Identity Verification
Last updated:
Overview
To help protect organizations from the ever-growing threat of social engineering attacks, Duo integrates with Persona to offer integrated identity verification (IDV) workflows which provide high-assurance of user identities before allowing critical workforce user lifecycle actions in your organization.
Identity verification is part of the Duo Premier, Duo Advantage, and Duo Essentials plans.
Identity Verification Use Cases
The beta phase includes help desk verification and enrollment verification.
| Use Case | Description | Availability |
|---|---|---|
| Help Desk Verification | Verify the identity of users who contact your help desk for support. | General Availability |
| Remote Onboarding | Require that users complete identity verification before beginning Duo enrollment. | General Availability |
| Self-Service Account Recovery | Require that users complete identity verification to gain access to the Duo self-service portal (SSP). | Future; contact us to learn more |
Additional use-case support will follow in future releases.
How Duo Identity Verification Works
-
Duo’s cloud service sends the user’s first name, last name, and date of birth directly to your organization’s Persona tenant as part of the inquiry creation. These attributes are never transmitted via the end-user browser interaction.
-
Persona performs these pre-configured verification checks:
a. Extracted Properties: this ensures extraction of the first name, last name, and date of birth from the government ID to match against the attribute values for the Duo user.
b. Inquiry Comparison: this checks the user’s ID against the information provided at inquiry creation. This ensures the user who undergoes verification is the Duo user who requested verification.
Attribute Match Requirement First Name Match within 2 characters different, or matches commonly used nickname (Example: "Jim" -> "James" = match) Last Name 100% Match Date of Birth 100% Match
Do not disable these verification checks! This is critical to the efficacy of the verification. There may be other checks that you may need to enable or disable based on your organization’s needs and configuration, but be sure to leave the pre-configured checks intact.
If you decide to make changes to the configuration, please review Persona’s documentation and work directly with Persona to ensure your check configuration is advisable and secure before implementing them.
Timeouts
These pre-configured timeouts reduce the risk of social engineering attacks while allowing legitimate users enough time to complete a verification, including users who may depend on assistive technologies.
- Access codes for end-users to start a verification are valid for 5 minutes.
- Users have 20 minutes to complete a verification once they have started.
- The verification result will remain in the admin panel for 15 minutes before no longer displaying the most recent result.
Prerequisites
-
You must already have a Persona Essential, Growth, or Enterprise plan in place, with "Admin" role access to the Persona dashboard.
- Persona will load a Duo Identity Verification template with the recommended configuration into your account by request, which simplifies setup. Contact your Persona account team to request the Duo template before you begin the deployment steps.
-
You must have the Duo Owner or Administrator admin role to configure identity verification in the Duo Admin Panel.
-
Users who will perform identity verification must have access to a computer or mobile device with a camera.
Required User Attributes
Help Desk Verification
Help Desk identity verification requires that all users have an email address value stored in Duo. Users must also have this information available, which you can choose to store in Duo or in Persona during configuration.
- First name
- Last name
- Date of birth
Enrollment Verification
Enrollment verification requires the same attributes as Help Desk verification: first name, last name, and date of birth. Users new to Duo will receive an error and be blocked from enrolling in Duo if values for these attributes are not present in Duo or Persona when you have required identity verification in your enrollment policy.
- If you will store the attribute values in Persona: users new to Duo must exist in Persona with the required attributes populated.
- If you will store the attribute values in Duo: users new to Duo must exist in Duo with the required attributes populated.
This means that enrollment identity verification cannot support self-enrollment of users unknown to both Persona and Duo. This is different from Duo enrollment without identity verification, which will create the new user in Duo as part of the enrollment process.
Do not enable identity verification in your Duo global enrollment policy without creating your users in Persona or Duo with the required attribute information!
Persona User Attributes
If you plan to store the first name, last name, and date of birth information in Persona, you will need to identify a unique attribute in Persona to use as the user account identifier and match it to a corresponding user attribute in Duo during identity verification setup.
Duo User Attributes
If you choose to save user matching attributes in Duo, then you need these user attributes populated with values:
| Admin Panel Attribute | Admin API Parameter | Description |
|---|---|---|
| Email Address | email |
The user's email address. Not required for enrollment verification. |
| First Name | firstname |
The user's given name. |
| Last Name | lastname |
The user's surname or family name. |
| Date of Birth | date_of_birth |
The user's birthdate in the format YYYY-MM-DD. |
You can add these values for users using any of these methods:
- Manual edits in the Admin Panel.
- Import from an external directory as a synced attribute: Active Directory, Microsoft Entra, or OpenLDAP.
Configure Duo Identity Verification
Locate the Persona Inquiry Template ID for Duo
You must have requested the Duo template from Persona before proceeding. Contact your Persona account team if you do not see the template in your dashboard.
-
Log in to your organization's Persona dashboard as an administrator with the "Admin" role.
-
Navigate to Inquiries → Templates under the "Identity" section on the left of the dashboard.
-
Locate the "Duo Identity Verification" template and ensure the template has a "Last published at" timestamp. If not, select the template and click Publish in the upper right.
-
Keep the Persona dashboard open and proceed to the next section.
Enter the Persona Inquiry Template ID in Duo
-
In a new browser tab or window, log in to the Duo Admin Panel as an administrator with the Owner or Administrator admin role.
-
Navigate to Users → Identity Verification.
-
Return to the Persona dashboard browser tab or window and copy the "Duo Identity Verification" template ID by clicking on the clipboard icon next to the identifier.
-
Paste the copied template ID in the Inquiry template ID field in the "Set up IDV" section of the "User Identity Verification" page in the Duo Admin Panel.
-
Keep the Duo Admin Panel browser tab or window open as you will return to it shortly.
Create a Persona API Key
A Persona API key is necessary to enable communication with Duo.
-
Return to the Persona dashboard browser tab or window.
-
Navigate to API → API Keys under the "Developers" section on the left of the dashboard.
-
Click + Create API key in the upper right.
-
Give the new API key a descriptive name, such as "Duo Identity Verification". You can add a note with more information if desired.
-
Go to the "Permissions" tab and unselect default permissions until you have the Inquiries "Action" permission enabled.
-
Click Save in the upper right to create the new API key, and then click the Copy button to copy the API key to your clipboard.
If you need the key again in the future you can copy it from the "Overview" tab when editing the key’s properties, or from the list of all API keys.
Enter the Persona API Key in Duo
-
Return to the browser tab or window with the Duo Admin Panel "User Identity Verification" page open.
-
Paste the API key value you just copied from the Persona dashboard into the API key field in the "Set up IDV" section of the "User Identity Verification" page.
-
Click Save.
