Duo Single Sign-On for Ivanti Connect Secure
Last updated:
Overview
Duo's SAML SSO for Ivanti Connect Secure supports inline self-service enrollment and authentication with Duo Universal Prompt for Connect Secure VPN client and web-based SSL VPN logins. This deployment option features Duo Single Sign-On as a SAML 2.0 identity provider (IdP). Primary and Duo secondary authentication occur at the Duo identity provider, not at the Connect Secure device itself.
Tested Ivanti Connect Secure Servers and Clients
Ivanti Connect Secure was tested using the following minimum software versions and configurations:
- Pulse Connect Secure 9.1R11 and Ivanti Connect Secure 22.1R1
- Ivanti Secure Access Desktop Client 9.1.11
- Pulse Secure on iOS and Android
About Duo Single Sign-On
Duo Single Sign-On is our cloud-hosted SSO product which layers Duo's strong authentication and flexible policy engine on top of Ivanti Connect Secure logins. Duo Single Sign-On acts as an identity provider (IdP), authenticating your users using existing on-premises Active Directory (AD) or another SSO IdP. Duo SSO prompts users for two-factor authentication and performs endpoint assessment and verification before permitting access to Ivanti Connect Secure.
Duo Single Sign-On is available in Duo Premier, Duo Advantage, and Duo Essentials plans, which also include the ability to define policies that enforce unique controls for each individual SSO application. For example, you can require that Salesforce users complete two-factor authentication at every login, but only once every seven days when accessing Ivanti Connect Secure. Duo checks the user, device, and network against an application's policy before allowing access to the application.
Configure Single Sign-On
Before configuring Ivanti Connect Secure with Duo SSO using Security Assertion Markup Language (SAML) 2.0 authentication you'll first need to configure a working authentication source.
Once you have your SSO authentication source working, continue to the next step of creating the Ivanti Connect Secure application in Duo.
Prepare Ivanti Connect Secure for SSO
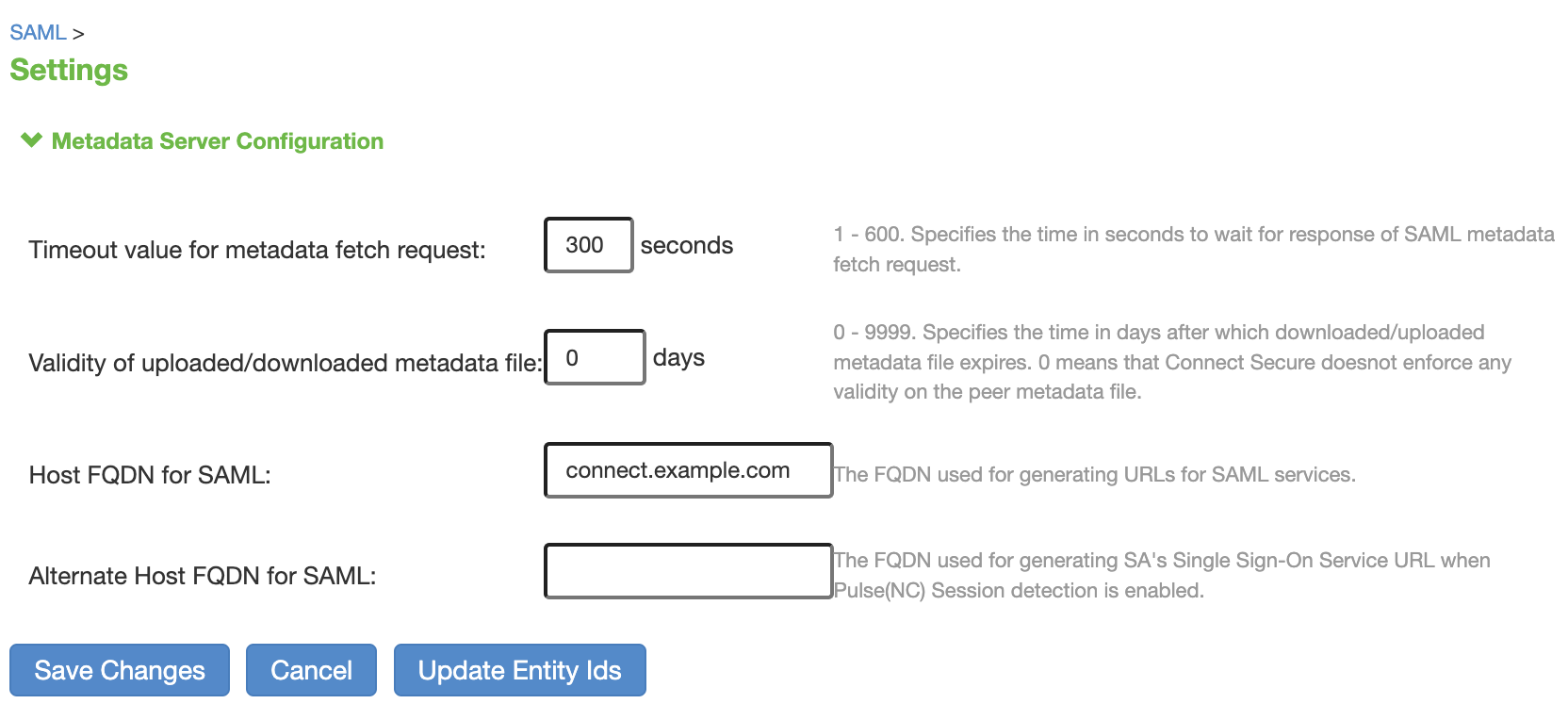
Create Host FQDN for SAML in Ivanti
-
Log into the admin console of your Ivanti Connect Secure.
