What is B2B identity management: what it is, how to use it?
In today’s digital business world, companies often work with outside partners, suppliers, and clients. These partnerships depend on secure access to shared systems and sensitive information.
In this environment, effective B2B IAM is essential. It provides the policies, processes, and technologies needed to authenticate and authorize outside entities. This helps ensure security, compliance, and efficiency.
What are B2B identities?
B2B identities are the digital credentials of businesses, partners, and contractors who interact with your organization and digital infrastructure.
Unlike regular identities, such as those of individual employees or customers, B2B identities generally focus on entities rather than individuals.
B2B Identity Management means the systems and processes used to securely verify, allow, and manage identities. This includes access permissions for people from outside organizations.
B2B IAM involves handling complex access requirements, ensuring secure collaboration, and maintaining compliance across networks.
Key differences between internal (employee) identities and B2B identities include:
Entity-based management: B2B user management often focuses on entire organizations rather than individual users. This requires handling a broader set of access permissions and roles that vary by organization.
Dynamic permissions: Access needs in B2B relationships can shift over time, depending on the nature of the collaboration. A supplier may need access to specific procurement systems during certain projects but not beyond that.
Cross-system interactions: Unlike regular user identity management, B2B identities must integrate across different IT environments, often involving multiple identity providers and platforms.
Compliance challenges: Businesses must comply with regulations that apply not only to their organization but also to their partners. Mismanagement of external identities can lead to legal risks and damage your business’ reputation.
Careful management of B2B IDs is important. It helps build trust and keeps data accurate in key business partnerships.
Who uses B2B identity management and why?
Efficient B2B identity management safeguards confidential information by providing customized access restrictions. It builds trust among companies, enabling secure and productive collaboration.
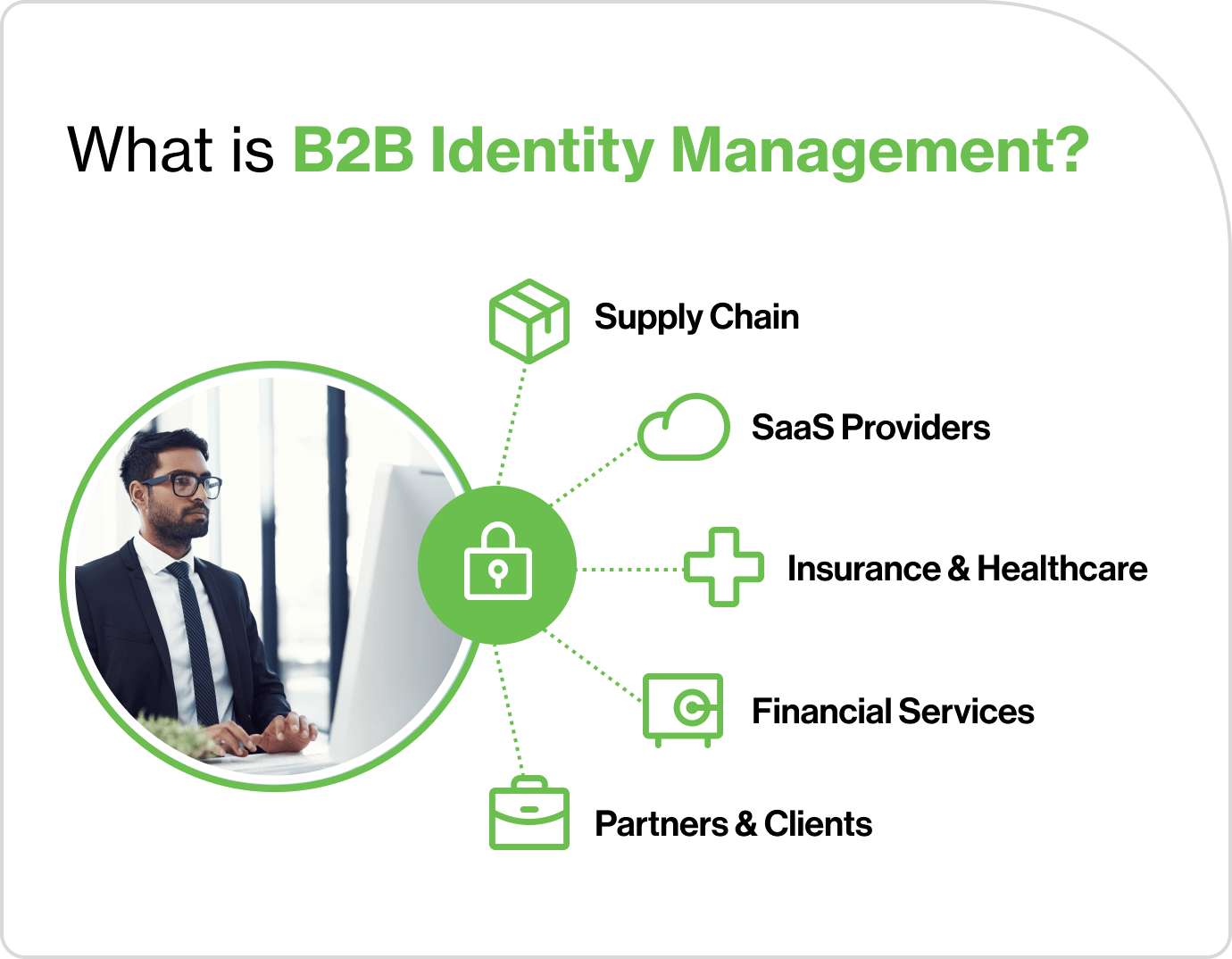
You can find B2B IAM in many industries, including:
Supply chain networks: Manufacturers, distributors, and retailers use B2B identity systems to share inventory data, track shipments, and coordinate orders. They also ensure data privacy.
