Automated Provisioning
Last updated:
Overview
User lifecycle changes can make access management a daunting and potentially insecure task. Automated provisioning simplifies this process, allowing you to use Duo to automatically provision, maintain, and deprovision users and groups into supported downstream SAML and OIDC single sign-on (SSO) service provider applications.
Take advantage of automated provisioning whether you are using Duo as your primary identity provider (IdP), or if you use Duo with an external identity provider or existing identity and access management (IAM) deployment.
Automated provisioning is a continuous process once configured. Once you assign groups to an application, Duo may automatically:
-
Provision all members of that group to the application.
-
Create groups in the application, as well as propagate group name changes (if supported by the application).
-
Provision new users added to provisioned groups to the application, or deprovision users from the application when removed from a provisioned group.
-
Update user attributes for members of provisioned groups when any provisioned attribute changes in Duo.
-
Deprovision all members of the group from the application if the group is ever removed from provisioning.
These described behaviors depend on provisioning support available in your target applications, so some results may vary.
Like Duo Single Sign-On, automated provisioning is part of the Duo Essentials, Duo Advantage, and Duo Premier plans.
Verify Provisioning Support for your Target Applications
Before you get started with automated provisioning, make sure your target applications support SCIM provisioning, and review the application documentation to identify:
- What user attributes they support and which of these attributes are required.
- What authentication mechanisms they support. We provide support for bearer token and client credential authentication mechanisms for all Duo Single Sign-On applications that support provisioning.
- We also offer a "Cloud Connection" (OAuth Auth Code grant) flow for limited verified applications.
Identify Supported Duo Applications
Automated provisioning support is available to most Duo Single Sign-On applications, including the Generic SAML Service Provider and Generic OIDC Relying Party applications. When viewing the Application Catalog in the Duo Admin Panel, look for applications with a "Provisioning" label. Use the "Supported Features" filter to show only applications that support provisioning.
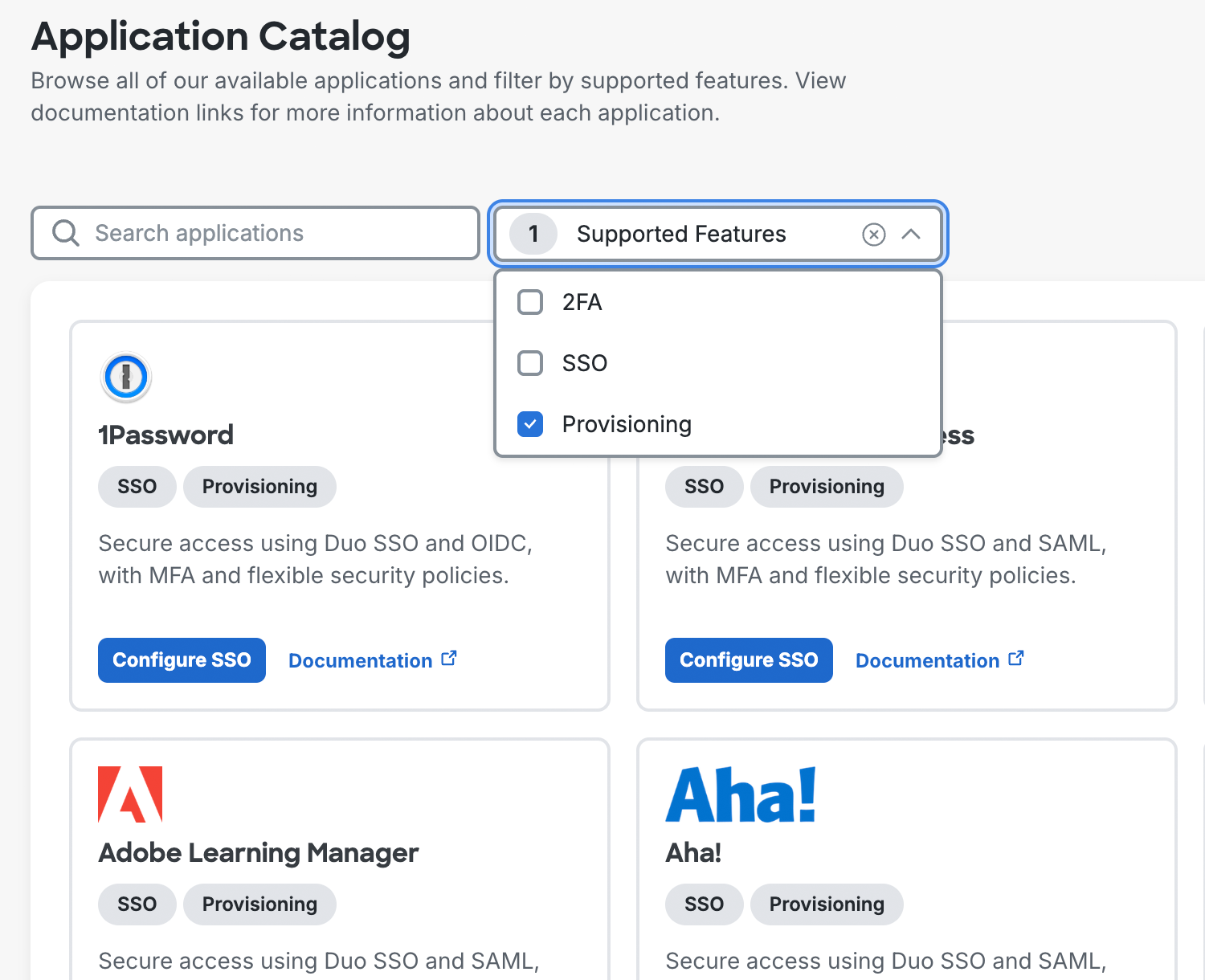
When you view an application that supports provisioning in the Duo Admin Panel, you'll see a "Provisioning" tab on the page. When you view this tab, you'll see that the application is either verified or unverified for automated provisioning. Applications without the "Provisioning" label in the Application Catalog or tab on the application's details page do not support automated provisioning.
