Duo Two-Factor Authentication for SailPoint IdentityNow
Last updated:
Overview
SailPoint helps the world's largest organizations securely and effectively manage user access through Identity Governance services like Provisioning, Access Requests, Access Certifications, Password Management and Separation of Duties.
Duo Security's two-factor authentication strengthens secured access to SailPoint’s IdentityNow platform by adding an extra level of authentication for user login and password reset.
The instructions and applications described on this page do not apply to the SailPoint Duo Connector for user management. To configure the Duo Connector you must create a Duo Admin API application and follow either the SailPoint and Duo IdentityIQ Connector configuration instructions or SailPoint and Duo IdentityNow Connector configuration instructions on the SailPoint site.
This application communicates with Duo's service on SSL TCP port 443.
Firewall configurations that restrict outbound access to Duo's service with rules using destination IP addresses or IP address ranges aren't recommended, since these may change over time to maintain our service's high availability. If your organization requires IP-based rules, please review Duo Knowledge Base article 1337.
Effective June 30, 2023, Duo no longer supports TLS 1.0 or 1.1 connections or insecure TLS/SSL cipher suites. See Duo Knowledge Base article 7546 for additional guidance.
Duo 2FA for IdentityNow Logins
This configuration adds Duo two-factor authentication to IdentityNow user logins.
Note: This Duo application is not compatible with the SailPoint Duo Connector. To configure the Duo Connector please create an Admin API Duo application and refer to the configuration instructions linked from the Duo Connector page on the SailPoint site.
First Steps
- Sign up for a Duo account.
- Log in to the Duo Admin Panel and navigate to Applications → Application Catalog.
- Locate the entry for SailPoint API with the "2FA" label in the catalog. Click the + Add button to create the application and get your integration key, secret key, and API hostname. You'll need this information to complete your setup. See Protecting Applications for more information about protecting applications with Duo and additional application options. (See Getting Started for help.)
- No active Duo users can log in to new applications until you grant access. Update the User access setting to grant access to this application to users in selected Duo groups, or to all users. Learn more about user access to applications. If you do not change this setting now, be sure to update it so that your test user has access before you test your setup.
This setting only applies to users who exist in Duo with "Active" status. This does not affect application access for existing users with "Bypass" status, existing users for whom the effective Authentication Policy for the application specifies "Bypass 2FA" or "Skip MFA", or users who do not exist in Duo when the effective New User Policy for the application allows access to users unknown to Duo without MFA.
- Do not enable Username Normalization for this application.
The security of your Duo application is tied to the security of your secret key (skey). Secure it as you would any sensitive credential. Don't share it with unauthorized individuals or email it to anyone under any circumstances!
Configure the Duo Security Integration in IdentityNow
Refer to the Duo Security Integration Guide on the SailPoint Identity Services documentation site. Follow the directions to configure Duo 2FA for logins in your IdentityNow environment.
Duo 2FA for IdentityNow Password Resets
This configuration adds Duo two-factor authentication as a verification option for IdentityNow password reset and account unlock.
Note: This Duo application is not compatible with the SailPoint Duo Connector. To configure the Duo Connector please create an Admin API Duo application and refer to the configuration instructions linked from the Duo Connector page on the SailPoint site.
First Steps
- Sign up for a Duo account.
- Log in to the Duo Admin Panel and navigate to Applications → Application Catalog.
-
Locate the entry for SailPoint Web with the "2FA" label in the catalog. Click the + Add button to create the application and get your Client ID, Client secret, and API hostname. You'll need this information to complete your setup. See Protecting Applications for more information about protecting applications with Duo and additional application options.
Previously, the Client ID was called the "Integration key" and the Client secret was called the "Secret key".
- No active Duo users can log in to new applications until you grant access. Update the User access setting to grant access to this application to users in selected Duo groups, or to all users. Learn more about user access to applications. If you do not change this setting now, be sure to update it so that your test user has access before you test your setup.
This setting only applies to users who exist in Duo with "Active" status. This does not affect application access for existing users with "Bypass" status, existing users for whom the effective Authentication Policy for the application specifies "Bypass 2FA" or "Skip MFA", or users who do not exist in Duo when the effective New User Policy for the application allows access to users unknown to Duo without MFA.
- Do not enable Username Normalization for this application.
The security of your Duo application is tied to the security of your secret key (skey). Secure it as you would any sensitive credential. Don't share it with unauthorized individuals or email it to anyone under any circumstances!
