Duo Administration - Policy & Control
Last updated:
Overview
Duo Premier, Duo Advantage, and Duo Essentials plans customers gain granular control with the Policy & Control feature.
Manage your Duo Policies centrally and apply them...
- globally, shared between user groups, or shared between applications, so you don’t have to specify the same setting in multiple places.
- to specific user groups accessing an application. This lets you set different rules depending on who is authenticating and their context.
Duo Free plan customers have limited access to Duo policies. Free plans may only control the New User Policy via a global or shared application policy. Configure all other available application settings at the individual application.
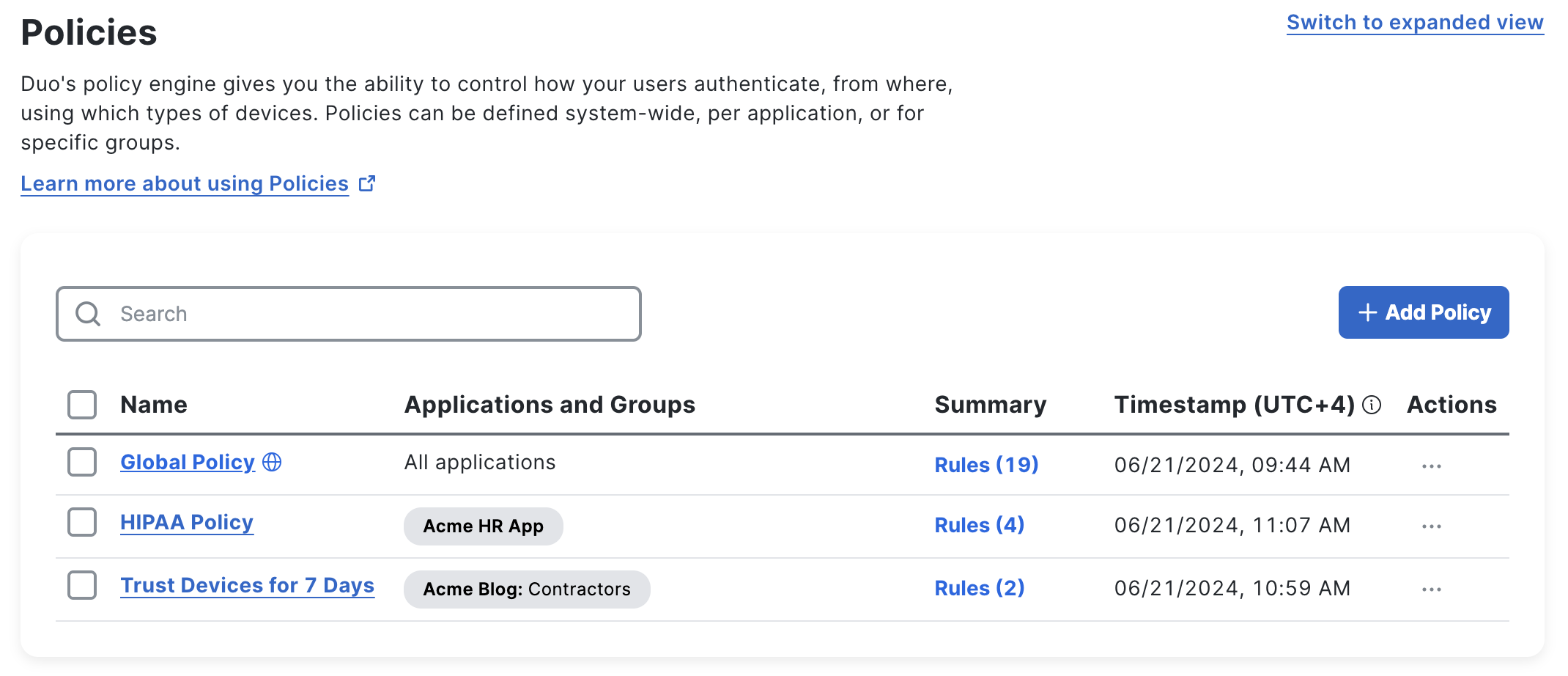
Create and manage your policies from the Policies page in the Duo Admin Panel.
Only admins with the Owner or Administrator roles can create or edit policies. Admins with the Application Manager role may assign existing policies to applications, but may not edit or create policies.
When creating policies that restrict access for users, keep in mind that users with bypass status are not subject to these restrictions, as they bypass Duo authentication entirely.
Compact View
While in the compact view, which is the default view, you can alphabetically sort your policies by clicking the "Name" column heading. The compact view shows the first few applications and groups assigned to each policy, as well as the last-modified time and date if edited since October 2023.
Click Rules in any row to view details about that policy, like creation and modification timestamps (since October 2023), configured and unconfigured policy rules groupings, and the full list of group or application assignments. Click a policy's name to open the policy editor.
Click on Actions to Duplicate, Apply, or Unassign the policy to groups and applications.
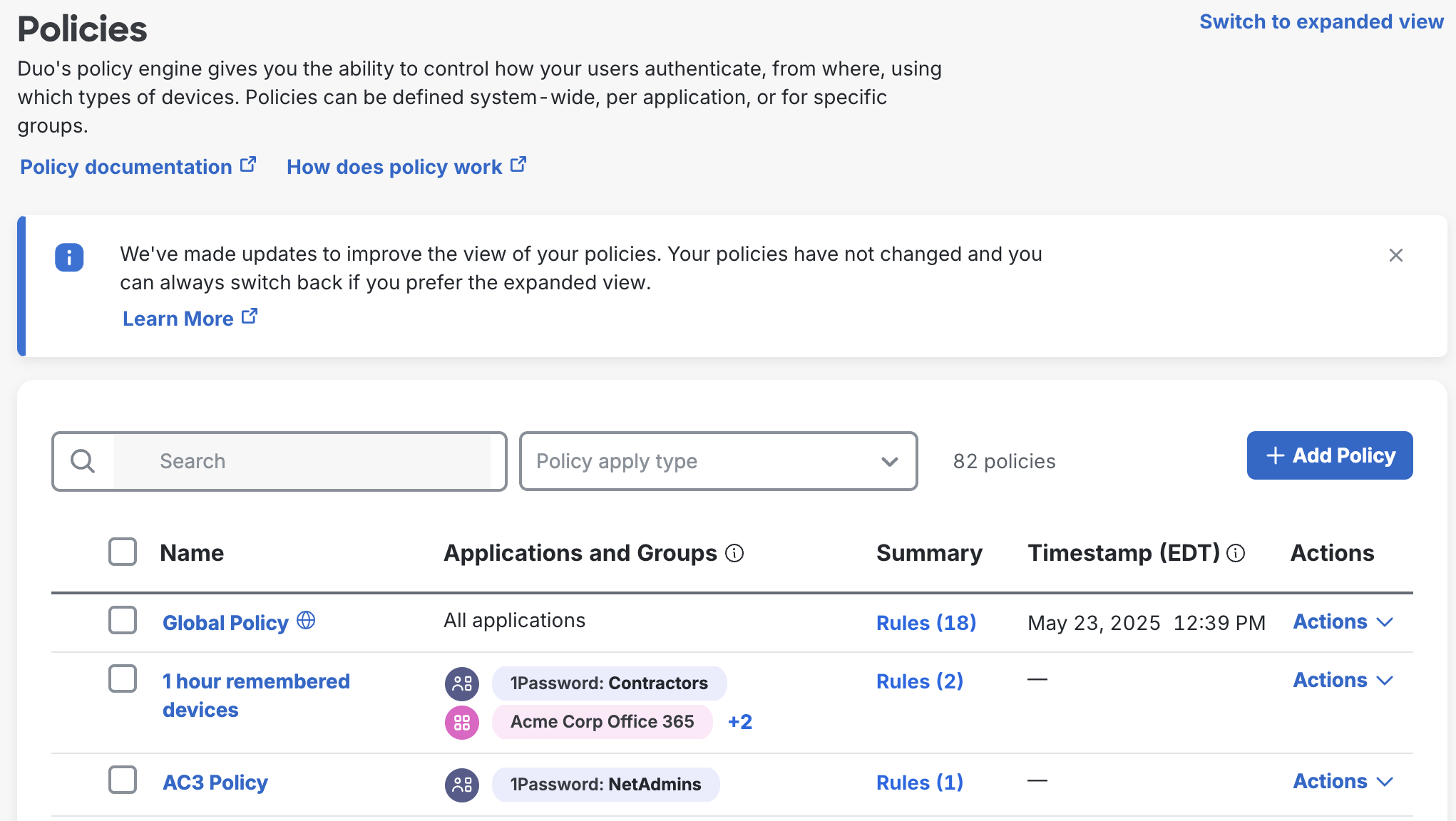
Click Switch to expanded view to see the expanded policies view.
New Policy Editor
We've made changes to the policy editor to give you an improved experience. If you're not ready to start using the new policy editor yet, click Switch to legacy editor in the upper-right to go back to the previous experience.
Policy Editor Improvements
- A cleaner user interface. Instead of opening a floating editor over the current page, the new policy editor opens in a full page.
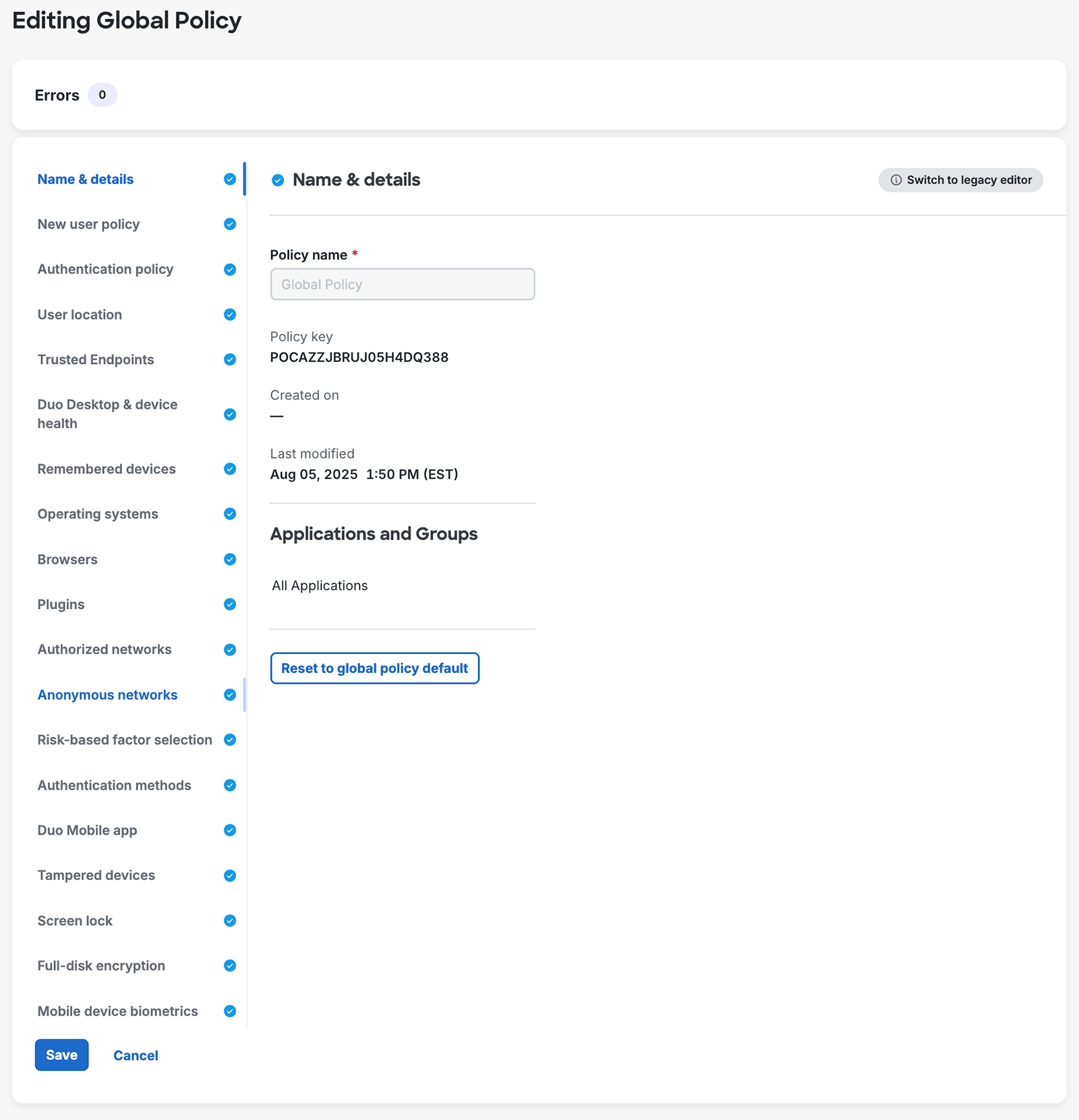
- A new "Name & details" navigation item added for you to enter a new custom policy's name, above the configurable policy sections.
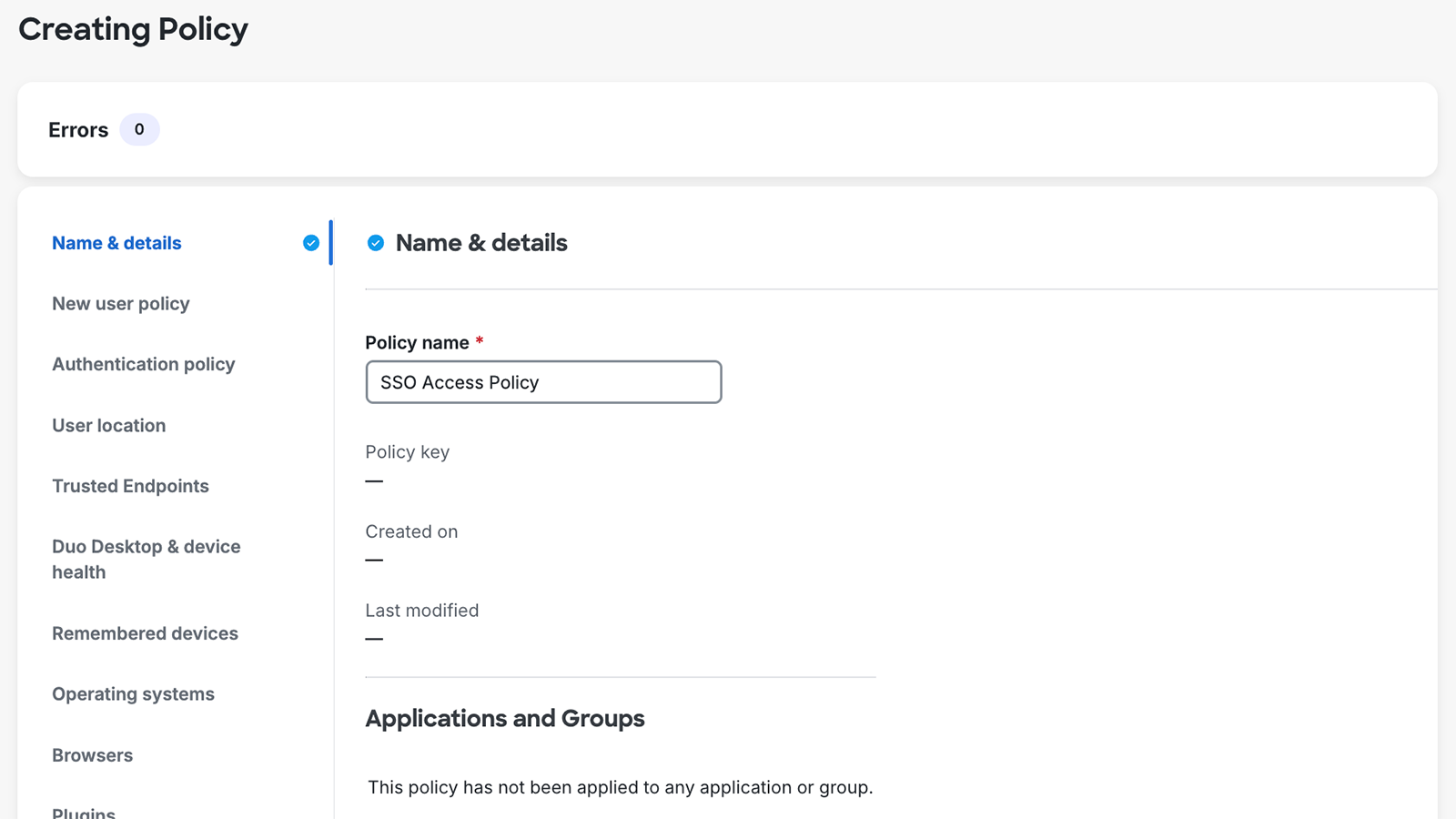
- When editing existing policies, the "Name & details" information shows the policy's key, creation date (if created after October 2023), modified date, and any application and group assignments.