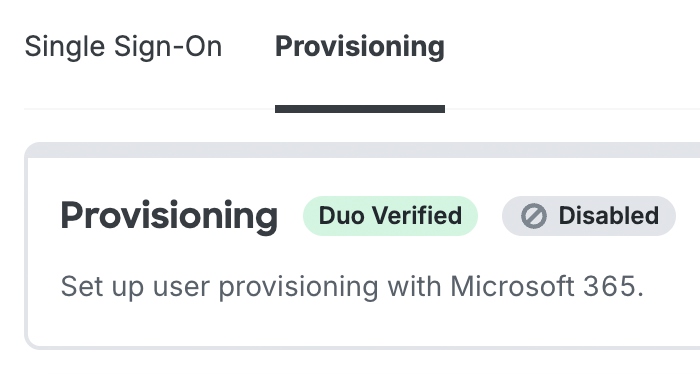
Duo Verified Applications
The presence of the "Duo Verified" label on the SSO application's "Provisioning" tab means that Duo has verified provisioning compatibility with the target application. You can find step-by-step automated provisioning instructions for verified applications on the same documentation page that you used to set up Duo SSO federation with the application.
Duo Verified Applications:
- Atlassian Cloud
- AWS IAM Identity Center
- Cisco Secure Access
- Google Workspace
- Microsoft 365
- Webex Control Hub
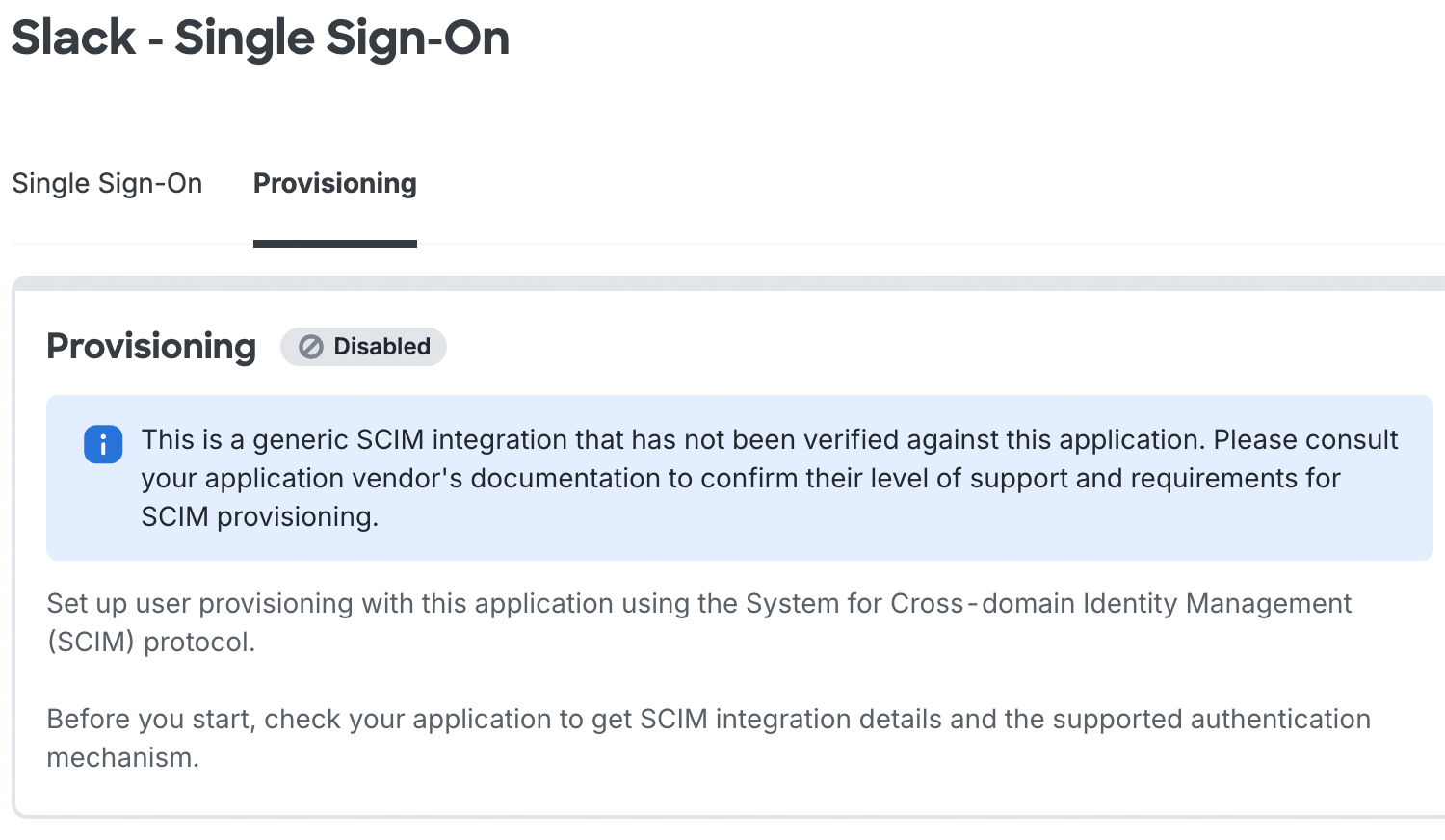
Generic SCIM Applications
SSO applications not yet verified by Duo may have generic SCIM 2.0 provisioning support available. The "Provisioning" tab for the application notes the availability of generic SCIM support and reminds you to check with the target application's vendor to determine compatibility with SCIM 2.0 provisioning.
Configure Automated Provisioning
You can configure automated provisioning as part of your initial SSO setup with a service provider application, or update an existing SSO application to add provisioning.
Refer to the SSO instructions for verified applications to learn how to configure automated provisioning for those applications.
To configure generic SCIM automated provisioning for other Duo SSO applications:
-
Log into the Duo Admin Panel.
-
Navigate to Applications → Applications and click on the Duo SSO application you want to configure for provisioning.
-
Click on the "Provisioning" tab to begin your automated provisioning setup.
Authentication
-
In the "Authentication" section of the application's "Provisioning" tab, select which Authentication mode you would like use to connect to your target application. Please consult your target application’s documentation to understand what authentication methods they support, and where to gather the credentials needed to authenticate.
