Duo Single Sign-On for F5 BIG-IP APM
Last updated:
About Duo Single Sign-On
Duo Single Sign-On is our cloud-hosted SSO product which layers Duo's strong authentication and flexible policy engine on top of F5 BIG-IP logins using the Security Assertion Markup Language (SAML) 2.0 or OpenID Connect (OIDC) authentication standards. Duo Single Sign-On acts as an OpenID provider (OP), authenticating your users using existing on-premises Active Directory (AD) or any SAML 2.0 IdP and prompting for two-factor authentication before permitting access to F5 BIG-IP.
Duo Single Sign-On is available in Duo Premier, Duo Advantage, and Duo Essentials plans, which also include the ability to define policies that enforce unique controls for each individual SSO application. For example, you can require that Salesforce users complete two-factor authentication at every login, but only once every seven days when accessing F5 BIG-IP. Duo checks the user, device, and network against an application's policy before allowing access to the application.
Configure Single Sign-On
Before configuring F5 BIG-IP with Duo SSO using OpenID Connect (OIDC) authentication you'll first need to configure a working authentication source.
Once you have your SSO authentication source working, continue to the next step of creating the F5 BIG-IP application in Duo.
When configuring an application to be protected with Duo Single Sign-On you'll need to send attributes from Duo Single Sign-On to the application. Active Directory will work with no additional setup, but if you used a SAML identity provider as your authentication source please verify that you configured it to send the correct SAML attributes.
These default attributes automatically map certain attributes from your authentication source.
| Default Attribute | Active Directory | SAML IdP |
|---|---|---|
<Username> |
sAMAccountName | Username |
<Email Address> |
||
<Display Name> |
displayName | DisplayName |
<First Name> |
givenName | FirstName |
<Last Name> |
sn | LastName |
<AMR> |
Not Applicable | Not Applicable |
AMR will be reported as [`pwd`, `auth-factor-dependent`].
Create the F5 BIG-IP Application in Duo
-
Log in to the Duo Admin Panel and navigate to Applications → Application Catalog.
-