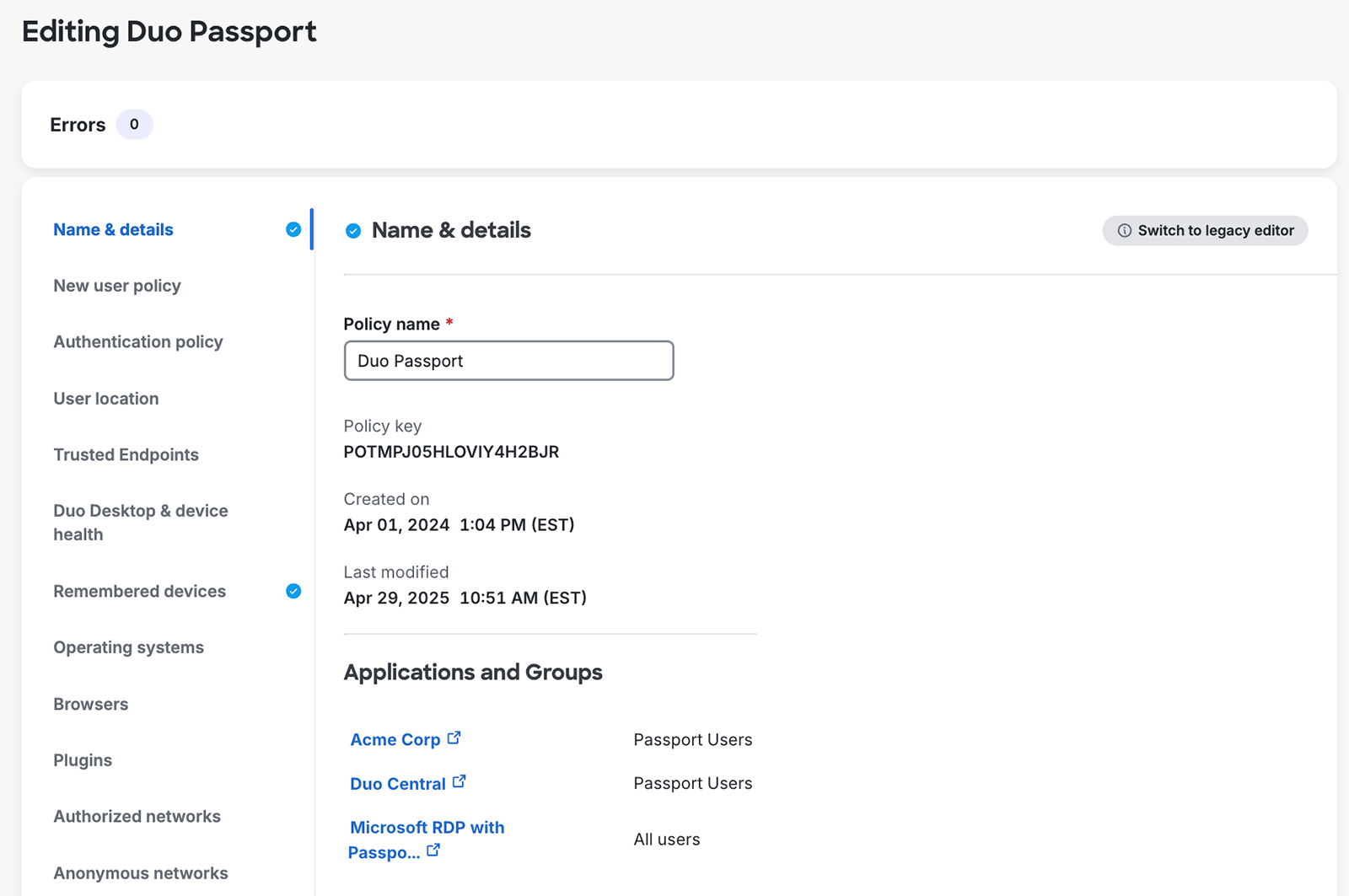
- You can now view the different policy sections and options without adding them to the policy. In the new editor you will use the Add toggle to add that policy setting to your new policy.
- Improved language for policy option names and descriptions, increasing clarity and consistency across all policy settings. We have reordered some policy options to present the most strict, secure, or recommended option first.
- A new section titled "What does this protect against?" underneath the policy options explains how the policy settings enhance the security of your Duo configuration.
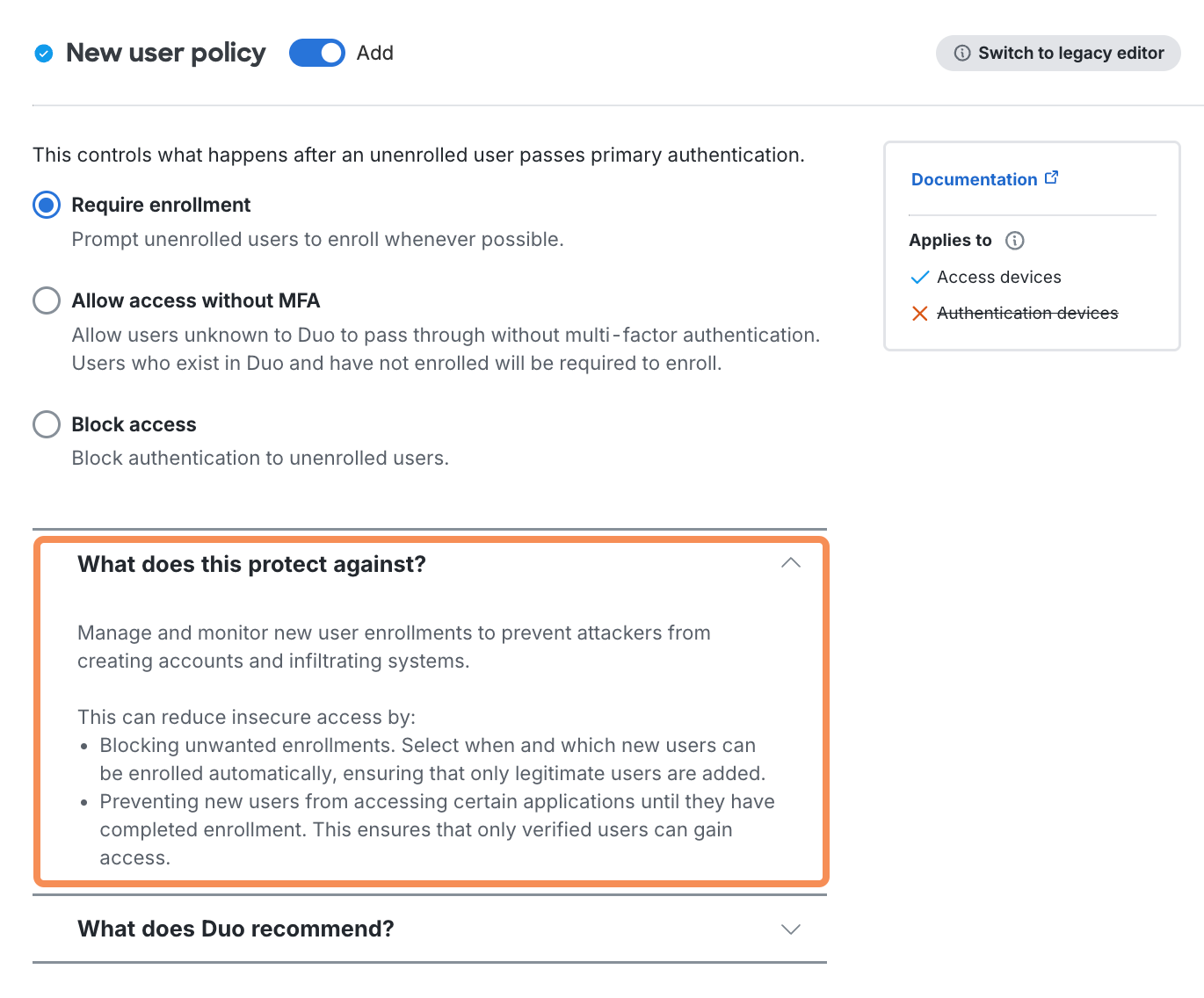
- Another new section titled "What does Duo recommend?" suggests optimal policy selections for different Duo use cases.
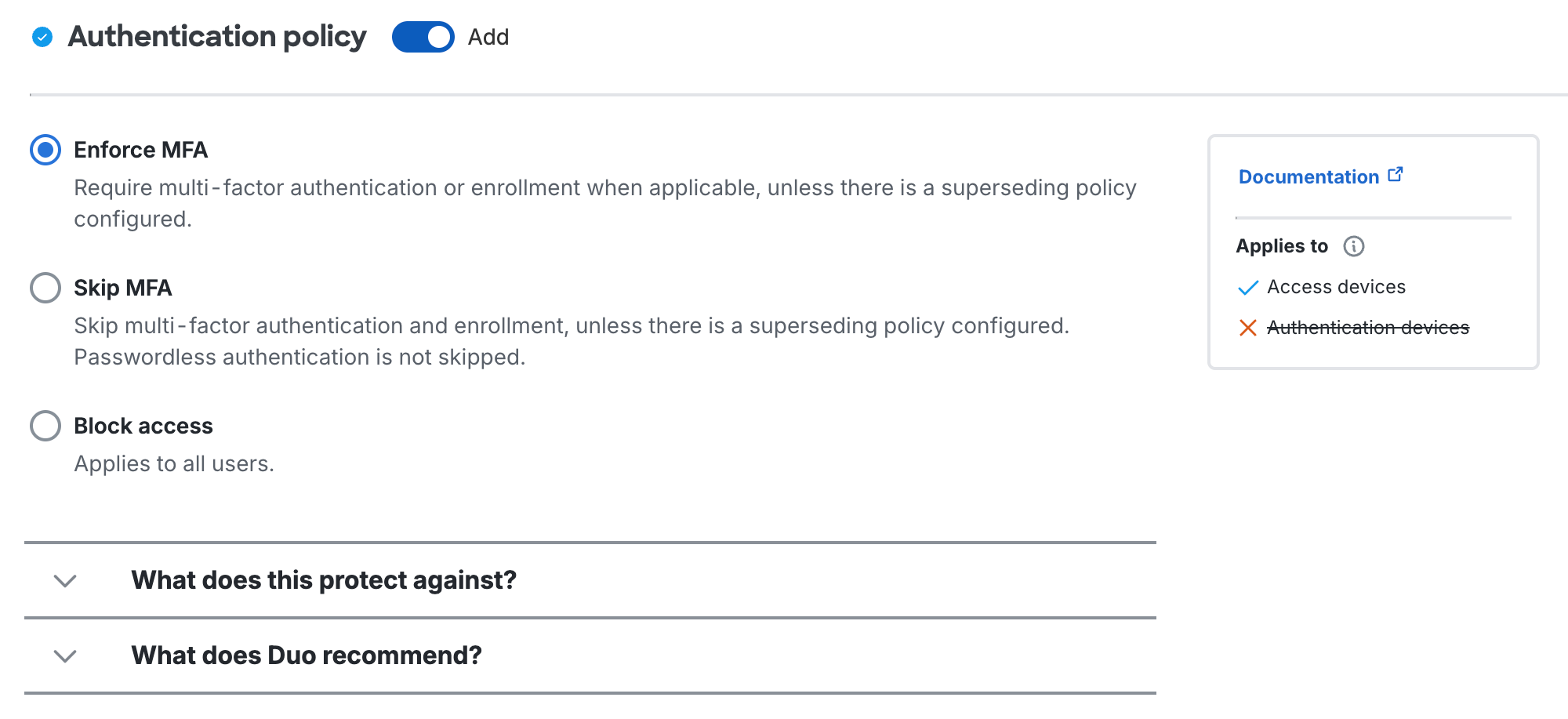
- A new legend to the right of each policy section so you can access related documentation, understand the effects of that policy on different device types, and review any dependencies and warnings related to the policy section.
Policy Editor Feedback
Let us know what you think of the new policy editor! Use the "How was your experience creating a policy?" feedback tool underneath the editor to share what you liked or disliked about the new experience.
Global Policy
The built-in Global Policy cannot be deleted. It always applies to all users and applications, so you should edit this policy if there are settings you'd like to control for your entire Duo account. You can view your current Global Policy settings by editing the Global Policy on the Polices page. Settings at the Duo defaults are greyed out.
Your Duo subscription level determines which policy options show up in the editor. For example, Duo Essentials receives a subset of the policy settings available to Duo Advantage and Duo Premier customers.
Note: If you downgrade your Duo subscription, your policy options may not be saved and may revert to the default settings. If your Duo trial is ending or you plan to downgrade your Duo subscription, make sure to note your policy settings beforehand.
As you review the various policy settings in this document, note the Duo plans listed in the Available in information to determine if a setting applies to your subscription or not.
Editing the Global Policy
Role required: Owner or Administrator
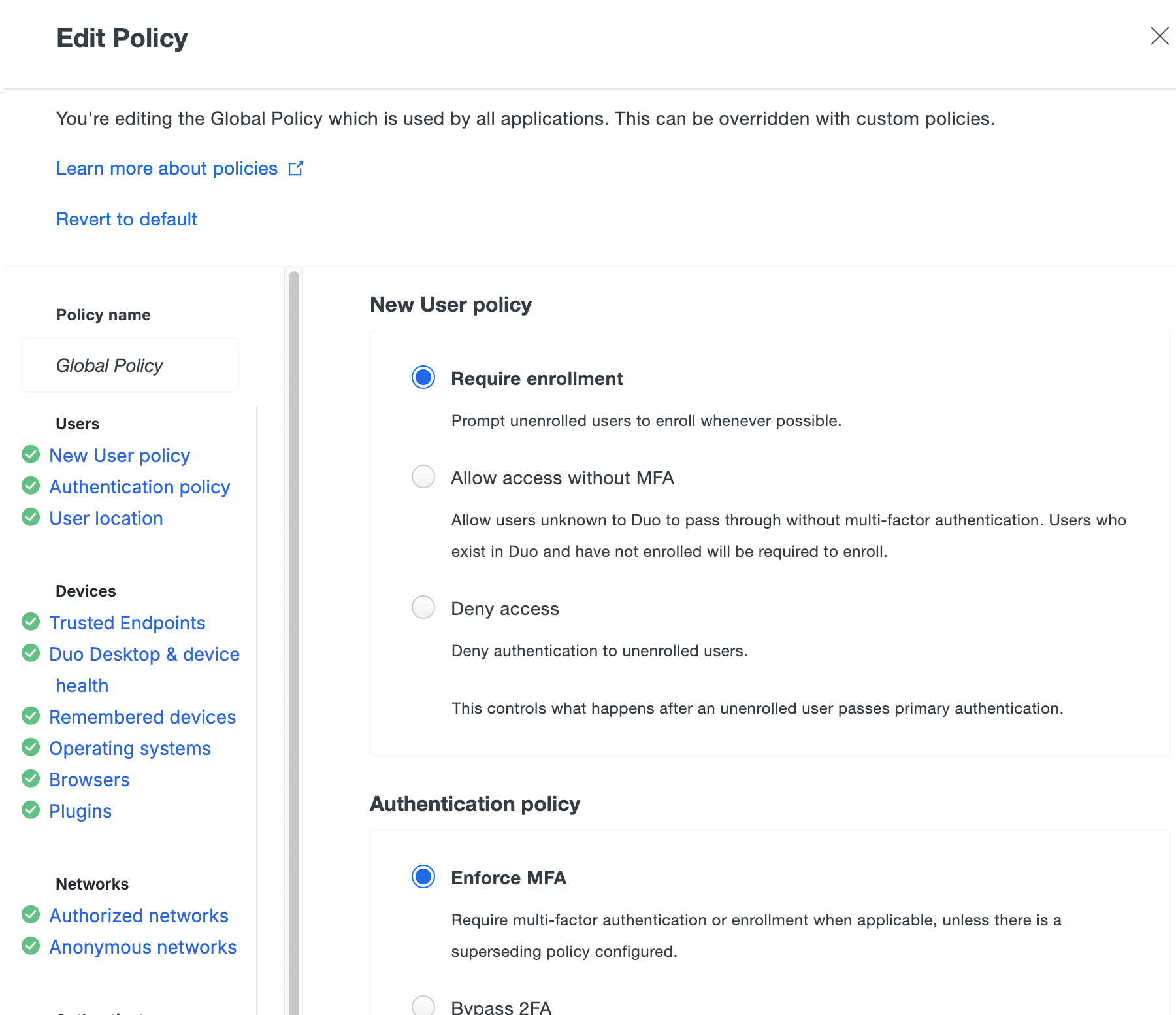
To edit the Global Policy from the "Policies" page:
-
Click Global Policy under "Name" to open the Global Policy editor.
