Data Security: what it is, best practices
Data is the fuel that powers today’s hyperconnected, IT-centric businesses. Safeguarding all of that critical information is a strategic imperative. As cyber threats become more advanced and data breach costs rise, knowing the basics of data security is crucial. It can make the difference between success and failure for today’s organizations.
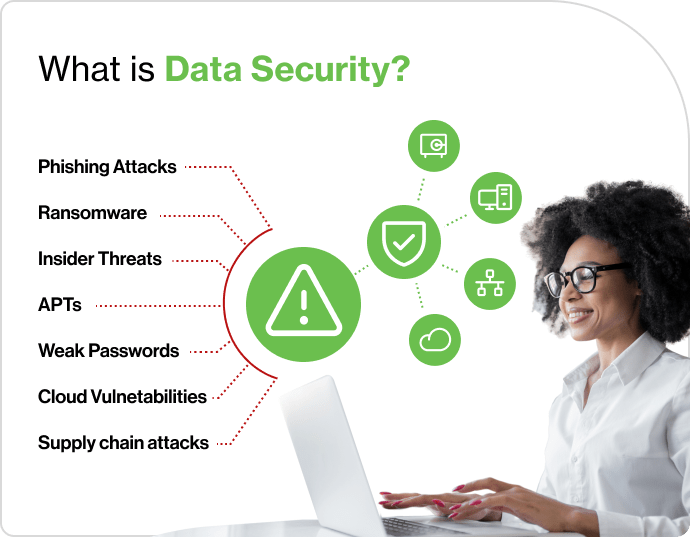
What is data security?
Data security includes all the steps and methods that organizations use to keep digital information safe from unauthorized access, corruption, or theft. This includes safeguarding sensitive data like customer records, intellectual property, financial information, and internal communications. Data security controls can range from encryption and access controls to broader strategies like zero-trust architecture.
The fundamentals of data security are rooted in what’s known as the CIA security triad , shorthand for data Confidentiality, Integrity, and Availability:
Confidentiality means that sensitive information is only available to authorized people.
Integrity focuses on keeping data accurate and consistent throughout its life.
Availability, along with data backup, makes sure information is easy to access when needed.
And the controls go beyond just digital systems. Physical security measures, such as securing servers in controlled environments and preventing unauthorized personnel from accessing hardware are key components of data security as well.
This integration of physical and digital security strategies is essential at a time when business data resides across distributed networks and in far-flung cloud environments.
Why is data security so important to modern business?
No matter the size, location, or vertical industry, businesses rely on well-protected data to maintain trust, comply with regulations, and safeguard their operations. Data breaches can wreak havoc on a business, causing financial losses, legal penalties, reputational damage, and lost competitive advantage. In highly regulated sectors like healthcare and finance in particular, the stakes are even higher thanks to stringent regulatory requirements and the sensitive nature of the data involved.
As businesses increasingly rely on digital platforms and remote workforces, the attack surface for cybercriminals has expanded. Protecting data isn’t just about prevention. It’s also about ensuring rapid detection and response to threats and attacks. Organizations need to view data security as a core element of their overall risk management strategy.
Global and regional regulations such as the General Data Protection Regulation (GDPR), the California Consumer Privacy Act (CCPA), and industry-specific standards like HIPAA (Health Insurance Portability and Accountability Act) underscore the importance of robust industry data security standards.
Failure to comply with these mandates can bring legal complications and heavy fines, making proactive data security measures an essential business function.
Top security threats to business data
Understanding the threat landscape is an essential first step to building effective data defenses. Common security threats include:
Phishing attacks: Cybercriminals use deceptive emails or messages to trick employees into revealing sensitive information or downloading malware. These attacks often brilliantly mimic trusted entities to snare even the most skeptical users.
Ransomware: Malicious software that encrypts data, rendering it inaccessible until a ransom is paid. This type of attack has grown exponentially in the past decade, targeting businesses of all sizes.
Insider threats: Disgruntled employees — past or present — with access to sensitive data often misuse their privileges sparking information theft and data leaks.
Advanced persistent threats (APTs): Sophisticated, long-term attacks targeting specific businesses to gain ongoing access to sensitive data. APTs often involve highly skilled nation-state attackers with lots of resources and advanced hacking tools.
Weak passwords and credential stuffing: The use of repeated, easily guessed passwords or the exploiting of stolen credentials to gain unauthorized access remains a major vulnerability for most organizations.
Cloud vulnerabilities: Misconfigurations or insufficient controls on cloud platforms that expose data to unauthorized users. Shared responsibility models require businesses to actively manage their security in cloud environments.
Supply chain attacks: Breaches sparked by vulnerabilities in systems connected to third-party vendors, partners, contractors, or suppliers frequently allow attackers to access the target organization’s critical business assets indirectly.
How to secure your critical business data
To build a strong data security framework, consider these best data-security practices:
Implement multi-layered security: Sometimes referred to as a defense-in-depth approach, creating a secure digital environment requires multiple layers of protection.