-
In the menu near the top of the page hover over System then Configuration and then click on SAML.
-
On the "Configuration -> SAML" page click Settings.
-
On the "SAML -> Settings" page next to Host FQDN for SAML enter a fully qualified domain name that points to your Ivanti Connect Secure server.
-
Click Save Changes.
-
Click Update Entity Ids and then on the "Confirm Update Entity Ids" click Update Entity Ids again.
Create SAML Authentication Server
-
In the menu near the top of the page hover over Authentication and then click Auth. Servers.
-
On the "Authentication Servers" page next to New click on the drop-down and select SAML Server and then click the New Server... button. You'll be taken to a new page.
-
On the "New SAML Server" page enter a name for your server in the Server Name field such as Duo SSO.
-
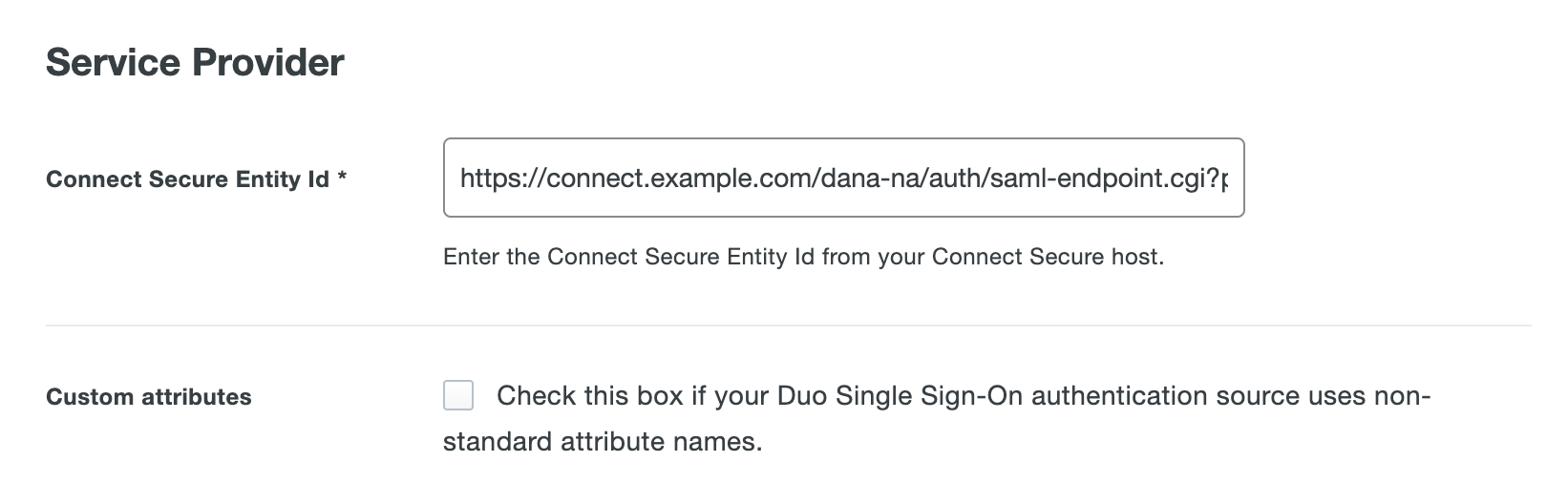
Verify the Connect Secure Entity Id starts with the Host FQDN for SAML you configured earlier. Leave this page open as you'll need it later.
Create the Ivanti Connect Secure Application in Duo
-
Log in to the Duo Admin Panel and navigate to Applications → Application Catalog.
-
Locate the entry for Ivanti Connect Secure with the "SSO" label in the catalog. Click the + Add button to start configuring Ivanti Connect Secure. See Protecting Applications for more information about protecting applications with Duo and additional application options. You'll need the information on the Ivanti Connect Secure page under Metadata later.
-
No active Duo users can log in to new applications until you grant access. Update the User access setting to grant access to this application to users in selected Duo groups, or to all users. Learn more about user access to applications. If you do not change this setting now, be sure to update it so that your test user has access before you test your setup.
This setting only applies to users who exist in Duo with "Active" status. This does not affect application access for existing users with "Bypass" status, existing users for whom the effective Authentication Policy for the application specifies "Bypass 2FA" or "Skip MFA", or users who do not exist in Duo when the effective New User Policy for the application allows access to users unknown to Duo without MFA. -
Copy the Connect Secure Entity Id from the Ivanti "New SAML Server" page into the Connect Secure Entity Id field in the Duo Admin Panel.
-
Ivanti Connect Secure uses the Mail attribute when authenticating. We've mapped the <Email Address> attribute to external authentication source attributes as follows:
Default Attribute Active Directory SAML IdP <Email Address> mail Email If you are using a non-standard email attribute for your authentication source, check the Custom attributes box and enter the name of the attribute you wish to use instead.
-
You can adjust additional settings for your new SAML application at this time — like changing the application's name from the default value, enabling self-service, or assigning a group policy.
-
Scroll to the bottom of the page and click the Save button. Leave this page open as you'll need it later.
