Duo Protection for Microsoft 365 with Duo Access Gateway
Last updated:
Duo Access Gateway reaches Last Day of Support on October 26, 2023 for Duo Essentials, Advantage, and Premier customers. As of that date Duo Support may only assist with the migration of existing Duo Access Gateway applications to Duo Single Sign-On. Customers may not create new DAG applications after May 19, 2022. Please see the Guide to Duo Access Gateway end of life for more details.
Use the Duo Single Sign-on for Microsoft 365 application to protect Microsoft 365 with Duo Single Sign-On, our cloud-hosted identity provider featuring Duo Central and the Duo Universal Prompt.
Overview
Duo Access Gateway (DAG), our on-premises single sign-on product, layers Duo's strong authentication and flexible policy engine on top of Microsoft 365 logins using the Security Assertion Markup Language (SAML) 2.0 authentication standard. Duo Access Gateway acts as an identity provider (IdP), authenticating your users using existing on-premises Active Directory (AD) credentials and prompting for two-factor authentication before permitting access to Microsoft 365.
Once you federate a custom domain your Microsoft Online tenant with Duo Access Gateway, all Microsoft 365 applications will redirect those federated users to Duo Access Gateway when they sign in, while cloud-only (non-federated) users continue to log in using the Microsoft online sign-in form.
Be aware that Duo Access Gateway does not support WS-Trust. If you have clients that rely on WS-Trust, like Azure-joined workstations, deploy Duo Single Sign-On for Microsoft 365 instead. Duo Single Sign-On for Microsoft 365 supports WS-Trust.
Duo Access Gateway is part of the Duo Premier, Duo Advantage, and Duo Essentials plans, which also include the ability to define policies that enforce unique controls for each individual SSO application. For example, you can require that Salesforce users complete two-factor authentication at every login, but only once every seven days when accessing Microsoft 365. Duo checks the user, device, and network against an application's policy before allowing access to the application.
If you'd like to explore Duo solutions for Microsoft 365 that do not require deploying an on-premises SAML IdP, see our instructions for Duo for Azure Active Directory Conditional Access or Duo Single Sign-On for Microsoft 365.
Video Overview
Deploy or Update Duo Access Gateway
-
Install Duo Access Gateway on a server in your DMZ. Follow our instructions for deploying the server and configuring DAG settings.
-
Include the AD attributes mail,sAMAccountName,userPrincipalName,objectGUID in the "Attributes" field when configuring the Active Directory authentication source in the DAG admin console. You must use Active Directory as your authentication source; other DAG authentication sources do not support Microsoft 365 logins.
If you've already configured the attributes list for another cloud service provider, append the additional attributes not already present to the list, separated by a comma.
-
After completing the initial DAG configuration steps, click Applications on the left side of the Duo Access Gateway admin console.
-
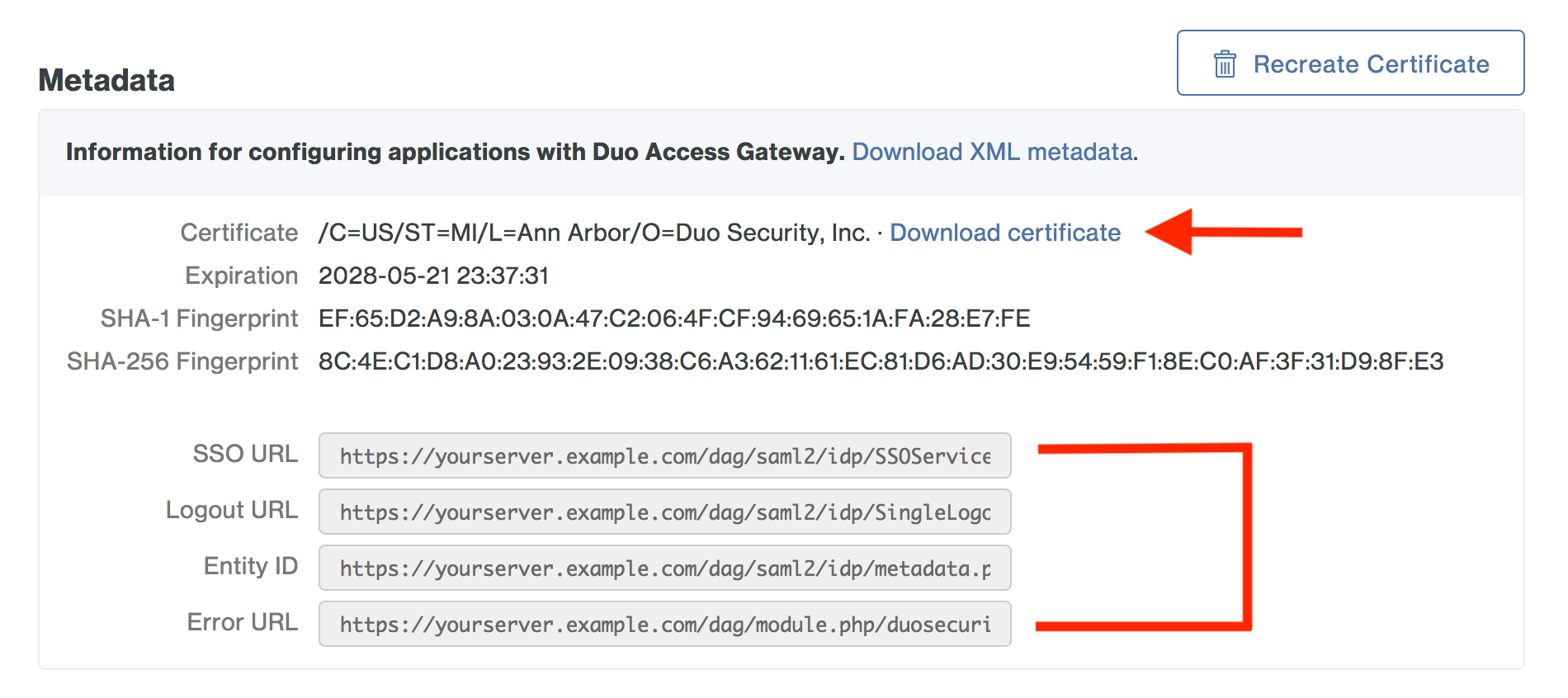
Scroll down the Applications page to the Metadata section. This is the information you need to provide to Microsoft 365 when configuring SSO. Click the Download Certificate link to obtain the token signing certificate (the downloaded file is named "dag.crt").