-
Once in the Global Policy editor, click the policy settings listed on the left side of the editor that you want to modify, then update the setting configuration on the right side of the editor.
-
Click Save Policy when your edits to the Global Policy are complete.
-
If you'd like to restore the original Global Policy settings, open the Global Policy editor again and click the Revert to default link at the top of the "Edit Policy" window. Click Save Policy to apply the Global Policy defaults.
Changes to existing policy settings take immediate effect.
Custom Policies
If your organization requires policy and controls that differ from the Global Policy, you can create a Custom Policy and assign it to user groups, applications, or applications for specific groups. Custom Policies only need to specify the settings they wish to enforce.
Create custom policies for groups or applications from either the main "Policies" page or from the properties page of any application. Policies may be shared between multiple groups and applications.
When you view an application, the Global Policy settings are shown because these settings apply to all applications unless they are superseded by a custom application or group policy.
You can configure and assign an application-group policy to override settings assigned by an application policy, which in turn overrides settings assigned in a user-group policy. When user-group, application, or application-group policy settings supersede a Global Policy setting, those superseded settings appear crossed out in the Global Policy view shown when viewing an application or in the Policy Calculator.
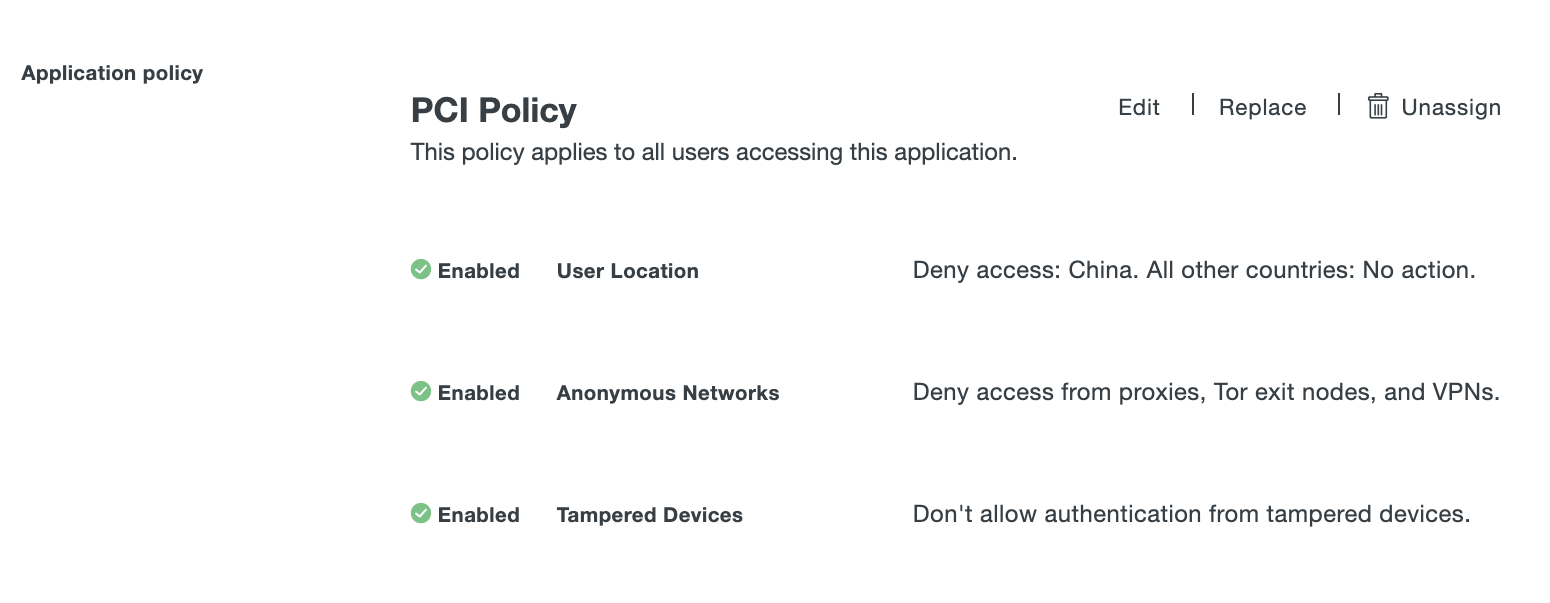
In the example below, the "HIPAA Policy" application policy settings (New User Policy, User Location, etc.) override those same settings in the Global Policy for that specific application.
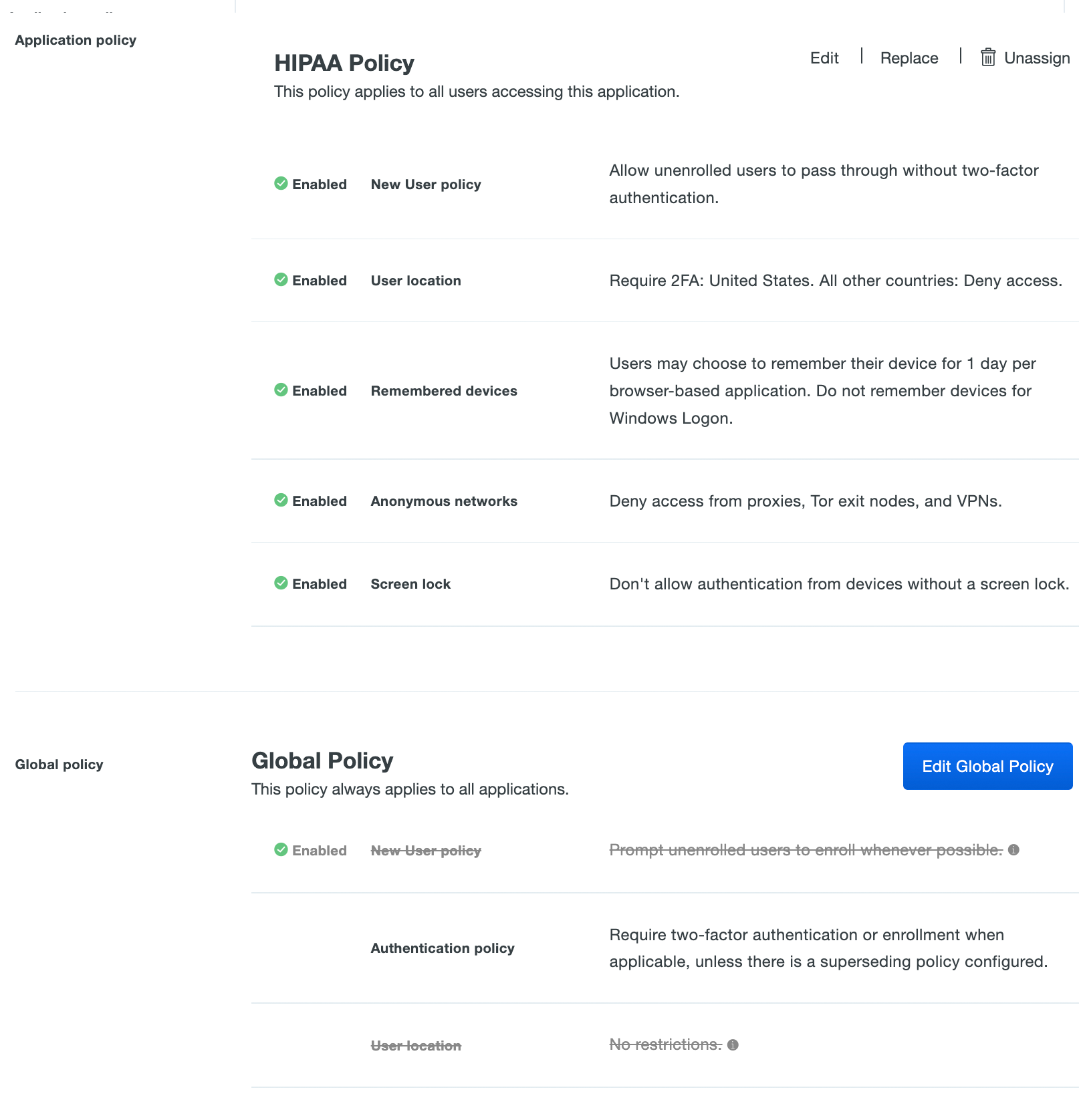
Create a Custom Policy
Role required: Owner or Administrator
To create a custom policy from the main "Policies" page:
-
Click + Add Policy.

The policy editor starts with an empty policy.
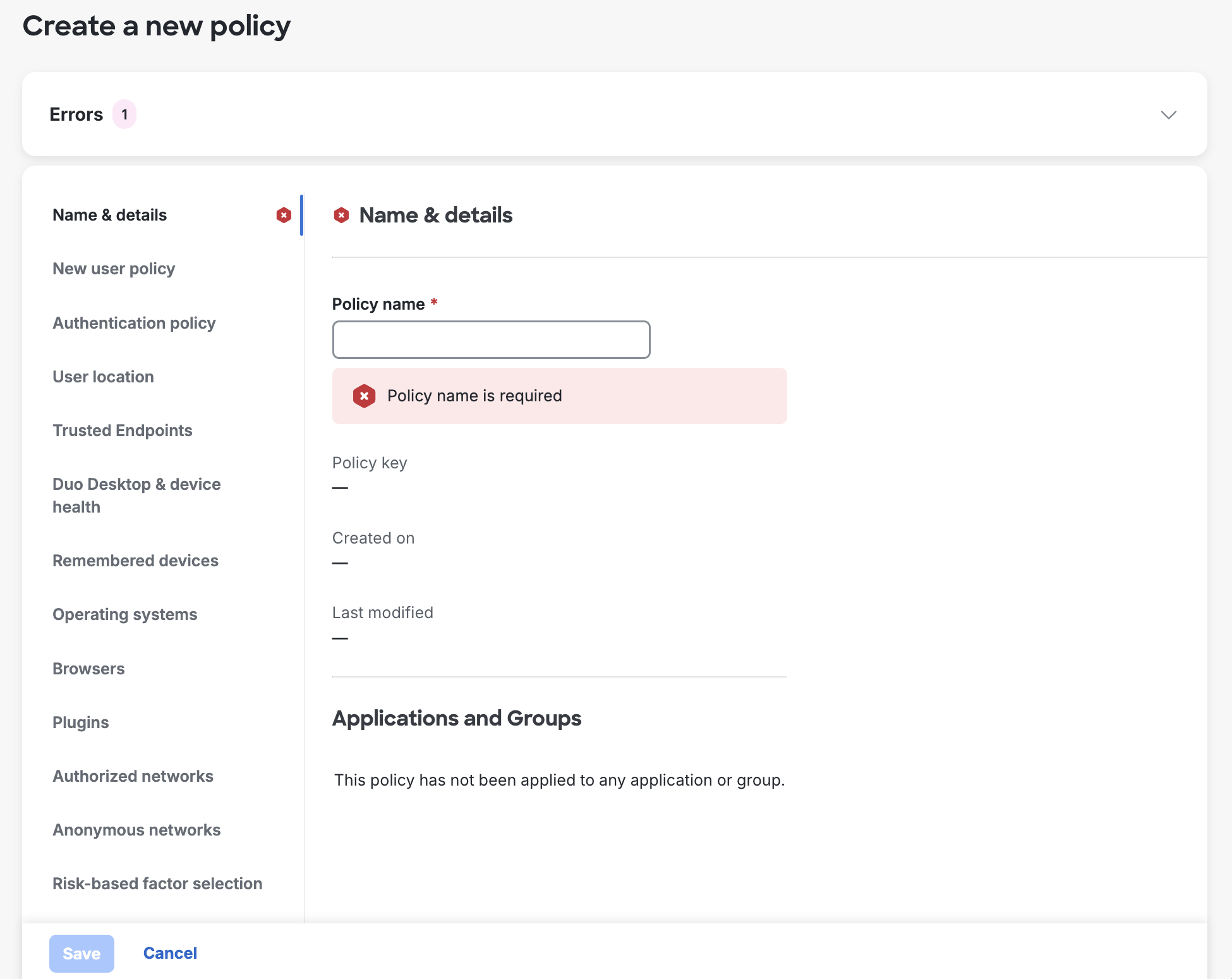
-
Enter a descriptive Policy Name on the "Name & details" page, and then click each policy section's name on the left and use the Add toggle to configure it in your new custom policy. For each policy section you add you can adjust the settings. Toggle Add back off to remove a setting from the new custom policy.
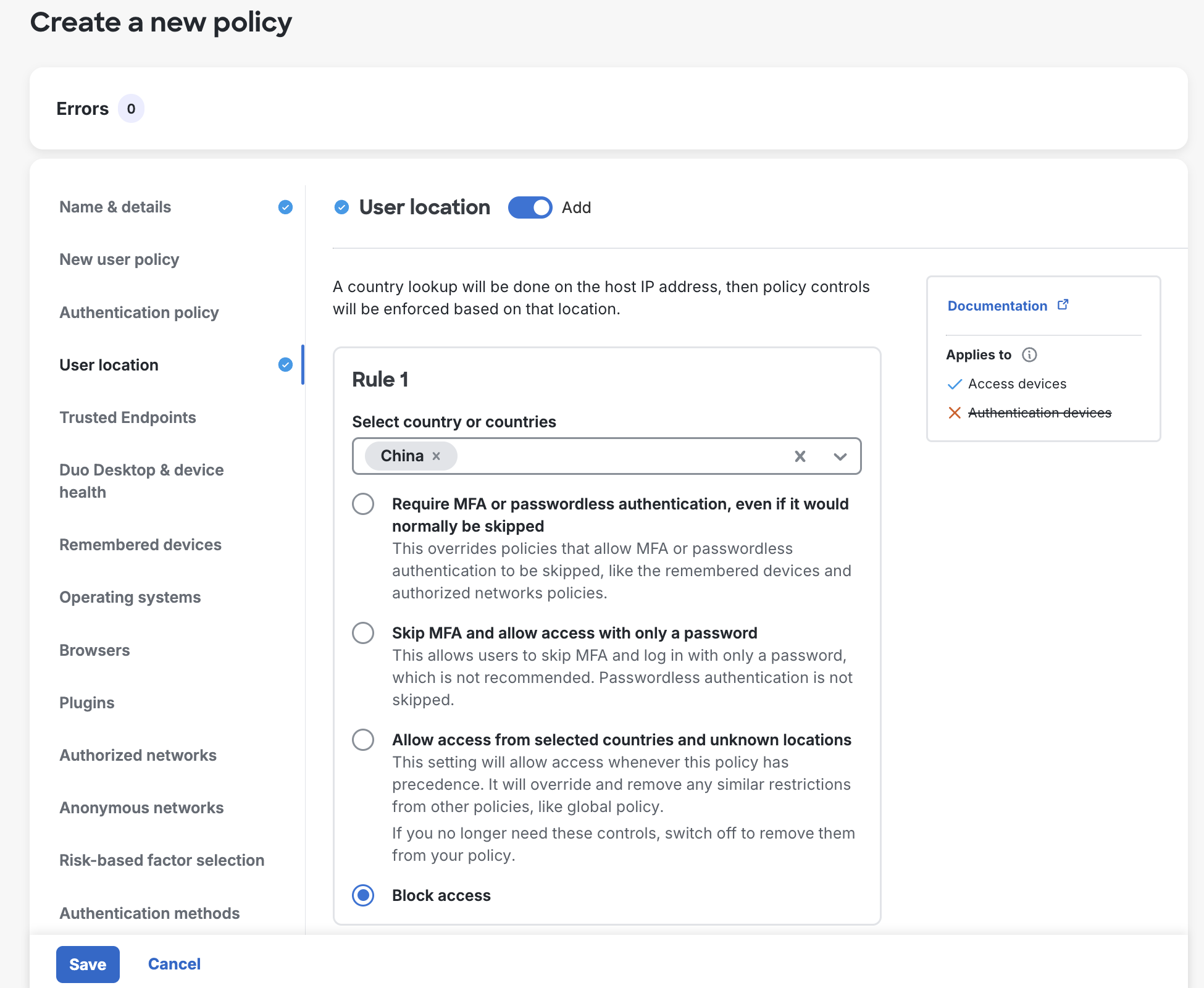
-
When you are done adding and configuring policy settings, click Save.