Locate the entry for F5 BIG-IP APM with the "SSO" label in the catalog. Click the + Add button to start configuring F5 BIG-IP APM. See Protecting Applications for more information about protecting applications with Duo and additional application options. You'll need the information on the F5 BIG-IP APM page under Metadata later.
-
No active Duo users can log in to new applications until you grant access. Update the User access setting to grant access to this application to users in selected Duo groups, or to all users. Learn more about user access to applications. If you do not change this setting now, be sure to update it so that your test user has access before you test your setup.
This setting only applies to users who exist in Duo with "Active" status. This does not affect application access for existing users with "Bypass" status, existing users for whom the effective Authentication Policy for the application specifies "Bypass 2FA" or "Skip MFA", or users who do not exist in Duo when the effective New User Policy for the application allows access to users unknown to Duo without MFA. -
The Metadata section contains OpenID provider information about Duo Single Sign-On you will provide to your F5 BIG-IP device at a later configuration step.
-
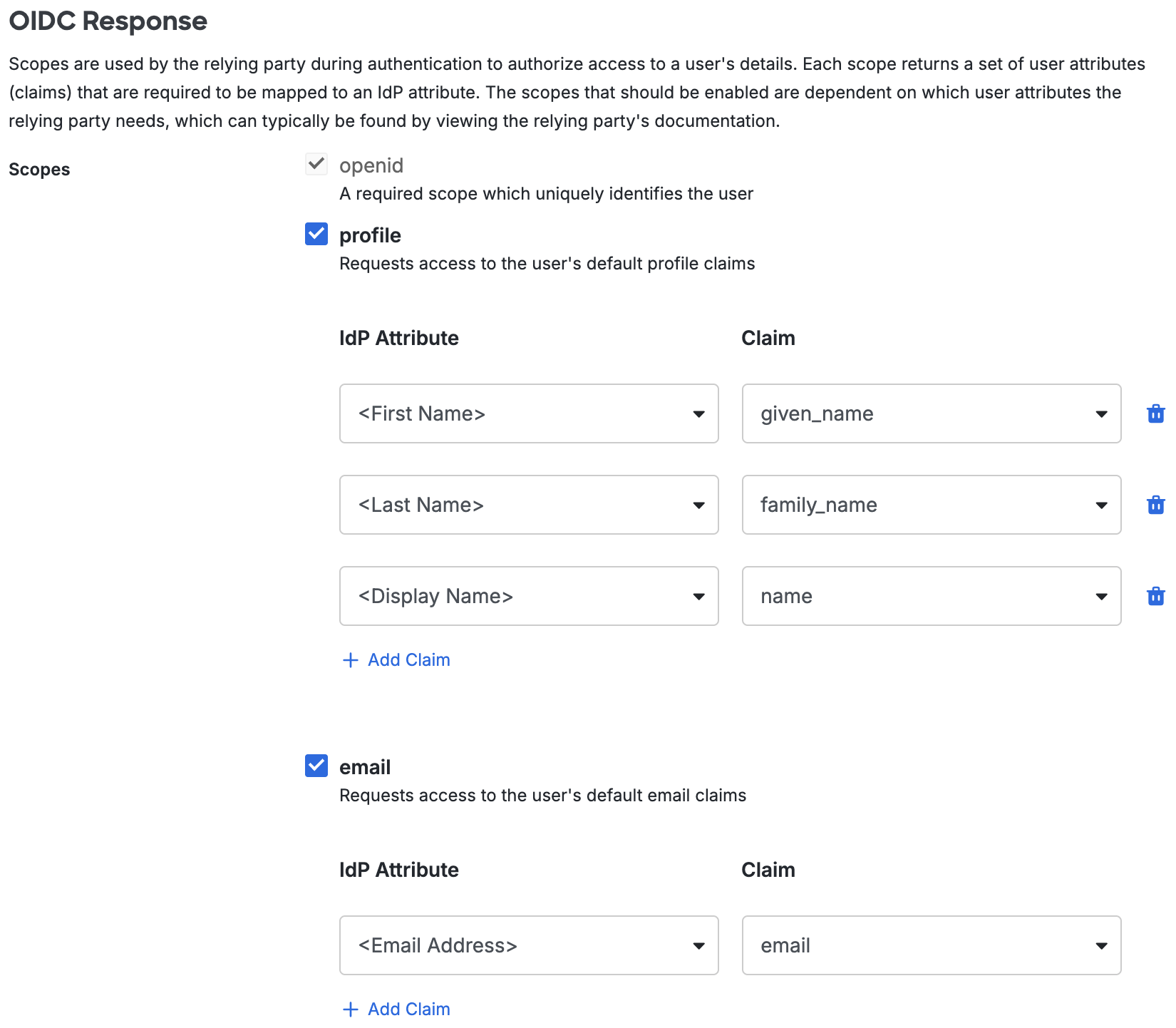
Scopes are used by F5 BIG-IP APM during authentication to authorize access to a user's details. Each scope returns a set of user attributes (claims) that must be mapped to IdP attributes. When an application sends an OIDC request to Duo SSO, the response sends only the claims from the requested scopes.
We've automatically enabled the following scopes and mapped the listed attributes. You can change the attribute sent from your authentication source by modifying the IdP Attribute name related to each claim:
-
Profile Scope:
IdP Attribute Claim <First Name> given_name <Last Name> family_name <Display Name> name -
Email Scope:
IdP Attribute Claim <Email> email
-
-
You can adjust additional settings for your new SSO application at this time — like changing the application's name from the default value, enabling self-service, or assigning a group policy.
-
Keep the Duo Admin Panel tab open. You will come back to it later.
Duo Universal Prompt
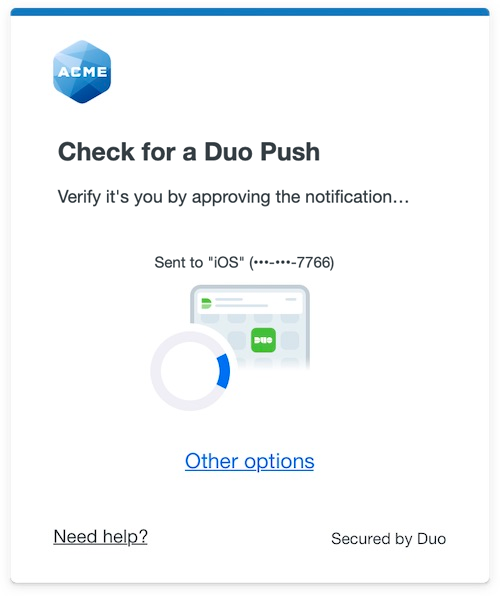
The Duo Universal Prompt provides a simplified and accessible Duo login experience for web-based applications, offering a redesigned visual interface with security and usability enhancements.