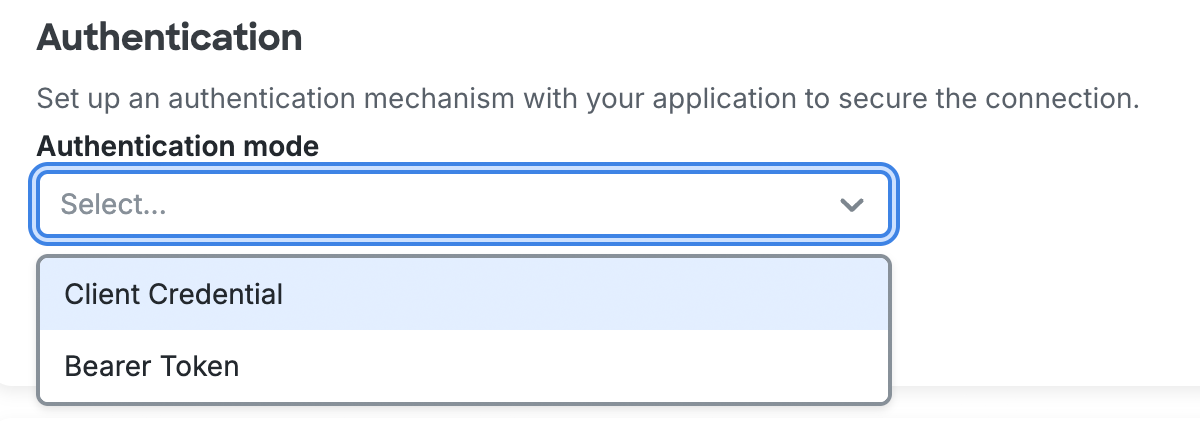
- Client Credential: A type of OAuth authentication that does not require user interaction in a browser.
- Bearer Token: A secret token that allows for authentication with the service provider application.
-
Enter the connection information from your service provider application.
-
If you selected Client Credential, you must provide a valid Base URL, Client ID, Client Secret, and Token URL from the service provider application to create the connection.
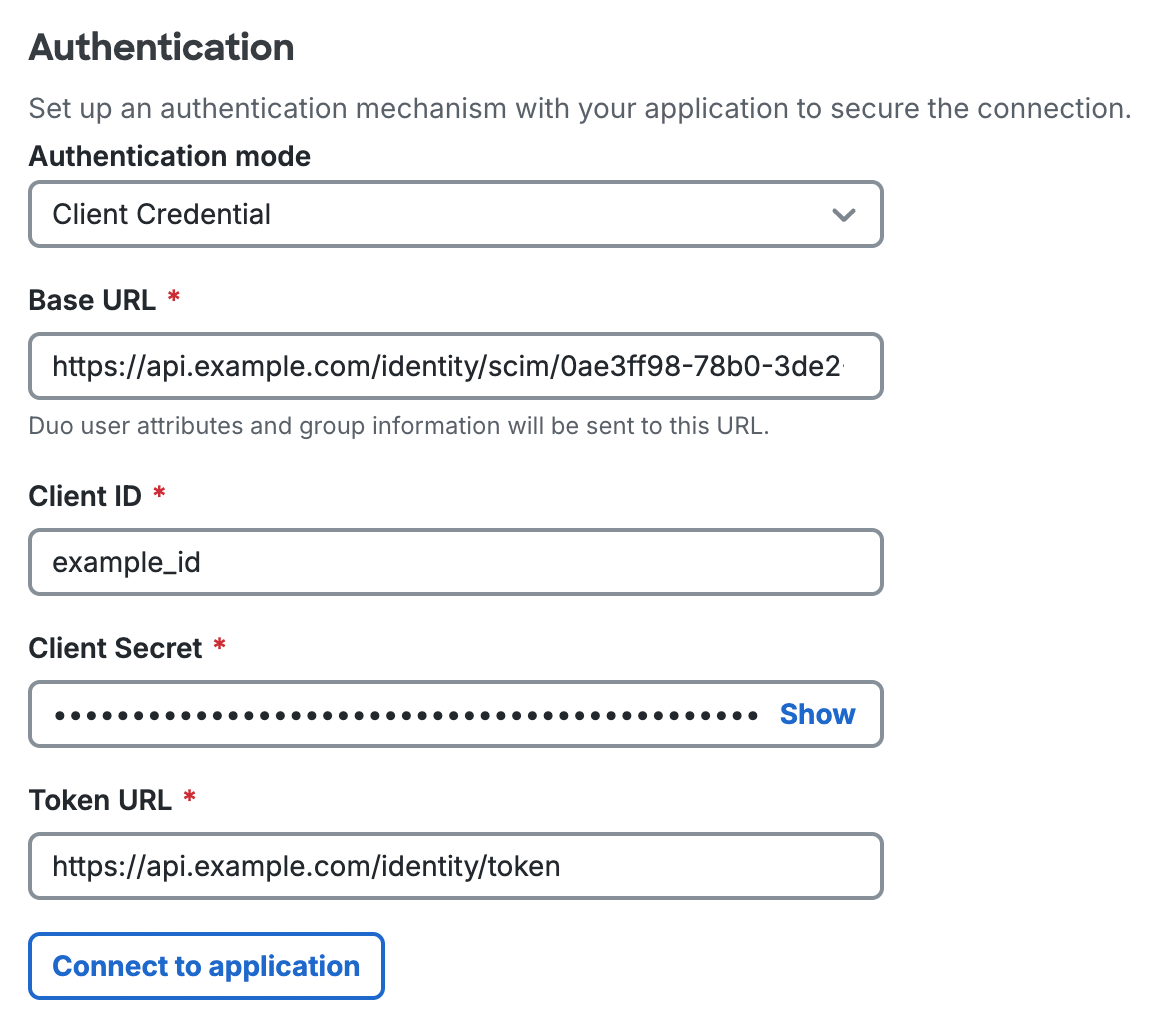
-
If you selected Bearer Token, you must provide a valid Base URL and Token from the service provider application to create the connection.
