Duo Access Gateway
Last updated:
Duo Access Gateway reached Last Day of Support on October 26, 2023 for Duo Essentials, Advantage, and Premier customers. As of that date, Duo Support may only assist with the migration of existing Duo Access Gateway applications to Duo Single Sign-On. Please see the Guide to Duo Access Gateway end of life for more details.
Learn more about Duo Single Sign-On, our cloud-hosted identity provider featuring Duo Central and the Duo Universal Prompt.
Overview
Duo Access Gateway is an on-premises solution that secures access to cloud applications with your users’ existing directory credentials (like Microsoft Active Directory or Google Workspace accounts) using the Security Assertion Markup Language (SAML) 2.0 authentication standard. SAML delegates authentication from a service provider to an identity provider, and is used for single sign-on (SSO) solutions.
Duo provides SAML connectors for enterprise cloud applications like Google Workspace, Amazon Web Services, Box, Salesforce and Microsoft Office 365. See the full list of named cloud applications here. We also offer a generic SAML application you can use with any SAML 2.0 service provider.
Protected cloud applications redirect your users to the Duo Access Gateway server on your network. Duo Access Gateway acts as a SAML identity provider (IdP), authenticating your users using your existing primary authentication source for credential verification, and then prompting for two-factor authentication before permitting access to the SAML application.
Duo Access Gateway is part of the Duo Premier, Duo Advantage, and Duo Essentials plans.
Duo Access Gateway supports local Active Directory (AD) and OpenLDAP directories as identity sources, as well as on-premises or cloud SAML IdPs.
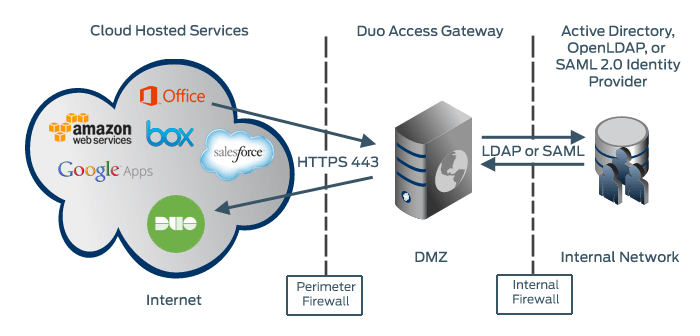
You can also use the Duo Access Gateway with Azure and Google directories or third-party IdPs hosted in the cloud.
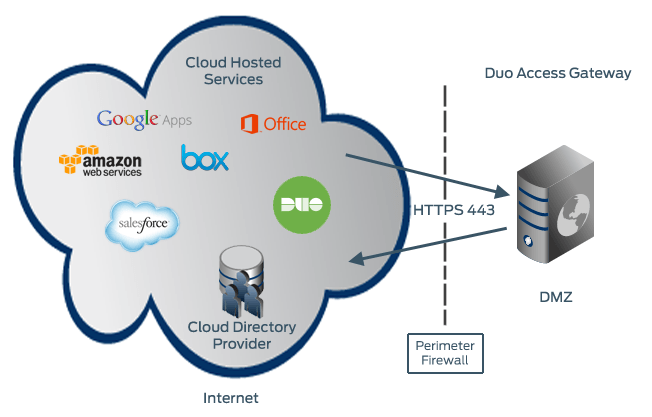
Define Duo policies that enforce unique controls for each individual SSO application. For example, you can require that Salesforce users complete two-factor authentication at every login, but only once every seven days when accessing Google Workspace. Duo checks the user, device, and network against an application's policy before allowing access to the application.
Once you deploy Duo Access Gateway with multiple service providers you can opt to minimize repeated Duo authentication prompts when switching between your SAML applications with shared remembered device policies for SSO.
Duo Access Gateway for Windows
Duo Access Gateway runs as an IIS virtual site on Windows Server 2016 and later. See the Duo Access Gateway Windows documentation for system requirements and installation instructions.
Duo Access Gateway for Linux
Duo Access Gateway runs in a Docker container on most modern Linux distributions. See the Duo Access Gateway Linux documentation for system requirements and installation instructions.