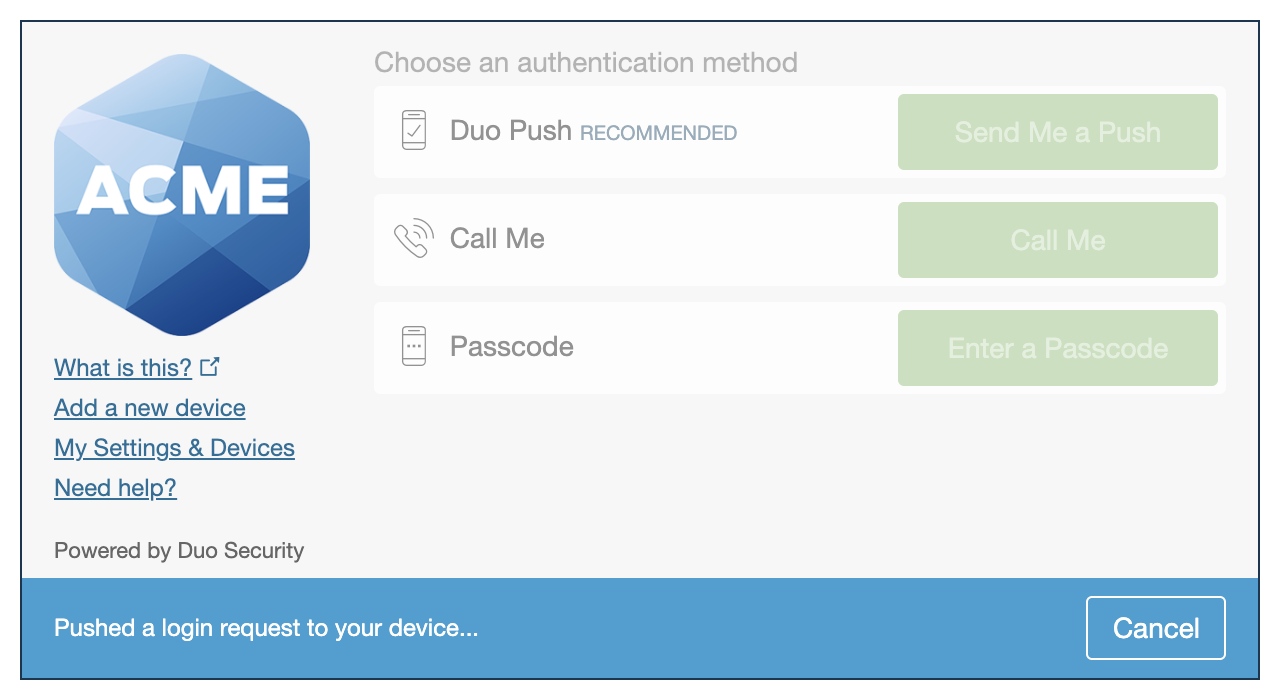
| Universal Prompt | Traditional Prompt |
 |
 |
The Duo F5 BIG-IP application supports the Universal Prompt by default, so there's no additional action required on your part to start using the newest authentication experience.
Activate Universal Prompt
Activation of the Universal Prompt is a per-application change. Activating it for one application does not change the login experience for your other Duo applications. Universal Prompt is already activated for new F5 BIG-IP applications at creation.
The "Universal Prompt" area of the application details page shows that this application's status is "Activation complete", with these activation control options:
- Show traditional prompt: Your users experience Duo's traditional prompt via redirect when logging in to this application.
- Show new Universal Prompt: (Default) Your users experience the Universal Prompt via redirect when logging in to this application.
The application's Universal Prompt status shows "Activation complete" both here and on the Universal Prompt Update Progress report.