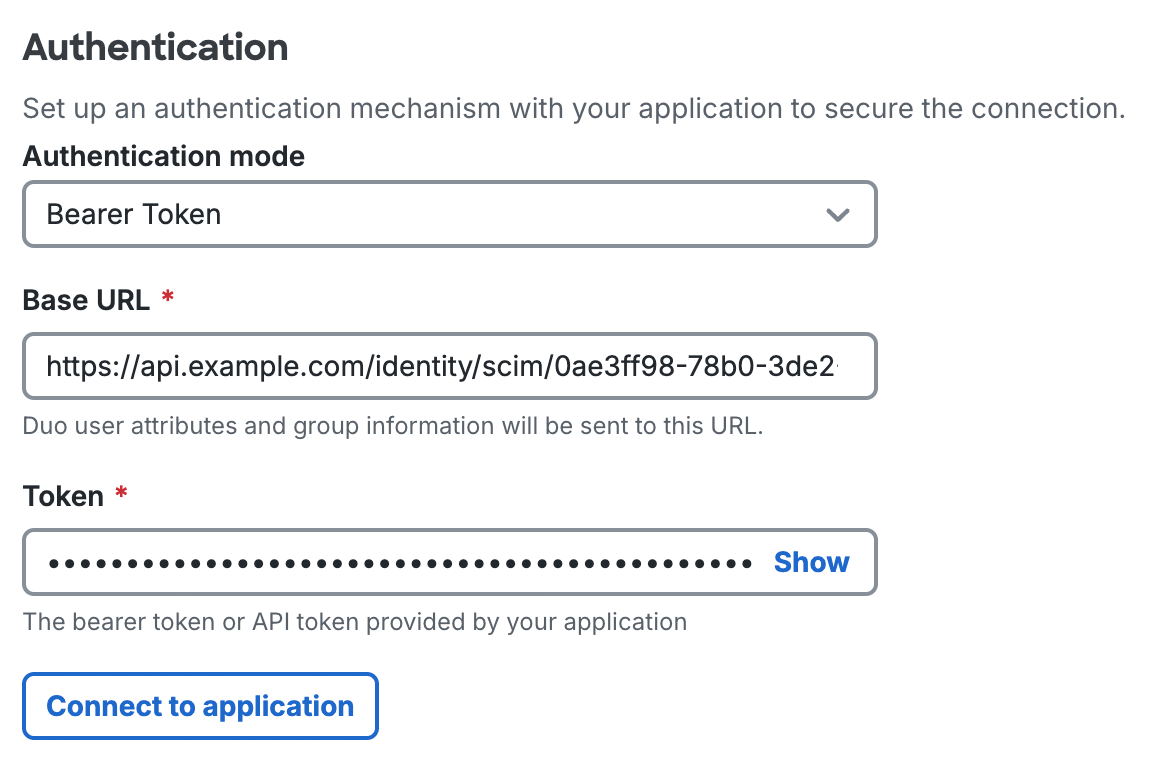
-
-
Click Connect to application after entering the application authentication information.
You'll receive a success message if the authentication information was correct. You may not proceed to attribute mapping until the connection succeeds.
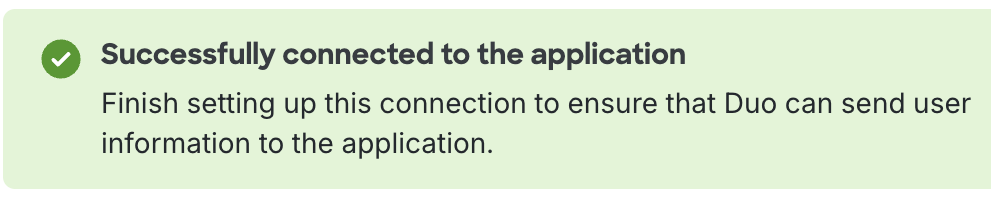
The target application may set an expiration date for your authentication token or credentials. You may need to regenerate the token on a regular basis for continuous provisioning. Refer to the target application's documentation for more information.
Attribute Mapping
You can choose which attributes Duo sends to the application. Confirm the target application's required and optional attributes by reviewing their provisioning documentation.
When Duo establishes a connection to the target application, we try to discover the target application's SCIM Schemas endpoint. If the application has a Schemas endpoint, it informs Duo which attributes the application supports receiving, and which of the attributes are required. If the application does not have a Schemas endpoint, then we provide a set of default SCIM attributes you may select to send to the target application.
-
On the application's "Provisioning" tab, go to the "Attribute Mapping" section. The list of mapped attributes is prepopulated with some required attributes. The required attributes may differ from application to application.
