What is Cloud Data Security? Best practices to use today
Organizations today rely heavily on cloud technology to innovate, scale, and grow their businesses. But for all the benefits of doing business in the cloud, defenders face a host of cloud-specific challenges to keeping their most sensitive data safe. Understanding and implementing strong cloud data security measures is essential to guard against devastating data breaches and costly compliance risks.
What is cloud data security?
Cloud data security includes all the cybersecurity measures that protect data. This data can be stored, processed, or sent in cloud and hosted IT environments.
It also includes many ways to protect digital assets. These measures keep data safe from unauthorized access, loss, or corruption.
Key components to cloud security include:
Data encryption
Compliance with regulatory frameworks
Leveraging these tools, organizations can maintain data integrity and confidentiality while using cloud services efficiently and effectively.
Cloud data security is not a one-size-fits-all concept to be sure. Different cloud models — public, private, and hybrid — each require tailored approaches to secure sensitive information.
Additionally, shared responsibility models in the cloud put some security duties on the service provider. The rest of these duties typically fall on the customer. Defenders must understand their organization’s responsibilities to keep data safe, no matter which cloud model is used.
As cloud adoption continues to grow, so too does the complexity of securing these environments. Security experts need to stay updated on new cloud threats and best practices, so we’ve provided a number of them here, from our experts.
How secure is data in the cloud?
This is a question nearly all security teams must confront. Data breaches and cyberattacks happen more often and are more advanced than before. A cloud security failure can have serious financial and reputational effects on most businesses.
In 2024, IBM’s 2024 cost of a data breach report, stated that the average global cost of a data breach was nearly $4.88 million, with impacts spanning lost customer trust, regulatory fines, and operational downtime.
Furthermore, regulatory compliance frameworks such:
Impose strict requirements on how cloud data must be protected. Not following these regulations can lead to serious penalties, especially for organizations in regulated industries like healthcare, finance, and retail.
By prioritizing cloud data security, organizations not only mitigate risks but also gain a competitive edge. Customers and partners are more likely to trust businesses that demonstrate proactive commitment to protecting sensitive information. Moreover, a secure cloud environment fosters innovation, allowing businesses to confidently adopt innovative technologies and services at scale.
Top security threats to data in the cloud
Data breaches: Unauthorized access to sensitive data remains the most significant threat. Attackers exploit vulnerabilities in cloud configurations or credentials to gain access. This often includes exploiting weak passwords, unpatched software, or poor access-control practices.
Insider threats: Rogue or disgruntled employees, partners, and contractors with access to critical systems can abuse their privileges to compromise data. Insider threats can also result from unintentional access errors and a lack of proper user training.
Misconfigurations: Badly designed cloud resources, like open storage buckets or unprotected servers, can accidentally show sensitive data to the public. These mistakes often happen because users do not have enough knowledge of cloud platform design and network setup.
Phishing and social engineering: Cybercriminals often target employees who have access to valuable cloud assets. They try to trick these employees into misusing their access or revealing their login details. Time and again social engineering attacks have proven effective against even the most advanced technical defenses.
Advanced persistent threats (APTs): These long and complex cyberattacks involve attackers who stay in important systems for a long time. They gather data slowly and steadily, making it hard to notice. APTs typically target high-value organizations with the most critical — and valuable — data to steal.
Lack of visibility and control: The cloud's distributed nature can create gaps in security monitoring, leaving cloud-based vulnerabilities hidden and unaddressed. Without proper visibility, organizations often miss the indicators of compromise that are the hallmarks of a breach.
Denial of service (DoS) attacks: The best, proactive cloud-security strategies includeOverwhelming cloud servers with traffic can disrupt business operations and potentially lead to data loss. Mitigating these attacks requires robust infrastructure and well-crafted, frequently tested incident response plans.
Best practices for securing critical cloud data
With an ever-expanding list of potential threats, organizations need comprehensive strategies to safeguard their cloud environments. These approaches should focus on fixing technical problems, improving user behavior, and following regulations. This will help build a strong, multi-layer defense against data breaches and other risks.
The best, proactive cloud-security strategies include:
Employ end-to-end data encryption: Using encryption helps protect data. It secures information both when it is stored and when it is sent. This makes it much harder for attackers to access sensitive information. A reminder, however: this approach also requires organizations to securely manage their encryption keys.
Implement strong access controls: The principle of least privilege (PoLP) means that users and systems get only the access they really need. A least-privilege strategy minimizes potential impact should accounts be compromised.
Conduct regular audits: Routine security and privacy assessments will identify and address vulnerabilities in the cloud infrastructure. Audits should cover both technical and procedural aspects of cloud security.
Leverage cloud-native security tools: Cloud service providers offer built-in security tools. These tools are great for monitoring, detecting threats, and ensuring compliance. These purpose-built cloud security tools integrate seamlessly with the platform and provide advanced data and systems defense capabilities.