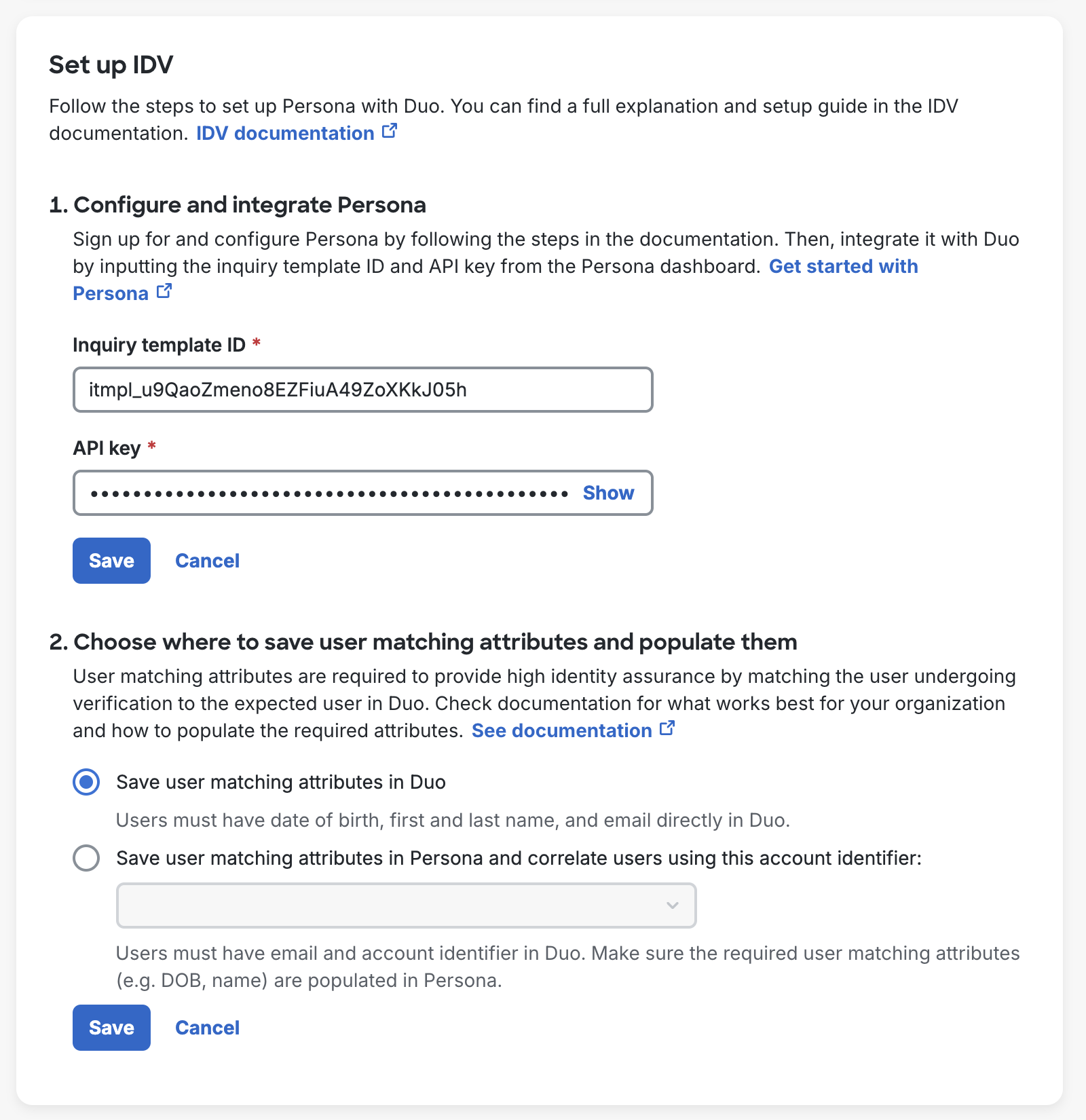
Select User Matching Attribute Location
-
Scroll down on the "User Identity Verification" page in the Duo Admin Panel to the "Set up IDV" section.
-
Choose an option:
-
Save user matching attributes in Duo - (Default) Users must have date of birth, first and last name, and email in Duo. See Duo User Attributes.
-
Save user matching attributes in Persona and correlate users using this account identifier - Type in the Persona attribute name to use as the account identifier corresponding to that user account’s “Reference ID” in Persona. If this attribute does not exist in Duo, click Add to create it.
If you select this option, you will also need the "Accounts" permission enabled for the Persona API key.
-
-
Click Save after making your selection.
Help Desk Identity Verification
Enable Help Desk Identity Verification for Users
After saving the Persona information you can choose to enable identity verification features for all your Duo users, or for select user groups.
-
Scroll down on the "User Identity Verification" page in the Duo Admin Panel to the "Enable IDV" section.
-
Choose an option for "Help desk-initiated identity verification":
- Disable it for all users - (Default) No users will have the identity verification action available for administrators.
- Enable it for specific groups of users - Members of the Duo groups you select will have the identity verification action available for administrators. Users must have the necessary attributes populated.
- Enable it for all users - All users with the necessary attributes populated will have the identity verification action available for administrators.

-
Click Save after making your selection.
You can return to this page in the future to make changes, such as expanding to additional groups or to switch from selected groups to all users.
Use Help Desk Verification
Once enabled, Duo administrators with the Owner, Administrator, User Manager, Help Desk, or Security Analyst admin roles can initiate identity verification for eligible users who have the necessary attributes populated with values.
-
Log in to the Duo Admin Panel and navigate to Users → Users in the left sidebar.
-
Select a user by clicking their username or use the search bar at the top to locate the user.
-
If the user has the necessary attributes populated and identity verification has been enabled then you'll see a Verify with government ID link in the top right of the user's details page.

If you don't see the link, verify the attribute values and that the help desk-initiated identity verification feature was enabled for all users or that the user is a member of a group enabled for verification.
-
Click Generate access code on the "Verify <user's name> with a government ID" page.