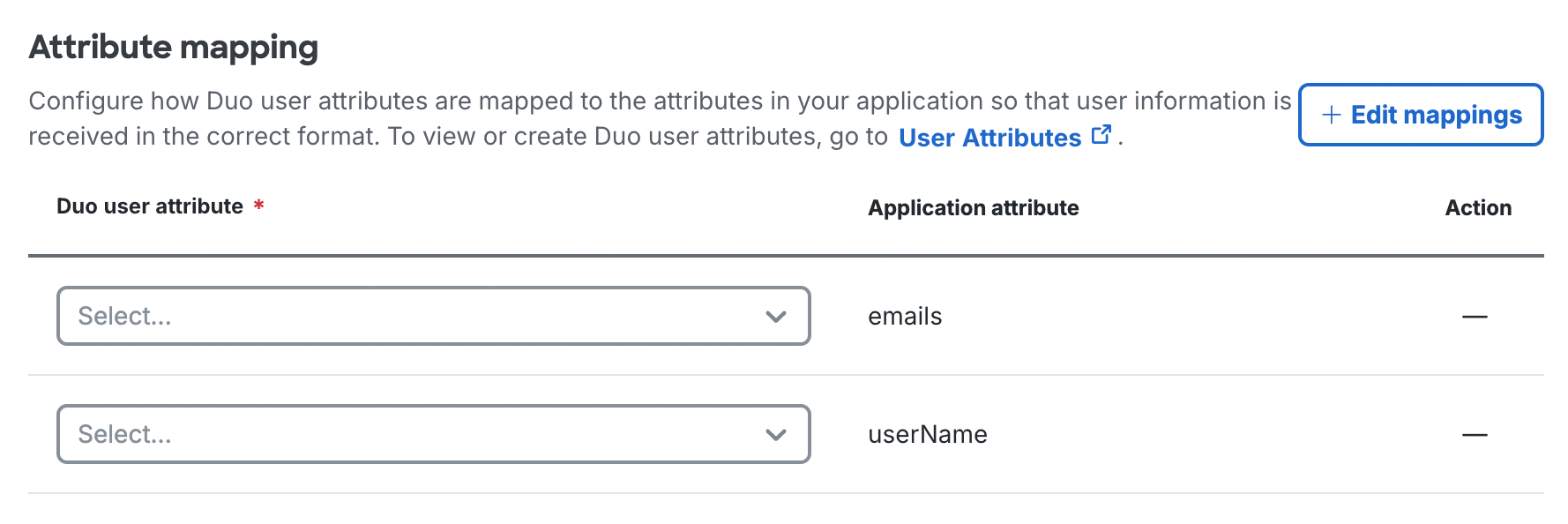
-
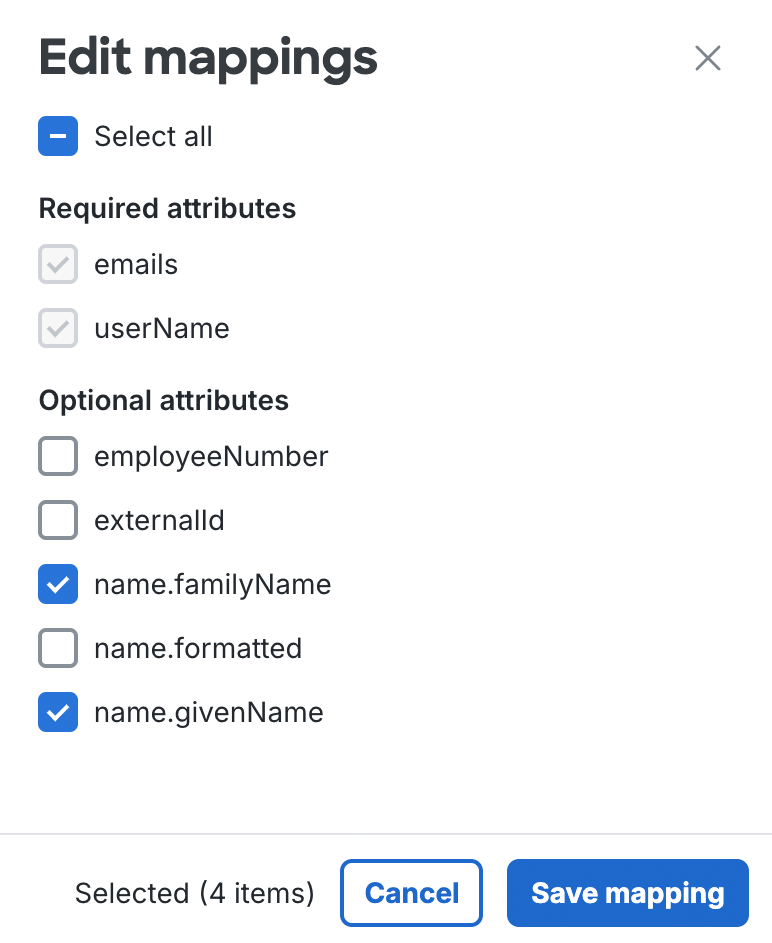
Click + Edit mappings to view all available attributes. The list of attributes may vary depending on whether the application provided SCIM schema information to Duo or not. You can add or remove mapping for optional attributes, but cannot remove required attributes.
To add attribute mappings, select the ones you want to add from the list (or Select all), and then click Save mapping. The additional attribute mappings are added to the "Attribute mapping" section of the page.
-
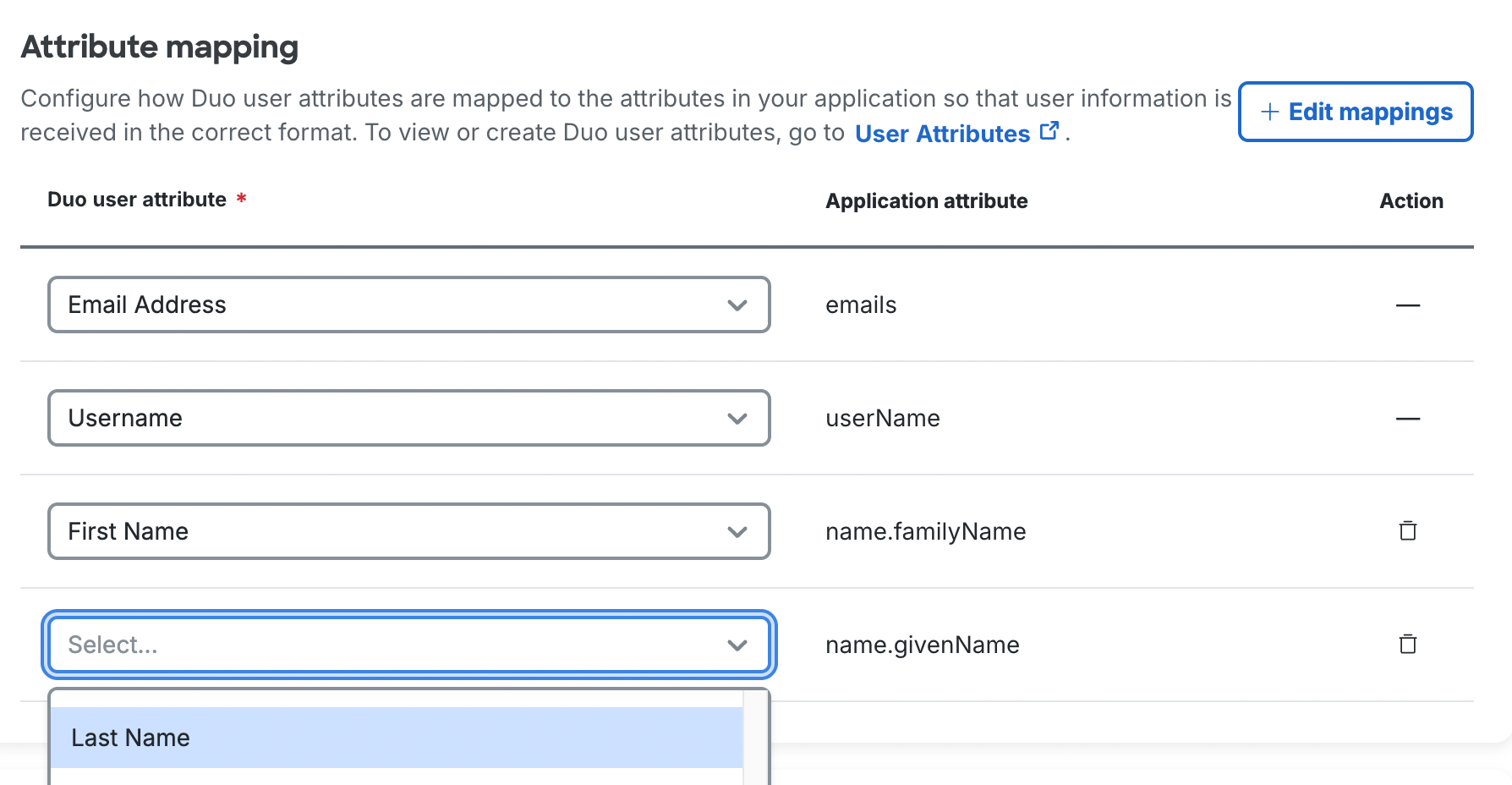
Use the drop-down to select the Duo user attribute you want to map to each of the application attributes. You can select from Duo's default user attributes or from any custom user attributes you've created and populated with values.
