F5 BIG-IP APM with RADIUS and Duo Prompt
Last updated:
Action required by March 31, 2026 - Duo CA bundle expiration
Duo’s existing certificate authority (CA) pinning bundle will expire in 2026. Duo products that use certificate pinning, such as the Duo Authentication Proxy, require a software update for uninterrupted use after February 2, 2026. The final cutoff for legacy clients is March 31, 2026.
Check your Duo Authentication Proxy installations used for F5 BIG-IP RADIUS authentication and upgrade them if they are not running version 6.5.1 or later.
Please visit Duo Knowledge Base article 9451 for more information and guidance.
End of Support Information
The iframe-based traditional Duo Prompt in F5 BIG-IP RADIUS configurations reached its end of support on March 30, 2024. Customers must migrate to a supported Duo Single Sign-On application with Universal Prompt or a RADIUS configuration without the iframe for continued support from Duo.
We recommend you deploy F5 BIG-IP APM OIDC, which features Duo Universal Prompt support. Another option is to use Duo Single Sign-On with a generic SAML application to protect F5 BIG-IP with Duo Single Sign-On, our cloud-hosted identity provider featuring Duo Central and the Duo Universal Prompt.
Another alternative is to reconfigure your existing radius_server_iframe Duo Authentication Proxy application so that it does not use the iframe, for example, BIG-IP RADIUS with Auto Push Instructions.
Learn more about options for out-of-scope applications in the Universal Prompt update guide, and review the Duo End of Sale, Last Date of Support, and End of Life Policy.
The instructions for this solution were removed on April 2, 2025. Customers who had this configuration deployed before then and need to refer to the original instructions may contact Duo Support.
Troubleshooting
Need some help? Review troubleshooting tips for the Authentication Proxy and try the connectivity tool included with Duo Authentication Proxy 2.9.0 and later to discover and troubleshoot general connectivity issues.
Also take a look at the F5 BIG-IP Frequently Asked Questions (FAQ) page or try searching our F5 BIG-IP Knowledge Base articles or Community discussions. For further assistance, contact Support.
Network Diagram
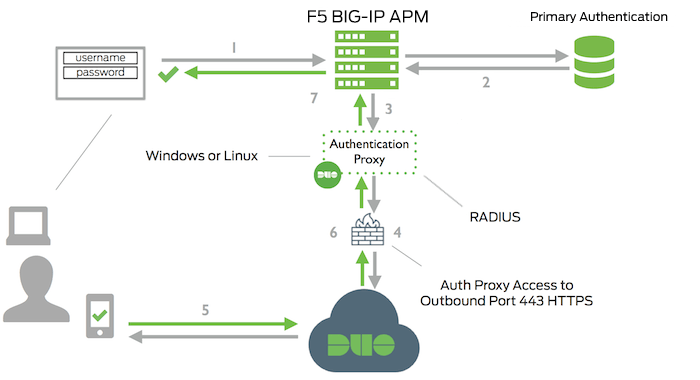
- Primary authentication initiated to F5 BIG-IP APM
- F5 BIG-IP APM verifies primary logon credentials with external directory using Active Directory or RADIUS
- F5 BIG-IP APN sends authentication request to Duo Security’s authentication proxy
- Duo authentication proxy connection established to Duo Security over TCP port 443
- User completes Duo two-factor authentication via the interactive web prompt served from Duo's service and their selected authentication factor.
- Duo Authentication Proxy receives authentication response
- F5 BIG-IP APM access granted