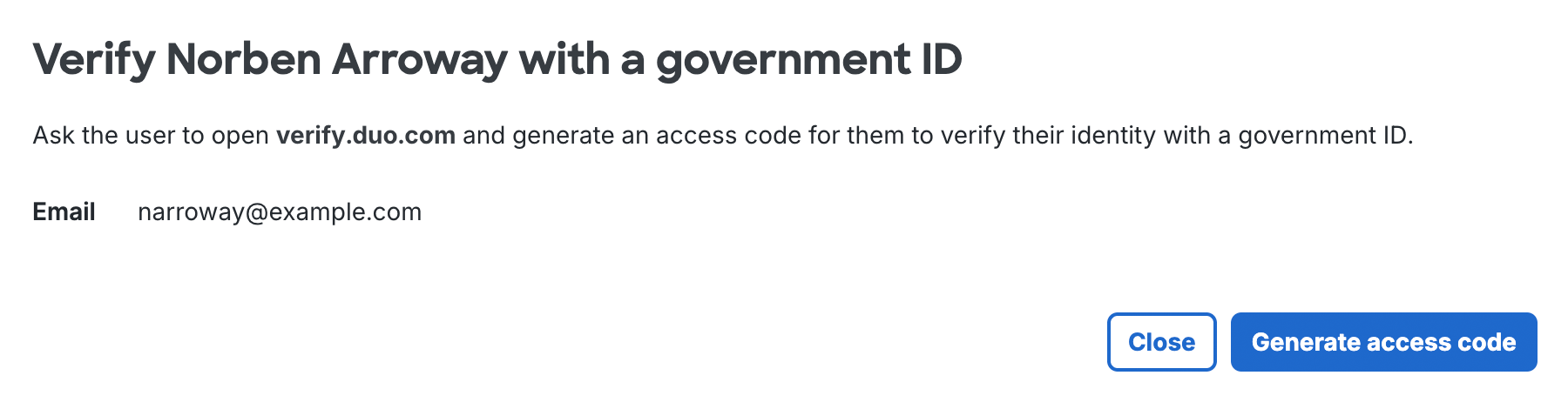
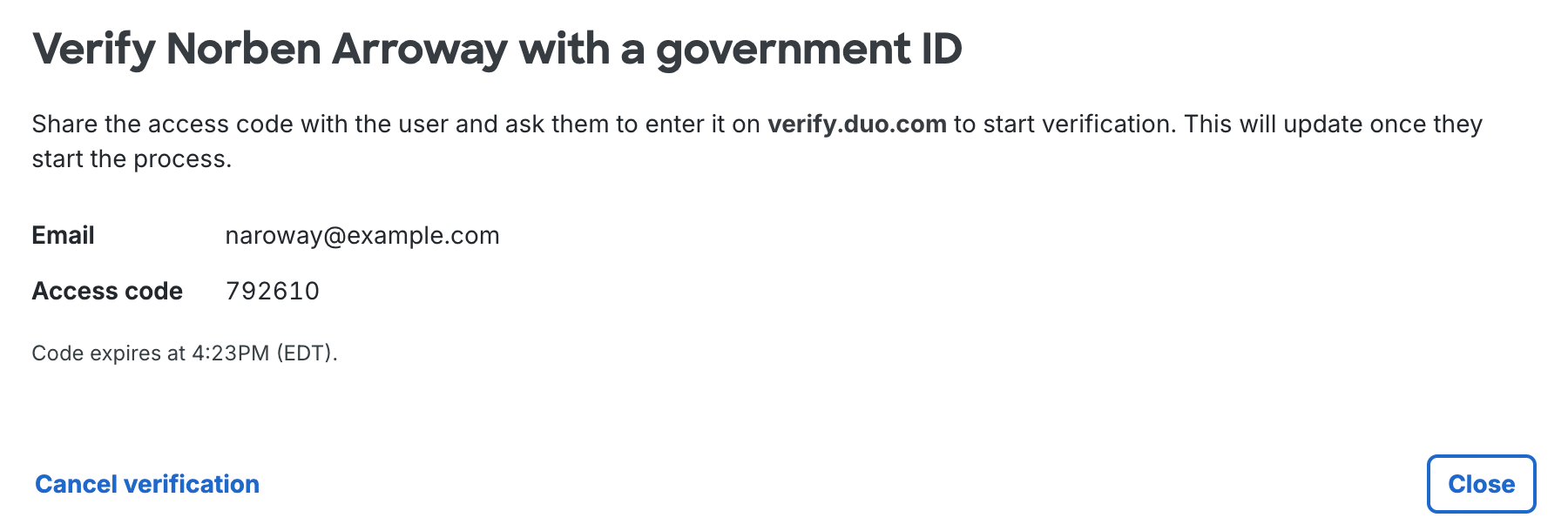
The access code is valid for five minutes. The user enters this access code in the Duo identity verification portal.
-
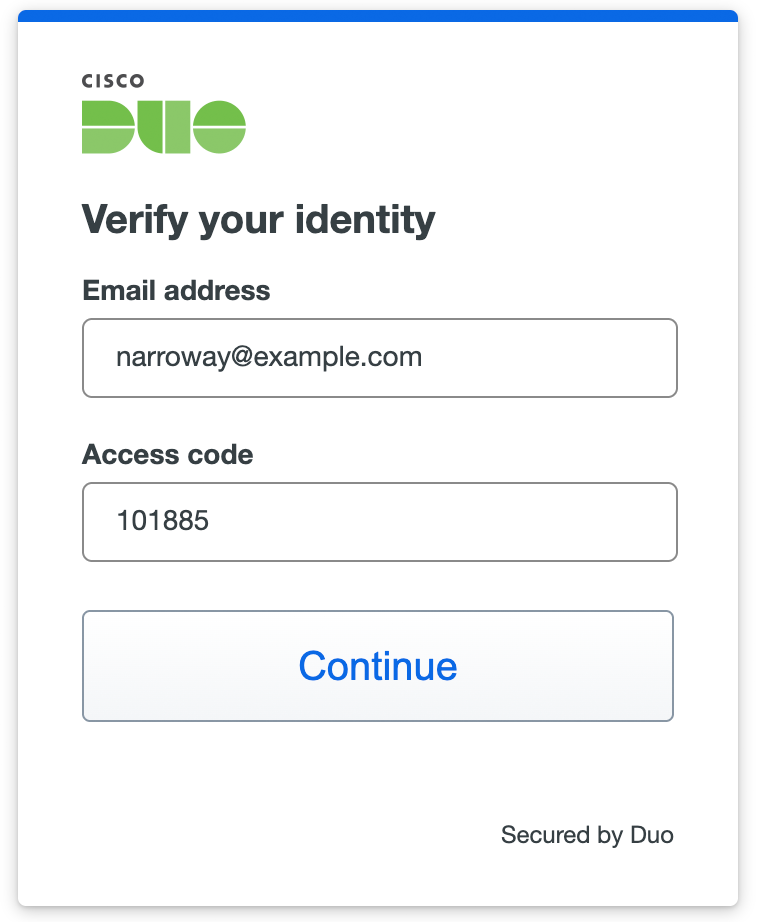
Instruct the user to open https://verify.duo.com in a desktop or mobile device browser, and then to enter the email address they use with Duo and the access code you generated in the Duo Admin Panel.
