Duo Trusted Endpoints - Manual Endpoint Trust Deployment with Duo Desktop
Last updated:
Overview
Duo's Trusted Endpoints feature secures your sensitive applications by ensuring that only known devices can access Duo protected services. When a user authenticates via the Duo Prompt, we'll check for the presence of Duo Desktop on that endpoint. You can monitor access to your applications from trusted and untrusted devices, and optionally block access from unmanaged, untrusted devices.
When a user authenticates via the Duo Prompt, we'll compare device identifiers collected by Duo Desktop installed on that endpoint with the identifiers of known Windows, macOS, and Linux devices stored in Duo. You can monitor access to your applications from trusted and untrusted devices, and optionally block access from devices not trusted by your organization.
Duo can verify your device’s trusted status with Duo Desktop without the need for a third party management system. Create a "Manual with Duo Desktop Trusted Endpoint" integration to add, manage and remove trusted endpoints. These device identifiers that you provide will be compared to the device identifier values collected by Duo Desktop to determine the endpoint’s trust status. You can add the device IDs manually or via CSV upload. The steps below walk you through how to do this.
Trusted Endpoints is part of the Duo Essentials, Duo Advantage, and Duo Premier plans.
Requirements
- Access to the Duo Admin Panel as an administrator with the Owner, Administrator, or Application Manager administrative roles.
Prerequisites
- Duo Desktop must be installed on Trusted Endpoints.
Collect Device Identifiers
Collect the required device identifiers for your endpoints. Depending on the approach you take to upload your device information to Duo, you may create a CSV file.
Windows
-
The unique device identifier is the Machine GUID. This value is present in the registry at:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography -
This value will look like
82be363f-5c10-j05h-p00l-d4d80d4156c7. -
One way to collect this value from your Windows endpoints is to run this PowerShell command at each workstation:
Get-ItemProperty -Path HKLM:\SOFTWARE\Microsoft\Cryptography -Name "MachineGuid"
macOS
-
The unique device identifier is the hardware UUID. This value looks like
D44E2E05-5C10-J05H-P00l-D4D46B79D663. -
One way to collect this value from your macOS endpoints is to run this command in the Terminal application at each workstation:
ioreg -d2 -c IOPlatformExpertDevice | awk -F\" '/IOPlatformUUID/{print $(NF-1)}'
Linux
-
The unique device identifier is the product/system UUID. This value looks like
3669cf64-3561-11ee-be56-0242ac120002. -
One way to collect this value from your Linux endpoints is to run this command from the terminal at each workstation:
sudo dmidecode --string system-uuid
Create the Manual with Duo Desktop Integration
- Log in to the Duo Admin Panel and navigate to Devices → Trusted Endpoints.
- If this is your first management integration, click the Get started button at the bottom of the Trusted Endpoints introduction page. If you're adding another management integration, click the Add Integration button you see at the top of the page instead.
- On the "Add Trusted Endpoint Integrations" page, locate Manual Enrollment in the list of integrations.
- Choose your operating system from the "Select operating system" drop-down, and then click the Add button.
The new Manual with Duo Desktop integration is created in the "Disabled" state. You'll turn it on when you're ready to apply your Duo trusted endpoints policy.
Please note that this integration requires Duo Desktop to be installed on the device to be considered trusted.
Add Trusted Device IDs Manually
The first step to trusting your users' devices is to add those device identifiers to your Manual Enrollment trusted device inventory. You can do this by manually adding individual device identifiers in the Duo Admin Panel.
-
Navigate to the Manual Enrollment integration you created.
-
Check to see that the "Enter Device IDs" option is selected.
-
Add up to 25 device identifiers. See how to collect device identifiers.
-
Add a trust expiry date for each device identifier. The default date is one year from the current date. Newly added rows will inherit the trust expiry date of the row above it.
-
Add an optional description per device identifier. A description is recommended to assist in keeping track of the device identifiers through search functionality.
-
Click Add device to inventory.
-
Repeat steps 3-5 as necessary until your inventory contains your trusted endpoints. You do not have to add all of your trusted endpoints at once, you can add to and remove from your inventory as needed. Your trusted endpoints will remain in your inventory until you delete them.
Add Trusted Device IDs via CSV Upload
You can also add devices to your Manual Enrollment trusted device inventory by uploading a CSV file containing those device identifiers. This is a good way to add many devices at once. You can switch between manually adding devices to the inventory and CSV uploads at will. Both methods will build upon the same trusted endpoint inventory for a given trusted endpoints integration.
Create a CSV File
Create a CSV file with the Windows, macOS, or Linux device identifiers you collected from your endpoints.
The CSV file should contain the following fields:
- device_id (required): device identifier
- trust_expiry_date (required): date the device should no longer be trusted in the format YYYY-MM-DD
- description (optional): description of your choosing up to 255 characters
A properly-formatted device identifiers CSV file will look like this for Windows MachineGUIDs:
device_id,trust_expiry_date,description
6984852C-7921-4D8A-AE8C-1B605AD58903,2024-12-31,device1
7450C1F3-C8FB-4EF0-B445-6FBB5217A399,2024-12-31,device2
8FBCEB28-ED33-48C7-9E2D-62ABC5F13794,2024-12-31,device3
9BC0D145-904C-498D-8654-8A7617954E8A,2024-12-31,device4
A9462540-756E-450A-A39A-F38E967EB575,2024-12-31,device5
C45689E3-4DD4-404A-B584-55572A1B2EFB,2024-12-31,device6
07280453-53D8-4F8C-A63F-DA3EE93479AE,2024-12-31,device7
E0FEFB56-0FE4-4938-B294-5414C0E111D5,2024-12-31,device8
Upload CSV File
-
Navigate to the Manual Enrollment integration you created.