Duo Universal Prompt
The Duo Universal Prompt provides a simplified and accessible Duo login experience for web-based applications, offering a redesigned visual interface with security and usability enhancements.
| Universal Prompt | Traditional Prompt |
 |
 |
We've already updated the Duo Ivanti Connect Secure application hosted in Duo's service to support the Universal Prompt, so there's no action required on your part to update the application itself. If you created your Ivanti Connect Secure application before March 2024, you can activate the Universal Prompt experience for users from the Duo Admin Panel. Ivanti Connect Secure applications created after March 2024 have the Universal Prompt activated by default.
If you created your Ivanti Connect Secure application before March 2024, it's a good idea to read the Universal Prompt Update Guide for more information, about the update process and the new login experience for users, before you activate the Universal Prompt for your application.
Activate Universal Prompt
Activation of the Universal Prompt is a per-application change. Activating it for one application does not change the login experience for your other Duo applications.
The "Universal Prompt" area of the application details page shows that this application is "Ready to activate", with these activation control options:
- Show traditional prompt: Your users experience Duo's traditional prompt via redirect when logging in to this application.
- Show new Universal Prompt: (Default) Your users experience the Universal Prompt via redirect when logging in to this application.
The application's Universal Prompt status shows "Activation complete" here and on the Universal Prompt Update Progress report.
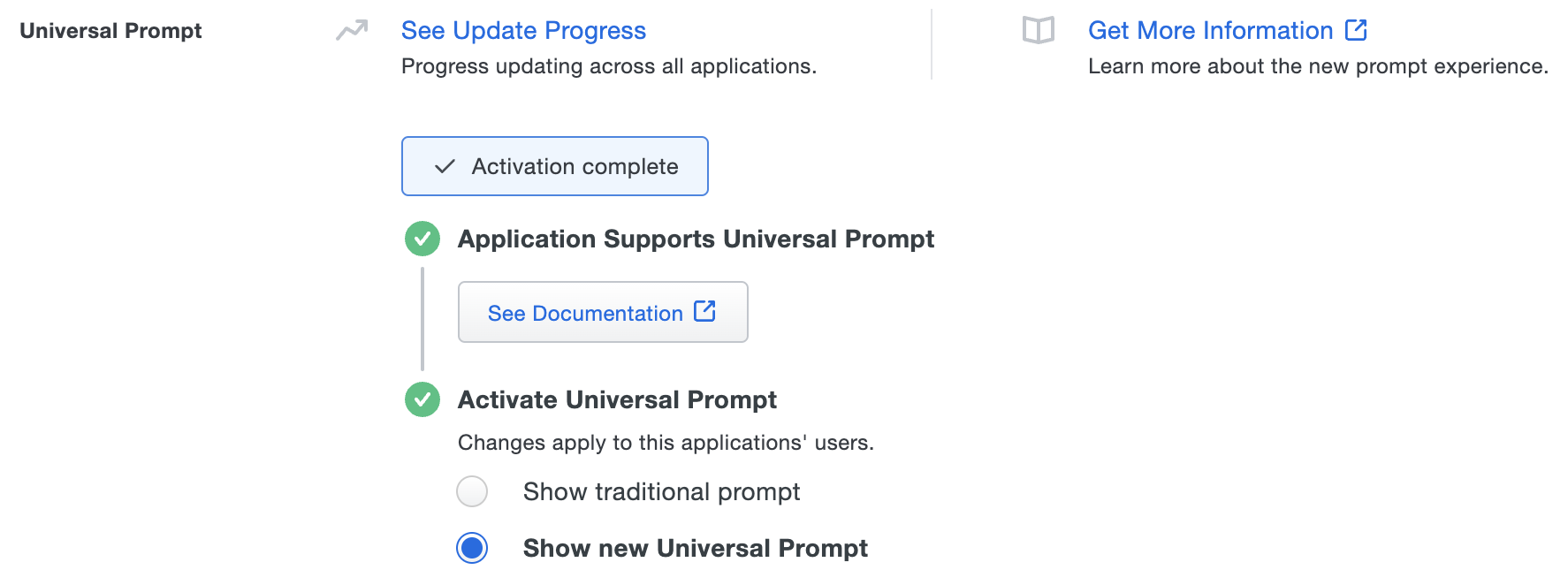
Should you ever want to roll back to the traditional prompt, you can return to this setting and change it back to Show traditional prompt. However, this will still deliver the Duo prompt via redirect, not in an iframe. Keep in mind that support for the traditional Duo prompt ended for the majority of applications in March 2024.
Universal Update Progress
Click the See Update Progress link to view the Universal Prompt Update Progress report. This report shows the update availability and migration progress for all your Duo applications. You can also activate the new prompt experience for multiple supported applications from the report page instead of visiting the individual details pages for each application.
Configure Ivanti Connect Secure
Add Duo Single Sign-On to Ivanti Connect Secure as a new single sign-on provider.
Configure SAML Authentication Server
-
Return back to the Ivanti Connect Secure page. Make sure you're still on the "New SAML Server" page from earlier.
-
Verify that Configuration Mode is set to Manual.
-
Under the "Settings" section make sure the SAML Version is set to 2.0.
-
Copy the Identity Provider Entity ID from the Duo Admin Panel Metadata section and paste it into the Ivanti Connect Secure Identity Provider Entity Id field.
Example: https://sso-abc1def2.sso.duosecurity.com/saml2/sp/DIABC123678901234567/metadata
-
Copy the Identity Provider Single Sign On Service URL from the Duo Admin Panel Metadata section and paste it into the Ivanti Connect Secure Identity Provider Single Sign On Service URL field.
