Upgrade your security, lower your costs
Duo vs. Traditional Two‑Factor
Technology has evolved. But old two-factor solutions have not - they were created for the client-server computing model of the 1980s-90s. With that comes a long list of upfront hardware, software, installation, maintenance and management costs.
But technology has evolved over the past twenty to thirty years, meaning new security threats have evolved too.
Ready to Get Started?
Try out Duo Access for 30 days to experience Trusted Access.
Start a Free TrialDuo's lightweight, cloud-based two-factor solution is designed to protect against threats in the modern era while eliminating costs and providing greater security value.
Traditional Two-Factor AuthenticationClient-Server Era
|
 Modern Era |
|
|---|---|---|
| Security Drivers | Compliance | Risk management |
| Who to Protect | Percentage of all employees | All stakeholders |
| What to Protect | A few apps | Dozens to 100s of apps |
| Deployment Time | Months to years | Days to weeks |
| End Users | Users are expected to comply | User freedom |
| Cost Structure | Capital & service-intensive | Low touch and pay-as-you-go |
Why Choose Duo?
Why you should choose Duo over other outdated two-factor solutions:
Lower total cost of ownership (TCO)
Duo's TCO is 60% lower than traditional solutions.*
There’s no need to worry about hardware, software, high availability or backup costs, token-related expenses or data center maintenance. As a cloud-based solution, Duo covers hosting costs and saves you help desk, training and productivity time. Transparent pricing means no hidden costs or creep-up fees.
* Replacing RSA SecurID: Why Are Customers Switching to Duo Security?

Easy to Manage
Hassle-free deployment without overhead.
Easy, straight-forward application integration makes deployment a breeze - taking just days or weeks instead of months or years. Duo’s engineering team rolls out frequent, automatic updates to keep up with evolving technology and security needs, while Duo’s full-time, in-house support staff is responsive and always committed to providing the best possible customer experience.
Easy For Users
If your users don’t use it, then you’re not secure.
Duo knows usability is key to security. That’s why Duo makes it easy for your users to log in quickly and securely with a free mobile app, letting them verify their identities by approving a push notification. No tokens, no hassle - with a ton of other supported authentication methods for every user.
See how easy it is to authenticate with Duo Push.
Secure by Design
Built-in security, modern technology.
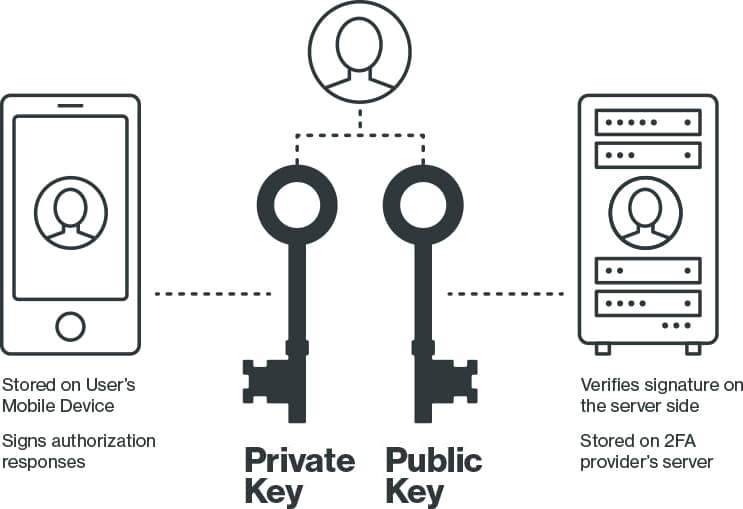
Some two-factor solutions rely on shared secrets to generate token numbers, which attackers can steal and use to compromise organizations. Duo’s solution uses asymmetric cryptography, keeping only the public key on our servers and storing private keys on your users’ devices in a tamper-proof secure element. Duo never stores your passwords - meaning your logins stay safe. Learn more about Duo’s Security and Reliability.
Plus, our frequent product updates means you’re always protected against the latest vulnerabilities, while other vendors may only update every six months.
Advanced Endpoint Security
Complete protection with Duo’s Trusted Access platform.
Evolving security threats require more than just two-factor authentication. For complete protection, Duo’s Trusted Access platform checks the security health of every device before granting them access to your applications. Admins can set policies to block users based on software versions, user location, network type and more to reduce exposure to risky devices.
Finally, Duo’s single sign-on (SSO) integrates security with the ease of logging in just once to access multiple cloud applications, letting you consolidate your authentication and identity solutions into one.

The Most Loved Company in Security
But don’t just take our word for it. Thousands of organizations worldwide trust Duo.
-
“The transition away from RSA has been very simple,” he said. “We’ve actually had people proactively shipping back their tokens. Duo is a great product with great service. That’s hard to come by these days.”
— Norman Bower, Information Security Engineer, Corporation Service Company -
“The process of applying Duo’s 2FA service was easily applied not only for our developers but also our daily administrators that are creating new user accounts for our partners. The ease of use, service flexibility, and responsiveness of their support team made a big difference in making our application that relies on 2FA successful.”
— Julie Dunn, NCFTA Team Lead, NCFTA -
I haven’t gotten a single complaint about it. Our overall experience with Duo has been extremely easy - that’s not something that always happens in the technology world.
— Tristan Hammond, IT Infrastructure Manager, Threadless -
Facebook is a very fast-paced environment and we needed technologies that would allow us to maintain that pace. Because of the ease of use of Duo Security and Yubico authentication technologies, we have seen minimal support and overhead costs. Other technologies didn’t fully support our need to allow multiple and rapid logins to SSH sessions.
— John “Four” Flynn, Information Security Manager, Facebook

Get the ultimate guide to comparing two-factor authentication solutions.
Gain insight on concrete criteria for evaluating technologies and vendors with Duo Security’s Two-Factor Evaluation Guide.
Download the Guide