-
Check to see that the "Import Device IDs" option is selected.
-
Click Choose File to select your created CSV file.
-
Click Upload devices to add devices in your CSV file to your inventory.
Finish Trusted Endpoints Deployment
Once your managed computers have Duo Desktop installed, you can update the Trusted Endpoints policy to start checking for management status as users authenticate to Duo-protected services and applications.
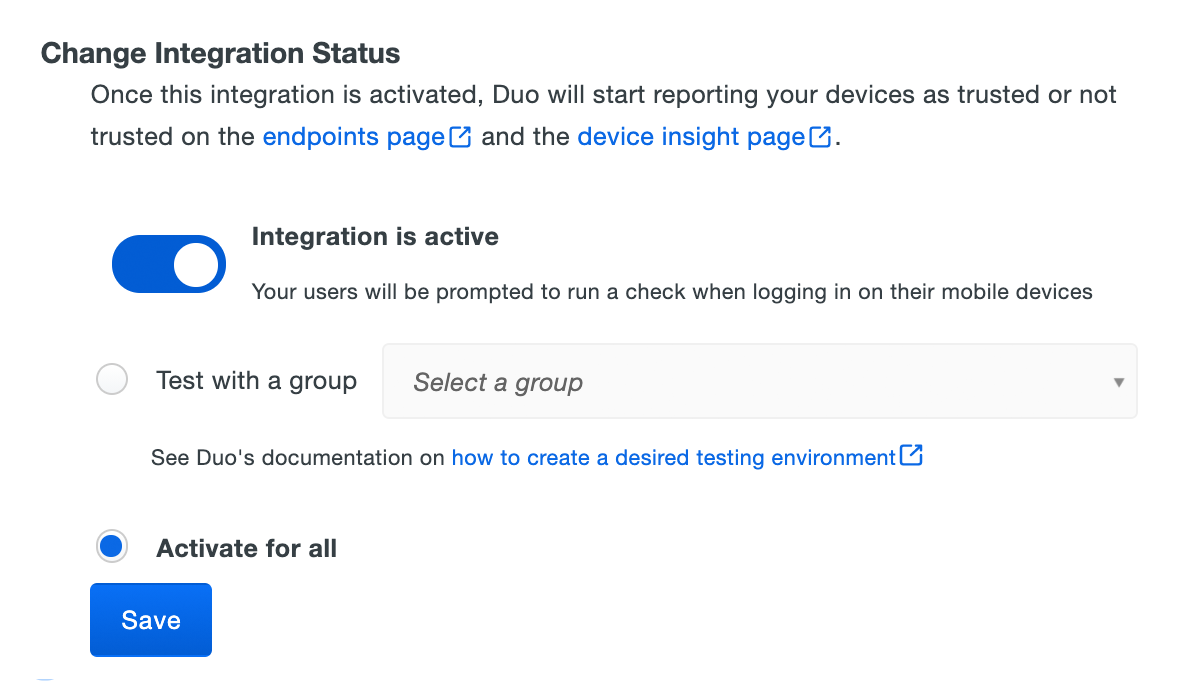
When your trusted endpoints policy is applied to your Duo applications, return to the manual enrollment integration in the Admin Panel. The "Change Integration Status" section of the page shows the current integration status (disabled by default after creation). You can choose to either activate this management integration only for members of a specified test group, or activate for all users. If you created more than one manual enrollment integration, you must activate each one individually. You will still be able to edit your inventory when the integration is activated.
The Device Insight and Endpoints pages in the Duo Admin Panel show trusted and untrusted access device status.
Verify Your Setup
When users access Duo-protected resources, Duo Desktop provides device information to Duo. If the information from the device matches the information stored in Duo, Duo grants access to the trusted device.
Manage Your Trusted Device Inventory
From the Manual Enrollment integration page, you can click the View managed devices button to see a table view of your trusted device inventory. Here, you can search, view statuses, edit properties, and remove devices from your inventory.
Search for a Trusted Device
A trusted device in inventory can be found by searching for any part of the device identifier or its description. Use the search function of the trusted device table on the Manual Enrollment integration page.
View a Trusted Device’s Status
When adding trusted devices to your inventory, a trust expiry date is also required in addition to the device identifier. This trust expiry date determines when a device is no longer considered trusted. A trusted device will become expired at 00:00:00 UTC on the chosen expiry date. Expired devices are not removed from the inventory but will not be trusted in the same way as if they were not in the inventory. They are also shown with an "Expired" label in the table to indicate that they have expired.
Edit a Trusted Device
Edit the properties of one or more trusted devices by selecting the checkbox next to the device in the trusted devices table on the Manual Enrollment integration page. Select either the "Edit descriptions" or "Change trust expiry dates" option in the drop-down menu. Enter your new description or date and click the "Save" button. This change will apply to all devices that you selected.
Remove a Trusted Device
Remove one or many trusted devices by selecting the checkbox next to the device in the trusted devices table on the Manual Enrollment integration page. Then select the "Delete device IDs" option in the drop-down menu. Finally, click the "Delete Devices" button to confirm.
Remove all Trusted Devices
If you have a need to remove all trusted devices from your inventory, at this time the recommended approach is to remove the Manual Enrollment integration and create a new one.
Removing the Manual Enrollment Integration
Deleting a trusted endpoints management tool integration from the Duo Admin Panel can prevent user authentication. Be sure to unassign your trusted endpoints policy from all applications or remove the "Trusted Endpoints" configuration item from your global policy before deleting an existing Manual with Duo Desktop integration from "Trusted Endpoints Configuration".
Leaving the policy settings in place after deleting a management tools integration may inadvertently block user access to applications.
Troubleshooting
Need some help? Take a look at our Trusted Endpoints Knowledge Base articles or Community discussions. For further assistance, contact Support.
