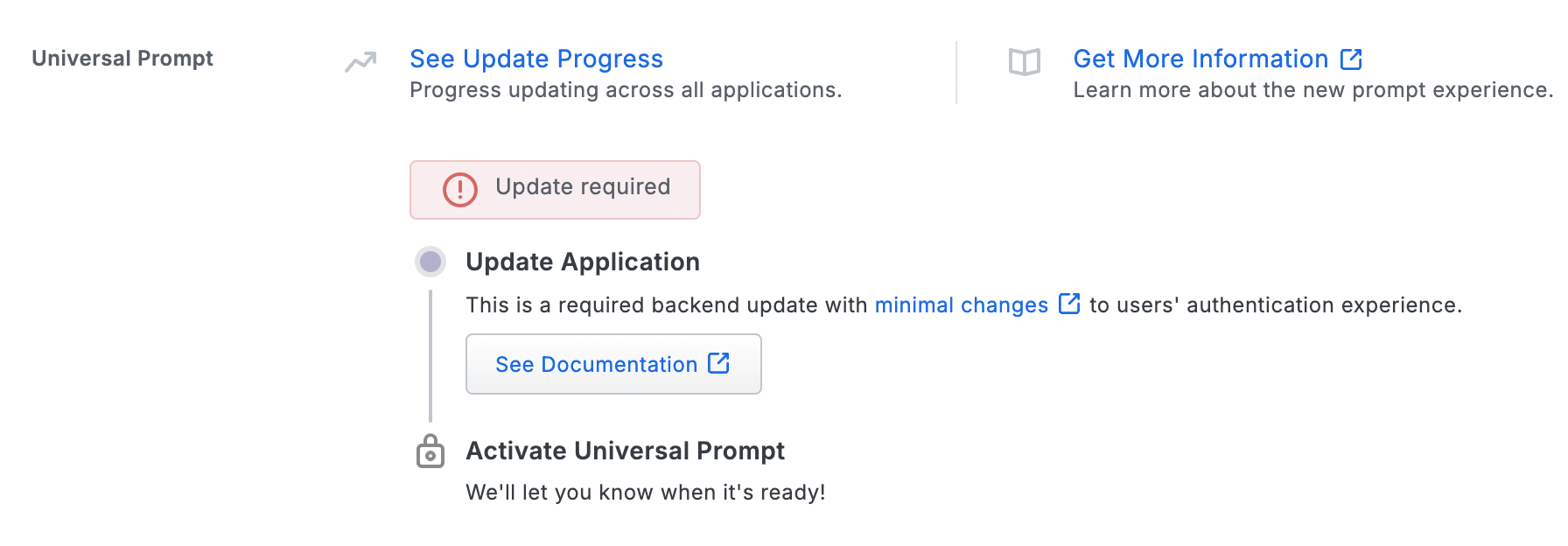
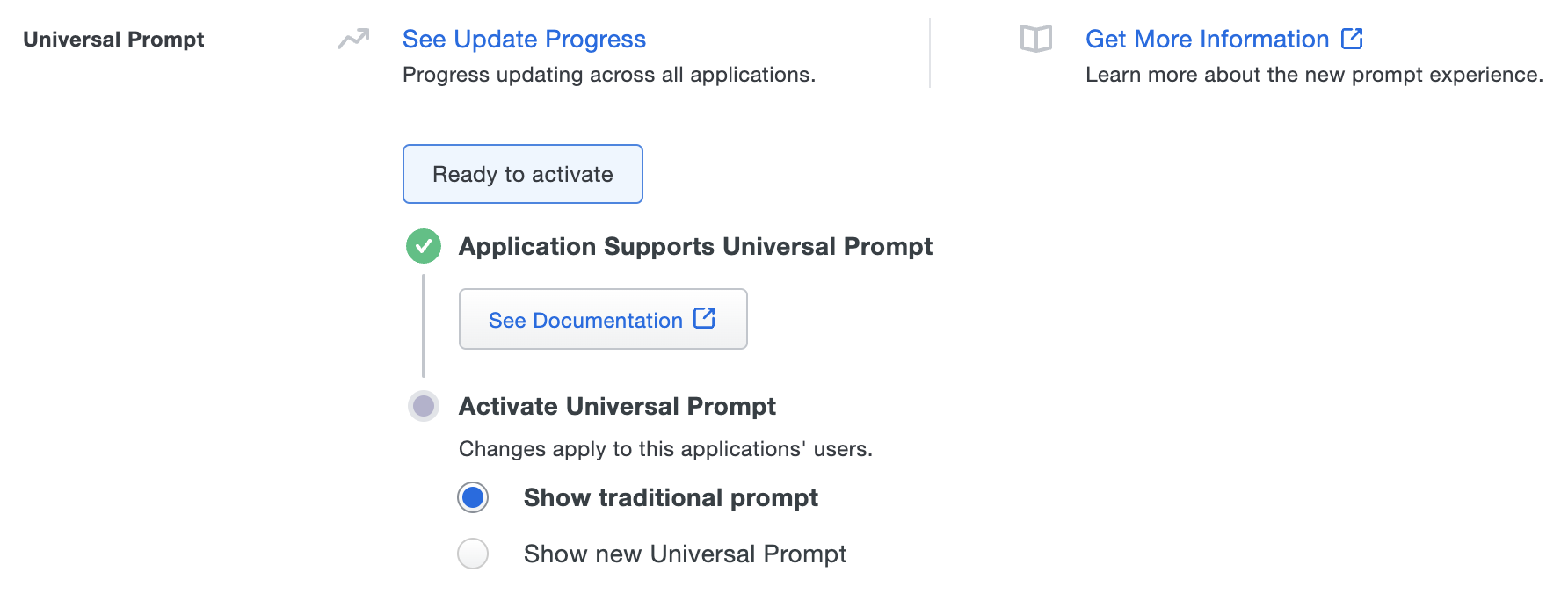
Once a user authenticates to Duo for OAM via the updated Duo plugin, the "Universal Prompt" section of the Oracle Access Manager application page reflects this status as "Ready to activate", with these activation control options:
- Show traditional prompt: (Default) Your users experience Duo's traditional prompt via redirect when logging in to this application.
- Show new Universal Prompt: Your users experience the Universal Prompt via redirect when logging in to this application.
In addition, the "Integration key" and "Secret key" property labels for the application update to "Client ID" and "Client secret" respectively. The values for these properties remain the same.
Activate Universal Prompt
Activation of the Universal Prompt is a per-application change. Activating it for one application does not change the login experience for your other Duo applications.
Enable the Universal Prompt experience by selecting Show new Universal Prompt, and then scrolling to the bottom of the page to click Save.
Once you activate the Universal Prompt, the application's Universal Prompt status shows "Activation Complete" here and on the Universal Prompt Update Progress report.

Should you ever want to roll back to the traditional prompt, you can return to this setting and change it back to Show traditional prompt. However, this will still deliver the Duo prompt via redirect, not in an iframe. Keep in mind that support for the traditional Duo prompt ended for the majority of applications in March 2024.
Universal Update Progress
Click the See Update Progress link to view the Universal Prompt Update Progress report. This report shows the update availability and migration progress for all your Duo applications. You can also activate the new prompt experience for multiple supported applications from the report page instead of visiting the individual details pages for each application.
Import the Duo JAR file
-
Sign into your Oracle Access Manager administrative console on your OAM server and click Application Security in the top right-hand corner.
-
On the launch pad page click Authentication Plug-ins located under "Plug-ins".
-
On the "Plug-ins" page click Import Plug-in....
-
Browse to and select the DuoUniversalPlugin.jar file you downloaded earlier. Click Import to import the Duo JAR file.
-
Click the refresh button on the "Plug-ins" page to reload the plug-ins.