The "Policies" page lists the newly created policy. From the "Policies" page you can edit, delete, replace, or apply the custom policy by clicking the "Actions" drop-down.
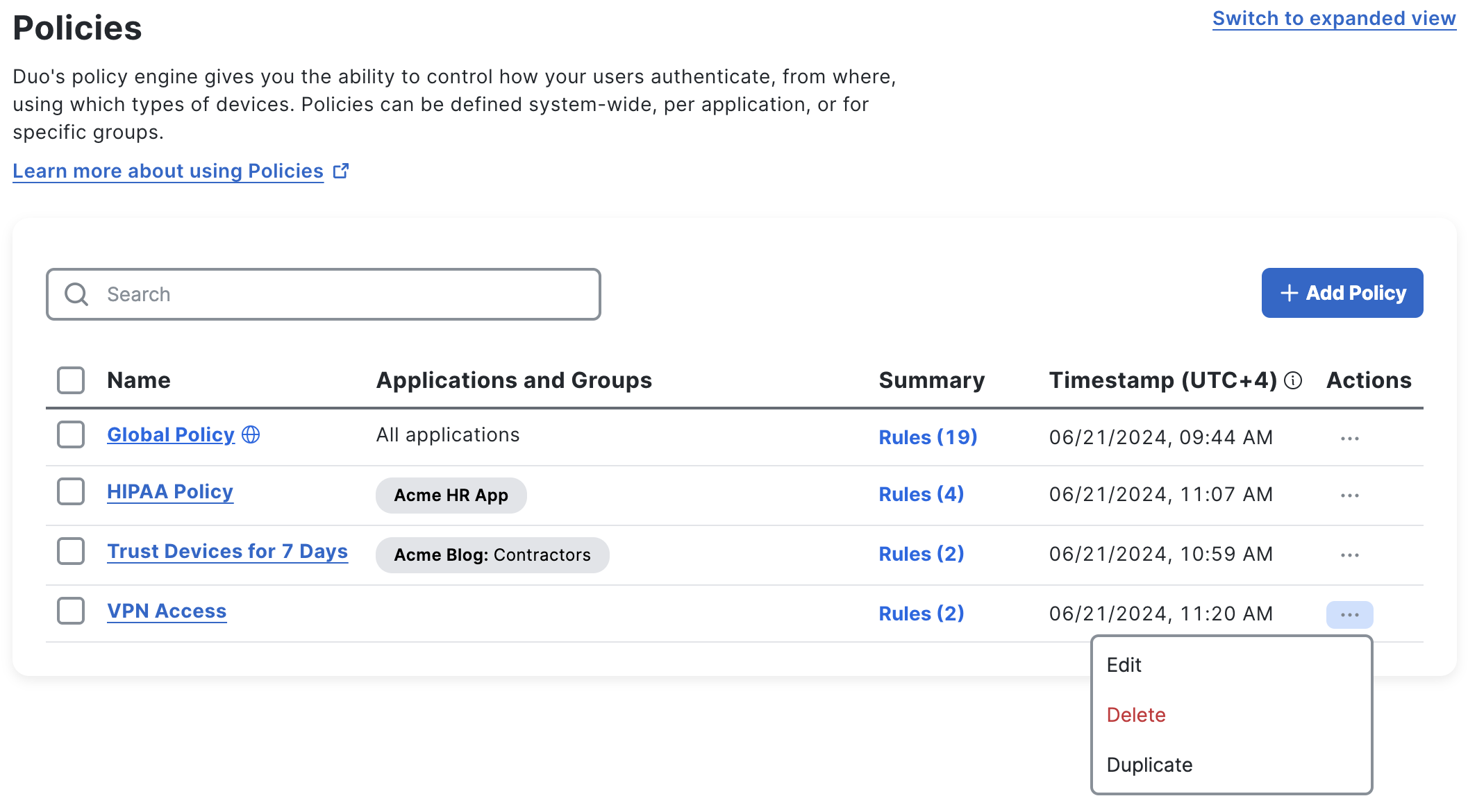
Apply a Custom Application Policy
Apply to a Single Application
Role required: Owner, Administrator, or Application Manager
You can assign a single application-level custom policy from an application's properties page. To do this:
-
Navigate to an application's properties page in the Duo Admin Panel and scroll down to "Application policy".
-
Click Apply a policy to all users to assign the policy to all users of that application.
-
Select the custom policy you want to apply to this application from the Policy drop-down list.
-
Click Apply Policy. The application page shows the new policy assignment.
Apply to Multiple Applications
Role required: Owner, Administrator, or Application Manager
To bulk assign an existing custom policy to one or more applications:
-
Navigate to the "Policies" page in the Duo Admin Panel.
-
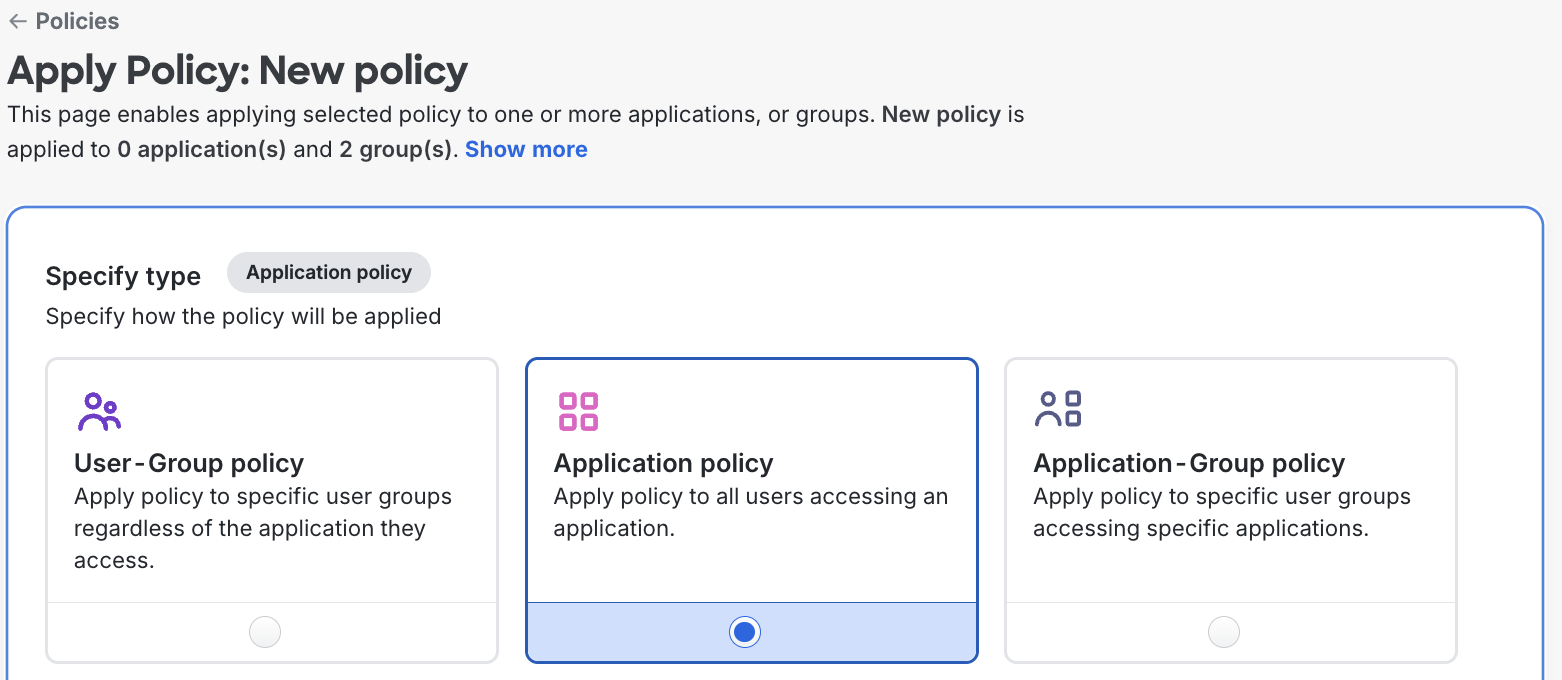
Click the Actions → Apply dropdown to navigate to the "Apply Policy" page.
-
Under Specify type, ensure Application policy is selected. Application policy ensures a policy will be applied to the application regardless of the user accessing it. This policy will only override the global and user-group policy.
-
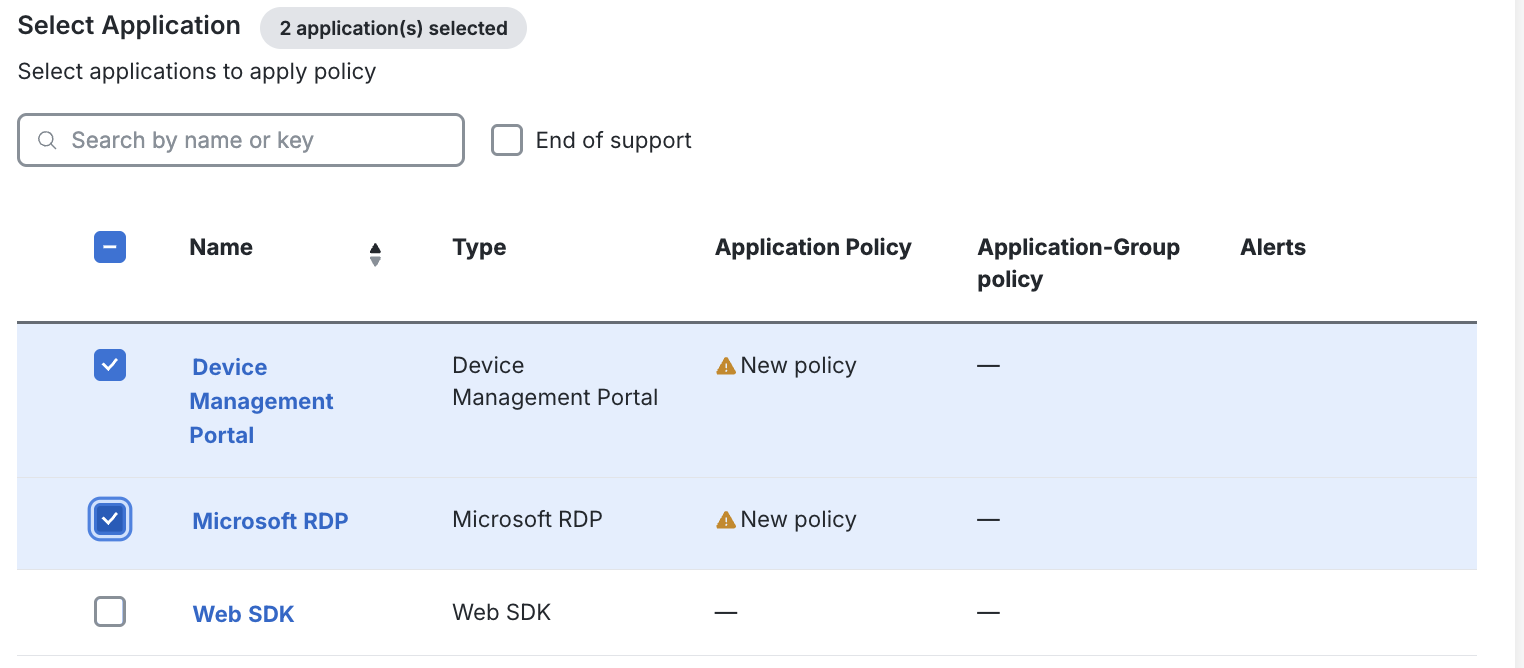
Under Select Application, select the application(s) you wish to apply the policy to.
-
Review the Summary to ensure you are applying the policy as intended.
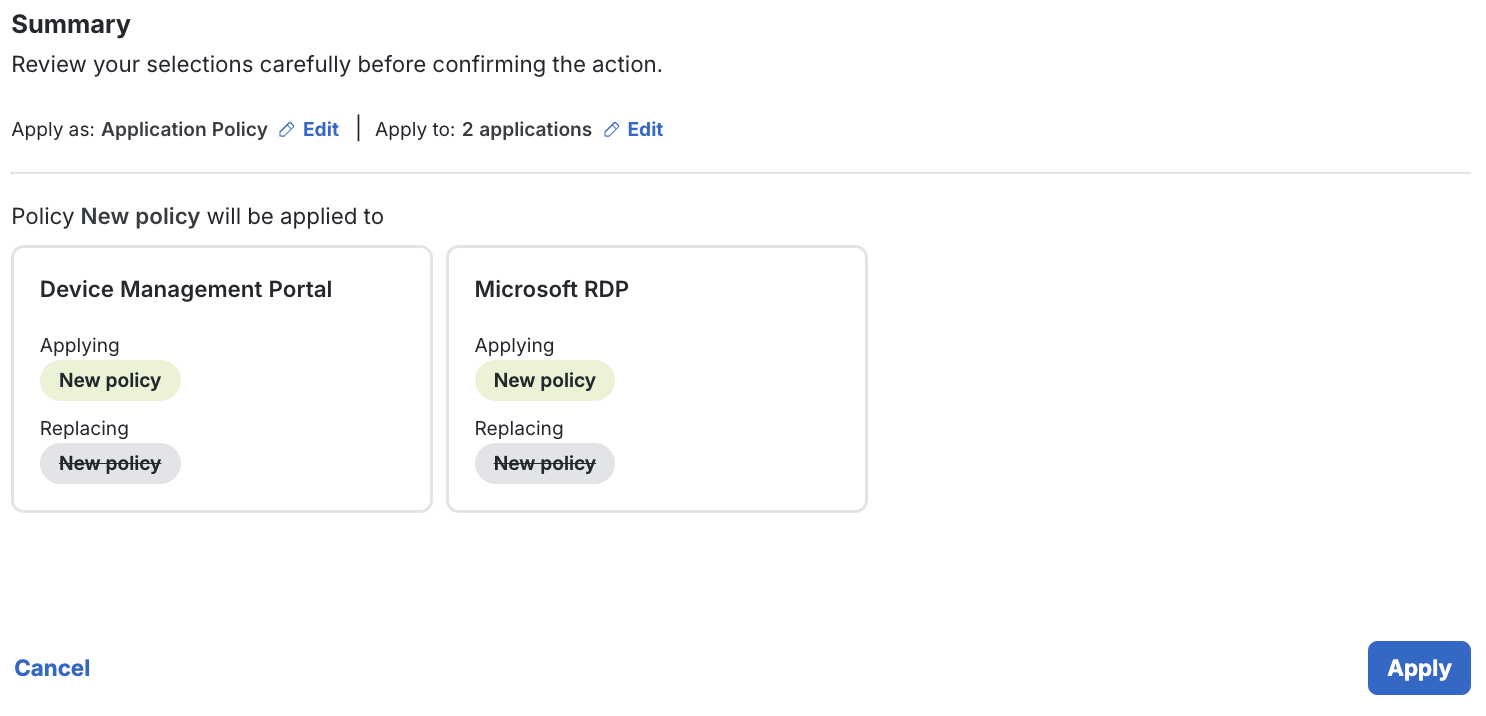
-
Click Apply in the lower-right section of the page when you are ready.