SaaS providers: Software companies manage access to their platforms for multiple corporate clients, requiring robust user ID management to deliver personalized services.
Healthcare organizations: Hospitals and clinics coordinate with insurance providers, vendors, and research institutions - they have to use secure identity protocols to protect patient data.
Financial services: Banks and investment firms handle sensitive transactions involving third-party vendors, auditors, and regulators.
What are the benefits of B2B identity management?
If you want to improve your partner and supplier operations, having strong B2B identity management is a must.
The essential benefits of good B2B identity management practice include:
Enhanced security for sensitive data
A robust B2B identity management system controls exactly what can have to access critical resources and sensitive data.
You can reduce risk of breaches and data theft by using controls like:
Role-based access controls (RBAC)
Real-time monitoring
Streamlined collaboration with partners and vendors
B2B identity management simplifies onboarding and offboarding processes for external organizations, allowing companies to establish secure working relationships quickly. Automated workflows ensure partners and vendors can access the resources they need without unnecessary delays, improving productivity and fostering stronger partnerships.
Regulatory compliance across borders
With evolving regulations like GDPR, CCPA, HIPAA, and PCI DSS, organizations must demonstrate tight control over external data access. A good B2B identity management system helps companies stay compliant, which can be important for things like cybersecurity insurance. It does this by offering audit trails, monitoring tools, and policy enforcement that meet regulatory needs.
Efficiency and cost reduction
Manual user management of external identities is resource-intensive and prone to errors. When you automate identity management processes, it reduces administrative overhead, minimizes human errors, and ensures that resources are allocated where they’re needed most. This efficiency translates to lower costs and improved ROI.
Improved risk management and business continuity
B2B identity management systems help reduce risks. They do this by offering centralized oversight and strong access controls. This protects against insider threats and unauthorized access during security incidents.
In case of disruptions, these systems help keep the business running. They make sure that important operations are safe and available to the right people.
Scalability for growing business needs
As businesses grow and their ecosystems expand, managing external identities becomes increasingly complex. Scalable B2B identity solutions adapt to changing needs, supporting more partners, vendors, and third-party integrations without compromising security, functionality, or usability.
Strengthened trust and brand reputation
Secure identity management demonstrates to partners and clients that an organization takes cybersecurity seriously. This builds stronger, trusting relationships, and enhances your business’ reputation in its industry, ultimately driving business growth and loyalty.
By addressing these critical areas, B2B identity management not only mitigates risks but also creates opportunities for innovation, efficiency, and lasting partnerships.
Gameplan for B2B identity management adoption
To implement strong B2B identity security controls, you need a clear and organized plan. This plan should meet the business's needs while ensuring security and compliance.
Some steps successful organizations typically take in their B2B identity management journey include:
Define objectives and scope
Identify the key goals of the B2B identity management program, such as enhancing security, ensuring compliance, or improving partner collaboration.
Determine the scope, including which external partners, vendors, and systems will be included in the identity management framework.
Conduct a comprehensive risk assessment
Assess the current risks associated with external access to systems and data.
Identify problem areas, such as weak B2B authentication methods, orphaned accounts, or excessive permissions, which might expose sensitive resources.
Develop a governance policy
Establish clear policies for identity lifecycle management, including onboarding, role changes, and offboarding of external partners, suppliers, and clients.
Define who is responsible for managing user identities, monitoring access, and enforcing policies.
Choose a robust identity and access management (IAM) solution
Select an IAM platform designed for B2B environments with capabilities like:
Role-Based Access Control (RBAC) assigns specific permissions based on roles in partner companies. It also includes extra controls based on factors like location, device type, and time of access.
Federated Identity Management to allow seamless user authentication across multiple organizations using identity providers.
Automation for streamlining processes for onboarding, updating, and removing external users.
Implement Multi-Factor Authentication (MFA)
Require MFA for all external entities accessing sensitive systems or data.
Use methods like biometrics, one-time passcodes, or hardware tokens to enhance security.
Secure API integrations
Many B2B interactions involve system-to-system communication via APIs. Secure these connections via:
Using API gateways to manage and authenticate requests.
Applying token-based user authentication for external systems.
Regularly auditing API permissions to ensure compliance with access policies.
Establish monitoring and analytics
Implement real-time monitoring tools to track access patterns, detect anomalies, and flag suspicious activities.
Use analytics to identify trends and optimize identity management processes.
Train and engage stakeholders
Provide training for employees and external partners to ensure they understand how to use the identity management system securely.
Encourage open communication to address any challenges and ensure a smooth adoption process.
Integrate with zero-trust architecture
Align the B2B identity management program with a zero-trust framework, where no entity is inherently trusted.
Require continuous verification of identities and restrict access to only what is necessary for specific tasks.
Stay ahead of emerging trends
Keep an eye on new technologies like AI, machine learning, and blockchain. These tools will greatly improve B2B IAM in the coming years.
Stay informed about new regulatory requirements to ensure ongoing compliance.
Conclusion: B2B identity management a business enabler
B2B identity management is a cornerstone of secure and efficient business operations in the digital age. By understanding the unique needs of business partners, suppliers, and clients, organizations can build trust. They can also protect sensitive information and improve collaboration with partners by using strong identity-based security solutions.
As technology changes, keeping up with trends and facing new challenges will be important for staying competitive. Taking a forward-looking approach to B2B identity management is not just about security. It is also about promoting growth, innovation, and strong partnerships in our connected world.