-
Once the user enters their email and access code, they'll click Verify with Persona, which redirects them to Persona to perform identity verification.
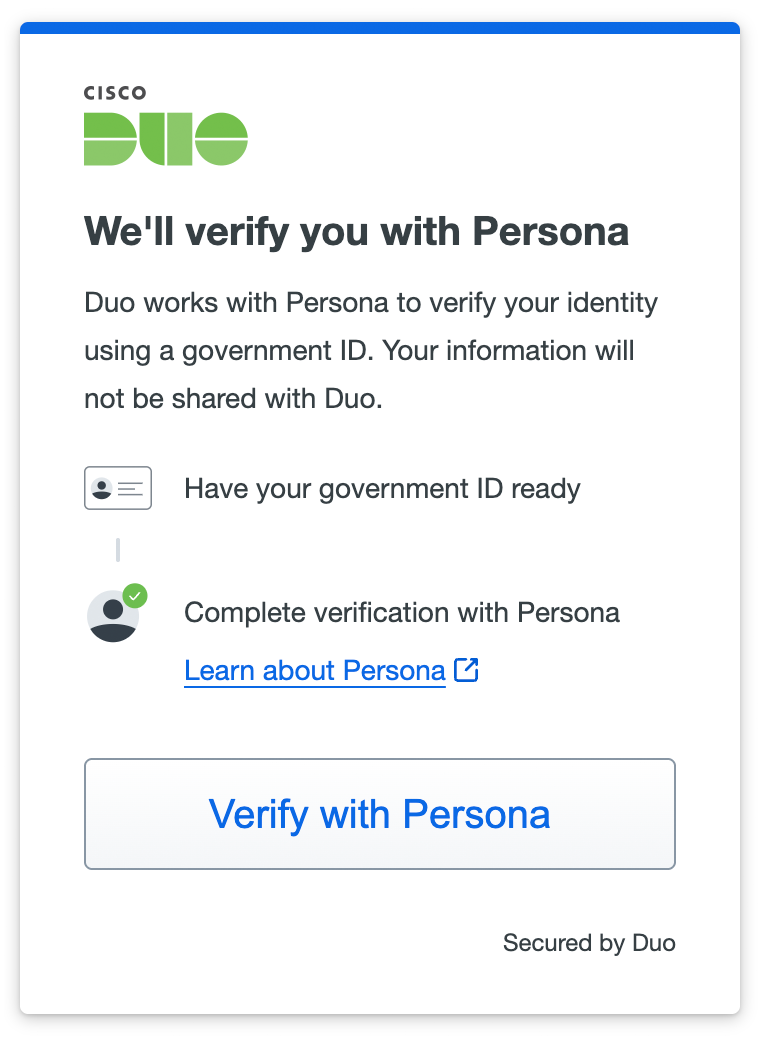
In the Duo Admin Panel, you'll see that the user has started the verification process.
-
At the Persona site, the user will step through the verification process. They will scan their choice of approved government-issued ID and perform facial recognition.
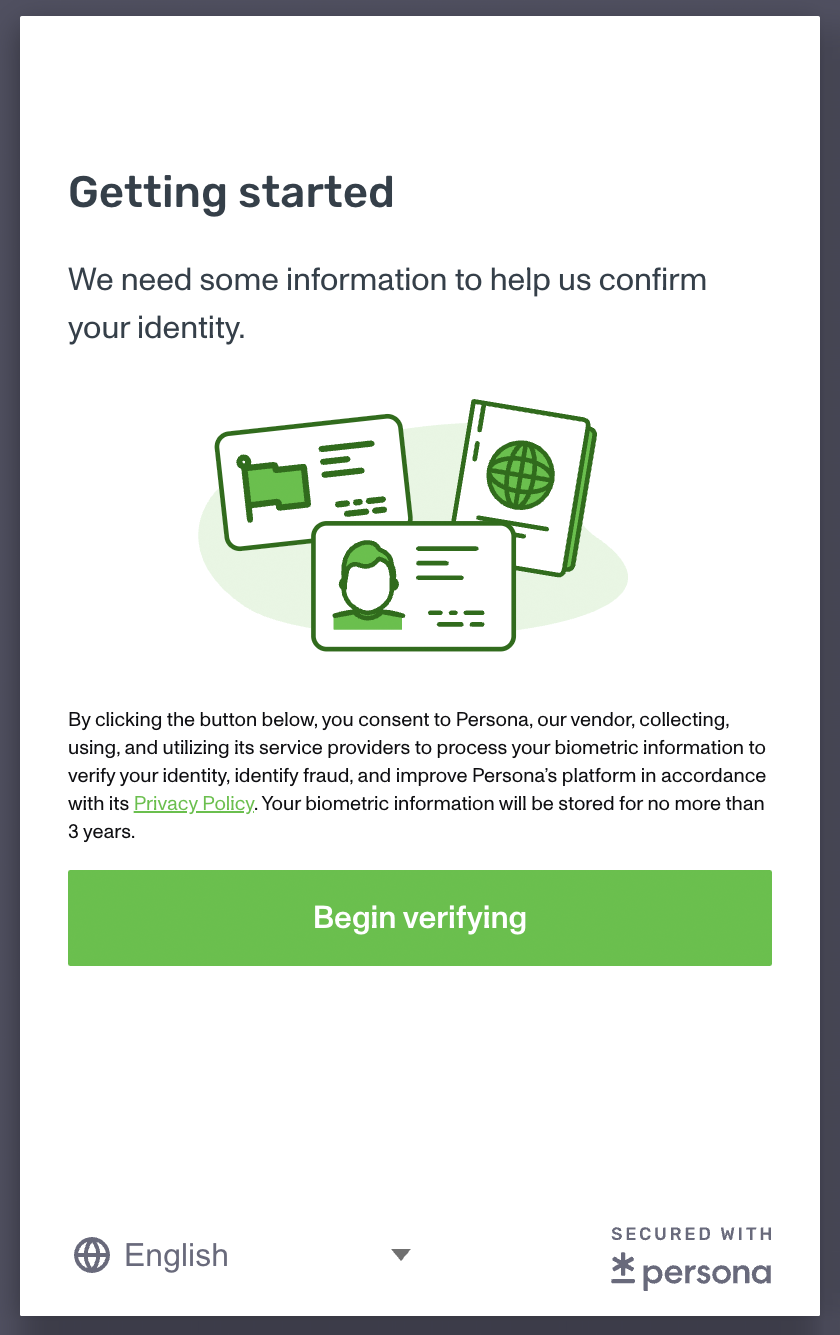
If the user accessed the identity verification portal from a device without a camera, they can click Continue on another device to receive a QR code to scan from a device with a camera and complete the verification process with that other device.
