Duo Two-Factor Authentication for Microsoft Remote Desktop Gateway on Windows 2016 and Later
Last updated:
Overview
Duo Authentication for Remote Desktop Gateway adds two-factor authentication to your RemoteApp Access logons, and blocks any connections to your Remote Desktop Gateway server(s) from users who have not completed two-factor authentication when all connection requests are proxied through a Remote Desktop Gateway. Users automatically receive a 2FA prompt in the form of a push request in Duo Mobile or a phone call when logging in.
Incompatibility with RD CAP and RAP
Installing Duo's RD Gateway plugin disables Remote Desktop Connection Authorization Policies (RD CAP) and Resource Authorization Policies (RD RAP). The CAPs and RAPs become inaccessible from the Remote Desktop Gateway Manager and previously configured policy settings are ignored by Remote Desktop Gateway. If operational requirements mandate continued use of RD CAPs/RAPs, you may want to consider installing Duo for Windows Logon at your RDS Session Hosts instead. Unlike Duo for RD Gateway, this alternative configuration featuring Duo for Windows Logon also supports passcode authentication.
Before you begin deploying Duo in your RDS environment, please read our Duo 2FA for Microsoft Remote Desktop Services overview to understand the capabilities and limitations of the different deployment options.
Duo Factor Support
This configuration does not support the verified Duo Push, SMS passcodes, hardware token passcodes, YubiKey passcodes, passcodes generated by Duo Mobile, WebAuthn security keys or platform authenticators, Duo Desktop authenticators, or bypass codes authentication methods.
Duo for RD Gateway supports these authentication methods ONLY:
- Duo Push
- Phone Call
Do not apply authentication methods policies that restrict use of Duo Push or phone call to your Duo RD Gateway application, as that would prevent user authentications.
Enroll Users Before Installation
Duo Authentication for RD Gateway doesn't support inline self-service enrollment for new Duo users. Unenrolled users, that is, users that do not yet exist in Duo with an attached 2FA device, must be created manually by an administrator, imported by an administrator or self-enrolled through another application which supports Duo’s self-service enrollment (see Test Your Setup).
The Duo username (or username alias) should match the Windows username. When you create your new RD Gateway application in Duo the username normalization setting defaults to "Simple", which means that the if the application sends the usernames "jsmith," "DOMAIN\jsmith," and "jsmith@domain.com" to Duo at login these would all resolve to a single "jsmith" Duo user.
Duo for RD Gateway supports Duo Push and phone callback authentication methods. Duo users must have one of these methods available to complete 2FA authentication.
Read the enrollment documentation to learn more about enrolling your users in Duo, and ensure your enrolled users have Duo Push or a phone enrolled..
Prerequisites
Make sure to complete these requirements before installing Duo Authentication for RD Gateway.
-
Check your server version. These instructions are for installing Duo Authentication for RD Gateway on Windows Server 2016 and later.
-
Make sure you have installed .NET Framework 4.5 on your RD Gateway server. You can do this, for example, by running the following PowerShell commands:
Import-Module ServerManager Add-WindowsFeature NET-Framework-Core -
Also make sure you have installed ASP.NET 4.5 support for IIS. The PowerShell commands for this are:
Import-Module ServerManager Add-WindowsFeature NET-Framework-45-ASPNET
This application communicates with Duo's service on SSL TCP port 443.
Firewall configurations that restrict outbound access to Duo's service with rules using destination IP addresses or IP address ranges aren't recommended, since these may change over time to maintain our service's high availability. If your organization requires IP-based rules, please review Duo Knowledge Base article 1337.
Effective June 30, 2023, Duo no longer supports TLS 1.0 or 1.1 connections or insecure TLS/SSL cipher suites. See Duo Knowledge Base article 7546 for additional guidance.
TLS Requirements
Effective June 30, 2023, Duo no longer supports TLS 1.0 or 1.1 connections or insecure TLS/SSL cipher suites.