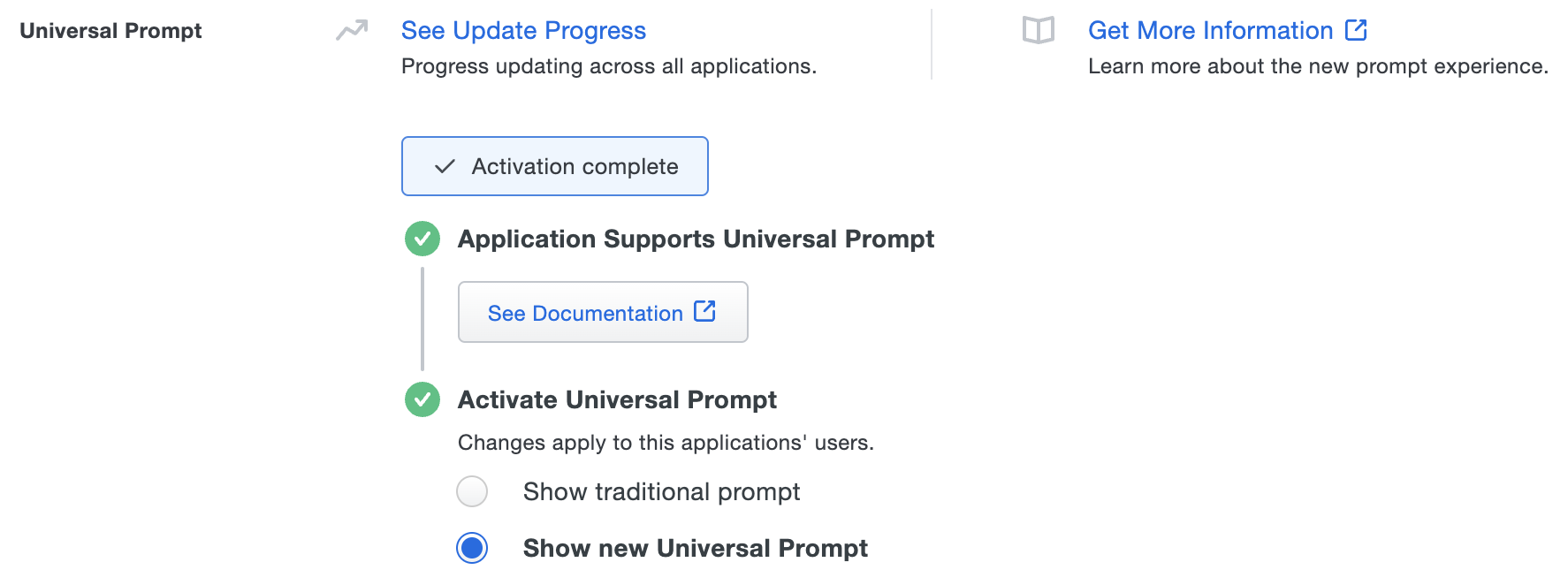
For the time being, you may change this setting to Show traditional prompt to use the legacy experience. Keep in mind that support for the traditional Duo prompt ended for the majority of applications in March 2024. This option will be removed in the future.
Universal Update Progress
Click the See Update Progress link to view the Universal Prompt Update Progress report. This report shows the update availability and migration progress for all your Duo applications. You can also activate the new prompt experience for multiple supported applications from the report page instead of visiting the individual details pages for each application.
Configure F5 BIG-IP
Create an OAuth Provider
-
Log into the BIG-IP management console as an administrator.
-
In the sidebar menu, make sure the Main tab is selected and navigate to Access → Federation → OAuth Client / Resource Server → Provider. If you do not see this navigation item, make sure you have a valid F5 BIG-IP APM feature license.
-
In the top-right corner of the page, click Create.
-
Under "General Properties", enter a unique name for your provider into the Name field.
-
Click the Type drop-down menu and select Custom.
-
Click the Ignore Expired Certificate Validation checkbox.
-
Make sure ca-bundle.crt is selected in the Trusted Certificate Authorities drop-down menu.
-
Make sure the following checkboxes are selected:
-
Allow Self-Signed JWK Config Certificate
-
Use Auto JWT
-
Support Introspection
-
-
Return to the Duo Admin Panel. Under "Metadata", copy the Discovery URL and paste it into the F5 BIG-IP OpenID URI field and then click Discover. Wait for the discovery process to complete.
-
In the BIG-IP management console, scroll down to the bottom of the page and click Save.
Configure the OAuth Server
-
At the top of the page in the BIG-IP management console, click the OAuth Client / Resource Server drop-down menu and select OAuth Server.
-
In the top-right corner of the page, click Create.
-
Under "General Properties", enter a unique name for your server into the Name field.
-
Make sure Client is selected in the Mode drop-down menu.
-
Click the Type drop-down menu and select Custom.
-
Click the OAuth Provider drop-down menu and select the provider that you created earlier.
-
Click the DNS Resolver drop-down menu and select f5-aws-dns or your specific DNS resolver.
