Duo Trusted Endpoints - Active Directory Domain Services
Last updated:
Overview
Duo's Trusted Endpoints feature secures your sensitive applications by ensuring that only known devices can access Duo protected services. When a user authenticates via the Duo Prompt, we'll check for the presence of Duo Desktop. You can monitor access to your applications from trusted and untrusted devices, and optionally block access from unmanaged, untrusted devices.
Trusted Endpoints is part of the Duo Essentials, Duo Advantage, and Duo Premier plans.
Requirements
Ensure you have the following access and privileges:
- Access to the Duo Admin Panel as an administrator with the Owner, Administrator, or Application Manager administrative roles.
- Access to your Active Directory domain as an administrator who can read information about the domain (Domain Admin or delegated permissions).
- Access to a Windows system with the ActiveDirectory PowerShell module (installed with the "Active Directory Domain Services" server role on a domain controller or with the Remote Server Administration Tools (RSAT) package).
Active Directory with Duo Desktop
This integration relies on having Duo Desktop present on your Active Directory (AD) domain-joined Windows endpoints. When users authenticate to applications protected with Duo's browser-based prompt, Duo matches the domain information reported by Duo Desktop with the management integration configuration.
Prerequisites
-
The Windows client systems must be directly joined to the Active Directory domain that you specify (via SID) during Active Directory with Duo Desktop configuration for trusted status confirmation.
-
The logged-in Windows user must be a domain account from the Active Directory domain that you specify (via SID), or trust verification during Duo authentication will fail.
-
Deploy Duo Desktop to your Windows endpoints. Refer to the Duo Desktop documentation to learn about different options for deploying the application.
Note that you do not need to configure a Duo Desktop policy in order to use Active Directory Domain Services with Duo Desktop for endpoint verification.
Create the Active Directory with Duo Desktop Integration
- Log in to the Duo Admin Panel and navigate to Devices → Trusted Endpoints.
- If this is your first management integration, click the Get started button at the bottom of the Trusted Endpoints introduction page. If you're adding another management integration, click the Add Integration button you see at the top of the page instead.
- On the "Add Trusted Endpoint Integrations" page, locate Active Directory Domain Services in the list of integrations.
- Choose Windows from the "Select operating system" drop-down, and then click the Add button.
The new Active Directory with Duo Desktop integration is created in the "Disabled" state. You'll turn it on when you're ready to apply your Duo trusted endpoints policy.
Please note that this integration requires Duo Desktop to be installed on the device to be considered trusted.
Keep the Admin Panel open in your browser to complete the next steps of obtaining your domain information and providing it to the Duo management integration.
Configure Active Directory with Duo Desktop
-
Log in to a domain controller or other Windows system with the RSAT package installed.
-
Launch PowerShell and paste in this cmdlet string:
(Get-ADDomain | Format-Table -Property DomainSID -HideTableHeaders | Out-String).Trim() | clipThis obtains the security identifier (SID) value for your AD domain and copies it to your clipboard automatically. You shouldn't see any output in the PowerShell window.
If you receive an error message stating "The term 'Get-ADDomain' is not recognized as the name of a cmdlet, function, script file, or operable program" then the ActiveDirectory PowerShell module may not be installed on the system where you ran the command. Install RSAT or locate a different system that has the module installed.
-
Return to the Active Directory with Duo Desktop management integration in the Admin Panel and paste in the copied domain SID in the field provided. It will look similar in format to
S-1-5-21-1004336348-1177238915-682003330. -
Click Save.
At this point the configured integration is disabled and applies to no users until you finish your deployment
Support for Multiple Domains
If you have endpoints in multiple domains with which you'd like to perform management verification with Duo Desktop, create a new Active Directory with Duo Desktop management integration for each domain, and configure each management integration with the unique SID for each domain. This also applies to child domains in a forest or external trusted domains.
Finish Trusted Endpoints Deployment
Once your managed computers have Duo Desktop installed, you can update the Trusted Endpoints policy to start checking for management status as users authenticate to Duo-protected services and applications.