Example: https://sso-abc1def2.sso.duosecurity.com/saml2/sp/DIABC123678901234567/sso
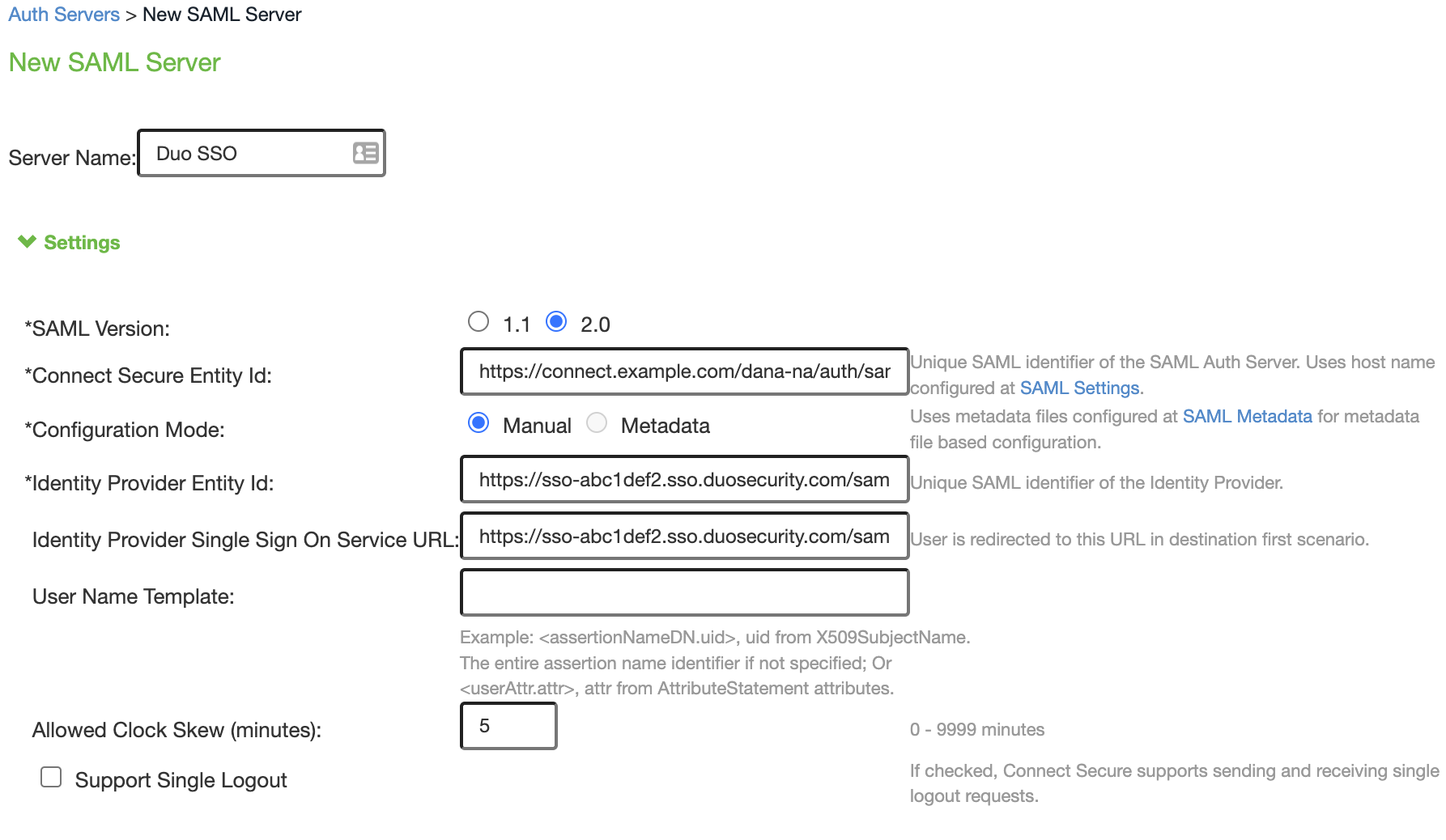
-
Scroll down to SSO Method leaving all other fields above it at their defaults. Verify that Post is selected next to Response Signing Certificate.
-
Click Download certificate next to "SAML Certificate" on the Ivanti Connect Secure application's page in the Duo Admin Panel under Downloads to download the Duo Single Sign-On signing certificate. Upload the certificate to the Response Signing Certificate section in Ivanti Connect Secure.
-
Scroll down to Metadata Validity and enter 9999 into the text field.
-
Click Save Changes
Create New User Realm
-
In the menu near the top of the page hover over Users and then click User Realms.
-
Click the New... button. You'll be taken to a new page.
-
On the "New Authentication Realm" page type in a name into the Name field.
-
Under "Servers" next to Authentication select your Duo SSO auth server from the drop-down.
-
Leave all other fields at their default. Click Save Changes. You'll be taken to the Role Mapping page.