-
Return to the Duo Admin Panel. Under "Metadata", copy the Client ID and paste it into the F5 BIG-IP Client Id field, under "Client Settings".
-
Return to the Duo Admin Panel. Copy the Client Secret and paste it into the F5 BIG-IP Client Secret field.
-
In the BIG-IP management console, click the Client's ServerSSL Profile Name drop-down menu and select serverssl.
-
At the bottom of the page, click Finished.
Add an Access Policy
After you configure your F5 BIG-IP OAuth server and provider, you need to add an access policy.
-
In the sidebar menu, navigate to Access → Profiles / Policies → Access Profiles (Per-Session Policies).
-
In the top-right corner of the page, click Create.
-
Under "General Properties", enter a unique name for your policy into the Name field.
-
Click the Profile Type drop-down menu and select All.
-
Make sure Profile is selected in the Profile Scope drop-down menu.
-
Make sure Modern is selected in the Customization Type drop-down menu.
-
Scroll down to "SSO Across Authentication Domains (Single Domain Mode)". Next to "Cookie Options", make sure the Secure checkbox is selected.
-
Click the HTTP Only checkbox.
-
Click the Samesite checkbox. A drop-down menu appears.
-
Click the drop-down menu and select Lax.
-
Scroll down to "Language Settings". Under "Factory Builtin Languages", select your desired language and click the arrow button to add it to the "Accepted Languages" field.
-
At the bottom of the page, click Finished.
Attach the Access Policy to the Virtual Server
After you add an access policy, you need to attach the access policy to the virtual server.
-
In the sidebar menu, navigate to Local Traffic → Virtual Servers → Virtual Server List.
-
In the Name column, click your virtual server.
-
Make sure the Properties tab is selected.
-
Next to "Destination Address/Mask", click the Host radio button and type your server IP address into the field. Make note of your server IP address. You will need it later.
-
Next to "Service Port", click the Port radio button and type your port number into the field. Make note of your port number. You will need it later.
-
Scroll down to "Access Policy". Click the Access Profile drop-down menu and select the policy you created earlier.
-
Scroll down to the bottom of the page and click Finished.
Apply the Access Policy
-
In the BIG IP management console's sidebar menu, navigate to Access → Profiles / Policies → Access Profiles (Per-Session Policies).
-
In the Access Profile Name column, locate the profile you created earlier. On your profile row, in the "Per-Session Policy" column, click Edit. Your access policy page opens in a new tab.
-
In your access policy page, click the red Deny flag. The "Select Ending" pop-up window opens.
-
Click the Allow radio button and then click Save. The pop-up window closes and the red Deny flag changes to a green Allow flag.
-
Click the (+) to the left of the green Allow flag. A pop-up window opens.
-
In the pop-up window, click the Authentication tab.
-
Click the OAuth Client radio button and then click Add Item. A different pop-up window opens.
-
In the pop-up window, make sure the Properties tab is selected.
-
Click the Server drop-down menu and select the server you created earlier.
-
Click the OpenID Connect drop-down menu and select Enabled.
-
Click the Authentication Redirect Request drop-down menu and select /Common/FSAuthRedirectRequestJWT.
-
Click the Token Request drop-down menu and select /Common/FSTokenJWTRequestByAuthzCode.
-
Click the Refresh Token Request drop-down menu and select /Common/FSTokenRefreshRequest.
-
Click the OpenID Connect UserInfo Request drop-down menu and select /Common/FSUserinfoRequest.
-
In the Redirection URI field, replace %(session.server.network.name) with the server IP address and port number you noted earlier.
Example: https://serveripaddress:portnumber/oauth/client/redirect
-
Type openid email profile into the Scope field.
-
Copy the Redirection URI and then click Save at the bottom of the pop-up window. The pop-up window closes.
-
At the top of the page, click Apply Access Policy.
-
Return to the Duo Admin Panel. Under "Relying Party", paste the Redirection URI you copied from F5 BIG-IP earlier and paste it into the Duo Admin Panel Sign-In Redirect URLs field, under "Relying Party".