Apply a Custom Application-Group Policy
Role required: Owner, Administrator, or Application Manager
Apply to Groups for a Single Application
You can assign a custom policy to one or more Duo groups from an application's properties page. To do this:
-
Navigate to an application's properties page in the Duo Admin Panel and scroll down to "Application-Group policies".
-
Click Apply a policy to groups of users to assign the policy to only certain users of that application
-
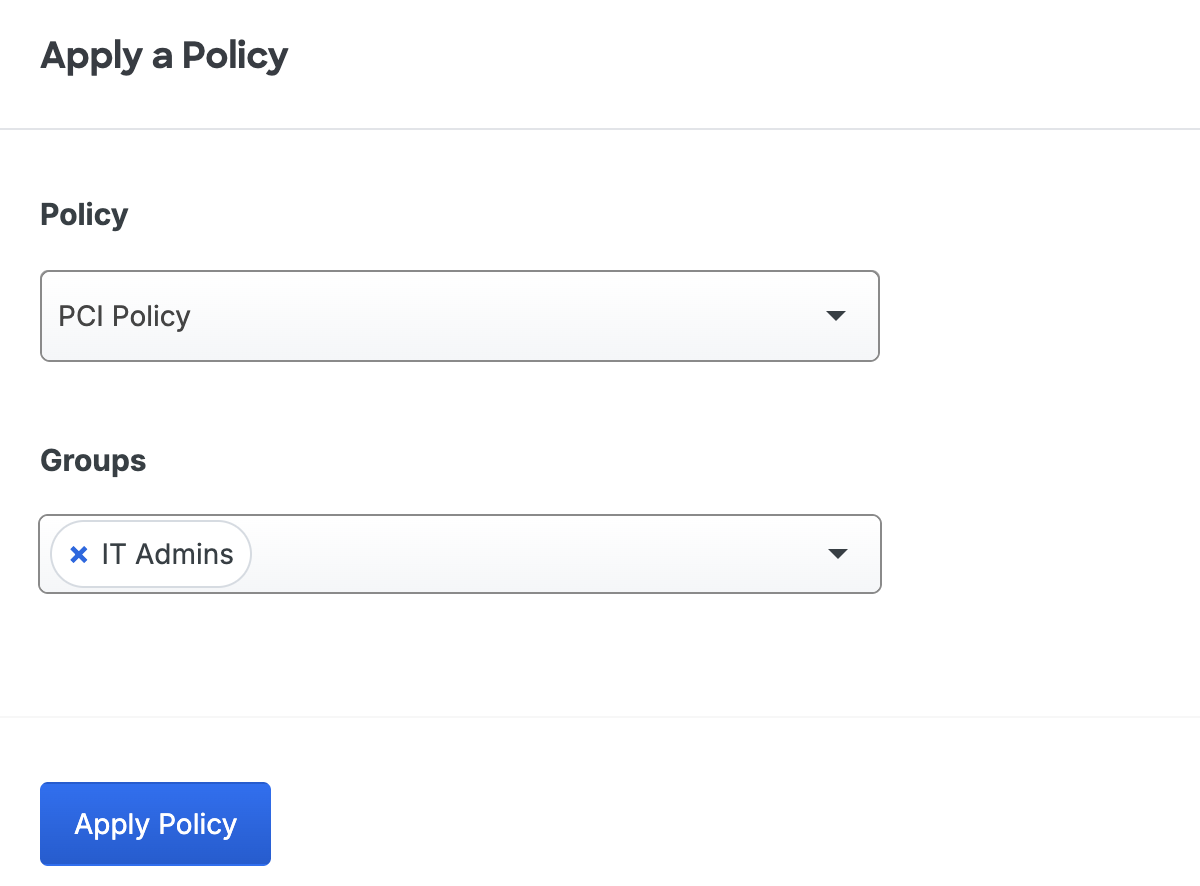
Select the custom policy you want to apply to this application from the Policy drop-down list.
-
Start typing in a group's name in the Groups field and select the policy target group(s) from the suggested names.
-
Click Apply Policy. The application page shows the new application-group policy assignment.
Apply to Groups for Multiple Applications
Role required: Owner, Administrator, or Application Manager
To bulk assign an existing custom policy to one or more groups for one or more applications:
-
Navigate to the "Policies" page in the Duo Admin Panel.
-
Click the Actions → Apply dropdown to navigate to the "Apply Policy" page.
-
Under Specify type, ensure Application policy is selected. Application-Group policy ensures a policy will be applied to the application only for specific groups. This policy will only override the global, user-group, and application policies.
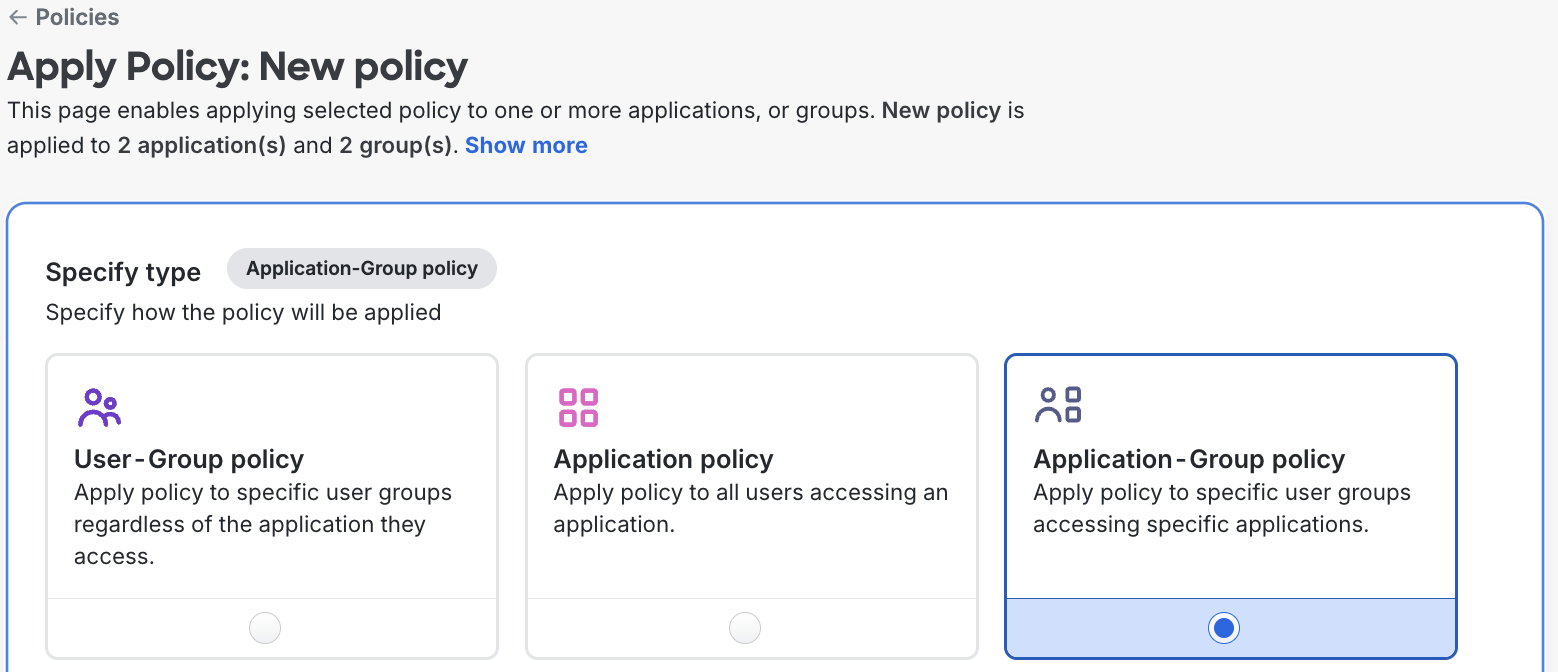
-
Under Select Application, select the application(s) you wish to apply the policy to.
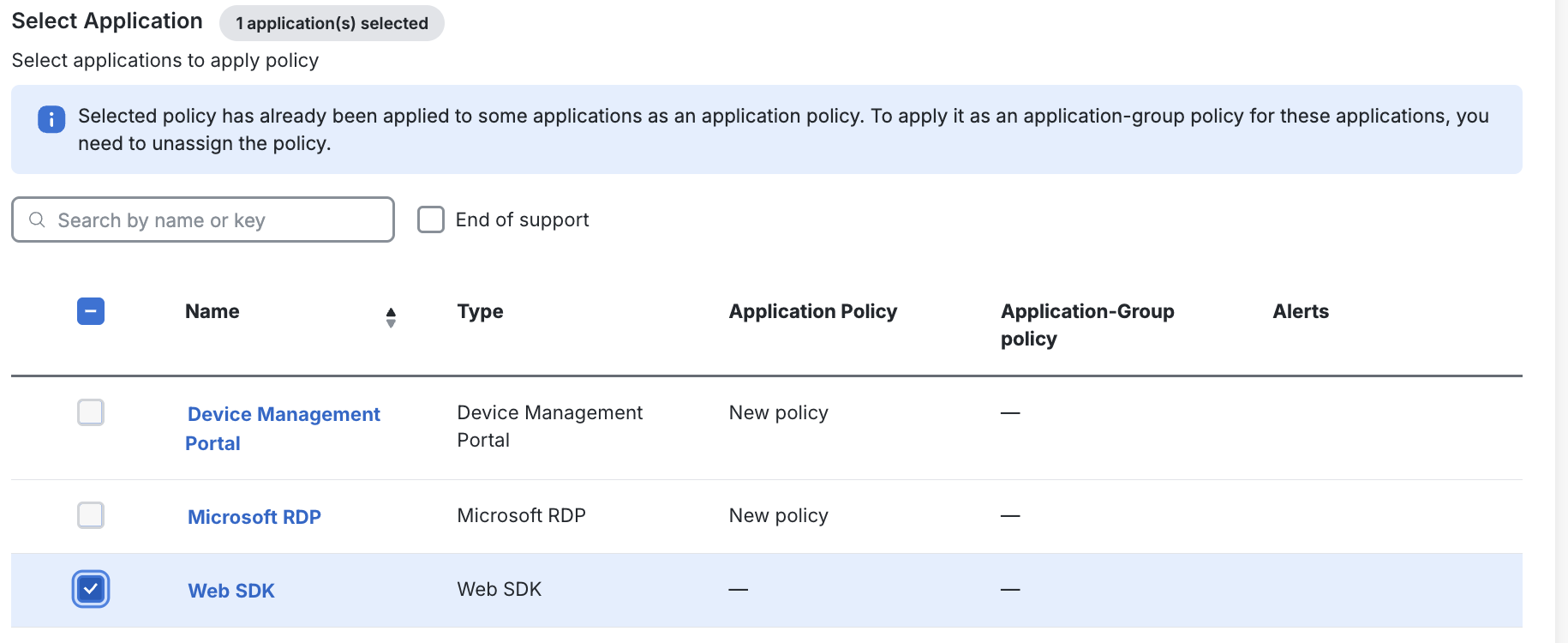
-
Under Select user groups, select the group(s) you wish to apply the policy to.
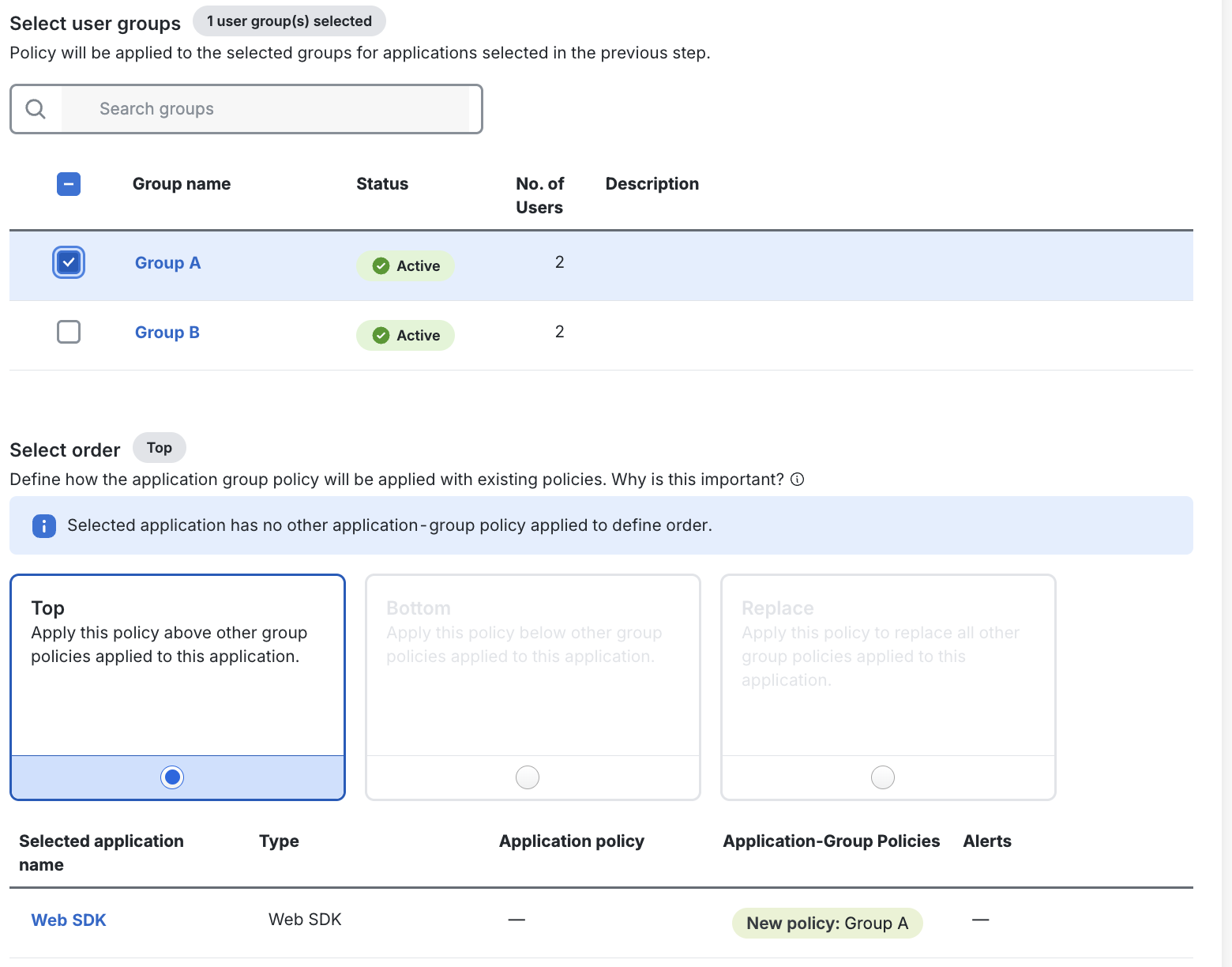
-
Under Select order, select how you wish this Application-Group policy to interact with other Application-Group policies. If you wish this Application-Group policy to override all policies for users who may be in multiple user groups with another Application-Group policy applied, select Top.
-
Review the Summary to ensure you are applying the policy as intended.