Duo Access Gateway and Universal Prompt
Duo's next-generation authentication experience, the Universal Prompt, provides a simplified and accessible Duo login experience for web-based applications, offering a redesigned visual interface with security and usability enhancements.
| Universal Prompt | Traditional Prompt |
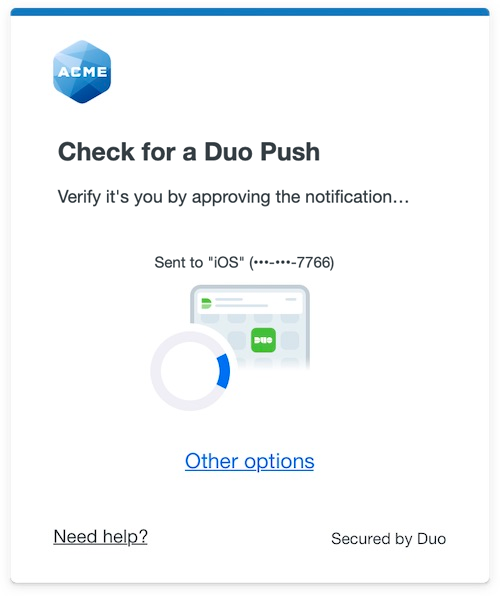 |
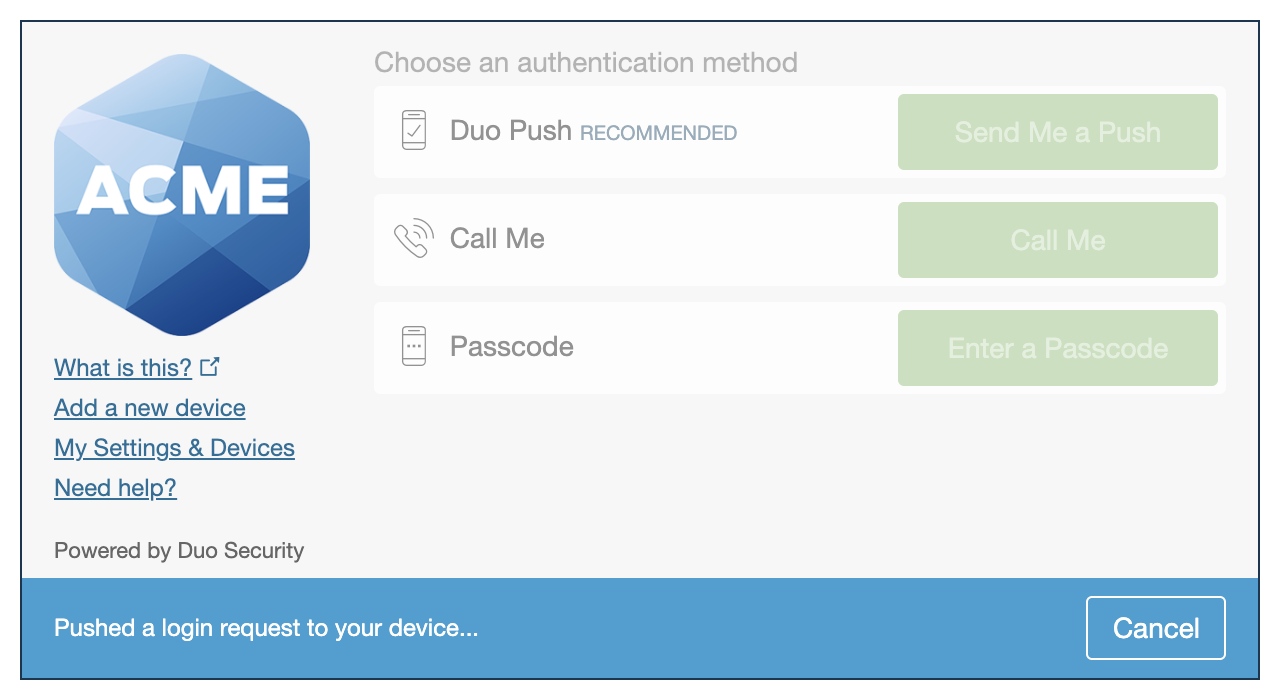 |
Duo is updating the login experience for our in-scope applications, and working with our technology partners to ensure they update their solutions for Universal Prompt as well.
With the general availability of Duo Single Sign-On, which includes support for the Duo Universal Prompt, we do not plan to release any additional enhancements to Duo Access Gateway, nor will we update Duo Access Gateway for the Universal Prompt. Review the list of applications excluded from the Universal Prompt update scope in the Universal Prompt Update Guide.
Consider deploying or migrating to Duo Single Sign-On today to future-proof your Duo experience and receive the latest updates.