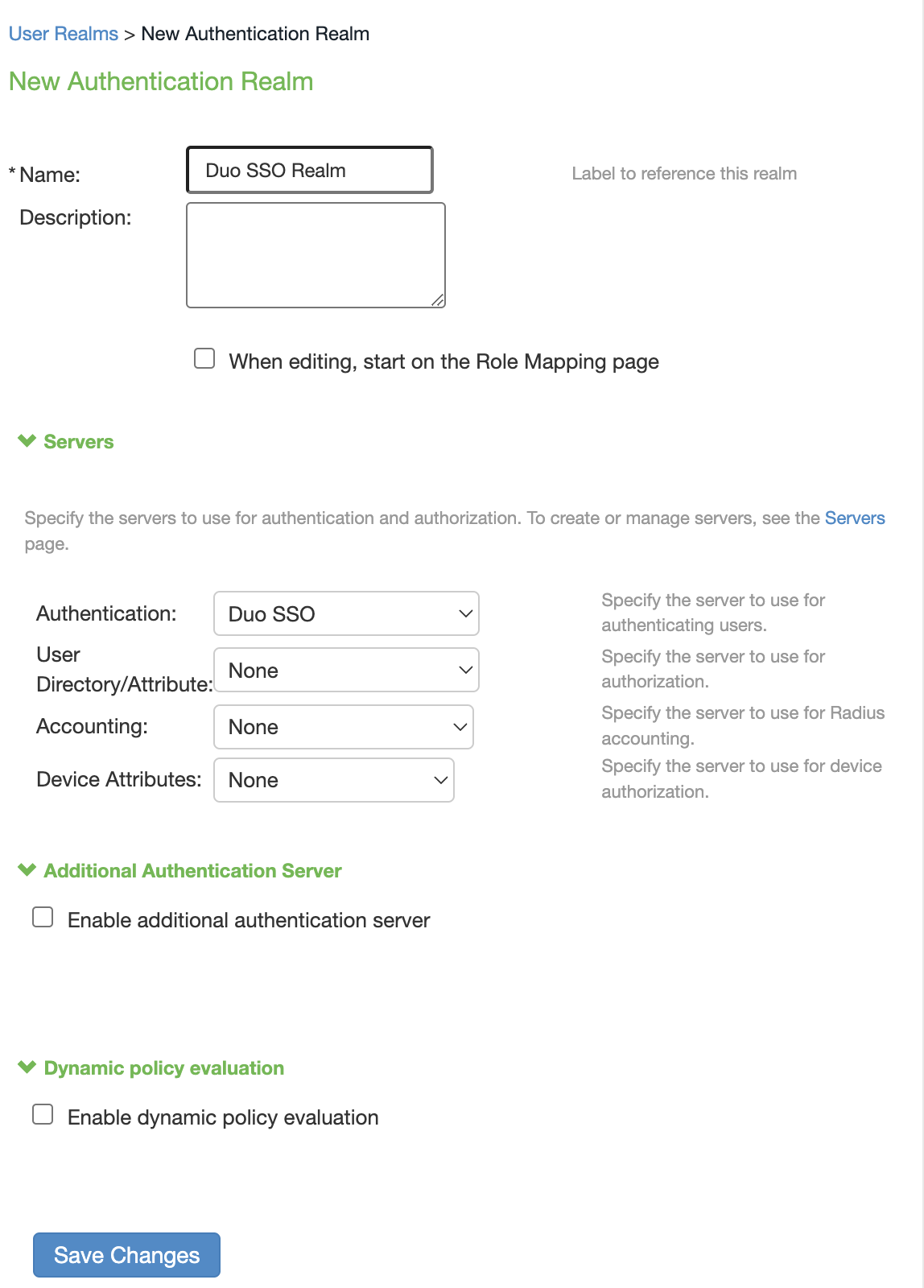
-
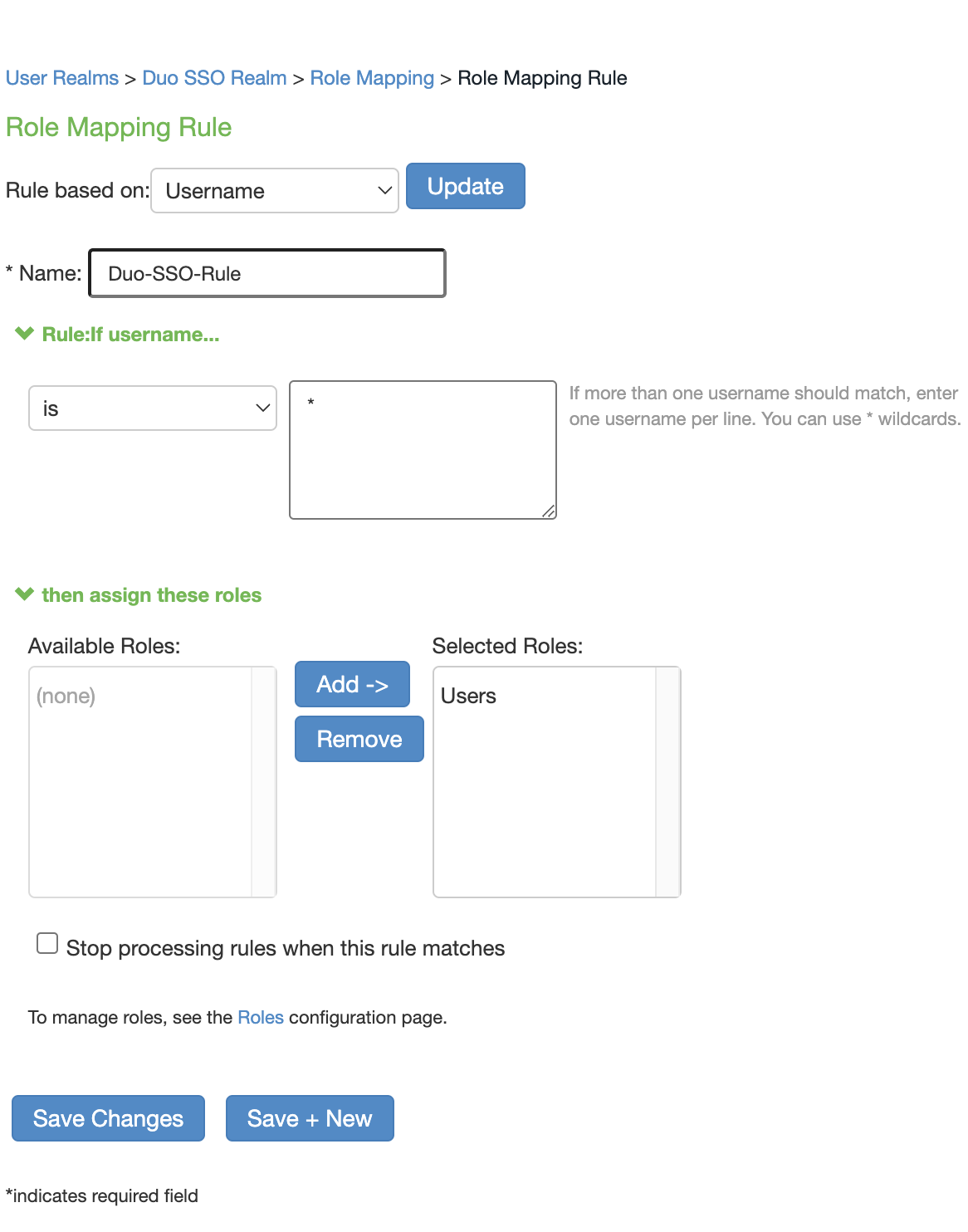
Click the New Rule... button. You'll be taken to the Role Mapping Rule page.
-
Leave Rule based on set to Username.
-
Enter a name for the rule into the Name field.
-
Under "Rule:If username" make sure is is select in the drop-down. In the textbox next to it type ✱. This will mean that all usernames will match this rule.
-