The current version of Duo for RD Gateway supports TLS 1.2 when installed on RDS servers running a version of Windows that also supports and uses TLS 1.2 or higher.
See the article Guide to TLS support for Duo applications and TLS 1.0 and 1.1 end of support for more information.
First Steps
Before moving on to the deployment steps, it's a good idea to familiarize yourself with Duo administration concepts and features like options for applications, available methods for enrolling Duo users, and Duo policy settings and how to apply them. See all Duo Administrator documentation.
- Sign up for a Duo account.
- Log in to the Duo Admin Panel and navigate to Applications → Application Catalog.
- Locate the entry for Microsoft RD Gateway with the "2FA" label in the catalog. Click the + Add button to create the application and get your integration key, secret key, and API hostname. You'll need this information to complete your setup. See Protecting Applications for more information about protecting applications with Duo and additional application options.
- No active Duo users can log in to new applications until you grant access. Update the User access setting to grant access to this application to users in selected Duo groups, or to all users. Learn more about user access to applications. If you do not change this setting now, be sure to update it so that your test user has access before you test your setup.
This setting only applies to users who exist in Duo with "Active" status. This does not affect application access for existing users with "Bypass" status, existing users for whom the effective Authentication Policy for the application specifies "Bypass 2FA" or "Skip MFA", or users who do not exist in Duo when the effective New User Policy for the application allows access to users unknown to Duo without MFA.
- Download the Duo Authentication for Remote Desktop Gateway Installer Package. View checksums for Duo downloads here.
The security of your Duo application is tied to the security of your secret key (skey). Secure it as you would any sensitive credential. Don't share it with unauthorized individuals or email it to anyone under any circumstances!
Deployment Tip
Set your application's New User Policy to "Allow Access" while testing. Enrolled users must complete two-factor authentication, while all other users are transparently let through.
Enrolled users that have Duo Push enabled on their smartphone will receive a push authentication prompt. Enrolled users that do not have Duo Push enabled will receive a phone call. Unenrolled users, that is, users that do not yet exist in Duo with an attached 2FA device, must be imported by an administrator or self-enrolled through another application which supports Duo’s self-service enrollment (see Test Your Setup).
Then (when you’re ready) change the "New user policy" to "Deny Access." This will cause unenrolled users to be denied access while requiring all enrolled users to authenticate with Duo after they type in their usernames and passwords.
Installation
-
Launch the Duo Security installer MSI from an elevated command prompt (right-click "Command Prompt" and select the "Run as Administrator" option). Accept the license agreement and continue.
-
Enter the integration key, secret key, and API hostname from the properties page of the "Microsoft RD Gateway" application you created earlier.