-
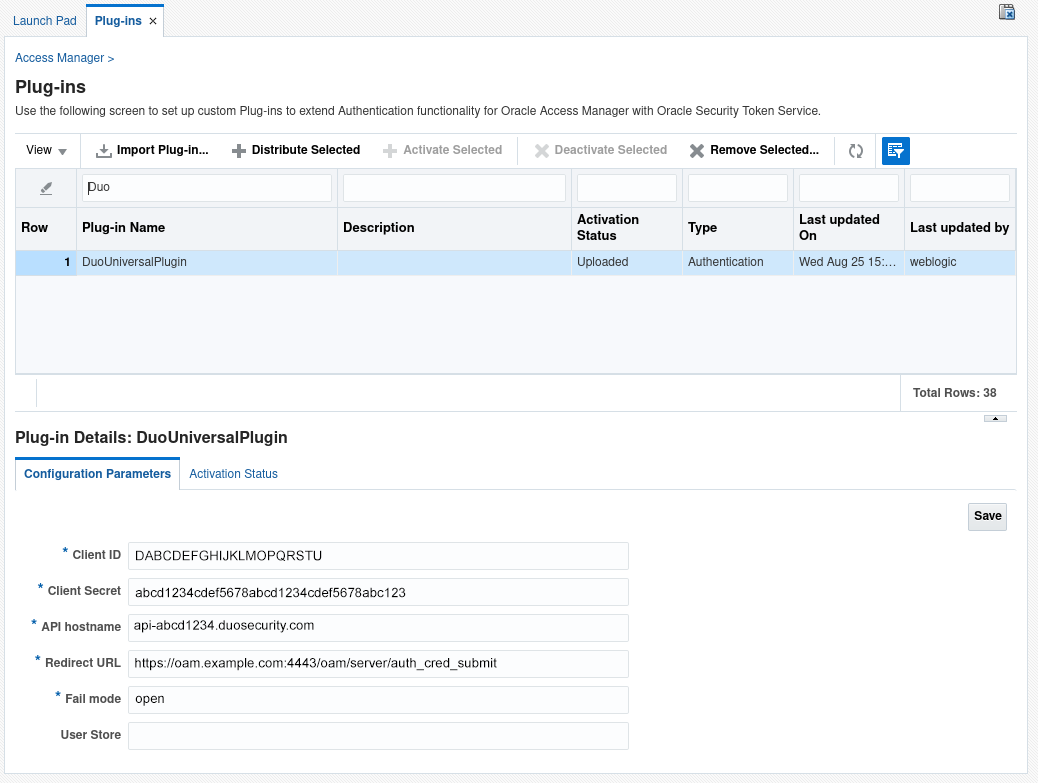
Scroll through the listed plug-ins and select DuoUniversalPlugin. It will show an "Activation Status" of Uploaded.
-
Fill out the Client ID, Client Secret, API hostname, Redirect URL, and Fail mode fields located under "Plug-in Details: DuoUniversalPlugin"
Client IDYour Client ID or Integration key from the OAM application in the Duo Admin Panel. Client SecretYour Client secret or Secret key from the OAM application in the Duo Admin Panel. API hostnameYour API hostname from the OAM application in the Duo Admin Panel. Redirect URLThe embedded credential endpoint URL for your OAM instance (example: https://<<oam-server-host>>:<<port>>/oam/server/auth_cred_submit).Fail modeEither safe or secure: failmode Description openIn the event that Duo's service cannot be contacted, users' authentication attempts will be permitted without 2FA if primary authentication succeeds. (Default) closedIn the event that Duo's service cannot be contacted, all users' authentication attempts will be rejected. User StoreOptional. If you'd like to use a different user identity store from the default system store, enter the name of the store here. Enter the store name exactly as shown in the "OAM ID Stores" table on the "User Identity Stores" configuration page. When all the fields have been populated click Save.
-
Once you've successfully saved the settings click the Distribute Selected button at the top of "Plug-ins" section. Click the refresh button to refresh the plug-ins page. The "Activation Status" will change to Distributed.
-
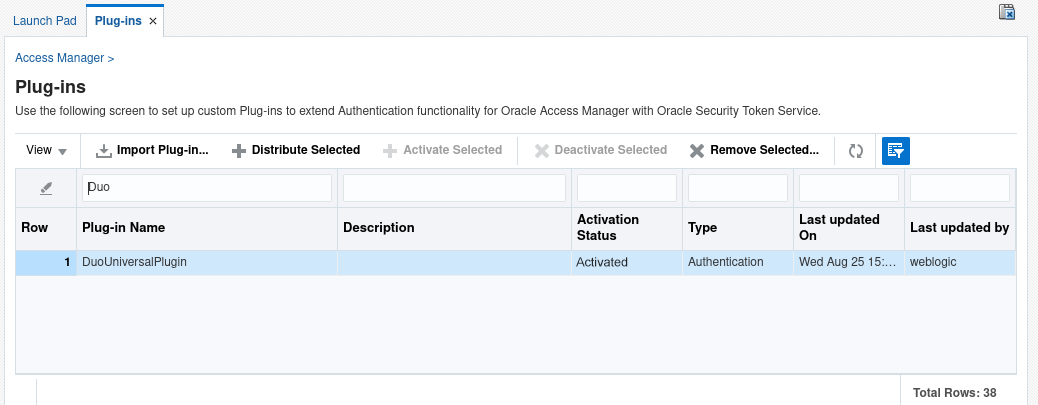
With the "DuoUniversalPlugin" selected click Activate Selected. Wait a moment for the page to reload and then click the refresh button. It will show an "Activation Status" of Activated.