-
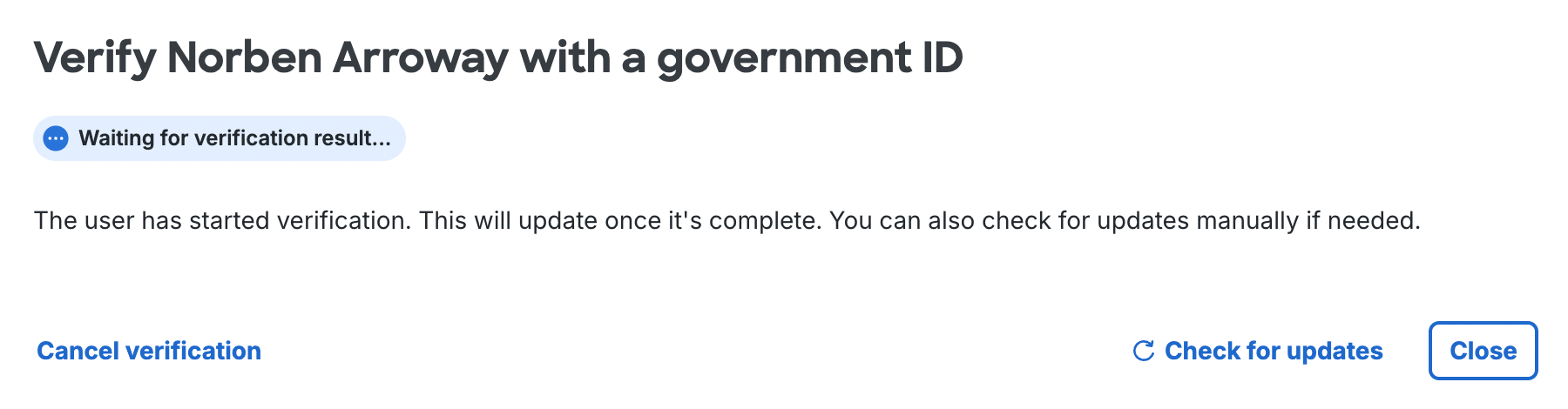
When the user informs you that identity verification completed successfully, click Check for updates on the "Verify <user's name> with a government ID" page in the Duo Admin Panel. You'll see the verification result.
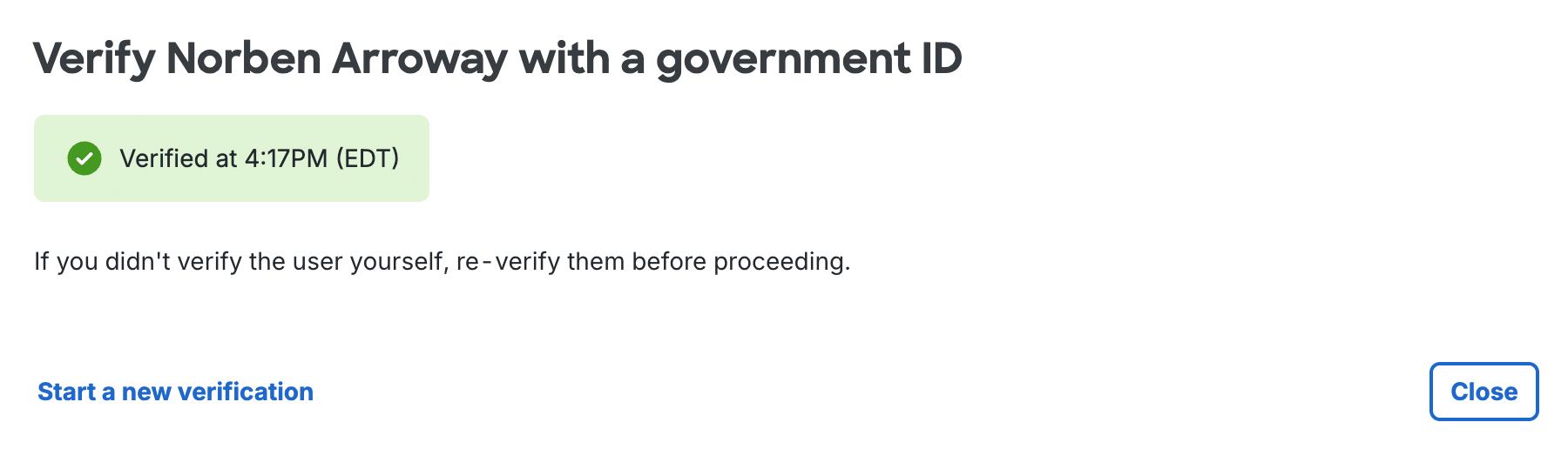
The verification result remains viewable for 15 minutes after completion.
Enrollment Identity Verification
Enable Enrollment Identity Verification for Users
Users must exist in either Persona or Duo with the required user attributes to complete enrollment with identity verification. Identity verification during enrollment will fail if users are missing from both Persona and Duo, or if they lack the required attribute values!
Once you complete the Persona configuration for identity verification you can require it as part of the Duo enrollment process. When a new user accesses the Duo enrollment portal, they will have to first complete verification of their government ID and identity with Persona before they can set a Duo password (if required) and enroll any Duo authentication methods for logging into protected applications.
Do not enable identity verification in your global enrollment policy unless you are certain that all new users who will need to complete Duo enrollment exist in Duo or Persona and have all the required user attributes populated.
You can control which new users will need to complete verification during enrollment with a group enrollment policy. This requires that you:
-
Create the new users in Duo without authentication devices. You can create them with directory sync import, bulk enrollment, or manual enrollment.
When you import or create the users, be sure to populate values for the required attributes: first name, last name, and date of birth.
-
Add the new users to a Duo group. If you imported the new users via directory sync, they are already members of the groups created by the sync process.
Next, create an enrollment policy with identity verification enabled:
-
Navigate in the Duo Admin Panel to the Policies → User Enrollment and Account Management page.
-
Click +Add policy.
-
Give the new enrollment policy a descriptive name.
-
Click Identity verification on the left, and then enable the Require identity verification before user enrollment option.