-
Continue configuring provisioning to select groups.
Groups
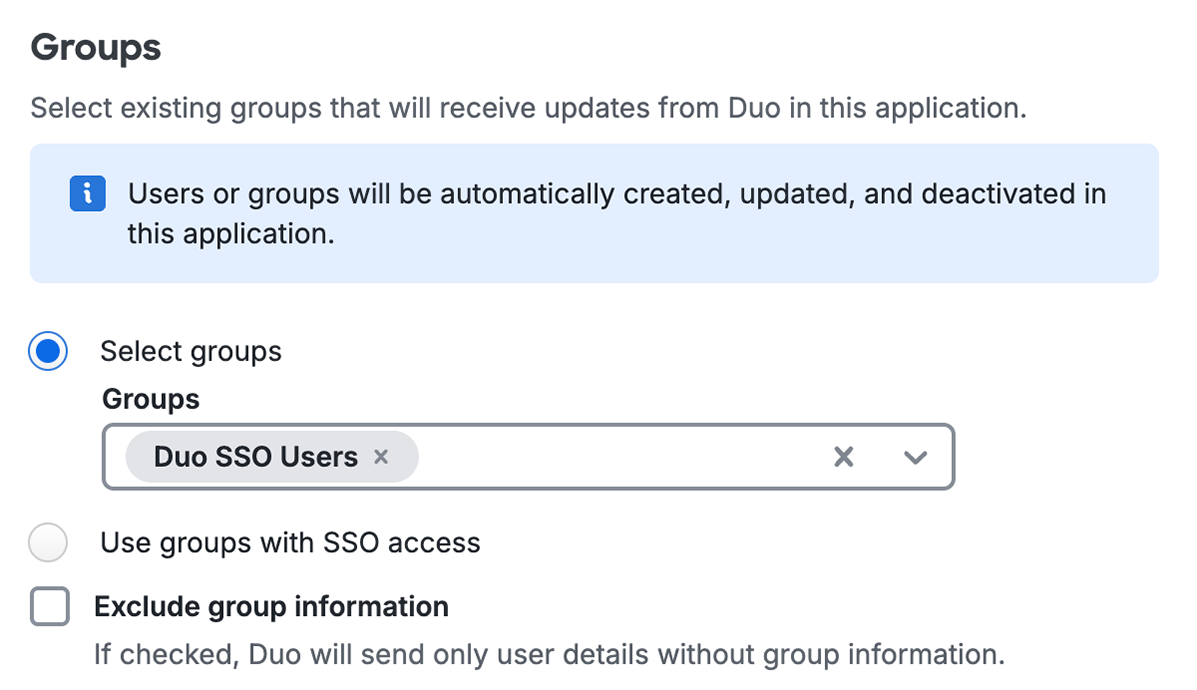
While you can't specify attribute mappings for groups, you can choose which groups to provision into the target application, or opt not to send any group information at all.
-
On the application's "Provisioning" tab, scroll down to "Groups".
-
Select which Duo groups you would like to provision into your target application.
If you have already set up Duo SSO with this application and want the same groups permitted for user access provisioned into the target application, select Use existing SSO permitted groups.
If you have not set up single sign-on for the target application yet, or want to provision a subset of your permitted groups into the target application, use the drop-down to select those Duo groups.
If you don't want Duo to create and manage groups in the target application, check Exclude group information.
Users
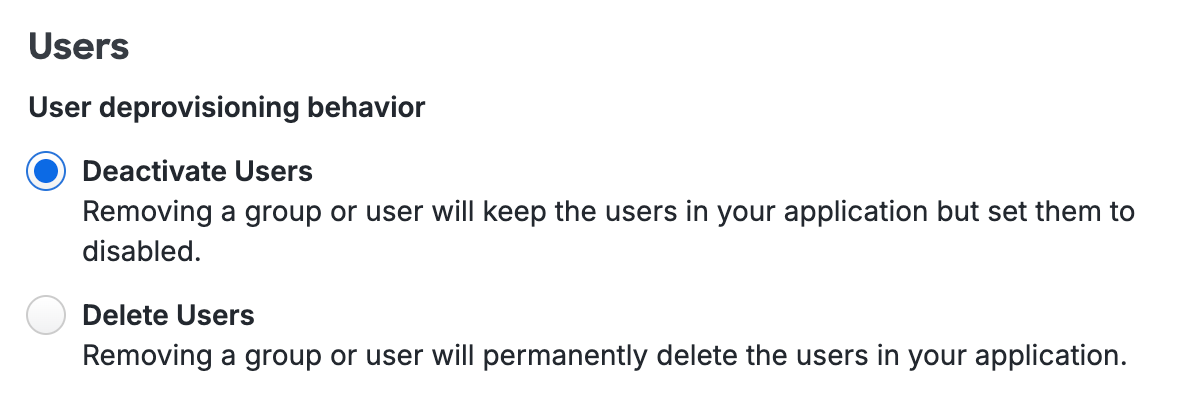
The default deprovisioning behavior for users is to deactivate them in the target application. You may change this to delete users instead. Verify that the target application supports user delete via SCIM before changing this setting.