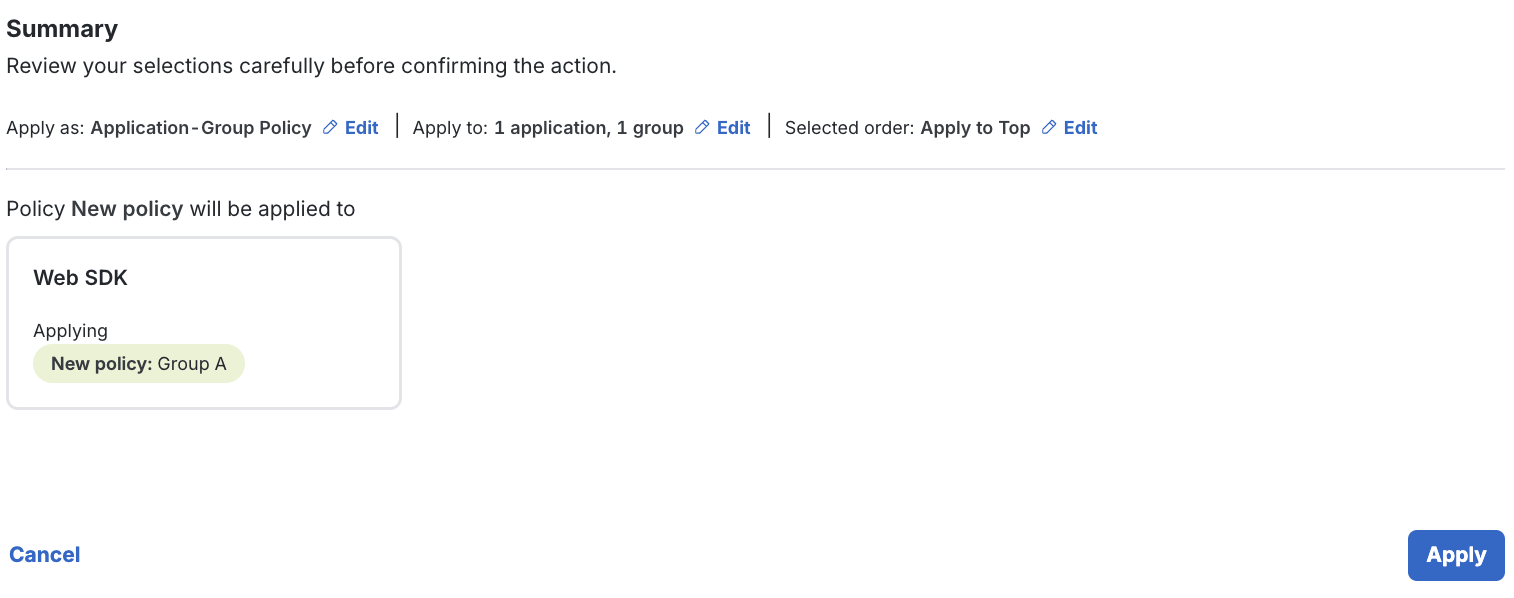
-
Click Apply in the lower-right section of the page when you are ready.
Apply a Custom User-Group Policy
Role required: Owner, Administrator, or Application Manager
User-Group policies apply to all applications. To assign an existing custom policy to a user group:
-
Navigate to the "Policies" page in the Duo Admin Panel.
-
Click the Actions → Apply dropdown for the policy you want to assign to navigate to the "Apply Policy" page.
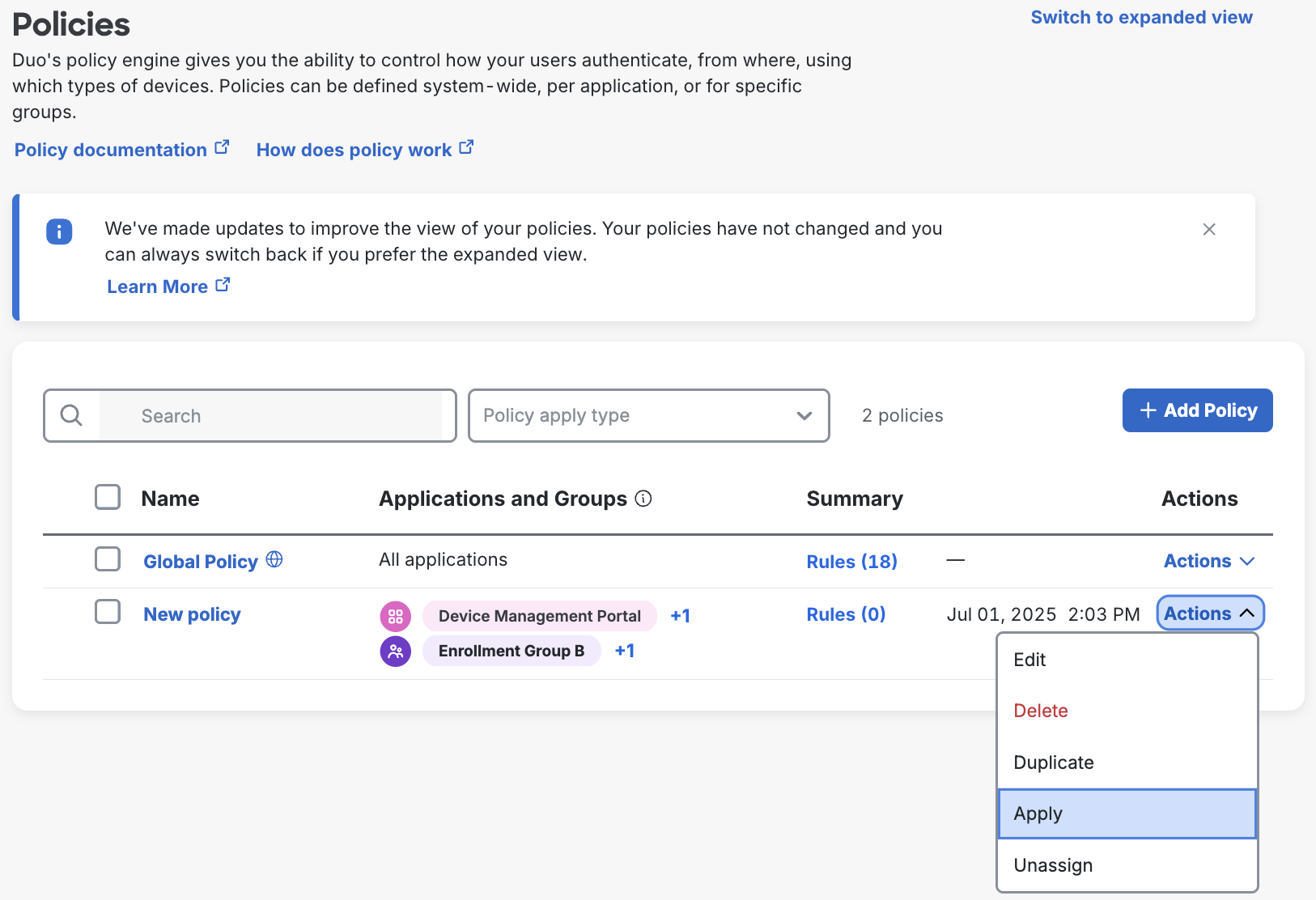
-
Under Specify type, ensure User-Group policy is selected. User-Group policy ensures a policy will be applied to a user group regardless of the application they access. User-Group policy will only override the global policy for the groups you select in the next step.
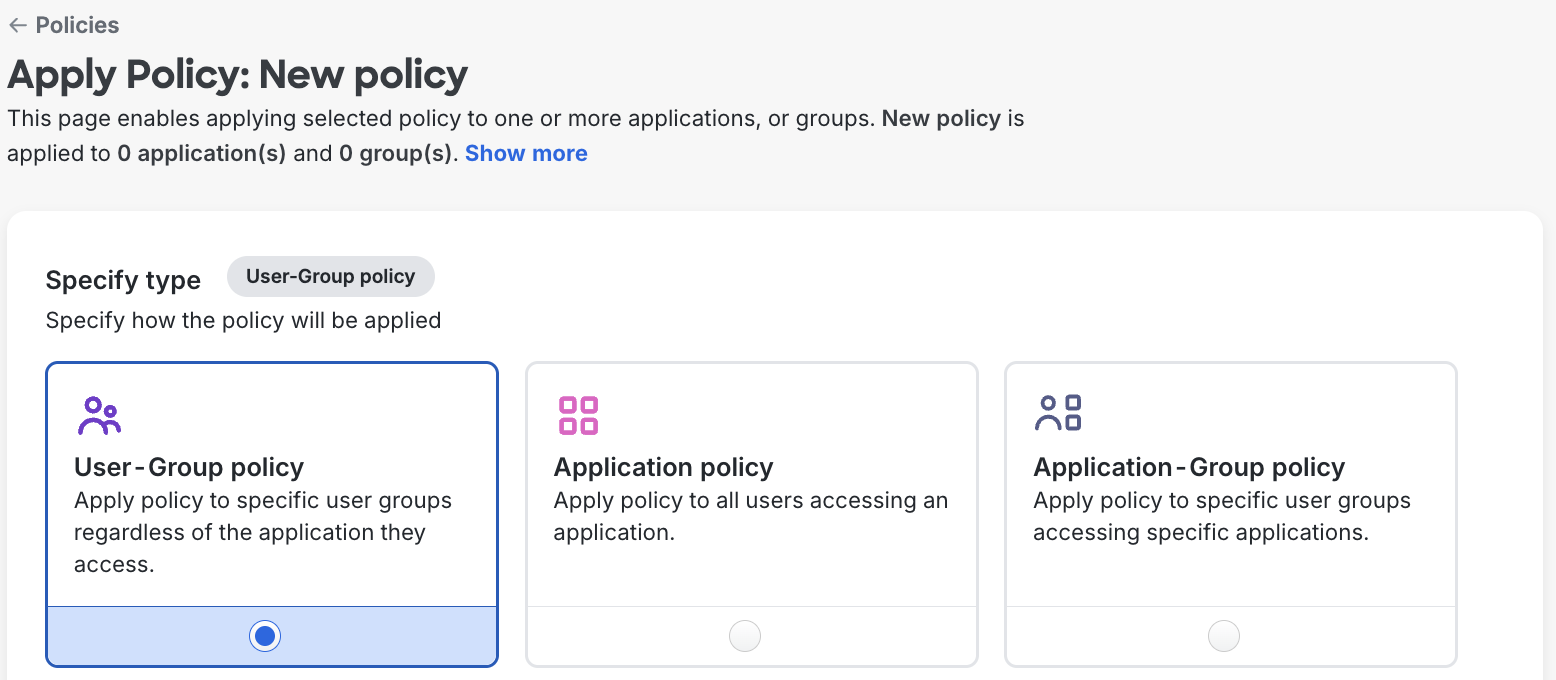
-
Under Select user groups, select the user group(s) you wish to apply the policy for.
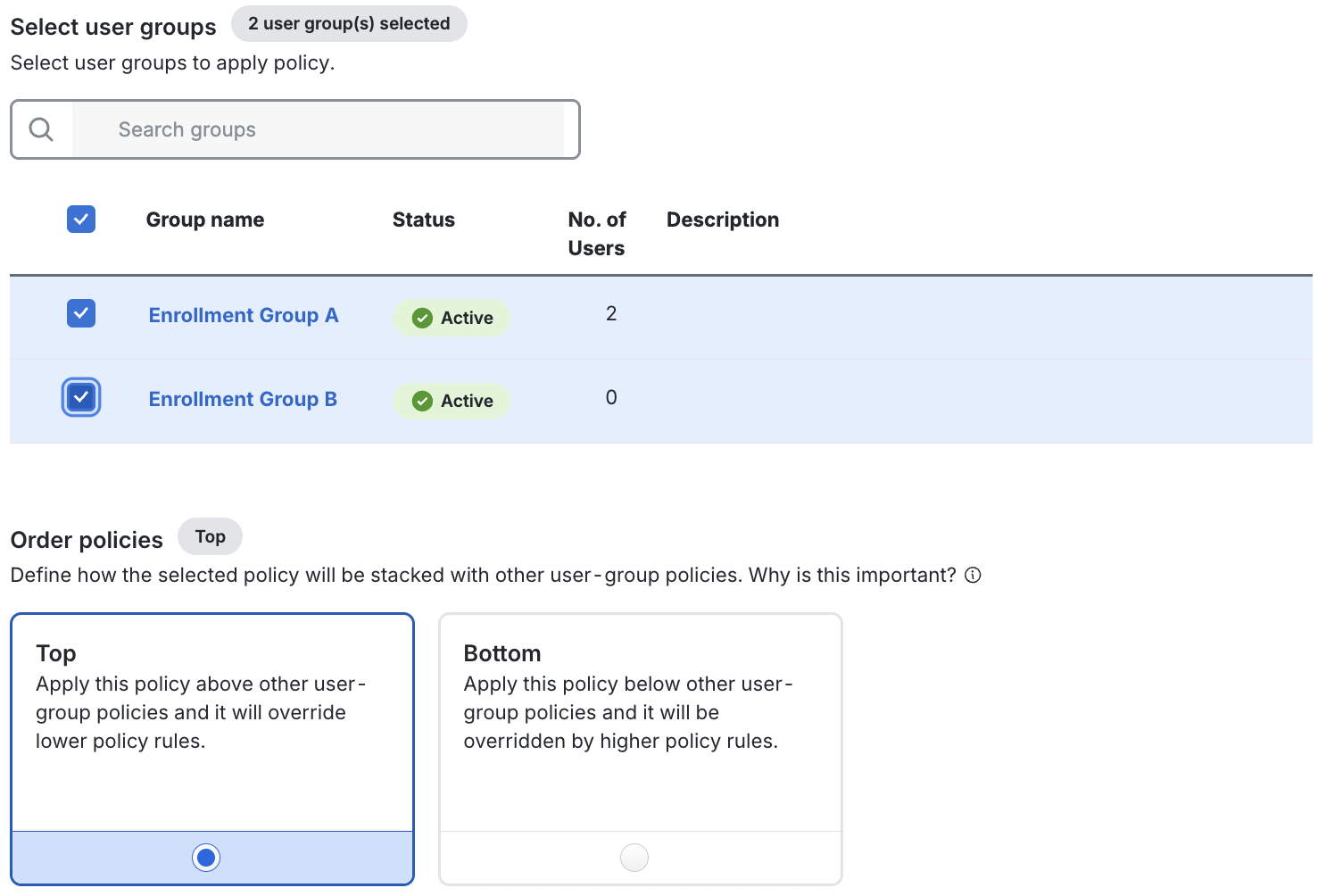
-
Under Order policies select how you wish this User-Group policy to interact with other User-Group policies. If you wish this new User-Group policy assignment to override policy for users who may be in multiple user groups with a User-Group policy applied, select Top.
-
Review the Summary to ensure you are applying the policy as intended.
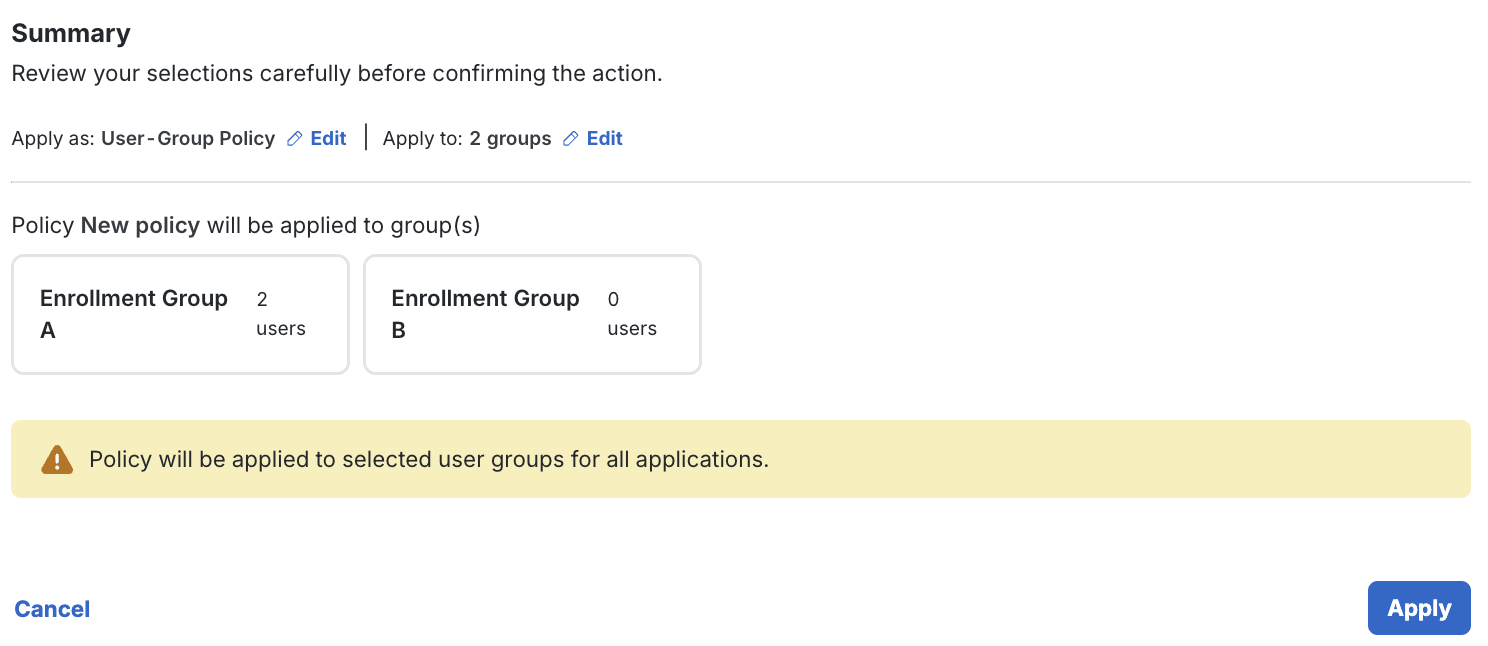
-
Click Apply in the lower-right section of the page when you are ready.