-
Click Create policy
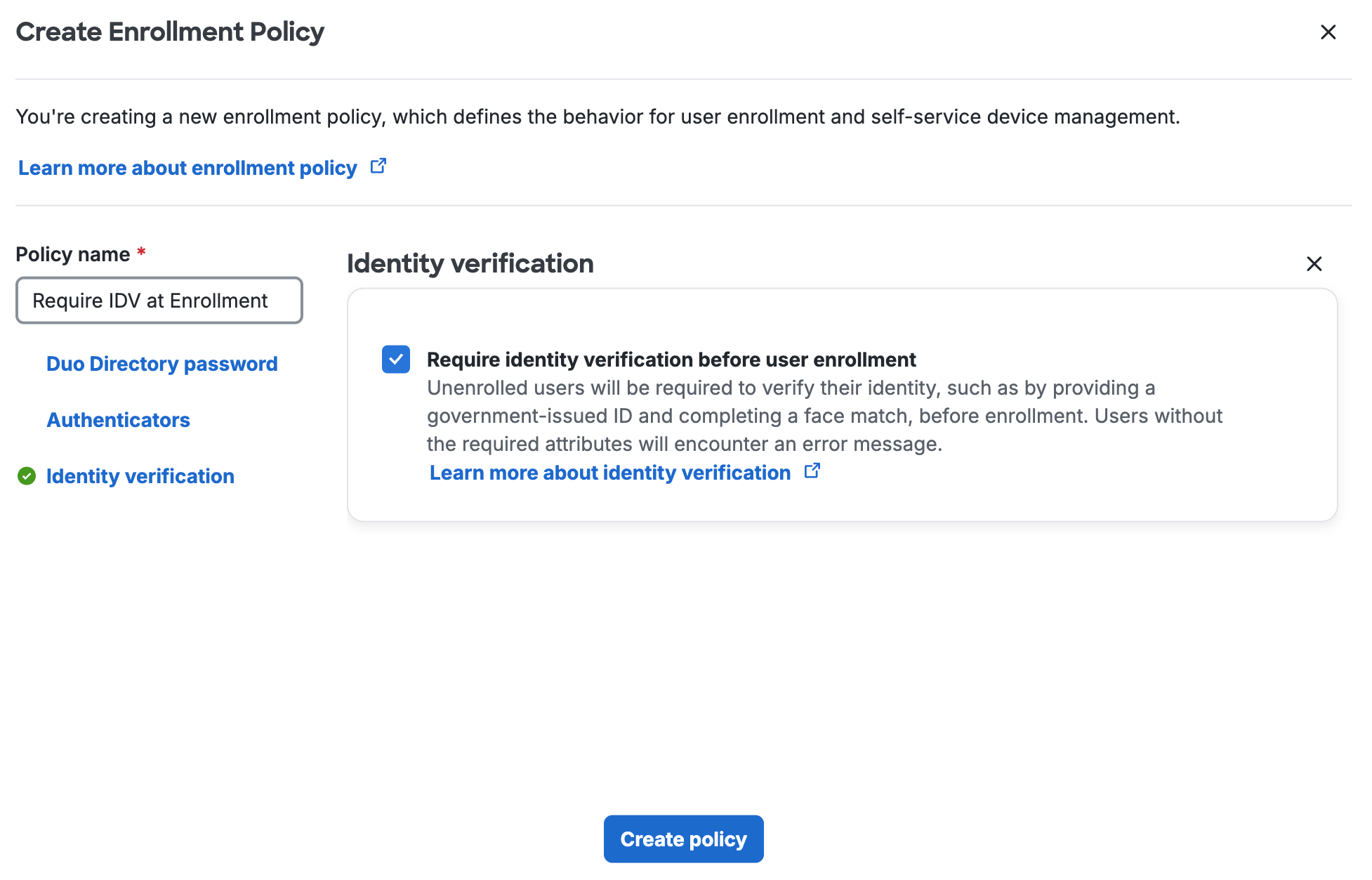
Then, assign the new enrollment policy to the Duo group that contains the new users you want to complete identity verification before Duo enrollment.
-
On the "User Enrollment and Account Management" page, scroll down to the "User Group Enrollment Policy" section and click Apply user group policy.
-
Select the enrollment policy with identity verification you created with the Policy drop-down, and also select the target group or groups with the Groups selector. Click Apply Policy.
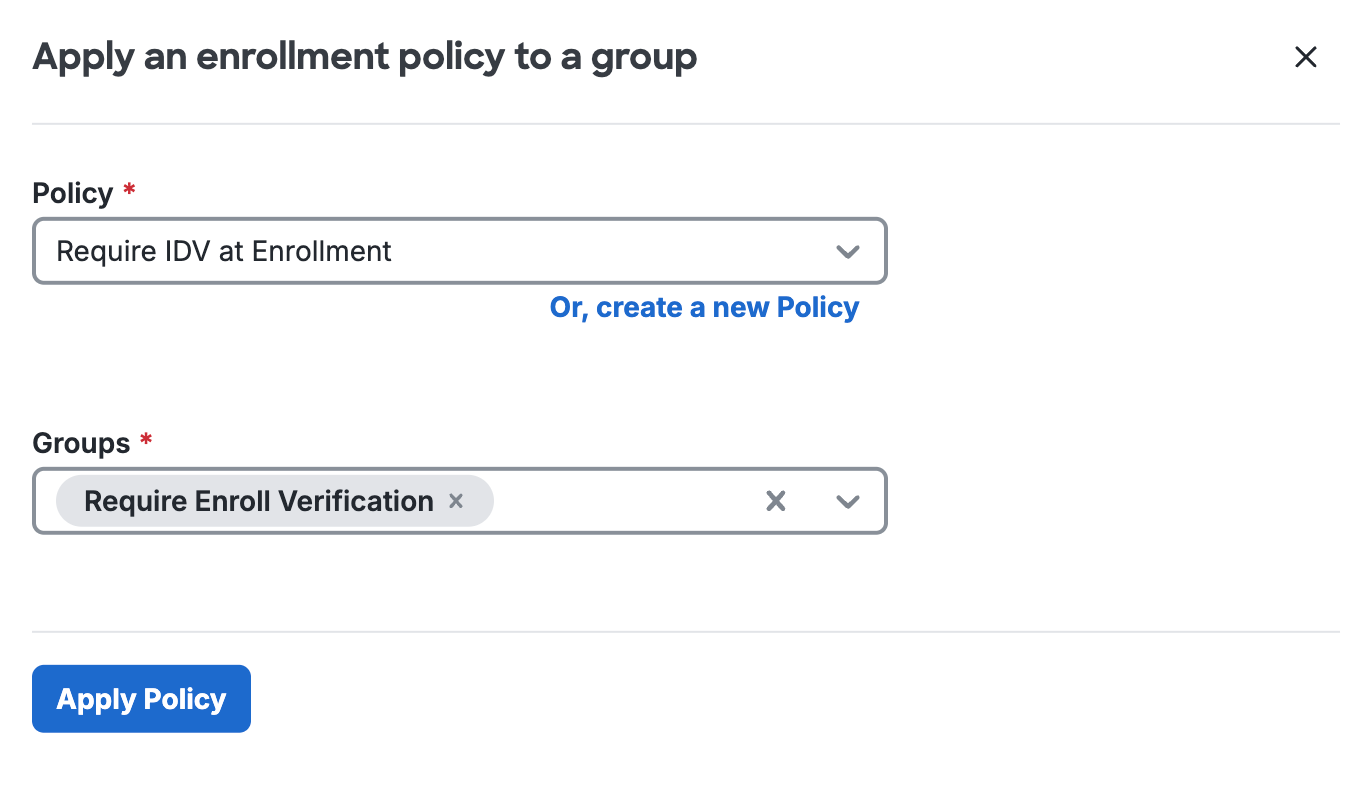
-
The "User Group Enrollment Policy" table shows the new policy assignment. You can use the Move up and Move down controls to rearrange your enrollment policies to your preferred order of precedence.