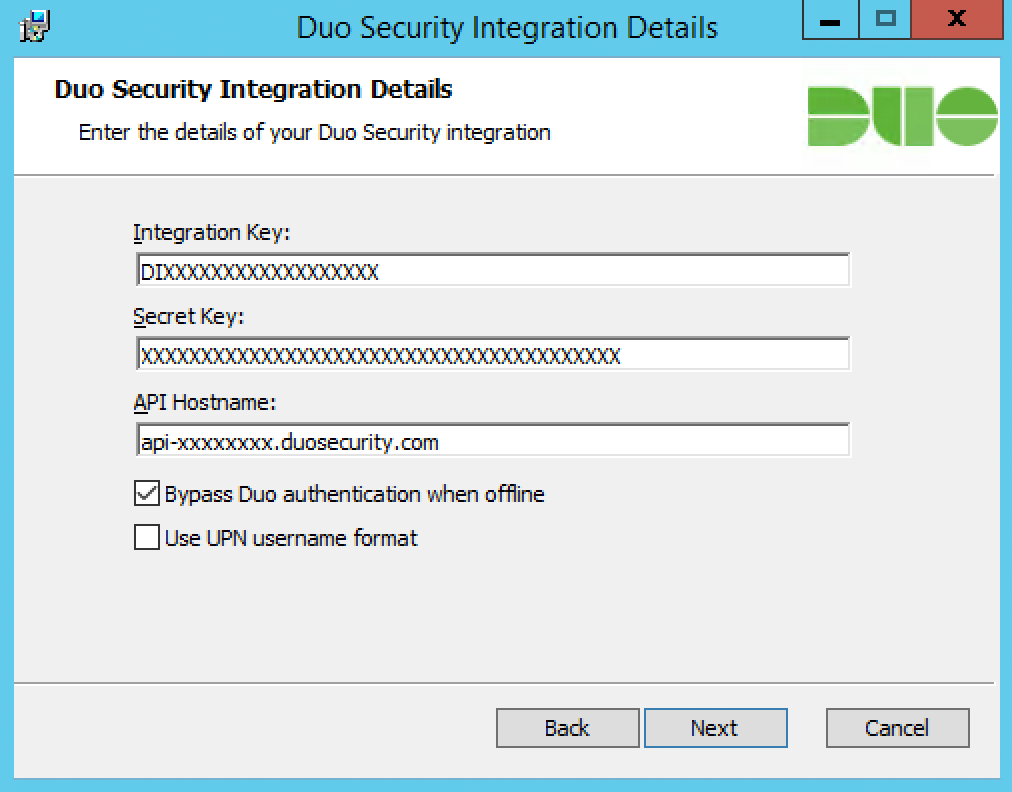
-
If you leave the "Bypass Duo authentication when offline" box in the Duo installer checked, then your users will be able to logon without completing two-factor authentication if the Duo Security cloud service is unreachable. If that box is unchecked then all RD Gateway login attempts will be denied if there is a problem contacting the Duo service.
-
Duo for RD Gateway sends a user's Windows
sAMAccountNameto Duo's service by default. To send theuserPrincipalNameto Duo instead, check the Use UPN username format box.If you enable the UPN username format option, you must also change the properties of your RD Gateway application in the Duo Admin Panel to change the "Username normalization" setting to None. Otherwise, Duo drops the domain suffix from the username sent from RD Gateway to our service, which may cause user mismatches or duplicate enrollment.
-
-
Complete the Duo installation. The Duo installer stops and then restarts the Remote Desktop Gateway service on your RD Gateway server automatically.
Test Your Setup
To test your setup, launch an application from RemoteApp and Desktop Connections or double-click a saved .RDP file for a published application or desktop. Enter your primary Windows credentials if prompted to do so by the Remote Desktop client. You will then automatically receive a push request in Duo Mobile or a phone call to confirm your identity. The app completes launch after approving the Duo authentication request.
Duo Authentication for Remote Desktop Gateway sets the idle timeout for a Remote Desktop session connecting through the protected RD Gateway server to two hours and the maximum RD session duration to eight hours. There are unsupported controls around idle and session timeout available in our Knowledge Base article here.
Grant Access to Users
If you did not already grant user access to the Duo users you want to use this application be sure to do that before inviting or requiring them to log in with Duo.
Update Duo for RD Gateway
You can upgrade your Duo installation over the existing version; there's no need to uninstall first.
-
Download the most recent Duo RD Gateway Installer Package and run the MSI from an elevated command prompt. View checksums for Duo downloads here.
-
Follow the on-screen prompts to complete the upgrade installation. Note that the installer restarts the Remote Desktop Gateway service.
Duo Secret Rotation
If you need to reset the secret key for Duo for RD Gateway after installation try the Duo Secret Rotation tool.
Troubleshooting
Need some help? Take a look at the RDS Frequently Asked Questions (FAQ) page or try searching our RDS Knowledge Base articles or Community discussions. For further assistance, contact Support.
If the Duo application denies access to your users, ensure that you have enrolled them in Duo with a username or username alias that matches the username they use to log into Windows, and with a 2FA device attached that is activated for Duo Push or can receive phone calls from Duo, or if you applied a new user policy that allows access without 2FA and expect it to allow the blocked users through that the blocked users do not exist in Duo. Refer to these articles to learn more about user enrollment states and how they combine with policy settings to affect user logins.