Modify a Custom Policy
Modify an existing custom policy's settings by clicking the Edit link shown to the right of the custom policy name on the main "Policies" page in the Admin Panel, or from the Policy section of an individual Duo application's details page. Make your desired changes in the policy editor, and then click Save Policy.
Changes to existing policy settings take immediate effect.
Reorder Policies
The policy framework applies custom group policy settings in the order they are listed in an application's Policy properties. When group policy settings conflict, the first policy listed has the highest precedence.
You can reorder group custom policies on an application by clicking Move to Top in the actions to the right of the group policy's name. This will move that policy one spot up in the list of group policies.
In the example below, the effective policy setting is that a member of both the "CorpHQ_Users" and "ITAdmins" groups may authenticate from a device without a screen lock enabled. Reordering the policies so that the "Require Screen Lock" group policy is listed first enforces that "ITAdmin" group members always need screen lock enabled to authenticate to this application.
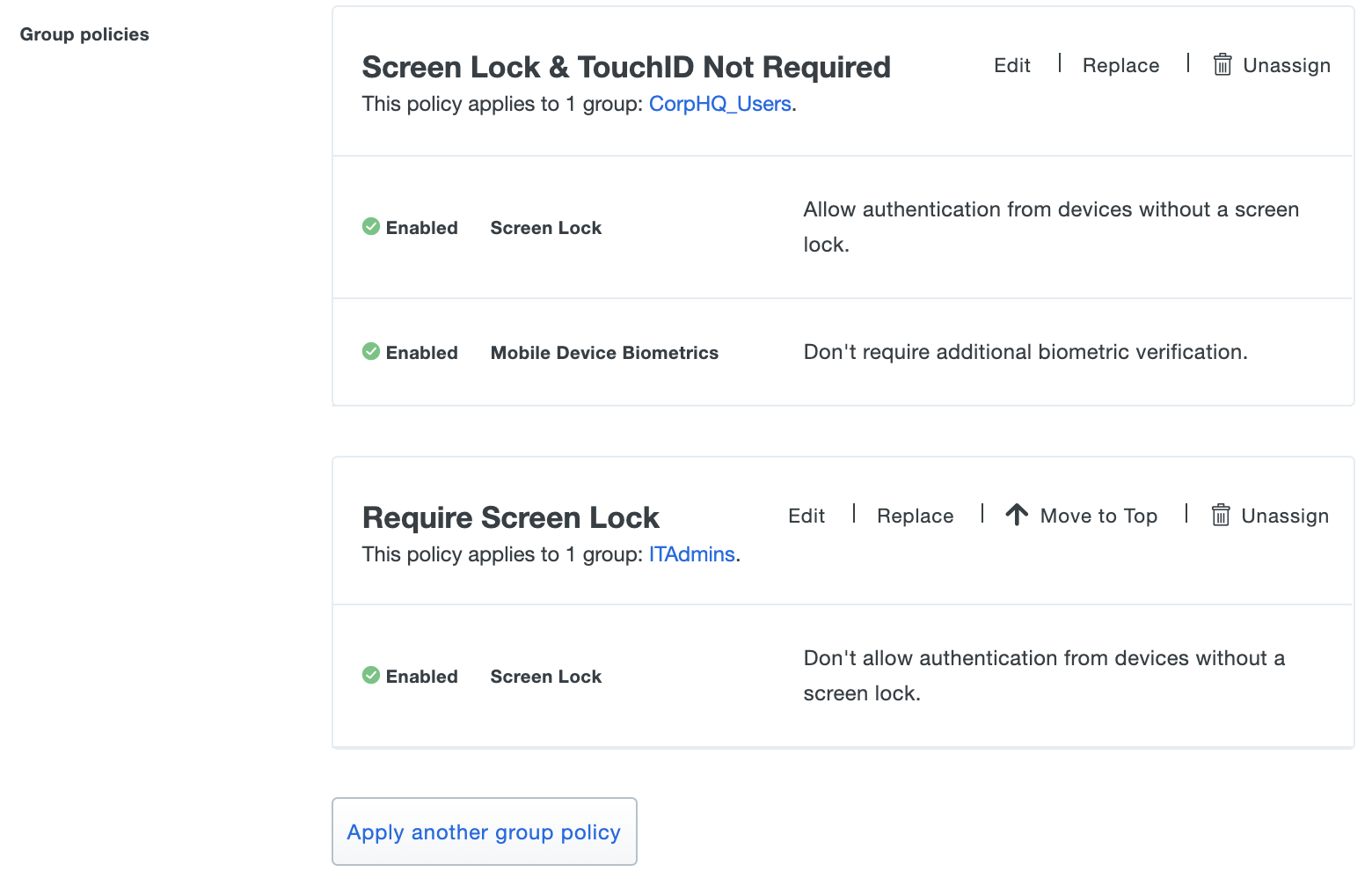
Update Policy Assignments
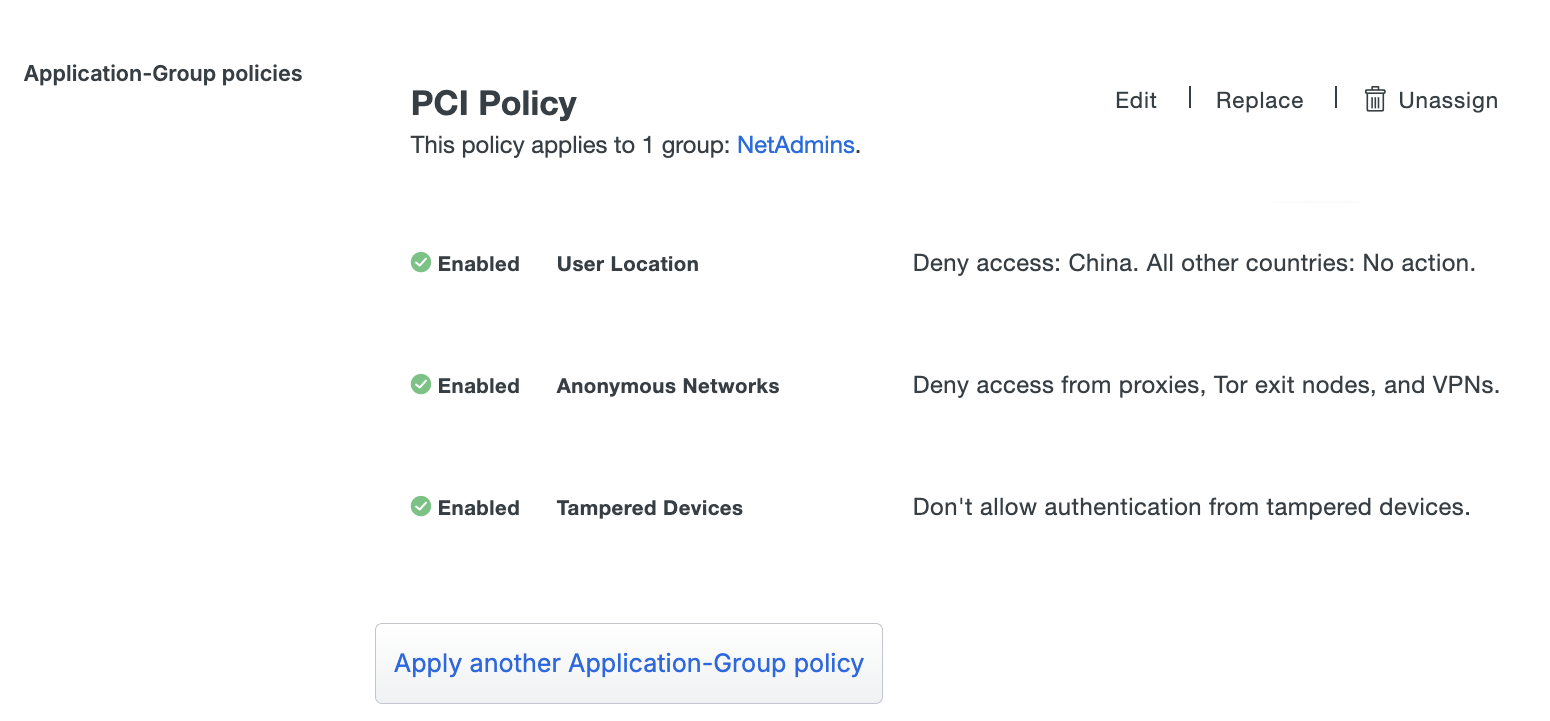
Clicking the Replace link next to any of an application's currently assigned custom policies brings up the Apply a Policy window. From this window you can pick a different custom policy to apply, or pick different groups to associate with a group policy.
View All Application Policy Assignments
The Applications page of the Duo Admin Panel lists all of your applications. The Application Policy and Application-Group Policies columns display current policy assignments for each application.
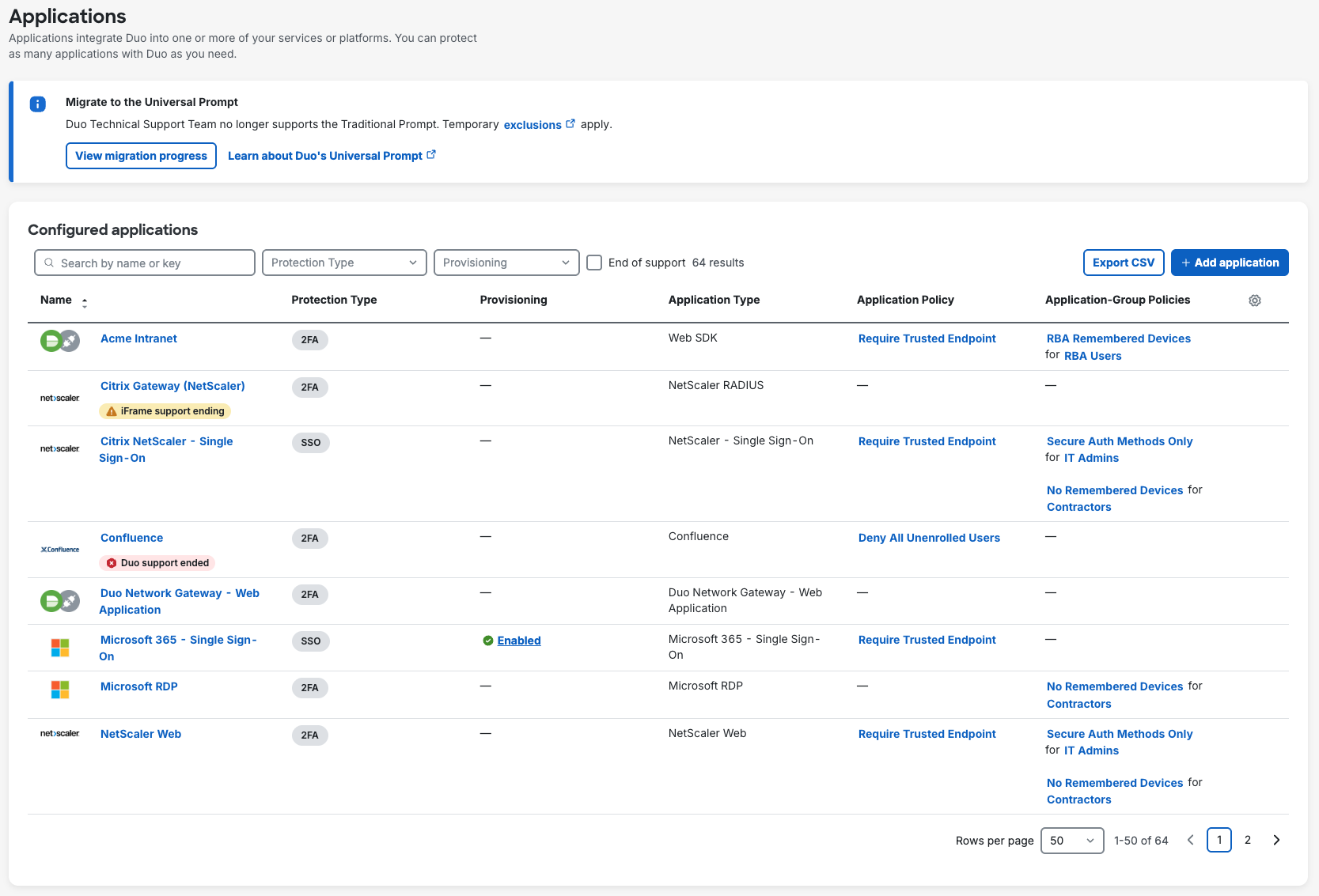
Clicking any policy name shown on the Applications page takes you to the Policy section of the properties page for that application.
Unassign or Delete Policies
Unassign policies in bulk from applications or user groups from the "Policies" page by using the Actions → Unassign action.
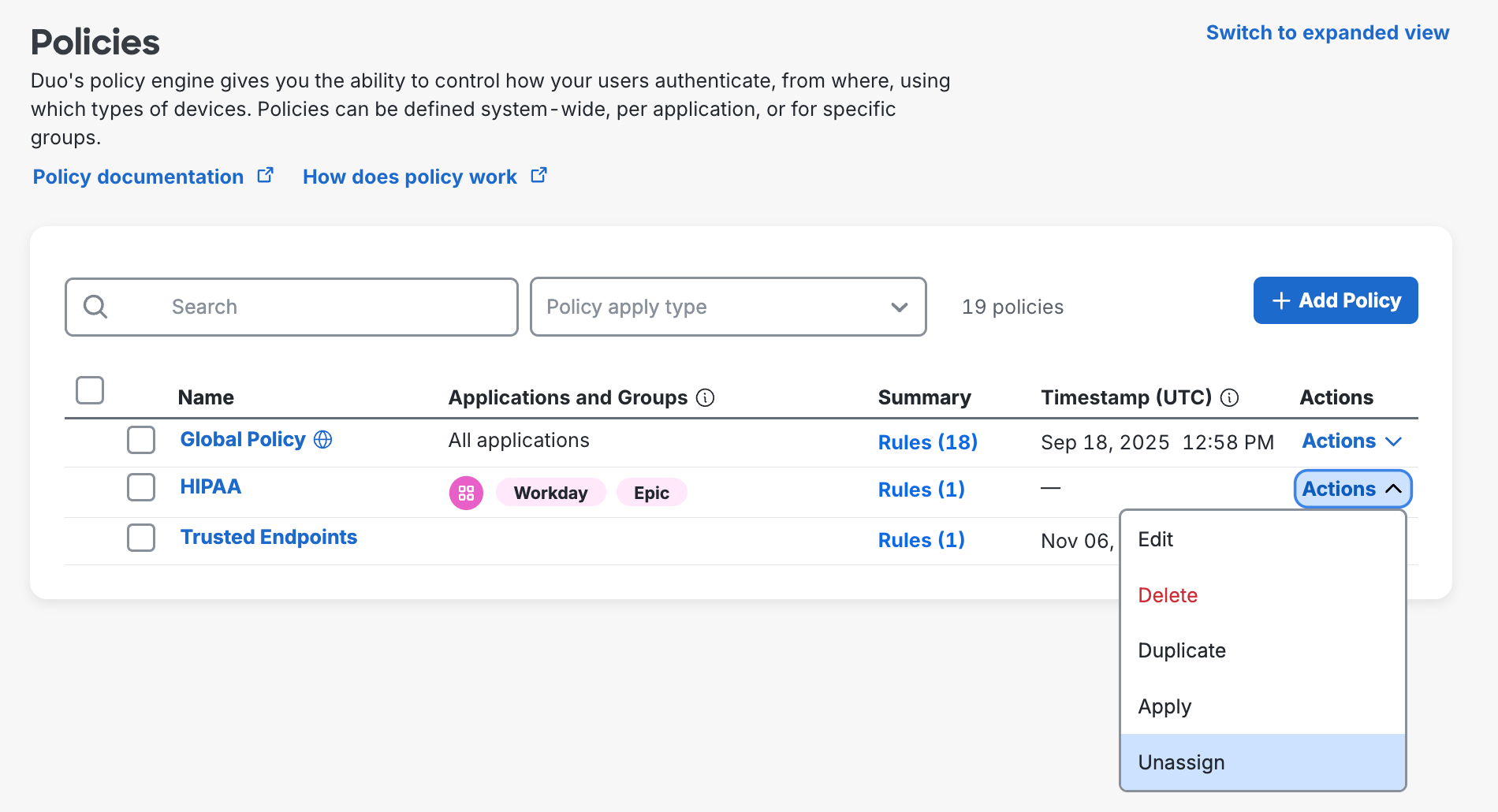
On the next page, you can choose which application(s) or group(s) to unassign this policy from before clicking Unassign.