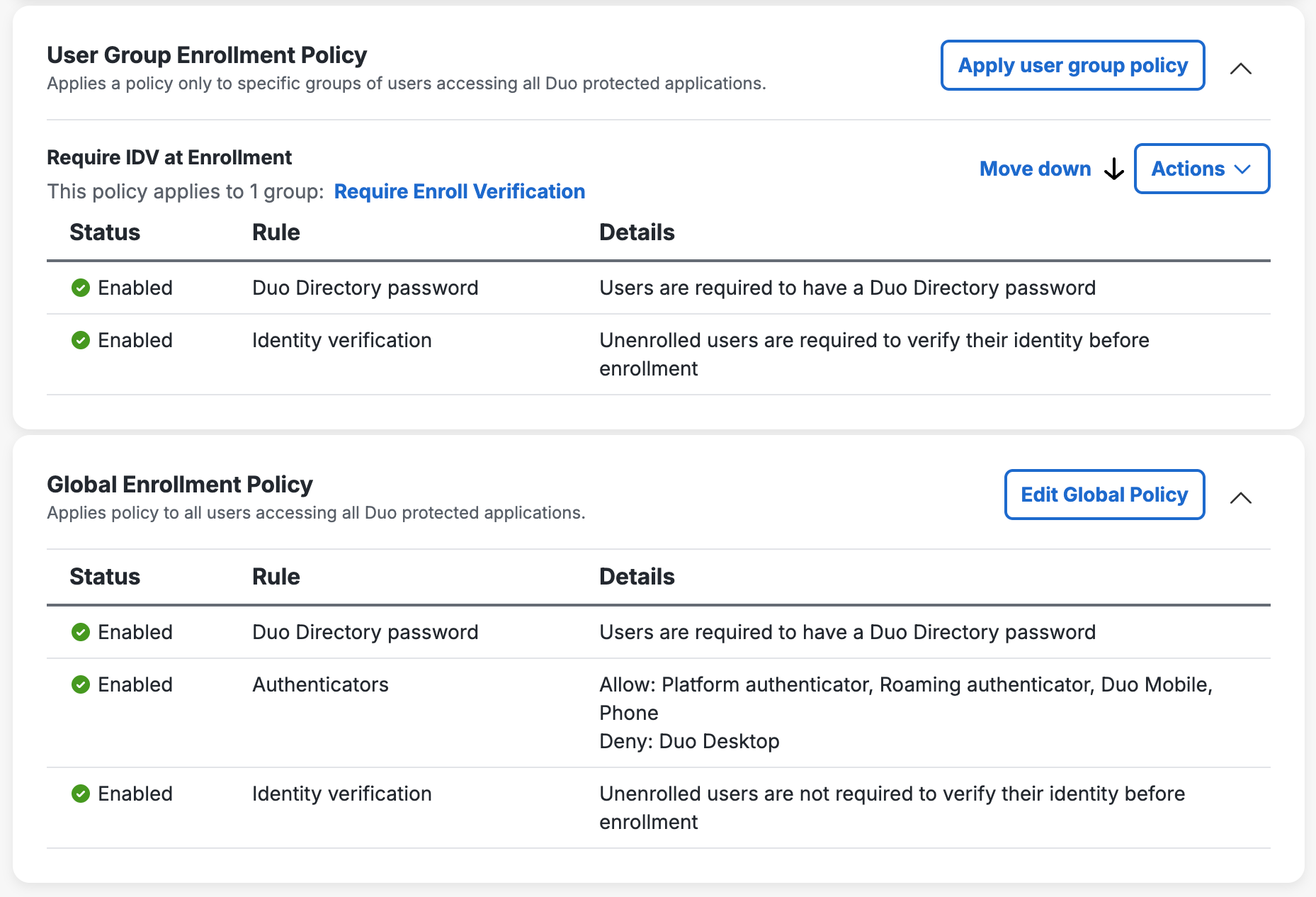
When unenrolled users (users without any registered Duo authentication methods, or without a password if you require Duo passwords) who are members of that target group access the Duo enrollment portal, they must complete identity verification in Persona first. Users who are not members of the target group will not need to complete identity verification.
If you create your users in Persona first, they do not have to exist in Duo, and you can edit the Global Enrollment Policy to require identity verification. All users who access the enrollment portal must complete Persona verification, whether they exist in Duo or not.
Enrollment with Identity Verification Experience
-
When a user subject to an enrollment policy that requires identity verification accesses the Duo enrollment portal, they will see a prompt to verify their identity before enrollment. They'll click Verify with Persona, which redirects them to Persona to perform identity verification.