Duo Universal Prompt
The Duo Universal Prompt provides a simplified and accessible Duo login experience for web-based applications, offering a redesigned visual interface with security and usability enhancements.
| Universal Prompt | Traditional Prompt |
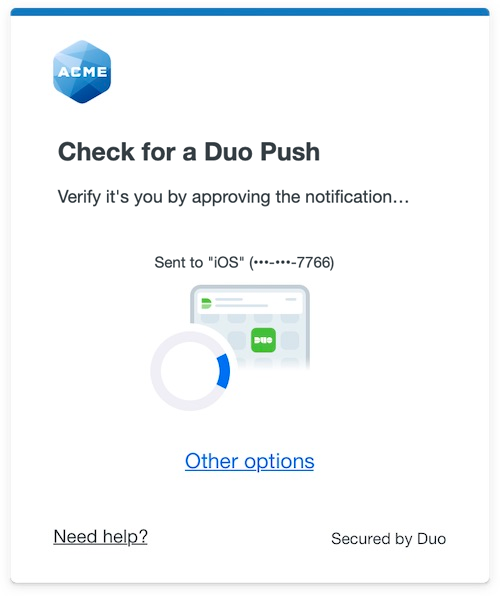 |
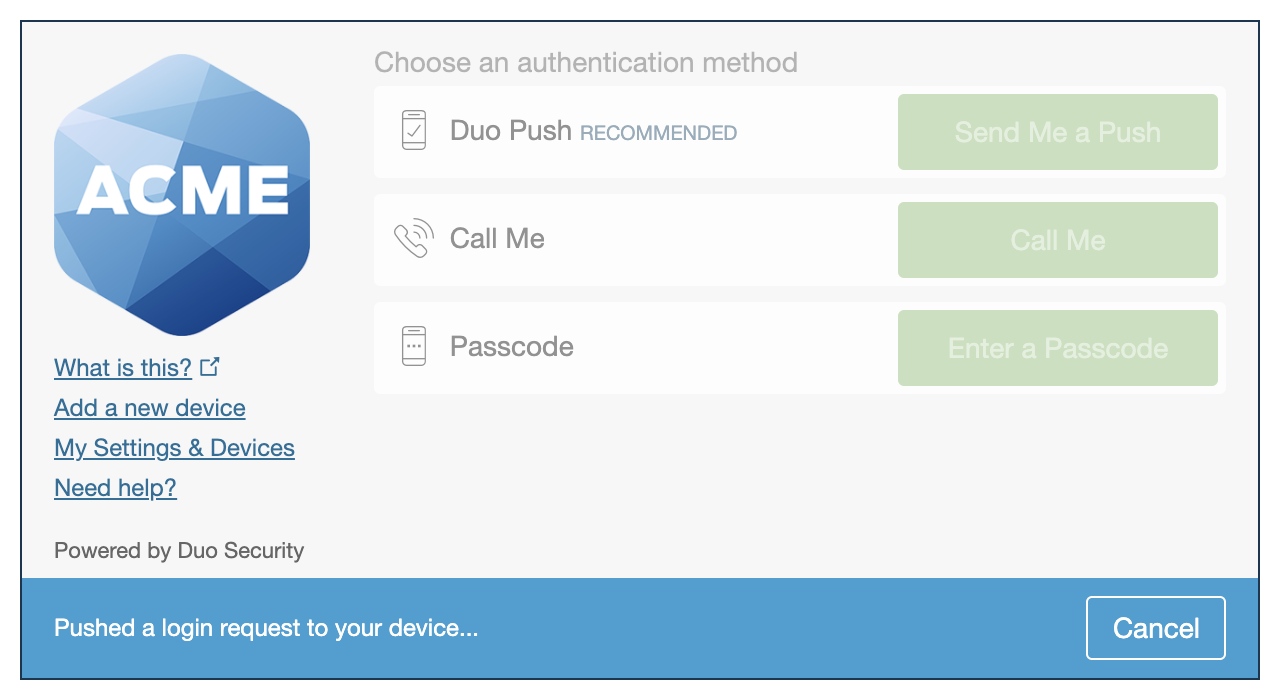 |
SailPoint has already updated their hosted Duo SailPoint Web application to support the Universal Prompt, so there's no installation effort required on your part to update the application itself. You can activate the Universal Prompt experience for existing Duo SailPoint Web applications from the Duo Admin Panel if the traditional prompt is still selected.
