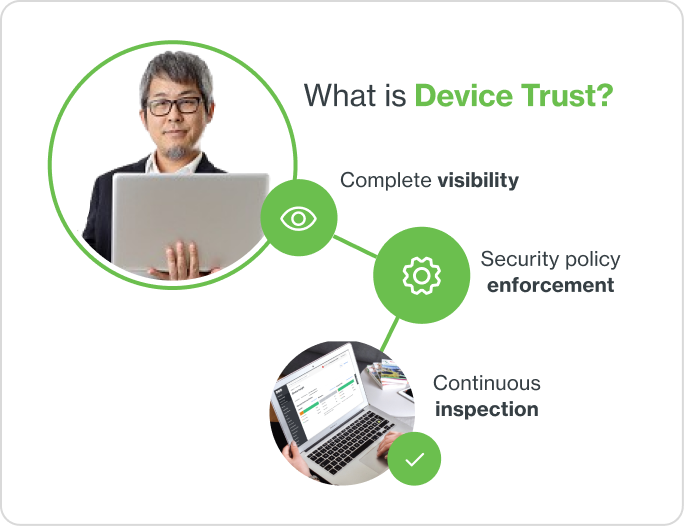
What is Device Trust?
Device trust refers to the process of verifying that a user’s device can be trusted to access your network and resources. Device trust includes determining if a device is known, up to date, secure, and compliant with organizational policies.
Why is device trust important?
Verifying device trust is important in hybrid and remote workforces to prevent unauthorized or compromised devices from accessing corporate networks and exposing them to threats.
Prevent data breaches – Device trust solutions provide comprehensive insight into the types of devices accessing corporate networks and applications, helping security teams monitor and flag risky devices to further secure their environment.
Achieve compliance – Organizations operating in regulated verticals need to ensure their modern IT environment complies with requirements – for example HIPAA, PCI-DSS, and NIST. Further, governments all over the globe are introducing data privacy laws such as GDPR and CCPA to hold organizations responsible for securing customer personally identifiable information (PII).
Balance security and productivity – It is critical to balance security and user productivity by verifying device trust in a manner that is easy for IT to manage and not disruptive to employee workflows.
What makes a device trusted?
There are key posture checks organizations should perform before granting access to attest whether a device is trustworthy:
Is the device managed?
Are the operating system (OS) and browser versions, including patch levels, up to date?
Is the enterprise antivirus (AV) agent installed and running?
Is the host firewall enabled?
Is disk encryption turned on?
Does the device have a password set?
Is the mobile device rooted or jailbroken?
Duo offers powerful security in an all-in-one solution that is platform agnostic, scalable, affordable, and easy for end users and administrators to use.
Broadest coverage – Duo offers the most comprehensive user and device trust capabilities on the market that cater to a diverse population of workforce devices (managed and unmanaged).
Ease of use – Duo helps organizations improve security in a manner that is user friendly and enables productivity. Users can self-enroll and self-remediate their authentication and access devices, reducing IT overhead.
Lower total cost of ownership – Duo is a stand-alone security solution that also integrates across the Cisco Security portfolio so customers (big or small) can reduce their total cost of ownership (TCO) by consolidating security vendors, streamlining security operations, and enabling automation.
The Essential Guide to Device Trust in the Enterprise
Learn about the challenges enterprises face in establishing device trust. See how Duo Device Trust delivers critical capabilities to help organizations minimize their risk surface, including real-world stories from Duo customers about how they use Duo Device Trust.
Read the Guide
PRODUCTDuo Desktop
Duo Desktop gives organizations more control over which laptop and desktop devices can access corporate applications.
Discover Duo Desktop
PRODUCTDuo Trust Monitor
Gain visibility and insight into what's normal and what’s atypical behavior as users and devices access your organization’s environment. Duo Trust Monitor delivers advanced anomaly detection by surfacing unusual access and device registration attempts, enabling you to detect and remediate compromised accounts proactively, and harden your network’s defenses.
Discover Duo Trust Monitor
Frequently Asked Questions
How do I secure remote access based on device trust?
Deploy a secure remote access solution that provides visibility into all devices on your network. Identifying risky devices and enforcing adaptive access policies enable you to allow application access to only healthy devices.
What is access management?
Access management is a set of tools and policy controls that ensures everyone has the right access to do their job, while preventing unauthorized access to sensitive information.
What is adaptive authentication?
Adaptive authentication is an advanced MFA feature that adjusts its security checks based on dynamic factors like user location, role, device, and other risk indicators.
Adaptive access policies allow just the right access level for each user, minimizing the risk of unauthorized entry and breaches. This ongoing verification of user and device trust for each access request helps secure a hybrid workforce and supports a zero trust approach to security.