Create the Microsoft 365 Application in Duo
-
Log in to the Duo Admin Panel and navigate to Applications → Application Catalog.
-
Locate the entry for Microsoft 365 with the "DAG" label in the catalog. Click the + Add button to start configuring Microsoft 365. See Protecting Applications for more information about protecting applications with Duo and additional application options.
-
No active Duo users can log in to new applications until you grant access. Update the User access setting to grant access to this application to users in selected Duo groups, or to all users. Learn more about user access to applications. If you do not change this setting now, be sure to update it so that your test user has access before you test your setup.
This setting only applies to users who exist in Duo with "Active" status. This does not affect application access for existing users with "Bypass" status, existing users for whom the effective Authentication Policy for the application specifies "Bypass 2FA" or "Skip MFA", or users who do not exist in Duo when the effective New User Policy for the application allows access to users unknown to Duo without MFA. -
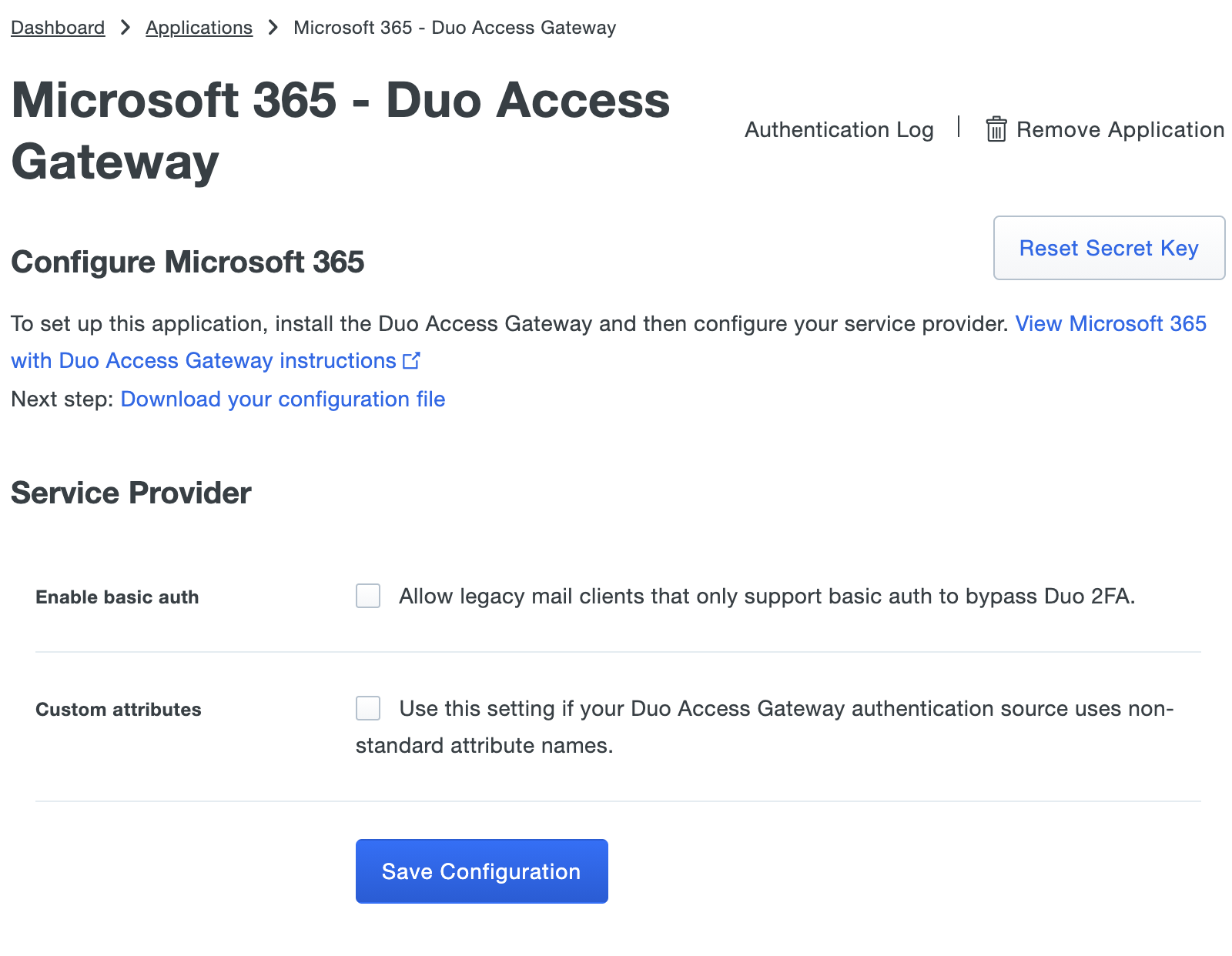
You can optionally check the box next to Enable Basic Auth to allow legacy mail clients that do not support Modern Auth to still log in using only their AD username and password. When this option is configured users logging in with legacy mail clients will bypass Duo 2FA. If this option is not chosen any mail client that does not support Modern Auth will not be able to log in.