Add Duo to an Authentication Module
Once the Duo plug-in has been uploaded and activated, add Duo to an existing authentication module and tell the plug-in how to respond during logins.
-
While logged into the administrative console for Oracle Access Manager click Application Security in the top right-hand corner of the screen.
-
On the launch pad page click Authentication Modules located under "Plug-ins".
-
On the "Authentication Modules" page click on the authentication module to which you want to add Duo as an authentication step.
-
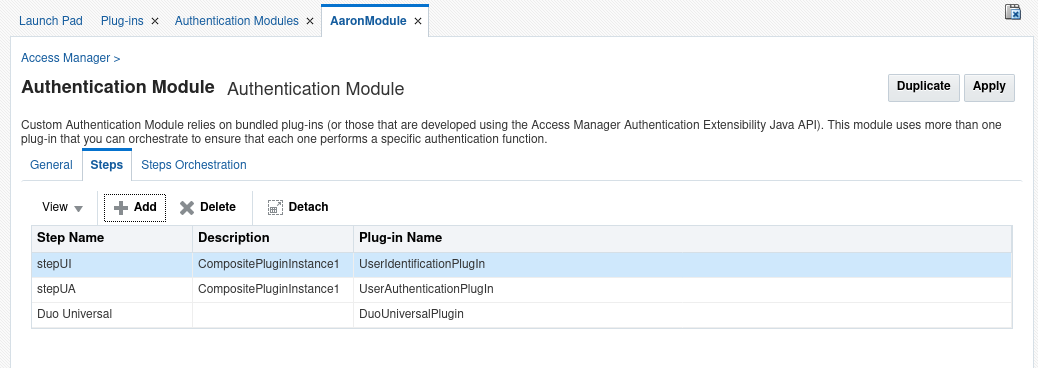
Click on the "Steps" tab. Click the + button to open the "Add new step" wizard.
-
Type Duo Universal for Step Name.
-
Leave the Description field blank.
-
Select DuoUniversalPlugin from the drop-down for Plug-in Name and click OK to add the new Duo step.
-
Click on the "Steps Orchestration" tab. You should see the Duo Universal as the last step in the list.
-
For the step immediately preceding Duo, change the On Success selection to Duo Universal using the drop-down. This means that if that step succeeds, the next step should invoke Duo authentication.
-
For the "Duo Universal" step, set On Success to success using the drop-down.
-
Set both the On Failure and On Error for the "Duo Universal" step to failure using the drop-down.
-
Click the Apply button. The page reloads confirming the module update.
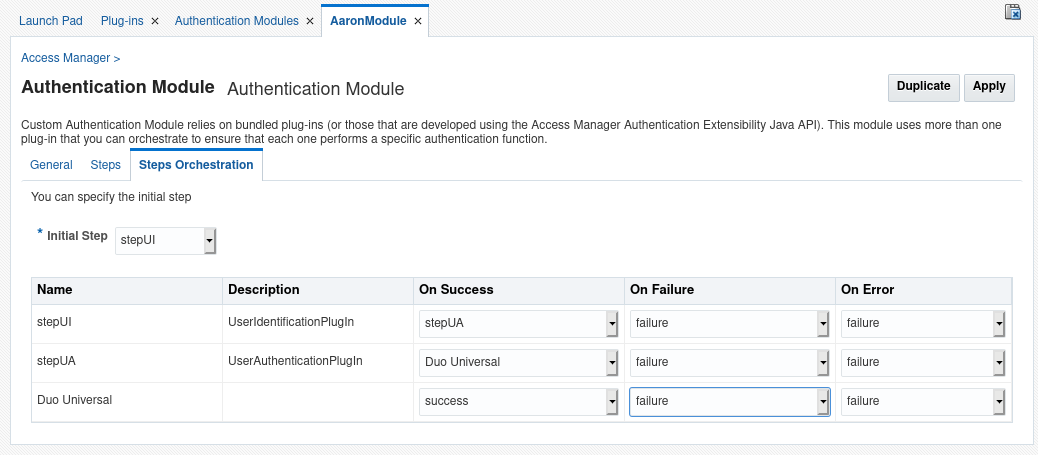
You can repeat these steps to add Duo Universal 2FA to other authentication modules.