If you created your SailPoint Web application before March 2024, it's a good idea to read the Universal Prompt Update Guide for more information, about the update process and the new login experience for users, before you activate the Universal Prompt for your application.
New SailPoint Web Applications
When you configure Duo in SailPoint IdentityNow for the first time, you're ready to use the Universal Prompt. SailPoint Web applications created after March 2024 have the Universal Prompt activated by default. If you're configuring SailPoint Web now, proceed with the installation instructions in this document.
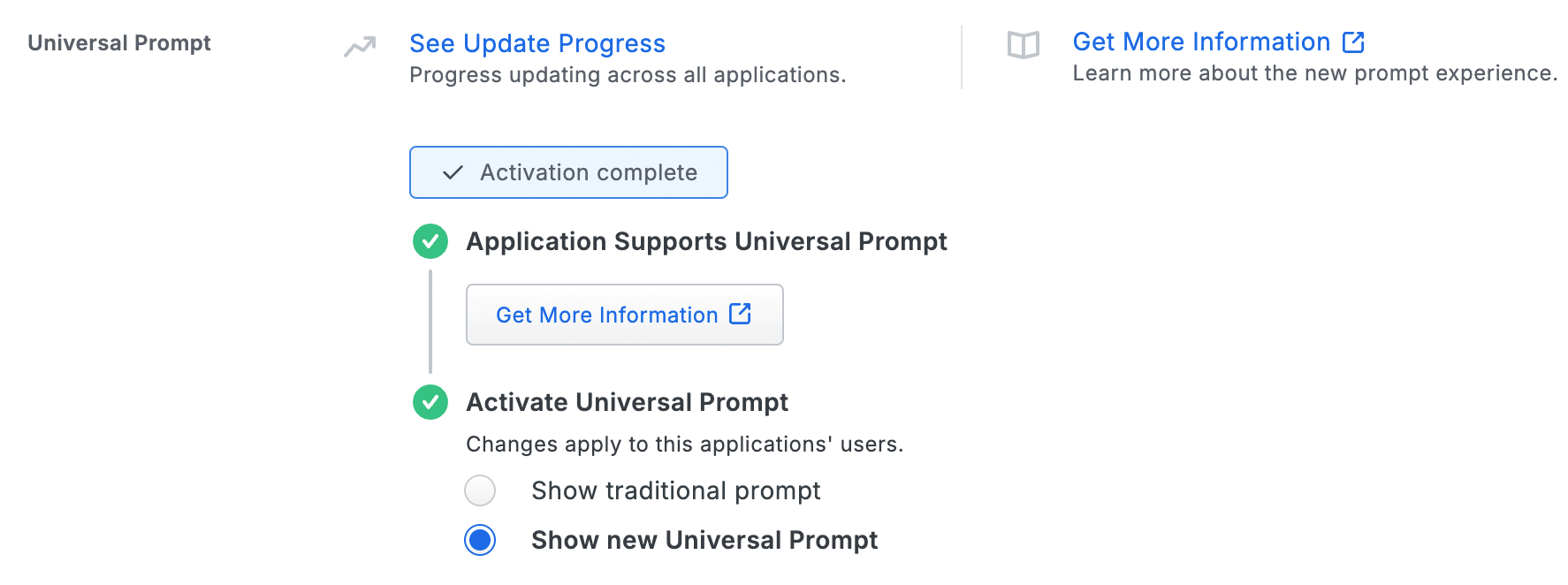
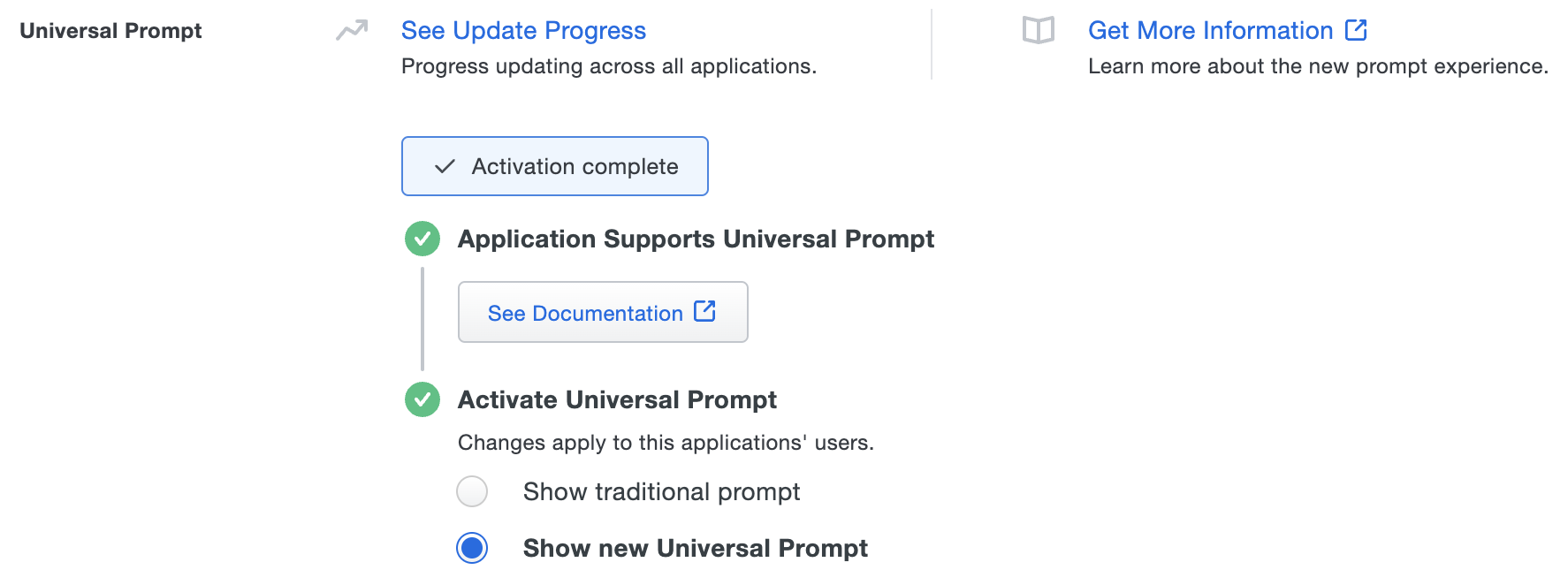
The "Universal Prompt" area of the application details page shows this application as "Activation complete", with these activation control options:
- Show traditional prompt: Your users experience Duo's traditional prompt via redirect when logging in to this application.
- Show new Universal Prompt: (Default) Your users experience the Universal Prompt via redirect when logging in to this application.
Existing SailPoint Web Applications
You don't need to make any changes in SailPoint IdentityNow to enable use of Duo Universal Prompt, because SailPoint already enabled use of frameless Duo authentication in their service.
Activate Universal Prompt
Activation of the Universal Prompt is a per-application change. Activating it for one application does not change the login experience for your other Duo applications.
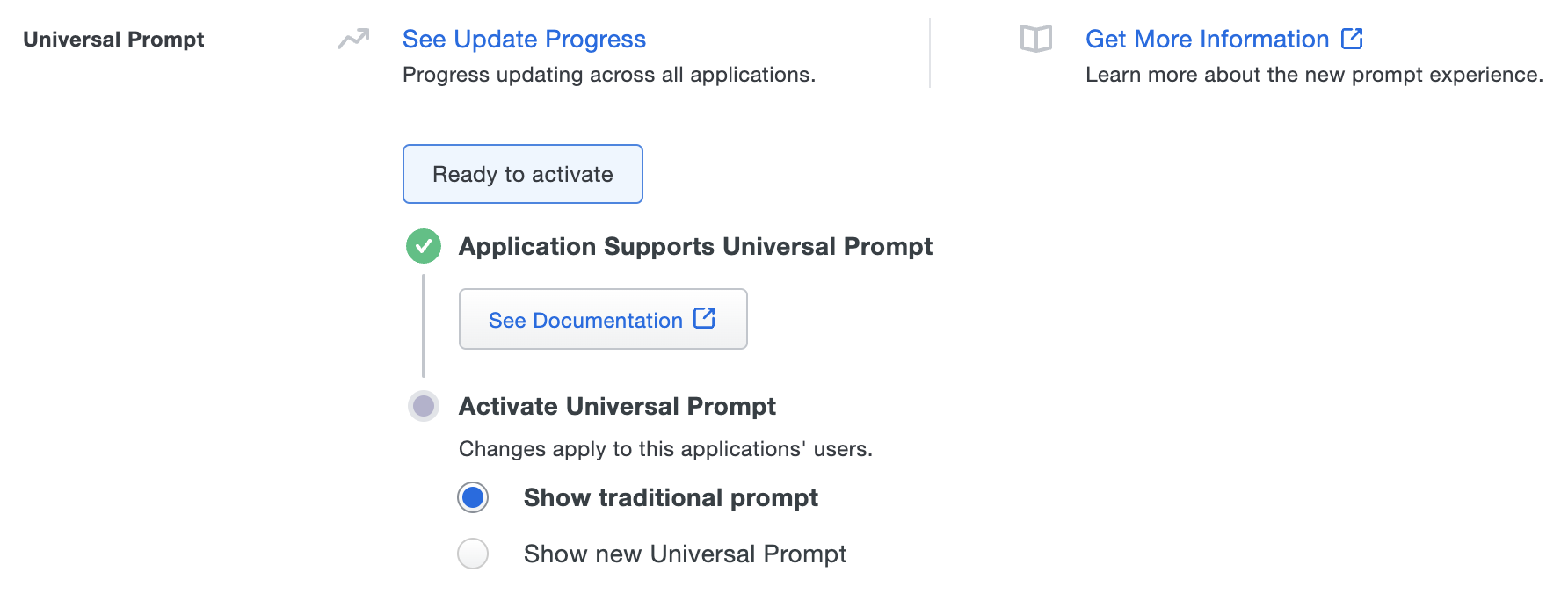
Once a user authenticates to the updated SailPoint IdentityNow, the "Universal Prompt" section of the SailPoint Web application page reflects this status as "Ready to activate", with these activation control options:
- Show traditional prompt: (Default) Your users experience Duo's traditional prompt when logging in to this application.
- Show new Universal Prompt: Your users experience the Universal Prompt via redirect when logging in to this application.
In addition, the "Integration key" and "Secret key" property labels for the application update to "Client ID" and "Client secret" respectively. The values for these properties remain the same.
Enable the Universal Prompt experience by selecting Show new Universal Prompt if the traditional prompt is still selected, and then scrolling to the bottom of the page to click Save.
Once you activate the Universal Prompt, the application's Universal Prompt status shows "Activation complete" here and on the Universal Prompt Update Progress report.
Should you ever want to roll back to the traditional prompt, you can return to this setting and change it back to Show traditional prompt. However, this will still deliver the Duo prompt via redirect, not in an iframe. Keep in mind that support for the traditional Duo prompt ended for the majority of applications in March 2024.
Universal Update Progress
Click the See Update Progress link to view the Universal Prompt Update Progress report. This report shows the update availability and migration progress for all your Duo applications. You can also activate the new prompt experience for multiple supported applications from the report page instead of visiting the individual details pages for each application.
Note this does not apply to the SailPoint API integration.
Best Practices
We recommend the following Duo policy settings to minimize potential 2FA bypass during IdentityNow self-service password reset and account unlock operations:
- Apply a New User policy set to Deny access to the SailPoint Web application. This prevents new user enrollment in Duo during password reset or account unlock.
- Do not apply an Authentication policy set to Bypass 2FA to the SailPoint Web application.
- Do not apply a User Location policy set to Allow access without 2FA to the SailPoint Web application.
- Do not apply a Remembered Devices policy to the SailPoint Web application.
- Do not apply an Authorized Networks policy set to Allow access without 2FA from these networks to the SailPoint Web application.
- Do not apply Bypass status to Duo users who will access the SailPoint Web application.
- Do not apply Bypass status to Duo groups containing users who will access the SailPoint Web application.
Configure the Duo Web Integration in IdentityNow
Refer to the Duo Web Integration Guide on the SailPoint Identity Services documentation site. Follow the directions to configure Duo 2FA verification for password reset in your IdentityNow environment.
When configuring your verification methods, ensure that another verification method must be satisfied before the Duo method is used.
Grant Access to Users
If you did not already grant user access to the Duo users you want to use this application be sure to do that before inviting or requiring them to log in with Duo.
Troubleshooting
Need some help? Reach out to Duo Support for assistance with creating the SailPoint application in Duo, enrolling users in Duo, Duo policy questions, or Duo authentication approval issues. For assistance configuring or managing IdentityNow, please contact SailPoint Support.