-
Scroll down to "Users".
-
Select Delete Users if you want users automatically deleted from the application instead of deactivated.
Start Provisioning
After entering your provisioning configuration information, click Save and enable at the bottom of the page. The provisioning status for the application will show "Enabled" and Duo will begin provisioning your users and groups into the target application.
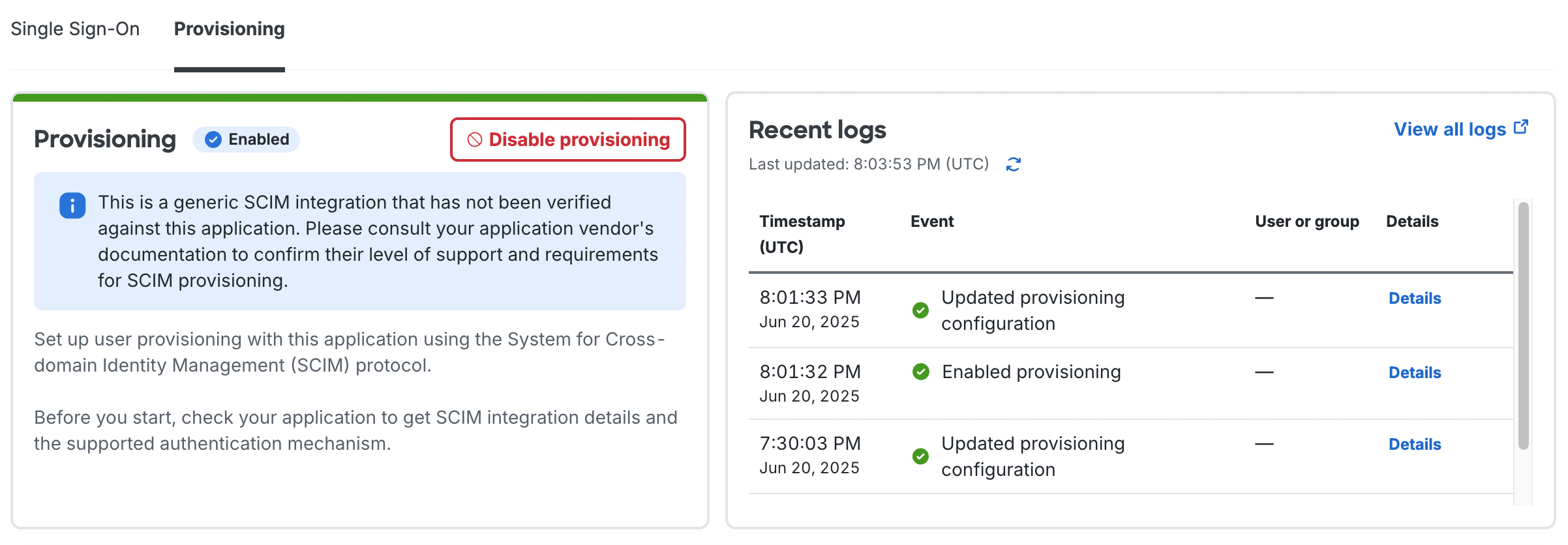
You can return to the "Provisioning" tab of this application to change the provisioning settings or review recent provisioning logs, or visit the Activity Log to review logged events for all applications configured for automated provisioning.
Status and Logs
Return to the "Provisioning" tab of this application to review recent provisioning logs, or visit the Activity Log to review logged events for all applications configured for automated provisioning. Logged events include:
- Provisioning configuration changed
- Provisioning enabled/disabled
- User sync successful
- User sync failed
- Group sync successful
- Group sync failed
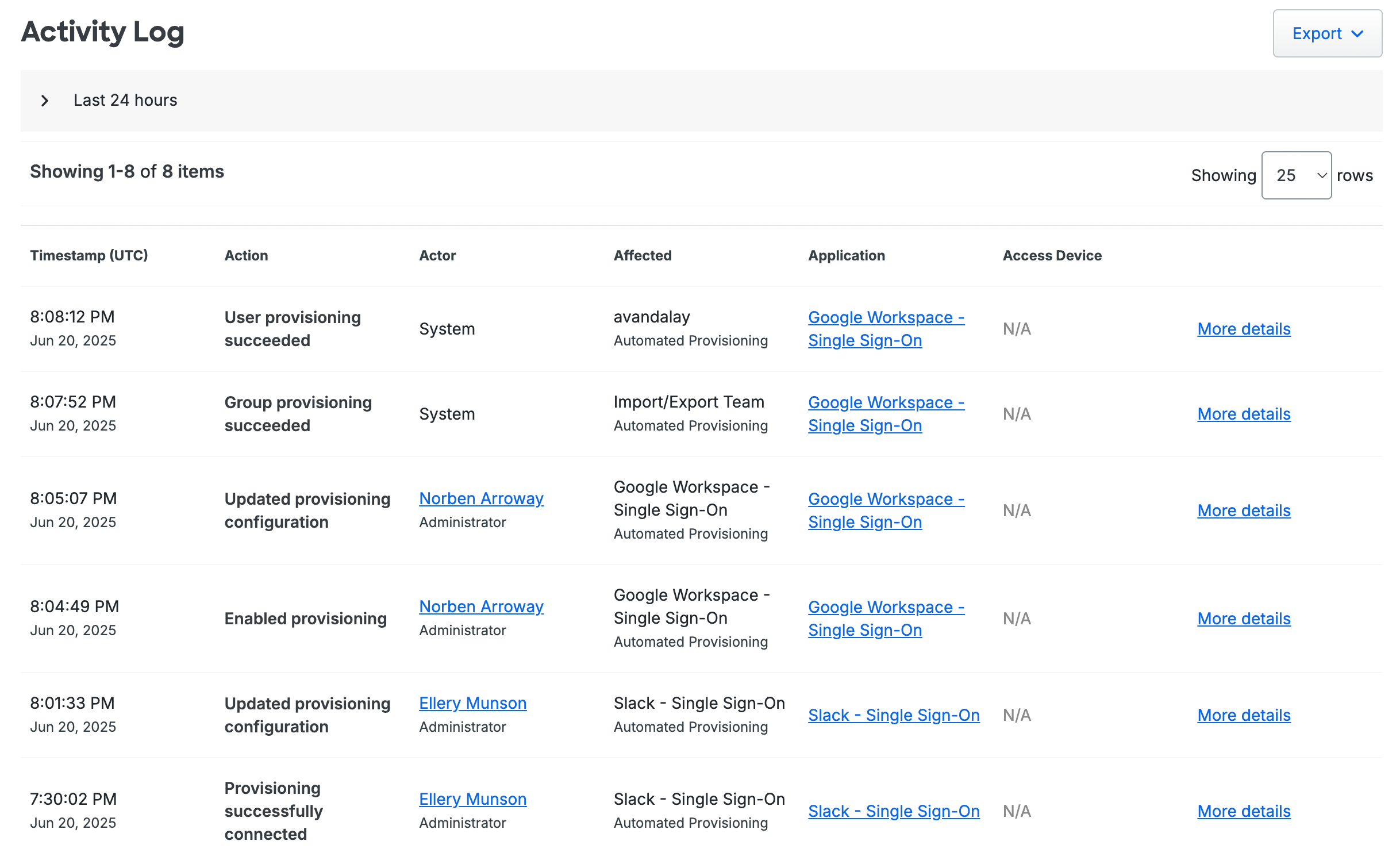
For any event, click Details on the application's "Provisioning" tab or More Details on the Activity Log to vew more information about the logged event. This may include details about any errors or failures in provisioning operations.
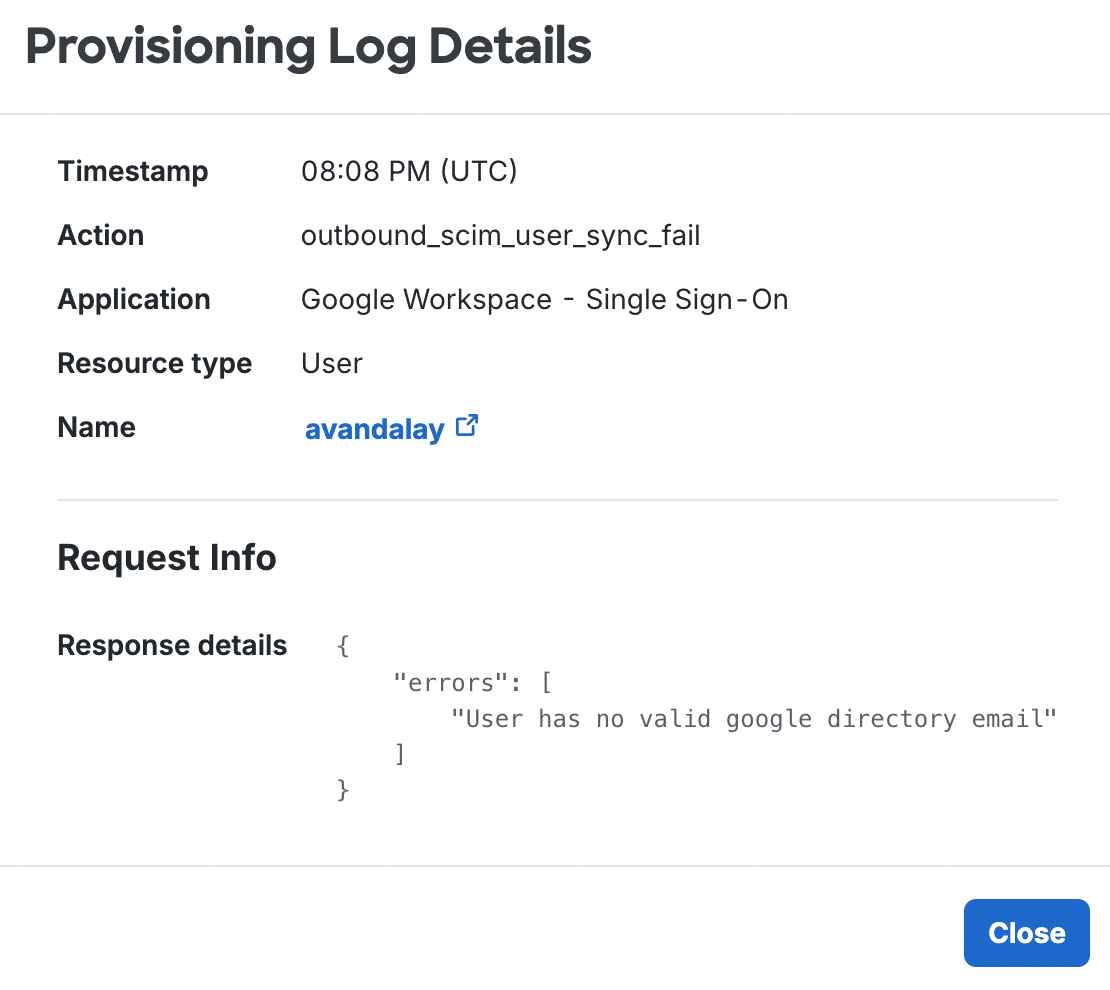
You may also visit the Administrator Actions report to view configuration change events from logged-in administrator actions.
Troubleshooting
Need some help? Take a look at our provisioning Knowledge Base articles or Community discussions. For further assistance, contact Support.