Restart Oracle Access Manager
The Duo plug-in requires that the Oracle Access Manager must be restarted before the plug-in can be used. There are two different methods for restarting Oracle Access Manager.
Method One
Restart Oracle Access Manager through the WebLogic console.
-
Sign into your WebLogic administrative console on your OAM server.
-
On the WebLogic administrative console click Environment in the left-hand side menu.
-
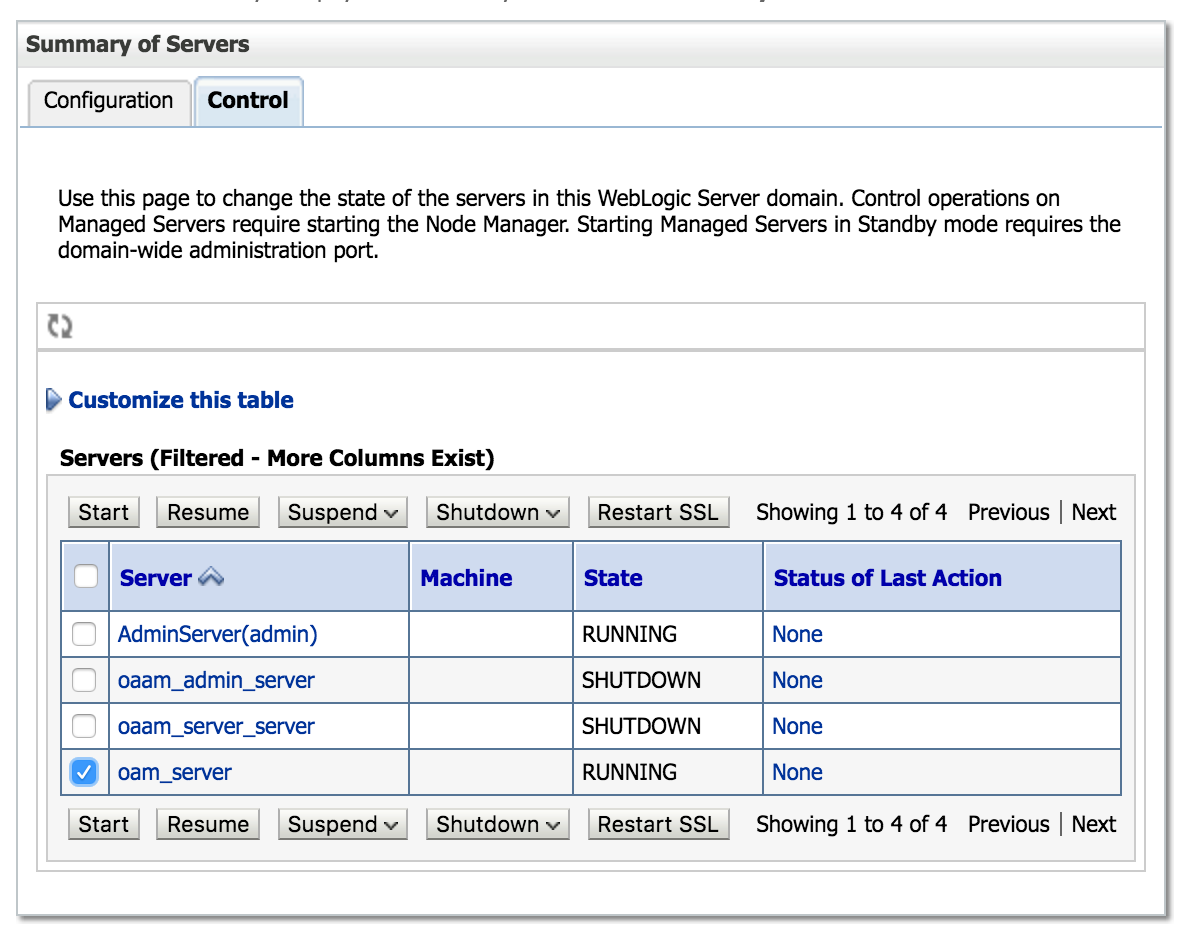
Click Servers on the "Summary of Environment" page.