Under "then assign these roles" and "Available roles" select the Users role and then click Add -> so that it shows up under Selected Roles.
-
Click Save Changes. You'll be taken to the main Role Mapping page.
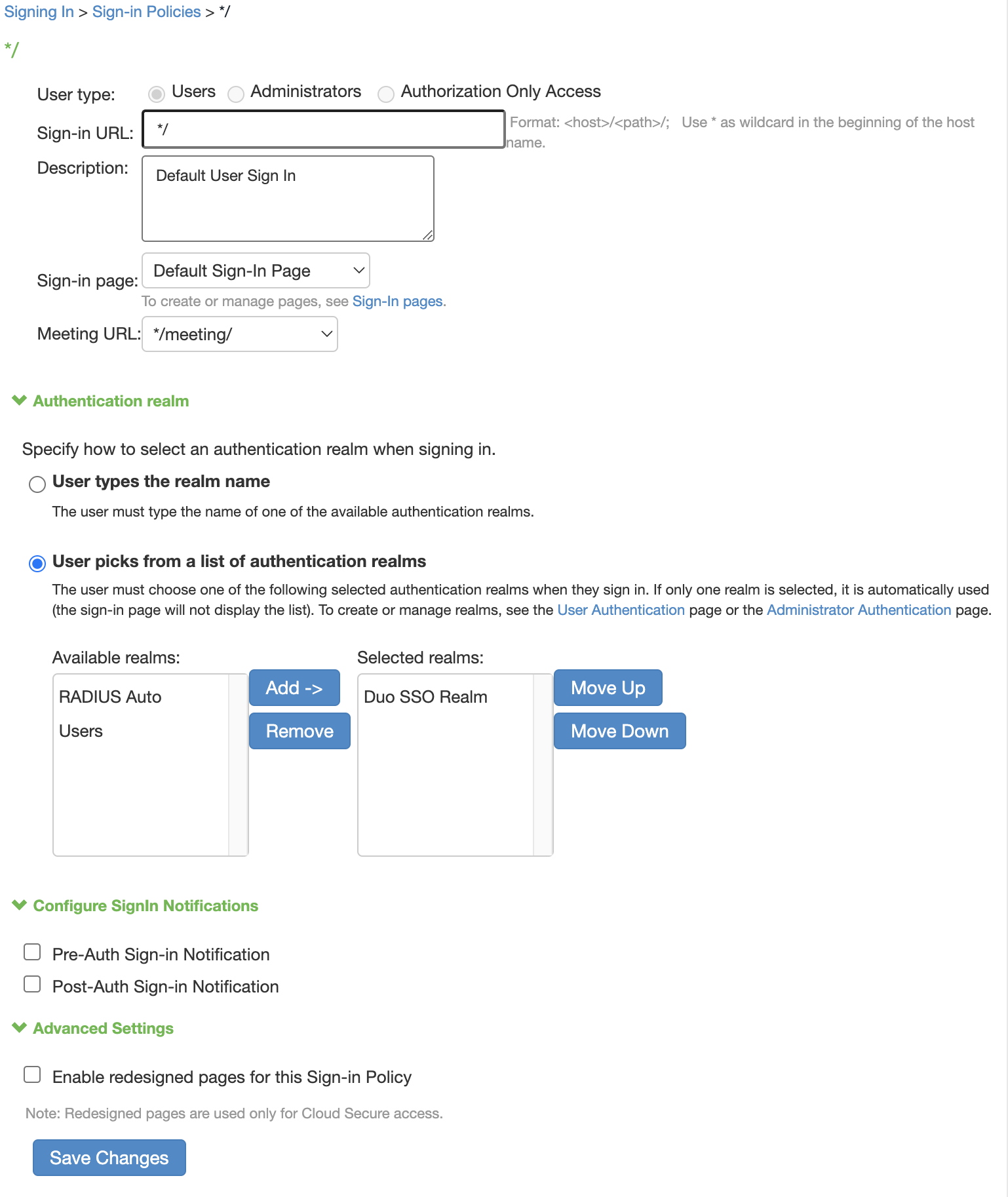
Modify Sign-In Policies
-
In the menu near the top of the page hover over Authentication then Signing In and click Sign-In Policies. You'll be taken to a new page.