When Microsoft sends a basic authentication request to the Duo Access Gateway it will only send the username preceding the domain name. For example, if the email address is
alice@example.com, only "alice" will be sent. This means that the Duo Access Gateway must be configured with a "Search attribute" on the Authentication Sources page which maps to an AD source attribute that is an exact match for the username segment of the user's email address preceding the@.The user's status in Duo and the effective enrollment policy of the Microsoft 365 application will be checked against Duo before authentication completes. If the effective New User policy for the Microsoft 365 Duo application is one that enforces enrollment (like "Require enrollment" or "Deny Access"), then any user logging in with basic authentication must exist in Duo with a 2FA device even though 2FA approval isn't required during M365 basic authentication.
Ensure that users logging in with basic authentication through Duo are not also required to complete Azure MFA. If a policy applied to the basic auth users enforces Azure MFA, basic auth through the Duo Access Gateway fails, preventing mailbox access.
Important: If you are currently using Microsoft 365 with the Duo Access Gateway and federated your Microsoft tenant before August 2017 please follow the steps in this KB article to revert your tenant back to managed and then federate your Microsoft tenant with an updated configuration.
-
If you checked Enable Basic Auth you can optionally check the box next to Basic Auth groups which will let you specify Duo groups; this option will allow basic auth for only members of those groups.
-
Microsoft 365 uses the Mail attribute and Object-GUID attribute when authenticating. We've mapped Mail attribute and Object-GUID attribute to DAG supported authentication source attributes as follows:
Duo Attribute Active Directory Mail attribute mail Object-GUID attribute objectGUID If you are using non-standard Mail or Object-GUID attributes for your authentication source, check the Custom attributes box and enter the name of the AD attributes you wish to use instead.
-
Click Save Configuration to generate a downloadable configuration file.
-
You can adjust additional settings for your new SAML application at this time — like changing the application's name from the default value, enabling self-service, or assigning a group policy — or come back and change the application's policies and settings after you finish SSO setup. If you do update any settings, click the Save button at the bottom of the page when done.
-
Click the Download your configuration file link to obtain the Microsoft 365 application settings (as a JSON file).
Important: This file contains information that uniquely identifies this application to Duo. Secure this file as you would any other sensitive or password information. Don't share it with unauthorized individuals or email it to anyone under any circumstances!
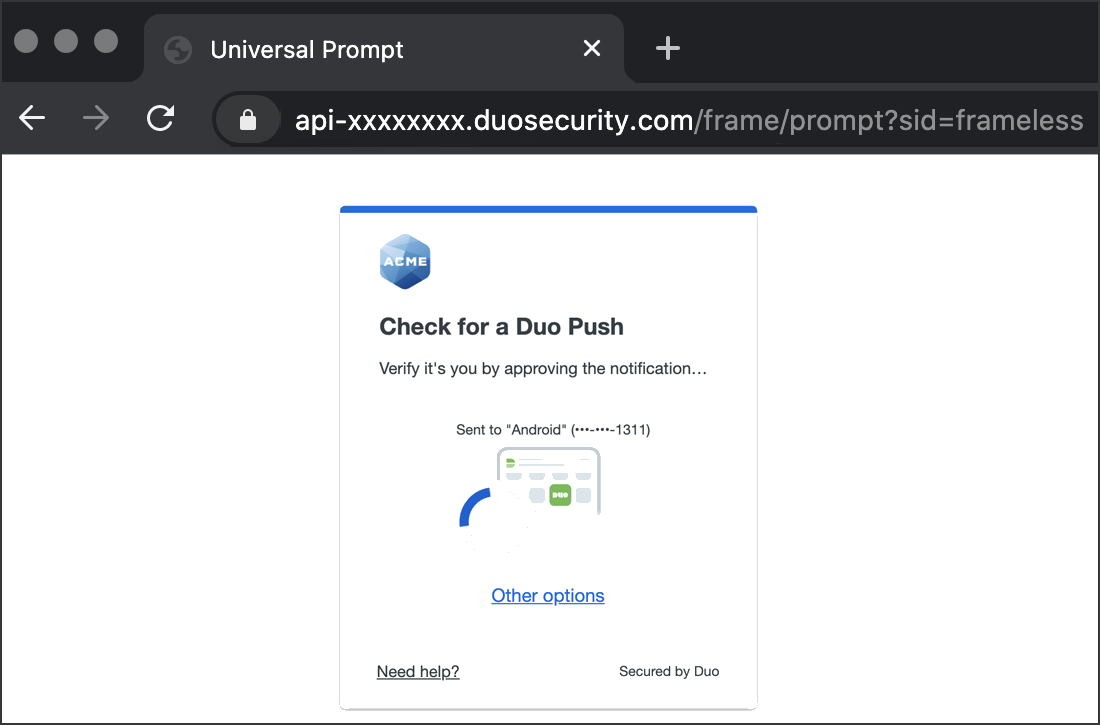
Duo Universal Prompt
The Duo Universal Prompt provides a simplified and accessible Duo login experience for web-based applications, offering a redesigned visual interface with security and usability enhancements.
| Universal Prompt | Traditional Prompt |
 |
 |
Read the Universal Prompt Update Guide for more information about the update process and the new login experience for users.