-
On the "Summary of Servers" page click the Control tab.
-
Locate your Oracle Access Manager server and click the checkbox next to it. Click the Shutdown button and choose between the shutdown options.
-
Once the server is completely shut down click Start.
Method Two
Restart Oracle Access Managers through scripts
-
While signed into the Oracle Access Manager server locally with a terminal open or through SSH, navigate to the bin directory of your Oracle Access Manager server.
Example: $ORACLE_HOME/user_projects/domains/your_domain_name/bin
-
Shutdown the Oracle Access Manager server by running the command below. Replace MANAGED_SERVER_NAME with the name of your Oracle Access Manager server, in this example it is oam_server. Replace ADMIN_SERVER_URL with the URL of your Oracle Access Manager console, an example would be https://oam.yourcompany.com:7001.
./stopManagedWebLogic.sh MANAGED_SERVER_NAME ADMIN_SERVER_URL -
Once the server has shut down, run the following command to start up the server using the same values from the last step.
./startManagedWebLogic.sh MANAGED_SERVER_NAME ADMIN_SERVER_URLNote: If you are running WebLogic and Oracle Access Manager on Windows instead of Linux replace
stopManagedWebLogic.shwithstopManagedWebLogic.cmdandstartManagedWebLogic.shwithstartManagedWebLogic.cmd.
Test Duo 2FA
Once your Oracle Access Manager server has been successfully restarted, log into an Application Domain protected with Duo. Enter your primary directory logon information, approve Duo two-factor authentication, and get redirected to your site after authenticating.
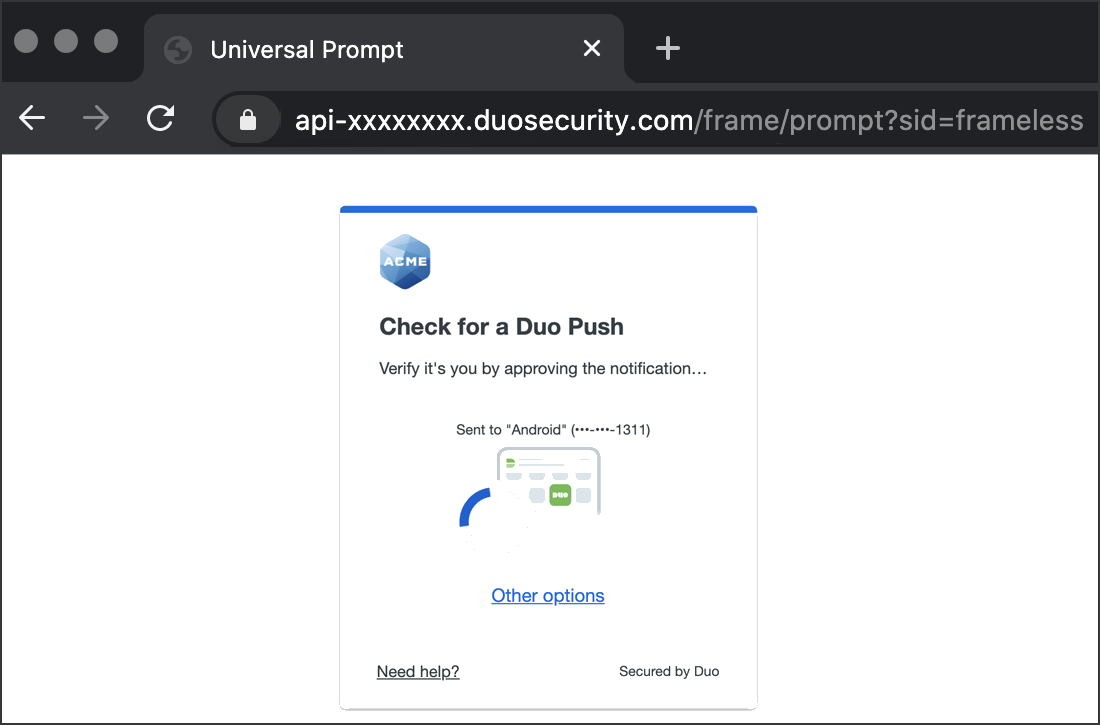
*Universal Prompt experience shown.