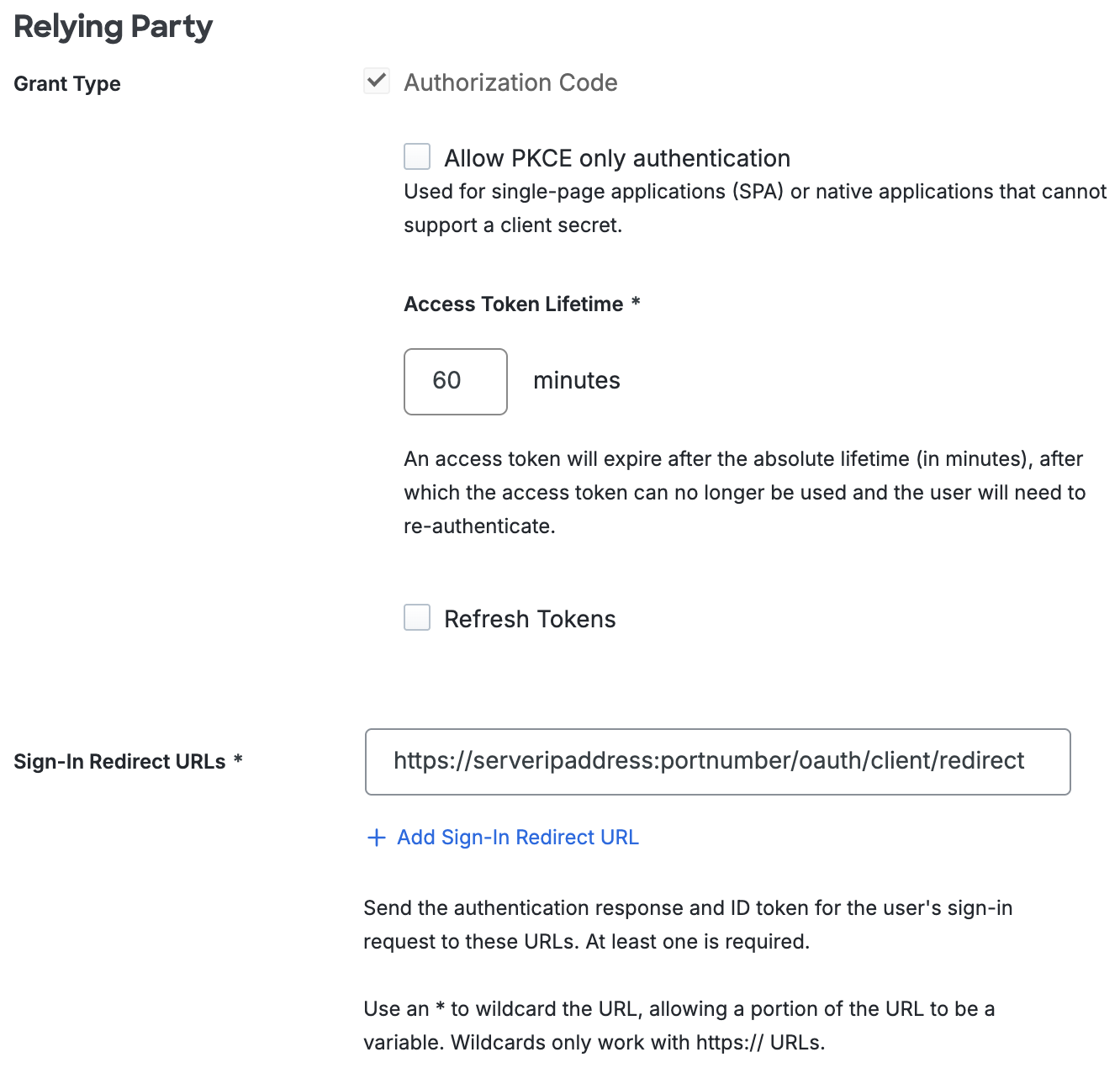
-
In the Duo Admin Panel, scroll down to the bottom of the page and click Save.
Learn more about F5 BIG-IP APM SSO at the MyF5 Knowledge Base.
Using SSO
You can log on to your F5 BIG-IP APM using SSO by navigating to your F5 BIG-IP SSO page using the server ip address and port number you noted earlier e.g., https://serveripaddress:portnumber. You will be automatically redirected to Duo Single Sign-On to begin authentication.