When your trusted endpoints policy is applied to your Duo applications, return to the Active Directory with Duo Desktop management integration in the Admin Panel. The "Change Integration Status" section of the page shows the current integration status (disabled by default after creation). You can choose to either activate this management integration only for members of a specified test group, or activate for all users.
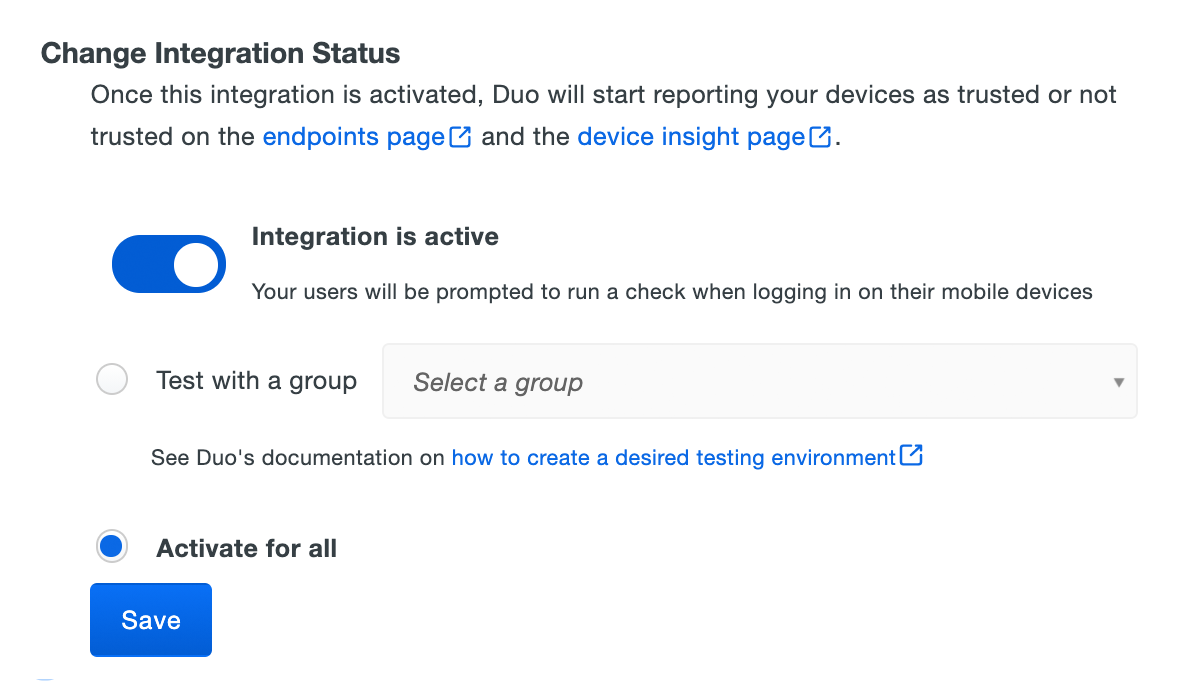
Duo Premier and Duo Advantage customers: The Device Insight and Endpoints pages in the Duo Admin Panel show trusted and untrusted access device status.
As more of your devices have Duo Desktop installed you can change the integration activation to apply to all users (if you just targeted test groups before), adjust your trusted endpoints policy to expand the target group, apply it to additional protected services, or start blocking access to applications from devices that do not pass the managed endpoint check. See the Trusted Endpoints documentation for more information.
Removing the Active Directory Management Integration
Deleting a trusted endpoints Active Directory management tool integration from the Duo Admin Panel immediately prevents identification of domain-joined devices from that configured domain using Duo Desktop. Be sure to unassign your trusted endpoints policy from all applications or remove the "Trusted Endpoints" configuration item from your global policy before deleting an existing Active Directory with Duo Desktop integration from "Trusted Endpoints Configuration". Leaving the policy settings in place after deleting a management tools integration may inadvertently block user access to applications.
Leaving the policy settings in place after deleting a management tools integration may inadvertently block user access to applications.
Troubleshooting
Need some help? Take a look at our Trusted Endpoints Knowledge Base articles or Community discussions. For further assistance, contact Support.