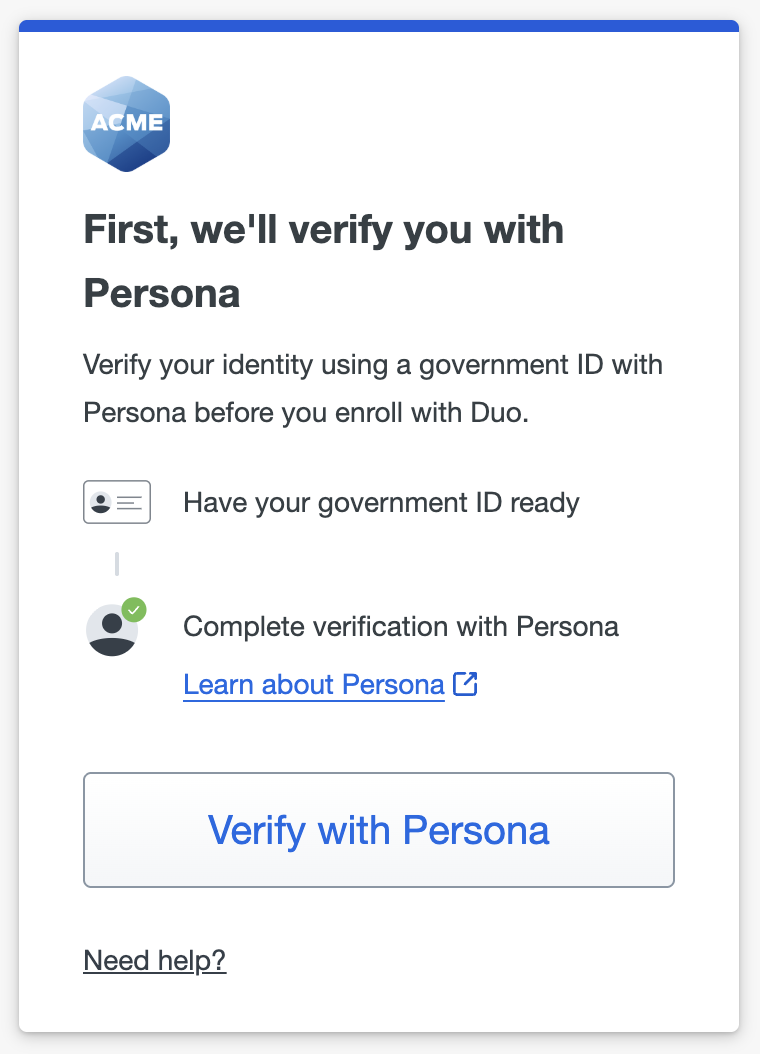
If the user does not exist in Duo or Persona with the required attributes, then they'll receive an error stating they are unable to start enrollment and to contact their Help Desk.
-
At the Persona site, the user will step through the verification process. They will scan their choice of approved government-issued ID and perform facial recognition.

If the user accessed the identity verification portal from a device without a camera, they can click Continue on another device to receive a QR code to scan from a device with a camera and complete the verification process with that other device.
-
When identity verification at the Persona site completes successfully, it redirects the user back to Duo to continue enrollment.
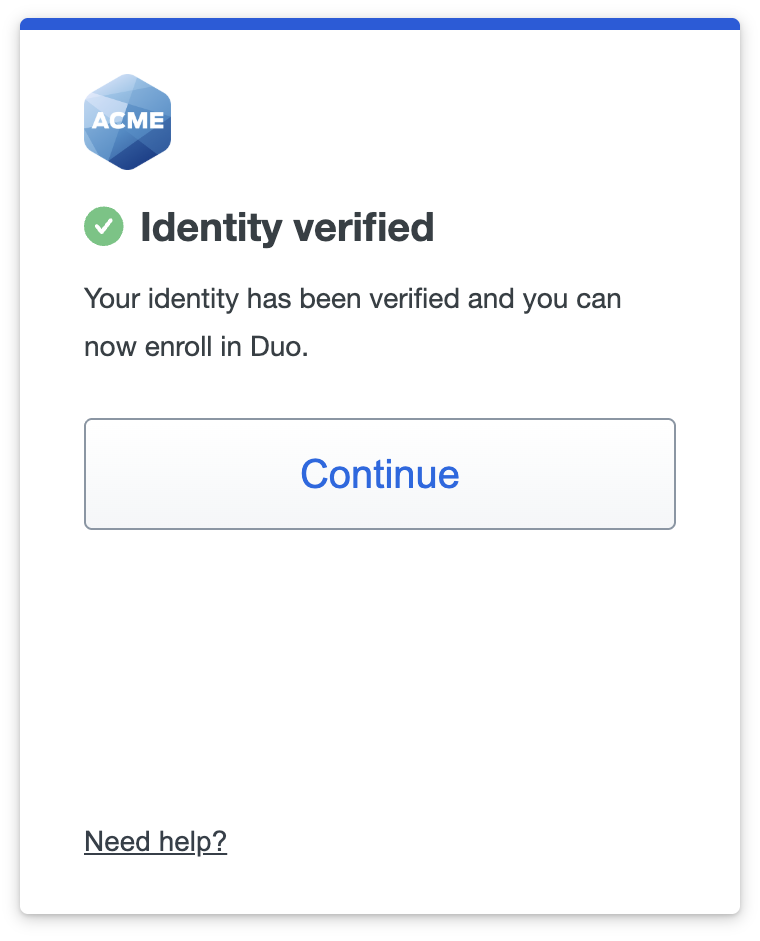
If the user is unable to complete identity verification at the Persona site, they will receive an error message when redirected back to Duo letting them know they must contact their Help Desk and cannot enroll in Duo.
Logging
Locate identity verification events at Reports → Activity Logs. Use the Identity Verifications filter at the top to focus on identity verification events.
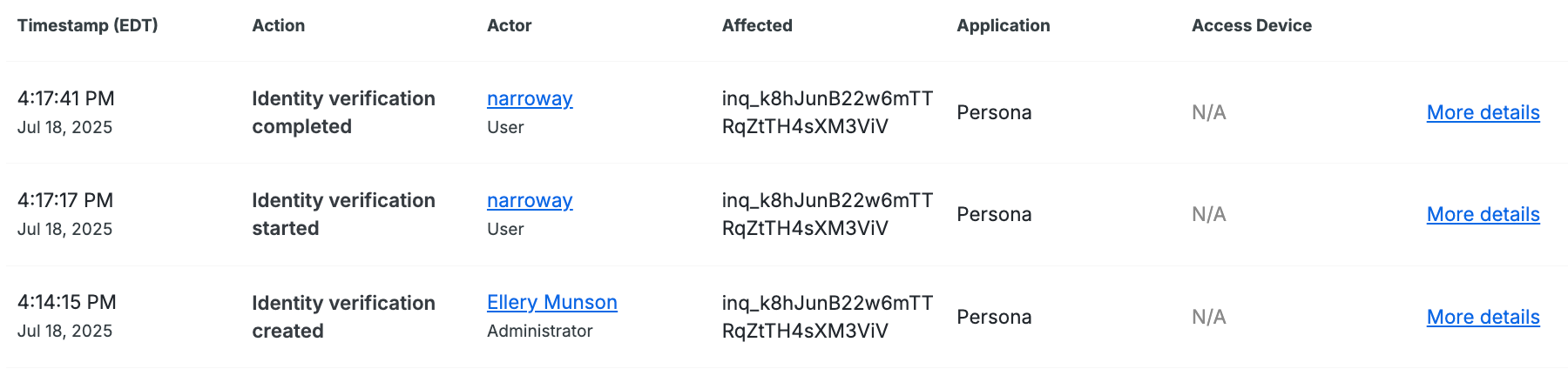
Click More details for any event to view additional information.
Known Limitations and Planned Improvements
-
Inbound Okta SCIM and Google Workspace directory sync to Duo do not include support for importing date of birth information.
-
CSV import does not support importing date of birth information.