-
On the "Sign-in Policies" page under User URLs click on the URL you'd like to use Duo SSO to sign in with. If you'd like this to impact the main URL select ✱/. You'll be taken to a new page.
-
On the policy page for the URL you clicked under "Authentication realms" select User picks from a list of authentication realms. New options will appear.
-
Under "Available realms" select the Duo SSO realm you created and click Add -> so it appears under "Selected Realms".
-
Click Save Changes.
Learn more about Ivanti Connect Secure SSO at Ivanti Support.
Verify SSO
You can log into your Ivanti Connect Secure using your organization’s login page e.g. https://connect.example.com. This redirects you to Duo Single Sign-On to begin authentication.
Active Directory Login
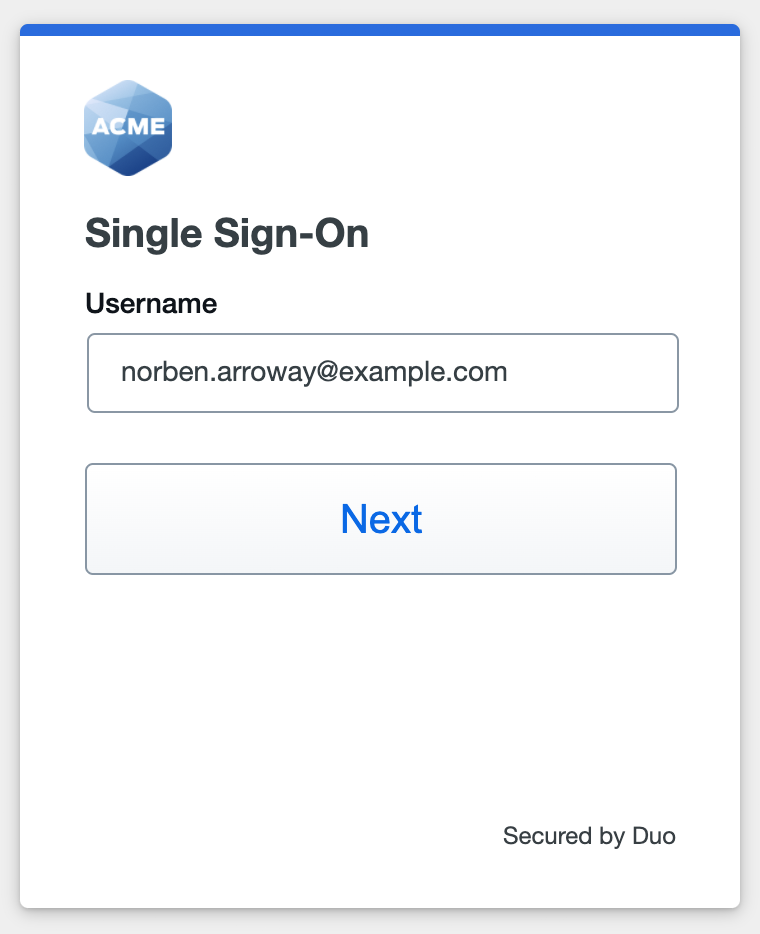
With Active Directory as the Duo SSO authentication source, enter the primary username (email address) on the Duo SSO login page and click or tap Next.
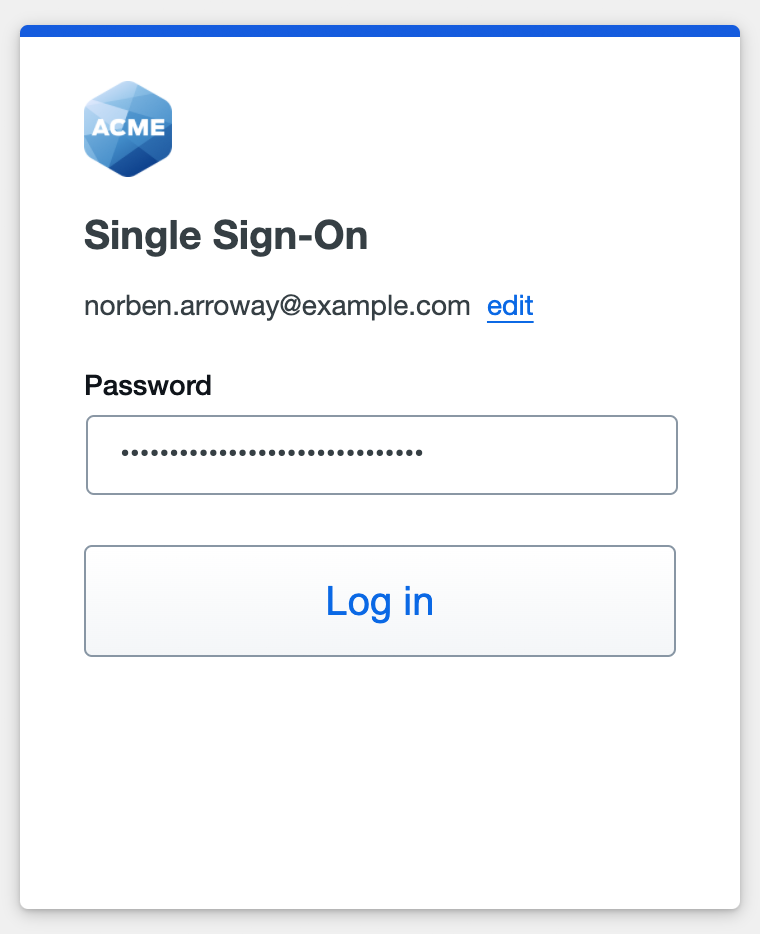
Enter the AD primary password and click or tap Log in to continue.