Active Directory Login
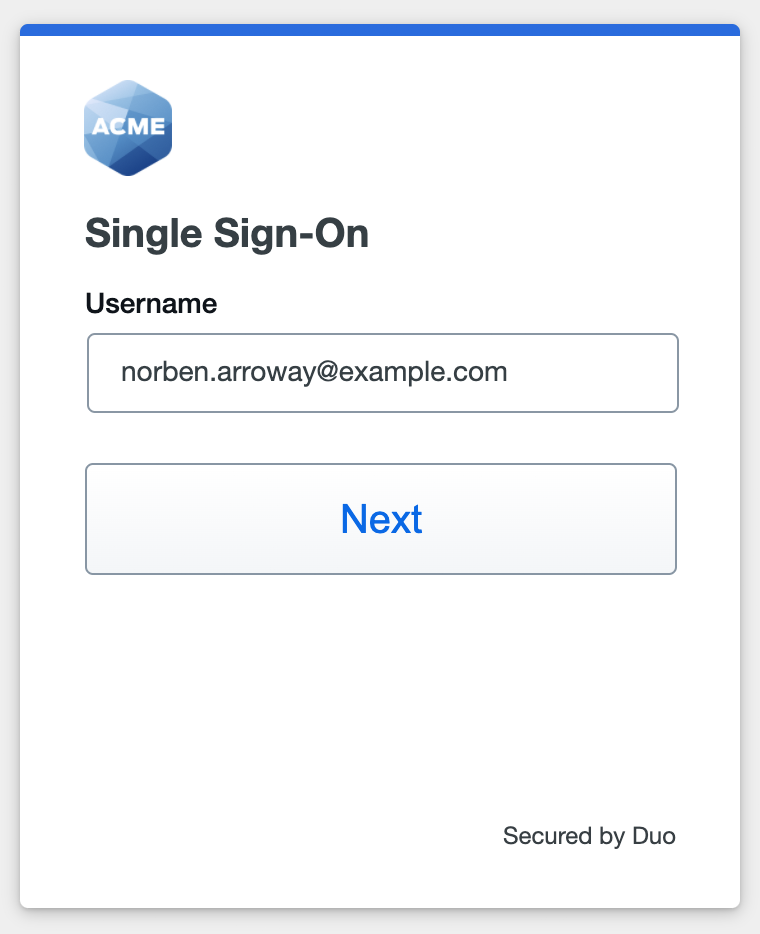
With Active Directory as the Duo SSO authentication source, enter the primary username (email address) on the Duo SSO login page and click or tap Next.
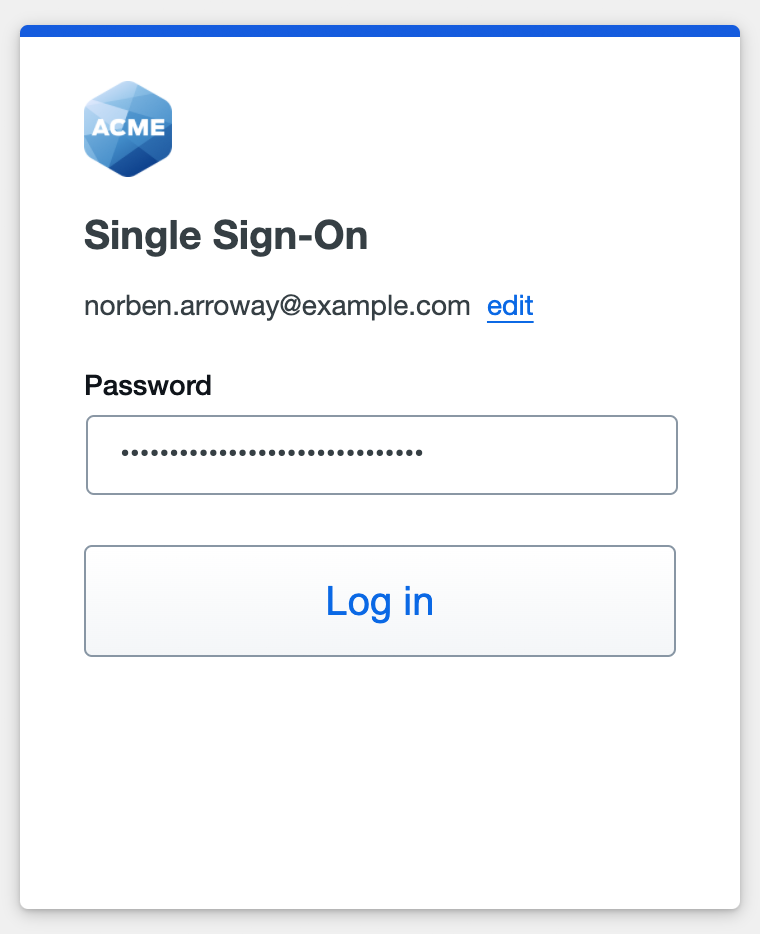
Enter the AD primary password and click or tap Log in to continue.