Duo Access Gateway Universal Prompt support is available to Duo Federal customers only starting with version 2.0.0. Activating Universal Prompt for DAG applications requires the following steps:
- Enable Use frameless in the local DAG server admin console on the **General** page.
- Complete the federation steps in this document for your SAML app.
- Log in as an end user and complete Duo authentication to the SAML application now federated with your Duo Access Gateway server. This first authentication shows the traditional Duo prompt in a redirect instead of an iframe.
- You then activate the Universal Prompt for all users of that specific DAG SAML application.
The "Universal Prompt" section of your DAG SAML app shows the status as "Update Required" when you first create it. The status will change after you log into the application and complete Duo authentication to the SAML application now federated with your Duo Access Gateway server.
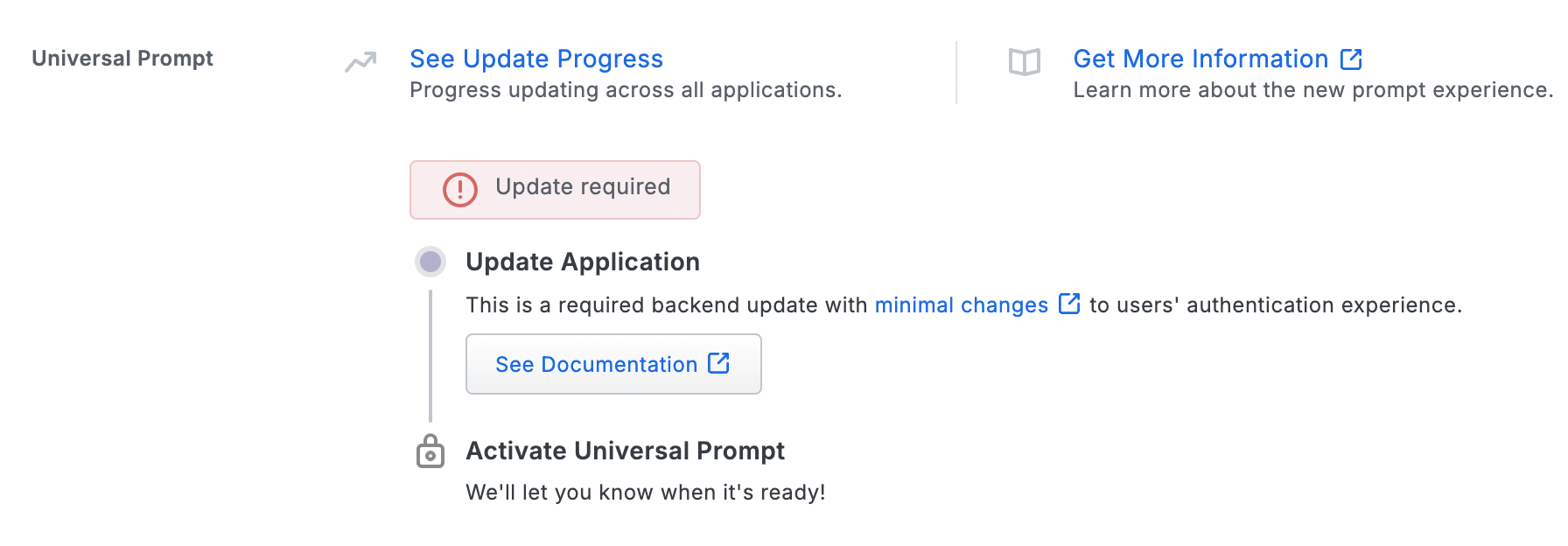
Edit the Duo JSON for GCC High
If your Microsoft 365 tenant is in GCC High then you must edit the JSON file you downloaded from the Duo Admin Panel before continuing.
The service URLs for Microsoft GCC High tenants end with 'microsoftonline.us' instead of 'microsoftonline.com'.