Firewalls can act as an initial barrier against unauthorized network access, while antivirus software identifies and removes malicious code and the endpoint.
Intrusion detection systems monitor for unusual activity that could signify a breach. Encryption ensures that even if data is intercepted, it remains unreadable to the attacker. Each corresponding security layer strengthens overall defenses, reducing vulnerabilities across all of the organization’s digital systems.Adopt a zero-trust model: As the name implies, a zero-trust approach assumes that no user or device is trustworthy by default. This model requires continuous verification, ensuring that every access request is scrutinized.
Policies lower the risk of insider threats and lateral movement in the network. This makes it harder for attackers to use stolen credentials.
Dig Deeper: How To Simplify Zero Trust Access Policies
Conduct regular security-awareness training for users: Employees are often the first point of attack — and the first line of defense — in the battle with cyber threats. Regular training sessions help end users recognize phishing emails, avoid downloading suspicious attachments, and adhere to security policies practices. Training empowers employees to act as vigilant defenders rather than unwitting victims, significantly reducing human-related security incidents.
Backup data often: Data backups are a vital safety net in the event of ransomware attacks or accidental information loss. Secure backups should be maintained in multiple locations, including offline storage to prevent tampering by attackers. And most important, regularly testing backups helps ensure they can be used effectively to restore data during emergencies, minimizing downtime and data loss.
Perform regular security audits: Routine audits do double duty; they identify weaknesses in your security infrastructure, and they attest to adherence with relevant regulations, such as PCI-DSS compliance. Regular security assessments provide insights into vulnerabilities that may have been overlooked and help refine existing security policies. Audits not only strengthen security but also demonstrate a commitment to best practices, which can bolster stakeholder trust.
Leverage endpoint protection: Modern workplaces rely on numerous endpoints, including laptops, mobile devices, tablets, and even unmanned and virtual machines. Endpoint protection tools monitor and secure all of these devices against potential threats while providing real-time insights into their activity. More advanced solutions like endpoint detection and response (EDR) can help quickly identify and mitigate cybersecurity issues before they escalate.
Establish and test incident response plans: A well-defined incident response plan outlines the steps to take during a security breach along with the chain of notification and a roster of responsible responding parties. IR plans are crafted to identify a breach, contain its spread, eradicate the threat, and recover affected systems. Clear roles and responsibilities ensure a coordinated effort, minimizing confusion and response times during the critical moments during and after an incident.
Identity security methods to improve data security
Identity security is the cornerstone of any robust data protection strategy. Identity controls include authentication, authorization, and access management, ensuring that only verified users can access sensitive data. When developing an overall data security program, consider these fundamental identity-focused security components:
Multi-Factor Authentication (MFA): Require users to verify their identity using multiple factors, such as a password along with a fingerprint or SMS code. MFA significantly reduces the risk of compromised credentials.
Single Sign-On (SSO): Simplifies authentication for employees while maintaining security through centralized identity management. This approach enhances user convenience and reduces password fatigue.
Behavioral biometrics: Analyzes user behaviors, like data-access time and locations, typing patterns, or navigation habits, to detect unusual activity and potential threats. Behavioral analysis provides a robust added layer of dynamic security.
Privileged access management (PAM): Limits and monitors access to critical systems for users with elevated permissions like executives and IT systems administration personnel. Enforcing least privilege access controls within a PAM schema helps minimize the risk of insider threats.
Identity governance: Implement tools to enforce compliance and track access permissions across the organization. Governance ensures alignment with regulatory standards and internal policies.
Use cases for robust, identity-focused data strategies
Businesses of all sizes and stripes are taking decisive action to protect and defend their most critical digital assets in the cloud. Some examples include:
Large business takes the bite out of phishing
A multinational corporation faced increasing phishing attacks targeting C-suite executives. By adopting an identity-focused strategy, including implementing MFA and PAM, they reduced unauthorized access attempts by 95% and successful attacks to zero.
The organization also used behavioral biometrics to monitor executives' account activity, ensuring early detection of anomalies. Additionally, the company deployed an AI-driven identity governance tool to automate permission reviews and improve operational efficiency.
Small business pairs security, ease-of-use
A regional accounting firm with limited IT resources implemented SSO and regular employee security awareness training to help secure client financial data. Despite being targeted in a phishing campaign, the firm’s use of MFA and secure backups prevented unauthorized access and ensured uninterrupted business continuity.
Beyond that, the accountants partnered with a managed security service provider (MSSP) to continuously monitor identity-related threats, giving them security scalability without overburdening meager internal resources.
Conclusion
Protecting business data is a non-negotiable aspect of operating in today’s digital-first environment. By understanding the threats to corporate data, adopting some security best practices, and implementing diligent identity security measures, your company can minimize risks and foster resilience against cyberattacks.
Think of data security not as a cost center, but as an investment in the business’s future. Staying proactive and flexible in the face of evolving data security threats truly lets your business thrive in the digital age.