Backup and test data regularly: Maintaining secure cloud data backups — and testing recovery mechanisms from those backups — ensures ongoing data integrity and availability even when production systems fail.
Automated backup solutions can help streamline the Business Continuity and Disaster Recovery (BCDR) process easier. They also reduce the risk of human error during backup and recovery.Educate employees: Ongoing training on cloud cybersecurity best practices helps reduce human error. This training teaches employees about risks like phishing, weak passwords, and mishandling sensitive data. Understanding these risks is important for protecting critical cloud assets.
Implement cloud-specific network segmentation: Dividing hosted network assets into separate segments stops attackers from moving around. This helps protect sensitive assets and lowers the overall risk of attacks.
Though more complex than traditional on-premises network delineation, cloud segmentation typically relies on security automation to manage and restrict virtual network access.
Advanced identity security bolsters cloud security posture
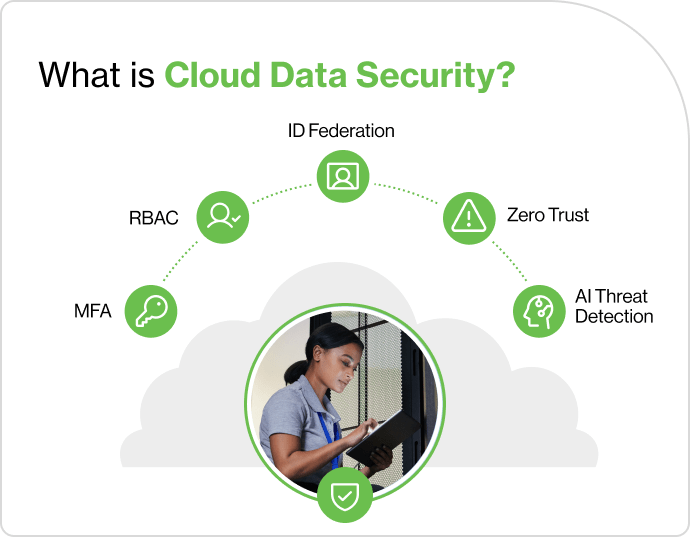
Identity security is now a cornerstone of robust cloud data protection strategies. This involves ensuring that only authenticated and authorized individuals or systems can access sensitive data. Among the top identity security practices in the cloud are:
Multi-factor authentication (MFA): Adding layers to the login process by requiring a combination of:
Something the user knows (ie. password)
Something they have (ie. a device)
Something they are (ie. biometric data)
MFA significantly reduces the risk of unauthorized access in cloud environments.
Learn more: What Is MFA and it’s business benefits
Role-Based Access Control (RBAC) assigns cloud data access based on job roles. This limits sensitive data exposure to those who don’t need it. RBAC simplifies cloud identity and access management. It also reduces the organization’s attack surface.
Identity federation: Streamlining user access across multiple systems with single sign-on (SSO) capabilities enhances user experience while maintaining strong security.
Zero-Trust architecture builds trust in users and devices. It does this through authentication and constant monitoring of access attempts. Custom security policies protect every application. This approach gives defenders a strong way to secure systems and lower risk.
AI-powered threat detection: Artificial intelligence can now handle identity security tasks. It monitors login patterns and finds unusual activity. This activity may show that cloud account credentials are compromised. The real-time insights that AI tools provide can help security teams prevent cloud data breaches before they escalate.
Robust, identity-focused cloud data security in practice
Businesses of all sizes are taking strong steps to protect their important digital assets in the cloud. Some examples include:
Large enterprise use case
A large, multinational financial institution focused on zero-trust principles as a way to strengthen its defenses across its entire cloud infrastructure.
By expanding its use of MFA and introducing AI-driven threat detection, the company mitigated risks to its hosted data assets from phishing attacks and insider threats.
This strategy not only enhanced data protection but also streamlined compliance with regulations such as GDPR and the Payment Card Industry Data Security Standard (PCI DSS). The implementation also reduced operational friction by automating access reviews and aligning security policies across departments.
Small and medium business use case
A mid-sized e-commerce company adopted identity federation and SSO to manage access across its various cloud-based applications.
With a lean IT department and no dedicated security team, this approach simplified user management and reduced login-related vulnerabilities.
The investment paid off when the company thwarted a phishing campaign targeting employee credentials.
The SMB used a subscription-based AI tool to spot unusual login behaviors. This helped improve its security without straining its limited resources.
Conclusion
Cloud data security is no longer optional for businesses serious about navigating the digital age safely and profitably. By understanding its importance, spotting potential threats, and using strong strategies, organizations can protect their assets. This includes advanced identity-security measures. These steps help ensure compliance and build trust with customers and stakeholders. No matter if you are a large company or a small business, taking action now can protect you from future cyber threats.
Cloud security is a continuous journey. As technology evolves and threats become more sophisticated, businesses must remain vigilant and adaptable. With the right strategies and tools, any organization can build strong cloud security and protect data while allowing for growth and innovation.