-
Open the JSON file you downloaded from the Duo Admin Panel in the previous step. If you did not rename your Microsoft 365 application before saving the configuration then the JSON file name is
Microsoft 365 - Duo Access Gateway.json. -
Locate the
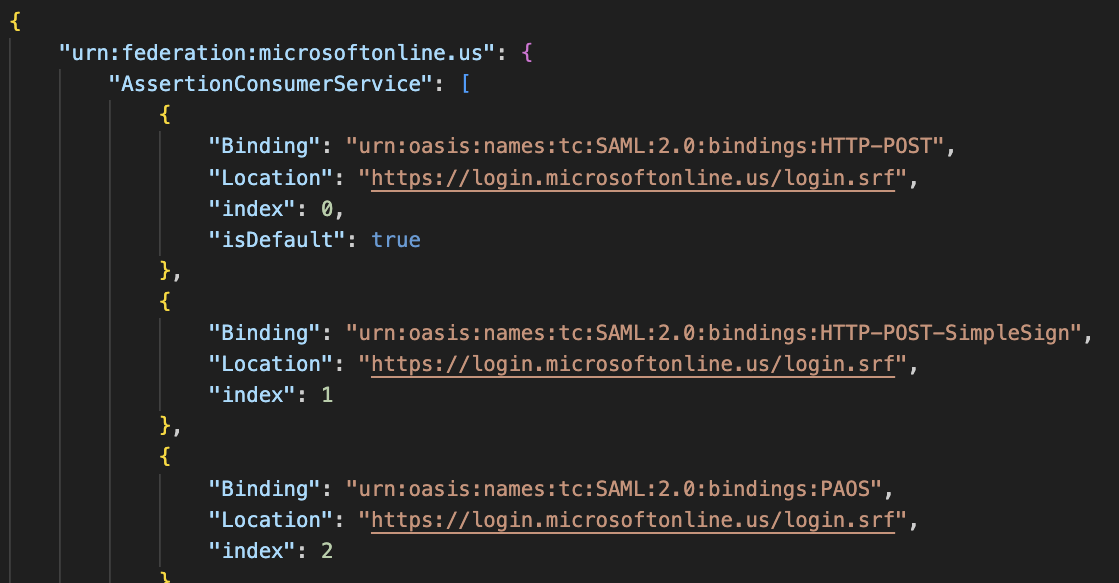
urn:federation:MicrosoftOnlineline in the JSON file, and change it to:urn:federation:microsoftonline.us(note this is case-sensitive). -
Locate the three instances of
login.microsoftonline.comand change them tologin.microsoftonline.us. -
Verify the edits to the JSON file are correct, and then save the file.
Add the Microsoft 365 Application to Duo Access Gateway
Before you do this, verify that you updated the "Attributes" list for your Duo Access Gateway AD authentication source as specified here.
-
Return to the Applications page of the DAG admin console session.
-
Click the Choose File button in the "Add Application" section of the page and locate the Microsoft 365 SAML application JSON file you downloaded from the Duo Admin Panel earlier. Click the Upload button after selecting the JSON configuration file.
-
The Microsoft 365 SAML application is added.
Enable Microsoft 365 SSO
When you federate a custom domain in your Microsoft 365 tenant with an external identity provider, like Duo Access Gateway, all of the users in that domain will be required to log into M365 resources and applications via Duo. You may want to add a separate custom domain which only contains test users so that you can verify federation works before you make changes to the custom domain that contains your actual users.
In order to federate your Microsoft 365 tenant with an external identity provider (like Duo Access Gateway) you must have added a custom domain to Microsoft 365. You cannot federate your "onmicrosoft.com" domain. Additionally, the custom domain you have added to Microsoft 365 cannot be set as the default domain.
We recommend that you have a tenant administrator account in your "onmicrosoft.com" so you don't lock yourself out of your tenant.
Enable Directory Synchronization in Microsoft 365
If you previously configured directory synchronization between your on-premises AD domain and Microsoft 365, skip these steps and proceed to Enable AD Federation to Microsoft 365 using DAG.
However, if you have already configured AD to Microsoft 365 synchronization and did not select the objectGUID attribute as the Source Anchor note that you cannot modify the selected Source Anchor attribute and must uninstall and reinstall Azure AD Connect in order to change it.
-
Log in to the Office Admin portal as the tenant administrator and open the Add or sync users to Microsoft Entra ID setup action. Click Get started to begin setup and step through the guided prompts.
-
On a computer joined to your AD domain open PowerShell and run
Install-Module Microsoft.Graphas described here to install the Microsoft Graph PowerShell SDK. -
When prompted to download and run Entra Connect, do not use the "Express Settings" and instead select Customize to perform a Custom installation of Entra Connect.
-
When on the "User sign-in" page of the Entra Connect tool select Do not configure as the "Sign On method". When on the "Uniquely identifying your users" page, under "Select how users should be identified with Microsoft Entra ID" select Choose a specific attribute and then select objectGUID from the drop-down.
-
Verify successful Active Directory Synchronization and activate Microsoft 365 licensing for unlicensed synchronized users.
Enable AD Federation to Microsoft 365 using DAG
The transition of your Microsoft 365 tenant from "managed" to "federated" is typically quick but Microsoft states that it can take two hours or more. Please plan accordingly when enabling federation (or restoring your existing federation configuration back to managed to switch from a previous solution to Duo Access Gateway), as the transition may temporarily impact your users' login access.
-
Log on to the domain-joined computer where you installed the Microsoft Graph PowerShell SDK.
-
Launch PowerShell and enter
Import-Module Microsoft.Graph. -
Enter this Microsoft Graph command in PowerShell:
Connect-MgGraph -Scopes "Domain.ReadWrite.All", "Directory.Read.All"If you are a Microsoft US Gov customer, you need to specify that environment in the Microsoft Graph command:
Connect-MgGraph -Environment USGov -Scopes "Domain.ReadWrite.All", "Directory.Read.All"Enter your Microsoft 365 administrator credentials for the domain you will be configuring for SSO using Duo Access Gateway.
-
Verify that your Microsoft 365 domain is not currently federated with this command:
Get-MgDomain -DomainName "your365domain.com"Look for "Managed" in the output.
Name Status Authentication ---- ------ -------------- your365domain.com Verified ManagedIf your Microsoft 365 domain is using Federated authentication, you need to convert it from Federated to Managed to modify the SSO settings.