Congratulations! Oracle Access Manager is now protected with Duo two-factor authentication.
Grant Access to Users
If you did not already grant user access to the Duo users you want to use this application be sure to do that before inviting or requiring them to log in with Duo.
Logging
Duo for Oracle Access Manager logs are saved within the normal Oracle Access Manager log files located at $ORACLE_HOME/user_projects/domains/your_domain_name/servers/your_oam_server/logs/.
Update the Duo Plugin
There is no direct update path from v1 of the Duo OAM plugin to v2. If you need to update to v2 you should completely remove the existing v1 plugin and configuration from your OAM server, and then download the v2 plugin JAR and follow the rest of the installation steps.
To remove the v1 Duo plugin from OAM:
- Edit any OAM Application Domain to which you added Duo to remove that rule.
- Delete any authentication schemas you created for the Duo v1 plugin and WAR file.
- Remove the v1 "Duo 2FA" authentication module.
- Go to the OAM Plug-ins page and first deactivate and then remove the v1 "Duo Plugin".
- Edit your WebLogic deployment's application assistants to delete the "DuoLogin" deployment and corresponding DuoLogin.war file.
- Verify that OAM login works without Duo, and then install the Duo v2 OAM plugin and update your authentication modules.
Troubleshooting
Need some help? Take a look at our OAM Knowledge Base articles or Community discussions. For further assistance, contact Support.
Network Diagram
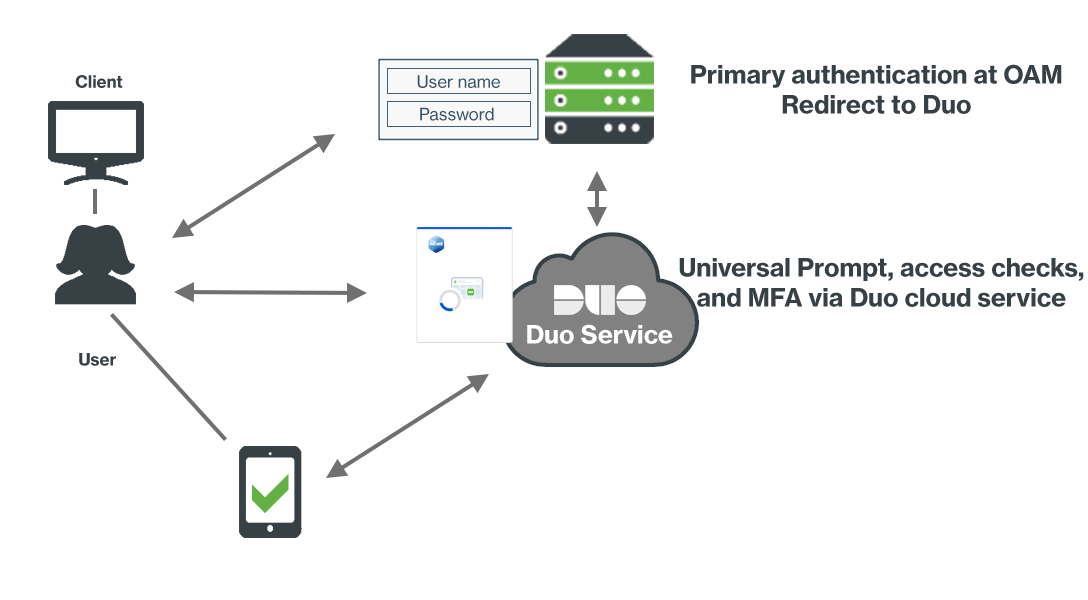
- OAM client connection initiated.
- Primary authentication at OAM server
- OIDC redirect to Duo's service.
- Secondary authentication and client access device checks via Duo Universal Prompt.
- OAM receives Duo authorization response.
- OAM user login complete.
