Duo Two-Factor Authentication for Cisco VPNs - FAQ
Last updated:
When did direct LDAP support for Cisco ASA reach end of life?
Direct LDAP connectivity for Cisco ASA SSL VPN reached end of life on February 20. 2025. Please see the article Guide to end of life for the Duo LDAP cloud service (LDAPS) used to provide 2FA for Cisco ASA, Juniper Networks Secure Access, and Pulse Secure Connect Secure SSL VPN for further details.
What are the differences between the different Duo Cisco deployment configurations?
Please refer to the Duo & AnyConnect or Cisco Secure Client Overview to learn more about the different options for protecting ASA and Firepower VPN logins with Duo MFA.
You can also learn more in this knowledge base article which compares the ASA configurations.
The Duo "IPsec VPN Instructions" supports push, phone call, or passcode authentication and protects connections that use Cisco's desktop VPN client with IKE encryption instead of SSL VPN.
Can I use Universal Prompt with Cisco ASA or Firepower Remote Access?
Yes, via SAML 2.0 federation with Duo Single Sign-On. Please see the SAML configuration instructions for ASA or FTD.
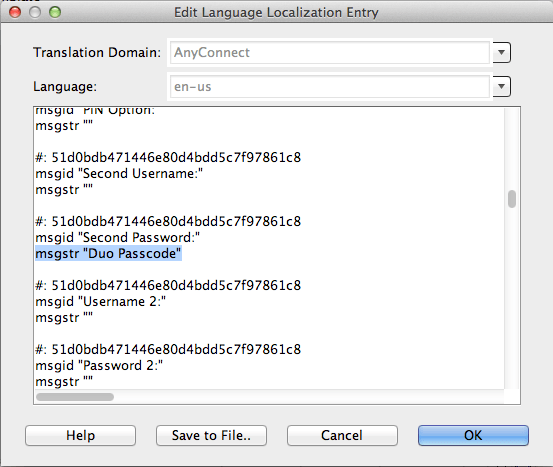
Can I customize the Cisco AnyConnect client "Second Password:" Field?
Yes, you can customize the Second Password Field by:
- From the Cisco ASDM select Network (Client) Access → AnyConnect Customization → GUI Text and Messages.
- Click Add and select the desired language that you would like to modify.
- Under msgid "Second Password" add the desired text to the msgstr "here" field
The customization is not updated until the client is restarted and makes another successful connection.
Is there any logging on the ASA to help troubleshoot authentication?
To monitor ASA activity during logon attempts, connect to your device using the ASDM utility and go to Monitoring → Logging → Real-Time Log Viewer. Set logging to a higher level (like "Debugging"" or "Informational") and click the View button. Then, attempt to authenticate again and watch the real-time log to see your authentication activity.
To view previously captured events, go to Monitoring → Logging → Log Buffer. Select a "Logging Level" and click the View button.
Can I use Duo to protect ASA local account logins?
To protect local ASA users with RADIUS in a Duo-only configuration, use the duo_only_client and radius_server_duo_only configurations in your Authentication Proxy setup, and again continue to use the "LOCAL" AAA Server Group for authentication and add the Duo RADIUS AAA server group for secondary authentication. In this scenario, your authproxy.cfg file would look something like this:
[duo_only_client]
[radius_server_duo_only]
ikey=DIXXXXXXXXXXXXXXXXXX
skey=XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
api_host=api-XXXXXXXX.duosecurity.com
failmode=safe
radius_ip_1=5.6.7.8
radius_secret_1=thisisaradiussecret
client=duo_only_clientWhy is the AnyConnect client connection attempt disconnecting after 12 seconds when I have increased the timeout?
An issue with the AnyConnect client causes it to ignore the timeout setting and use the 12 second default when the fully qualified host domain name (FQDN) of the Cisco ASA is not present in the AnyConnect client profile. This may cause the AnyConnect client to disconnect during the two-factor authentication attempt (Cisco forum link).
To fix this, add a <ServerList> section to the AnyConnect profile as shown in the example below. If your AnyConnect profile already contains a server list section, replace the <HostAddress> IP address or non-qualified host name of your ASA with the fully qualified domain name as shown in the example.
<ServerList>
<HostEntry>
<HostName>ASA-01
</HostName>
<HostAddress>asa-01.cisco.com
</HostAddress>
</HostEntry>
</ServerList>
See the instructions for using the ASDM AnyConnect Client Profile Editor and configuring the Server List at the Cisco site for more information.
While the Cisco forum link above references AnyConnect 2.x versions, the issue persists in later versions. AnyConnect version 4.8.02045, released in February 2020, increases the default timeout from 12 to 30 seconds. See the AnyConnect release notes for details.
Additional Troubleshooting
Need more help? Try searching our Cisco Knowledge Base articles or Community discussions. For further assistance, contact Support.