Update-MgDomain -DomainId your365domain.com -AuthenticationType ManagedRerun the
Get-MgDomaincommand again to verify that the Microsoft 365 domain is no longer federated. -
Open the
dag.crtfile downloaded from the Duo Access Gateway admin console in a text editor. You will need thecertDatavalue from this file to complete federation. -
Gather the federation parameter information.
Parameter Description or Value DomainName The fully qualified Microsoft 365 tenant domain name (FQDN) to update: your365domain.com IssuerUri / MetadataUri The Entity ID URL from the DAG Metadata shown in the DAG admin console: https://yourserver.example.com/dag/saml2/idp/metadata.php PassiveLogOnUri / ActiveUri The DAG login URL where web clients are redirected when signing in to Microsoft 365. This is the SSO URL from the DAG Metadata shown in the DAG admin console: https://yourserver.example.com/dag/saml2/idp/SSOService.php LogOffUri The DAG logout URL where web clients are redirected when signing out of Microsoft 365. This is the Logout URL from the DAG Metadata shown in the DAG admin console: https://yourserver.example.com/dag/saml2/idp/SingleLogoutService.php -
Download the
Microsoft_365_DAG.ps1script from Duo and copy it to the system with the Microsoft Graph PowerShell SDK. -
Open the downloaded
Microsoft_365_DAG.ps1script in a text editor and update the first eight lines with the parameter information you gathered in step 7 and the contents of thedag.crtcertificate file as$certDatafrom step 6, as shown in this example:$dom = 'yourdomain365.com' $fedBrandName = 'DAG SSO' $issuerUri = 'https://yourserver.example.com/dag/saml2/idp/metadata.php' $passiveUri = 'https://yourserver.example.com/dag/saml2/idp/SSOService.php' $activeUri = 'https://yourserver.example.com/dag/saml2/idp/SSOService.php' $metadataUri = 'https://yourserver.example.com/dag/saml2/idp/metadata.php' $logoffUri = 'https://yourserver.example.com/dag/saml2/idp/SingleLogoutService.php' $certData = '-----BEGIN CERTIFICATE----- MIIDZDCCAexamplecertdata -----END CERTIFICATE----- 'The
$fedBrandNamevalue can be any name you wish.If you are a Microsoft US Gov customer, edit the script to specify that environment in the Microsoft Graph Connect-MgGraph command. Locate this line in the script:
Connect-MgGraph -ErrorAction Stop -scopes "Domain.ReadWrite.All, Domain.Read.All, Directory.Read.All, Directory.AccessAsUser.All"and insert "-Environment USGov" before the scopes, so it looks like:
Connect-MgGraph -ErrorAction Stop -Environment USGov -scopes "Domain.ReadWrite.All, Domain.Read.All, Directory.Read.All, Directory.AccessAsUser.All" -
Save the
Microsoft_365_DAG.ps1script after making the changes. -
Run the edited
Microsoft_365_DAG.ps1script from PowerShell from the directory where the edited script is located with this command, which permits a one-time bypass of your PowerShell execution policy to complete federation:powershell -ep ByPass "&'.\Microsoft_365_DAG.ps1'" -
As the PowerShell script runs it informs you of the steps it takes and asks for your confirmation when necessary. Follow the prompts to federate your domain to your Duo Access Gateway server.
You must provide a Microsoft 365 tenant administrator username and password during the flow to complete the federation. If you are running this script on a Windows Server operating system and Internet Explorer Enhanced Security Mode is enabled you may need to add websites used during the authentication process to your trusted sites.
-
When the script completes the domain federation process it will output the new federated settings for your Microsoft 365 domain.
Verify SSO
Navigate to https://login.microsoftonline.com and enter your Microsoft 365 username or email address (with no password). You will be automatically redirected to your Duo Access Gateway sign-in page to complete authentication. Enter your Active Directory username and password on the Duo Access Gateway login page, and approve the prompt for Duo two-factor authentication. You are logged into Microsoft 365.

Congratulations! Your Microsoft 365 users now authenticate using Duo Access Gateway.
Activate Universal Prompt
Once you authenticate to your newly-federated SAML application, the "Universal Prompt" section of the application's details page in the Admin Panel reflects this status as "Ready to activate", with these activation control options:
- Show traditional prompt: (Default) Your users experience Duo's traditional prompt via redirect when logging in to this application.
- Show new Universal Prompt: Your users experience the Universal Prompt via redirect when logging in to this application.