Enable Duo Passwordless to log in to Duo SSO backed by Active Directory authentication without entering a password in the future.
SAML Login
With another SAML identity provider as the Duo SSO authentication source, Duo SSO immediately redirects the login attempt to that SAML IdP for primary authentication. Users do not see the Duo SSO primary login screen.
Duo Authentication
Successful verification of your primary credentials by Active Directory or a SAML IdP redirects back to Duo. Complete Duo two-factor authentication when prompted and then you'll return to F5 BIG-IP to complete the login process.
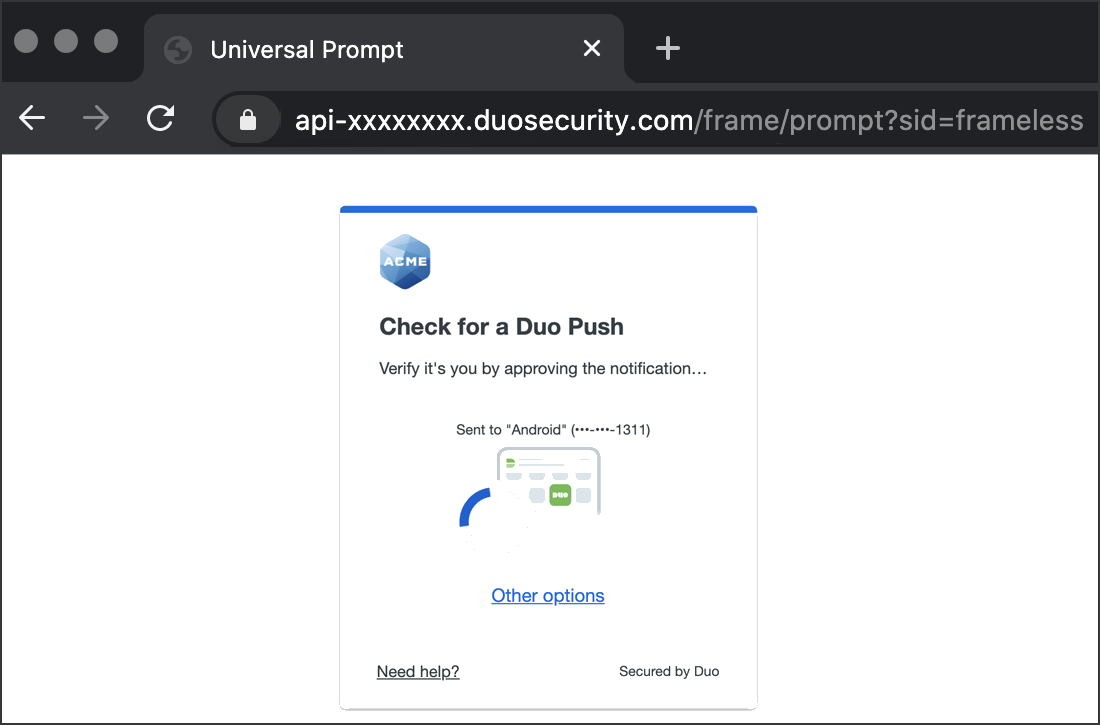
* Universal Prompt experience shown.
F5 BIG-IP supports SP-initiated authentication only, meaning that you must start your SSO login from that application's sign-in page. You won't be able to add as an application tile in Duo Central for IdP-initiated logins.
Congratulations! Your F5 BIG-IP users now authenticate using Duo Single Sign-On.
See the full user login experience, including expired password reset (available for Active Directory authentication sources) in the Duo End User Guide for SSO.
Grant Access to Users
If you did not already grant user access to the Duo users you want to use this application be sure to do that before inviting or requiring them to log in with Duo.
Enable Remembered Devices
To minimize additional Duo two-factor prompts when switching between and your other Duo Single Sign-On SAML applications, be sure to apply a shared "Remembered Devices" policy to your SAML applications.
Automated Provisioning
You may be able to create, manage, and delete users and groups in this application automatically from Duo using SCIM 2.0 provisioning. See Automated Provisioning to learn how.
Troubleshooting
Need some help? Try searching our Knowledge Base articles or Community discussions. For further assistance, contact Support.