SAML Login
With another SAML identity provider as the Duo SSO authentication source, Duo SSO immediately redirects the login attempt to that SAML IdP for primary authentication. Users do not see the Duo SSO primary login screen.
Duo Authentication
Successful verification of your primary credentials by Active Directory or a SAML IdP redirects back to Duo. Complete Duo two-factor authentication when prompted and then you'll return to the VPN service to complete the login process.
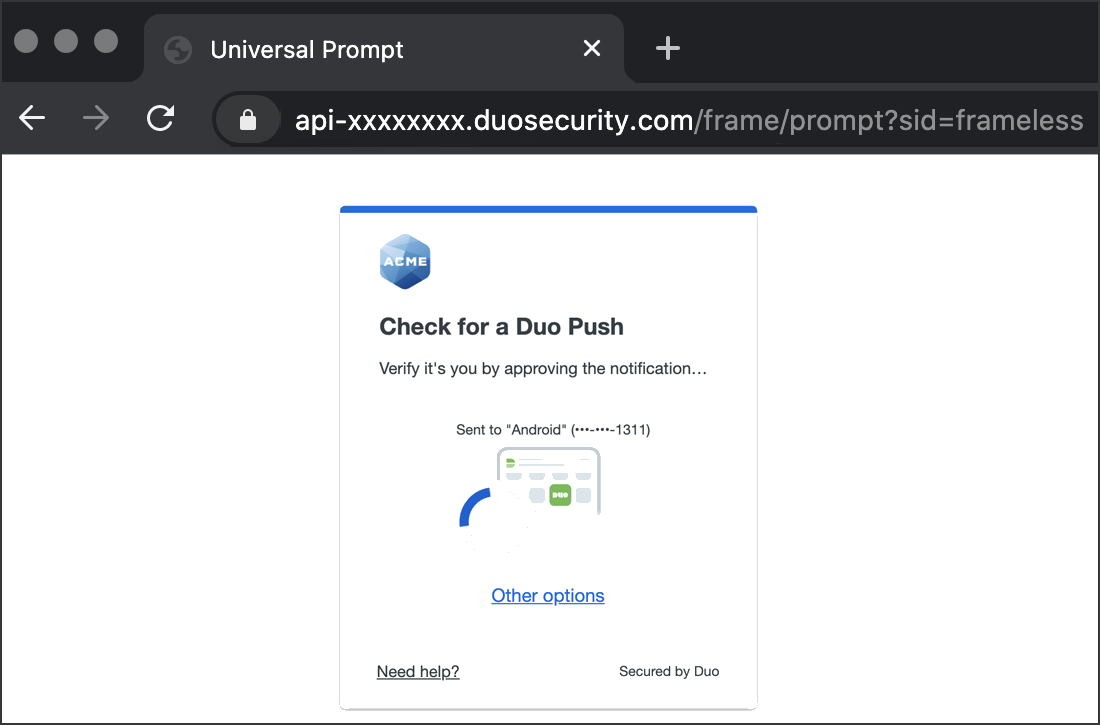
*Universal Prompt experience shown.
You can also log into Ivanti Connect Secure using Duo Central, our cloud-hosted portal which allows users to access all of their applications in one spot. Link to Ivanti Connect Secure in Duo Central by adding it as an application tile. Once the tile has been added, log into Duo Central and click the tile for IdP-initiated authentication to Ivanti Connect Secure.
Pulse Secure mobile or Ivanti Secure Access Client desktop apps will redirect you to authenticate to Duo Single Sign-On.
Congratulations! Your Ivanti Connect Secure users now authenticate using Duo Single Sign-On.
See the full Duo SSO user login experience, including expired password reset (available for Active Directory authentication sources) in the Duo End User Guide for SSO.
Grant Access to Users
If you did not already grant user access to the Duo users you want to use this application be sure to do that before inviting or requiring them to log in with Duo.
Enable Remembered Devices
To minimize additional Duo two-factor prompts when switching between Ivanti Connect Secure and your other Duo Single Sign-On SAML applications, be sure to apply a shared "Remembered Devices" policy to your SAML applications.
Automated Provisioning
You may be able to create, manage, and delete users and groups in this application automatically from Duo using SCIM 2.0 provisioning. See Automated Provisioning to learn how.
Troubleshooting
Need some help? Try searching our Knowledge Base articles or Community discussions. For further assistance, contact Support.