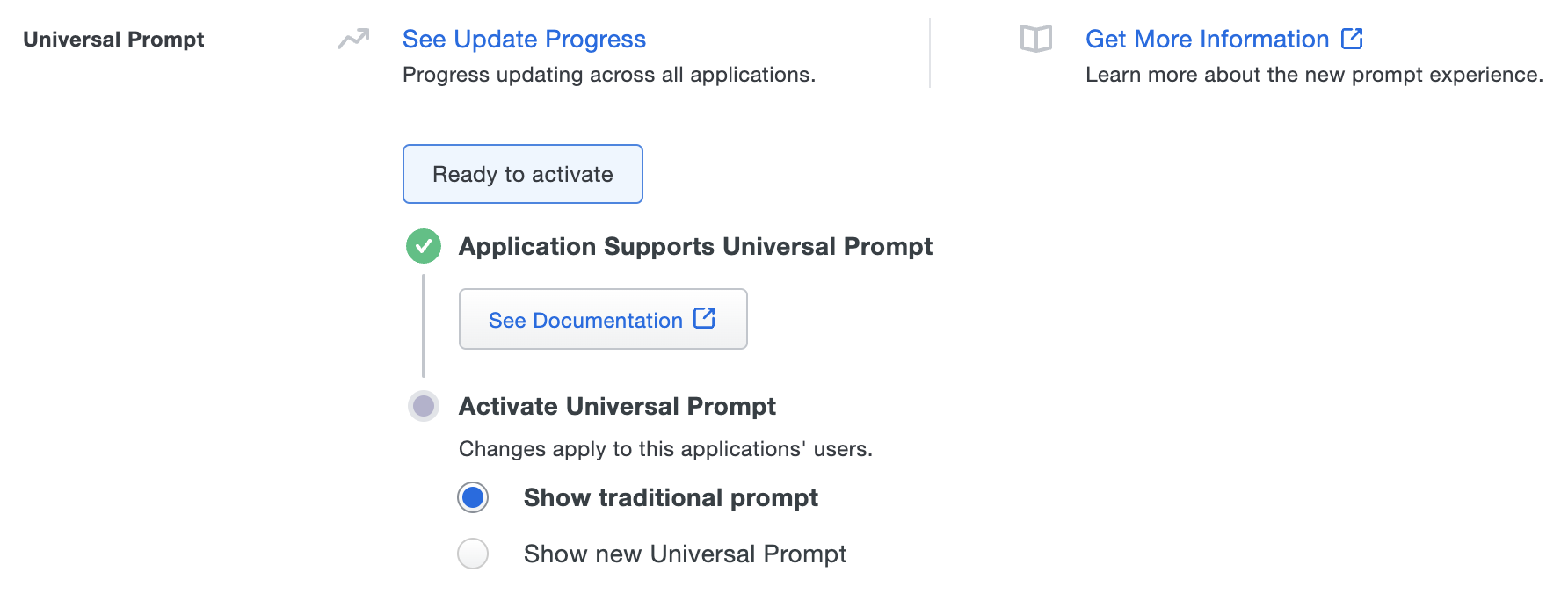
Enable the Universal Prompt experience by selecting Show new Universal Prompt, and then scrolling to the bottom of the page to click Save.
Once you activate the Universal Prompt, the application's Universal Prompt status shows "Activation Complete" here and on the Universal Prompt Update Progress report.
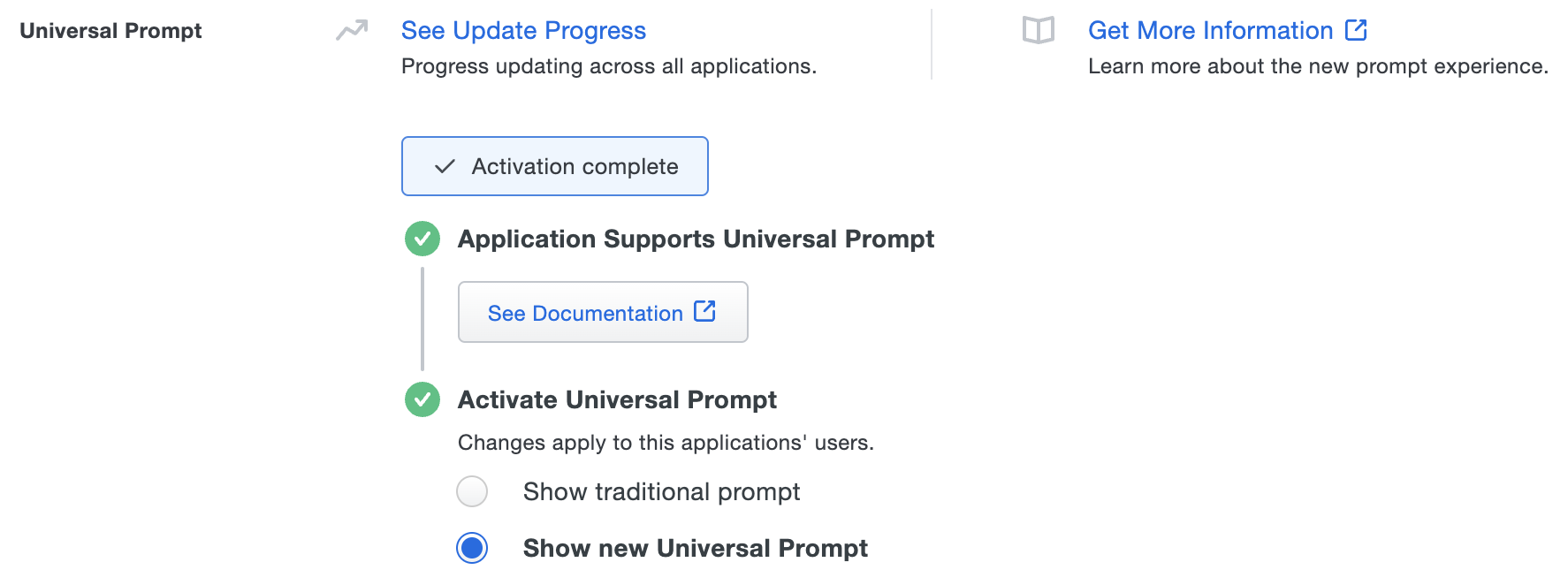
The next time your users log in to this application, they will see the new Universal Prompt experience instead of the traditional Duo prompt.
If you plan to permit use of WebAuthn authentication methods (security keys, U2F tokens, or Touch ID) in the traditional Duo Prompt, Duo recommends configuring allowed hostnames for this application and any others that show the inline Duo Prompt before onboarding your end-users.
The Duo Universal Prompt has built-in protection from unauthorized domains so this setting does not apply.
Grant Access to Users
If you did not already grant user access to the Duo users you want to use this application be sure to do that before inviting or requiring them to log in with Duo.
Office Client Access
Office 2013 and later desktop applications (including Outlook and Skype for Business) can connect to Microsoft 365 after federation with the Duo Access Gateway, implementing the Duo custom control for Azure conditional access, or Duo AD FS adapter installation only if Modern Authentication is enabled for your Microsoft 365 tenant. More information about Modern Authentication, including a list of Office applications that support Modern Authentication, is available at the Office Blog.
- Modern Authentication may already be enabled on your Microsoft 365 tenant. Follow these instructions to verify or enable Modern Authentication on your Exchange Online tenant and these instructions to do the same for your Skype for Business Online tenant.
- Apply registry updates for Office 2013 (Office 2016 and later applications and Skype for Business natively support Modern Authentication).
Please see the DAG FAQ or ADFS FAQ for additional details.
When you log in to Microsoft 365 for the first time after federation using an Office application, you'll see the Duo Access Gateway primary login page within the Office application, followed by the Duo authentication prompt.
Important: If users had a preexisting Microsoft 365 Outlook profile before federating with the Duo Access Gateway they might not be able to log in with modern authentication after federation and may then need to delete the existing Microsoft 365 client credentials in order to log in with Modern Authentication. Learn how to delete Microsoft 365 client credentials and more about M365 mail client behavior with Duo.
Outlook and Duo Access Gateway
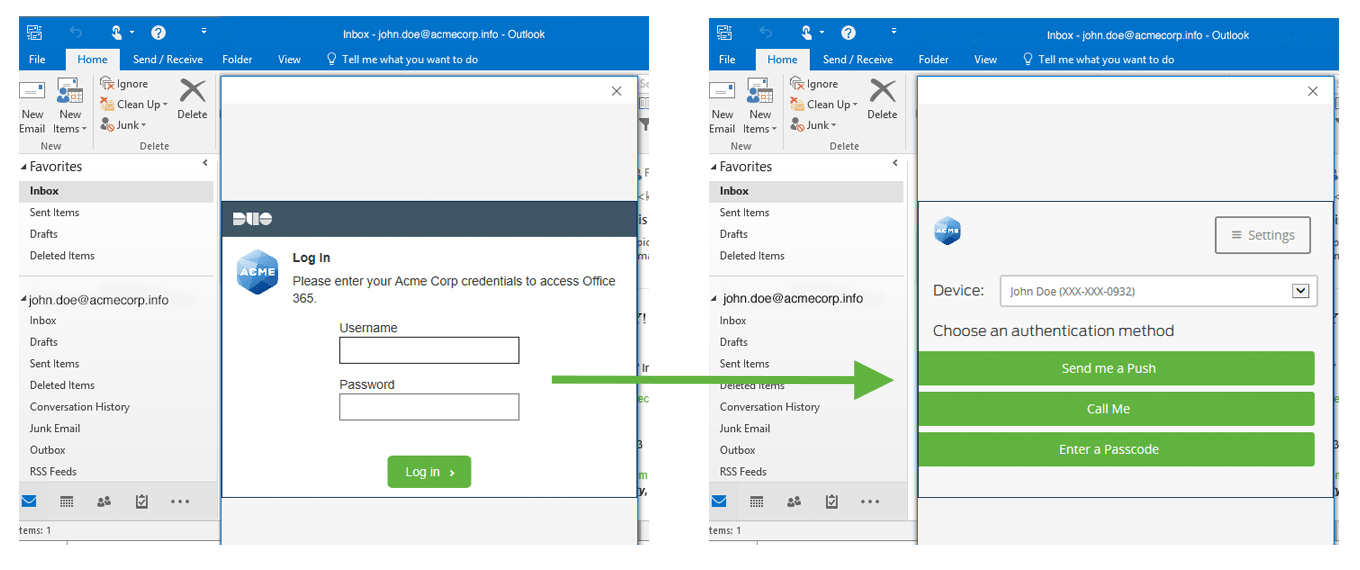
Office Apps and Mail Clients
Microsoft 365 rich clients that support Modern Authentication that are configured after federation will see the Duo Access Gateway login page within the mail client, followed by the Duo authentication prompt.
Clients that do not support Modern Authentication will not be able to log in unless the Enable Basic Auth setting is enabled in the Create the Microsoft 365 Application in Duo section. If the option is enabled users will continue to log into their mail clients using only their username and password.
Service Accounts
If you use service accounts to send e-mails from devices that don't support Modern Authentication, such as copiers, printers, or scanners, you can use the Enable Basic Auth setting in the Create the Microsoft 365 Application in Duo section to allow those accounts to continue to send e-mail. You will need to create Duo user accounts for the service accounts.
Troubleshooting
Need some help? Take a look at our Microsoft 365 Knowledge Base articles or Community discussions. For further assistance, contact Support.