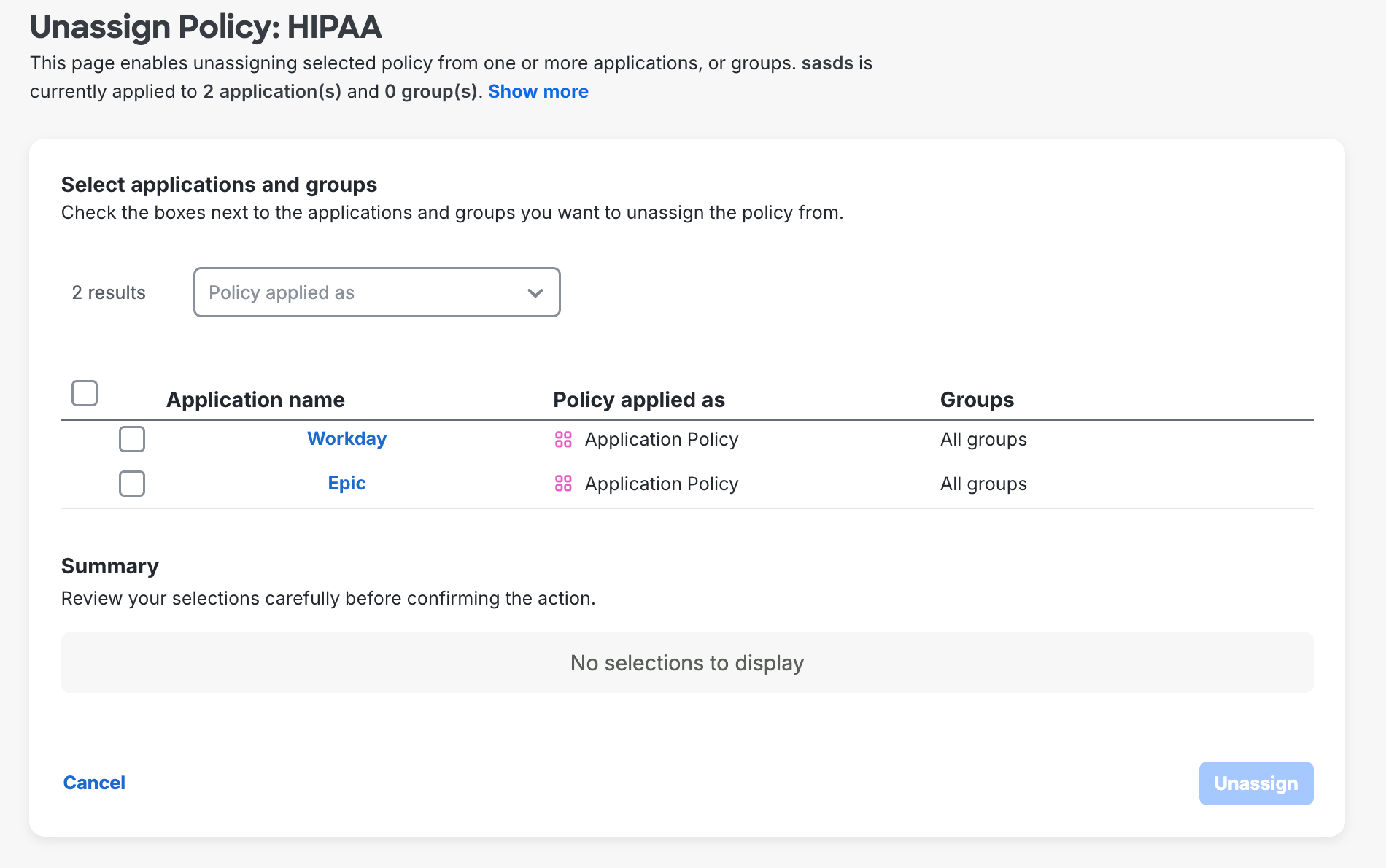
To remove a custom policy from a single application's details page, click Unassign near that policy's name in the Policy section of an application's properties page.
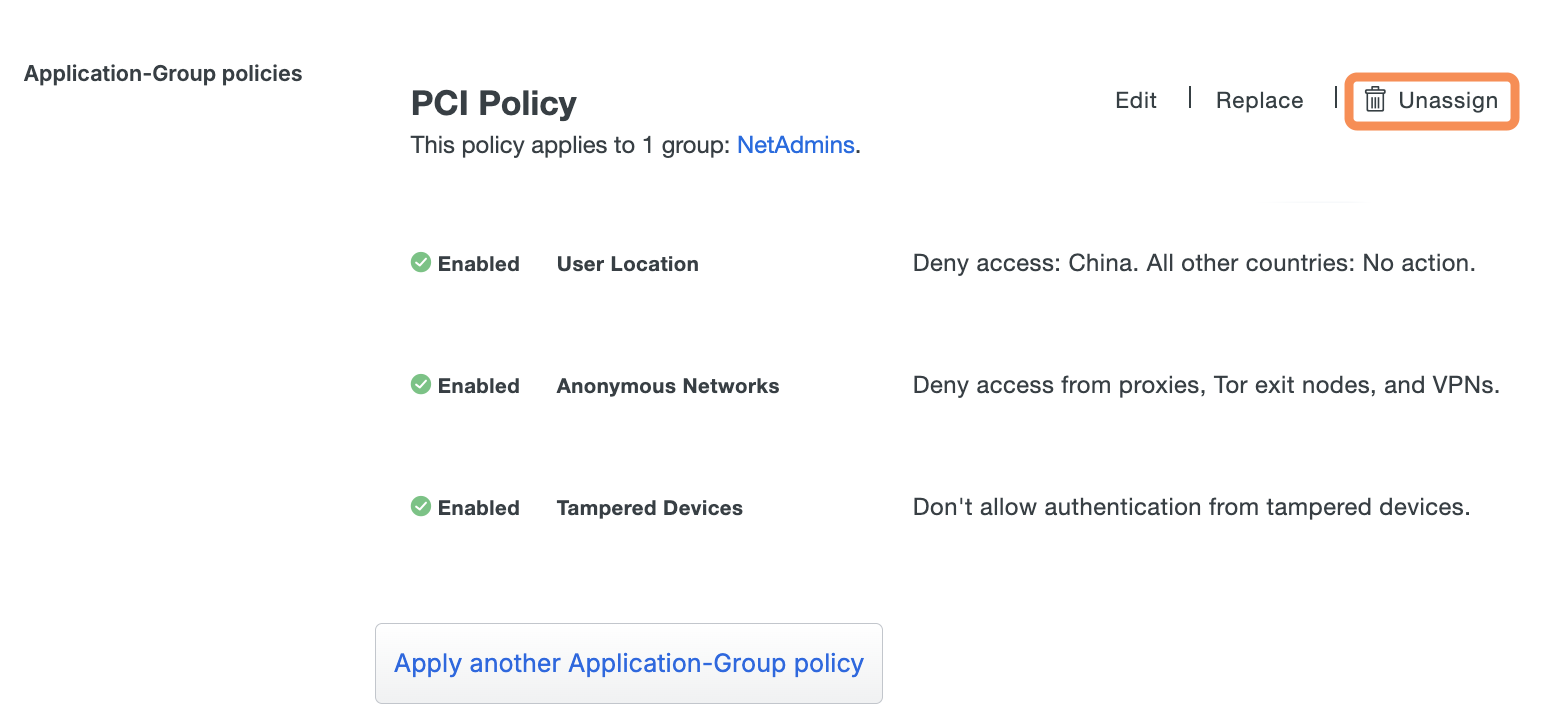
To delete a custom policy from Duo, navigate to the "Policies" page and click Actions → Delete in the desired policy row. Deleting the policy also removes it from any group or application assignments. The alert shows which applications and user groups (if any) the policy currently affects.
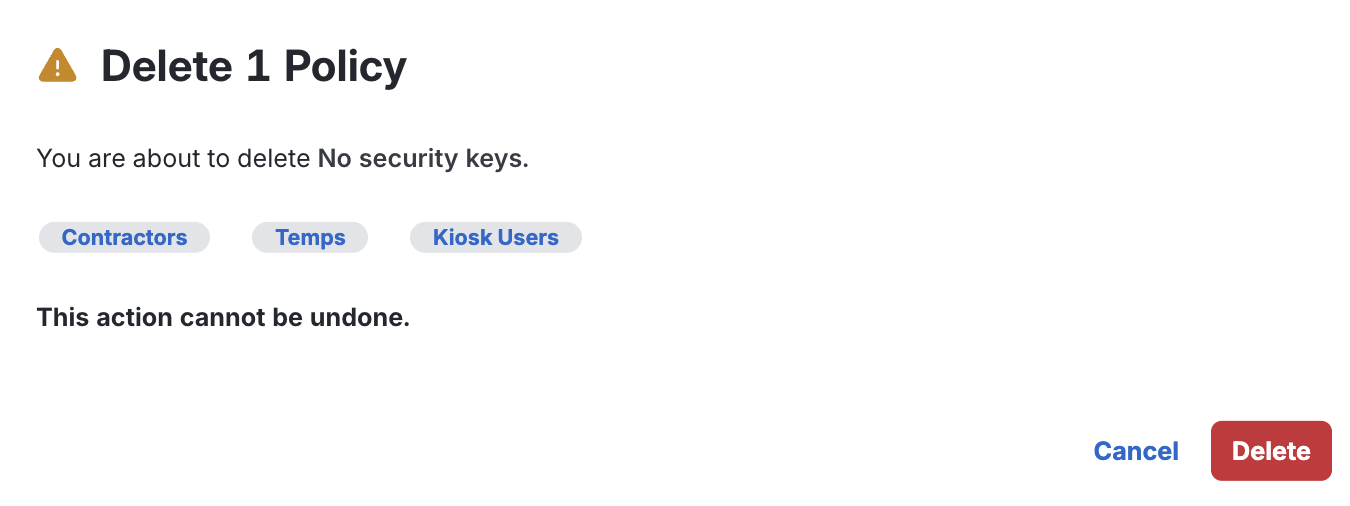
Policy Calculator
The Policy Calculator is a tool that is designed to help you manage multiple security policies in Duo. It allows you to view which policies apply when a user accesses an application, providing a clear, rule-by-rule breakdown of the final policy in effect. Not only does it give you the final calculated policy, but it also shows which specific policy each rule originates from.
You can use the Policy Calculator to:
-
Verify your policy changes. The Policy Calculator lets you view how these modifications affect the final policy for a user accessing an application.
-
Understand why a user was denied access. View the breakdown of policies leading to the denial, helping you to troubleshoot and make any necessary adjustments.
-
View rules from each of these policies and identify the rules from policies with higher precedence for the final policy.
To use the Policy Calculator:
- Log in to the Duo Admin Panel and navigate to Policies → Policy Calculator.
- Select a User and Application name from the drop-down menus.
- The effective policy for the selected user and application is shown. Scroll through the information for details.
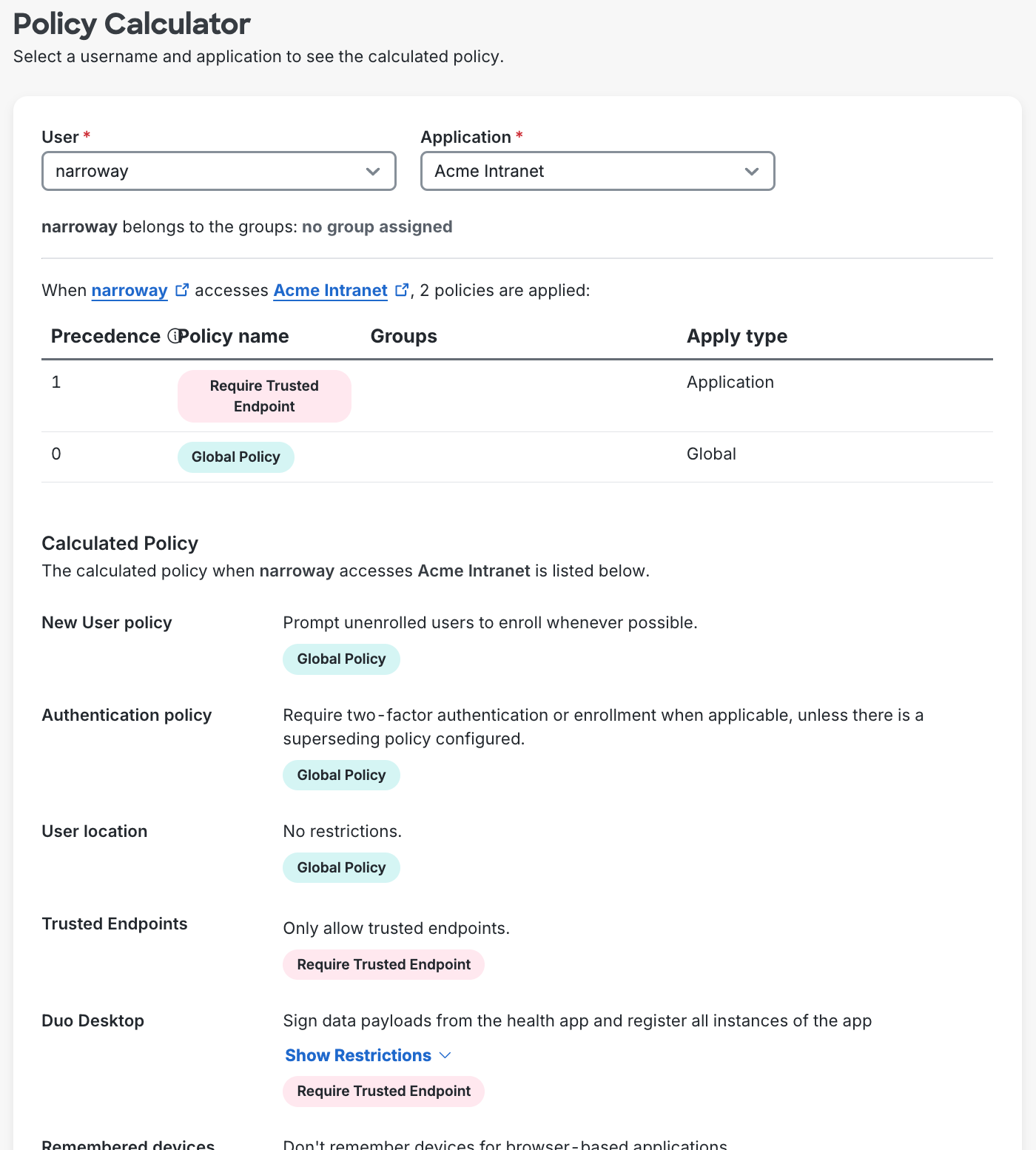
Logging
Duo captures policy related events — such as custom policy creation and edits to the Global Policy — in the Administrator Actions log.
Users Policy Settings
New User Policy
Available in: Duo Free, Duo Essentials, Duo Advantage, and Duo Premier
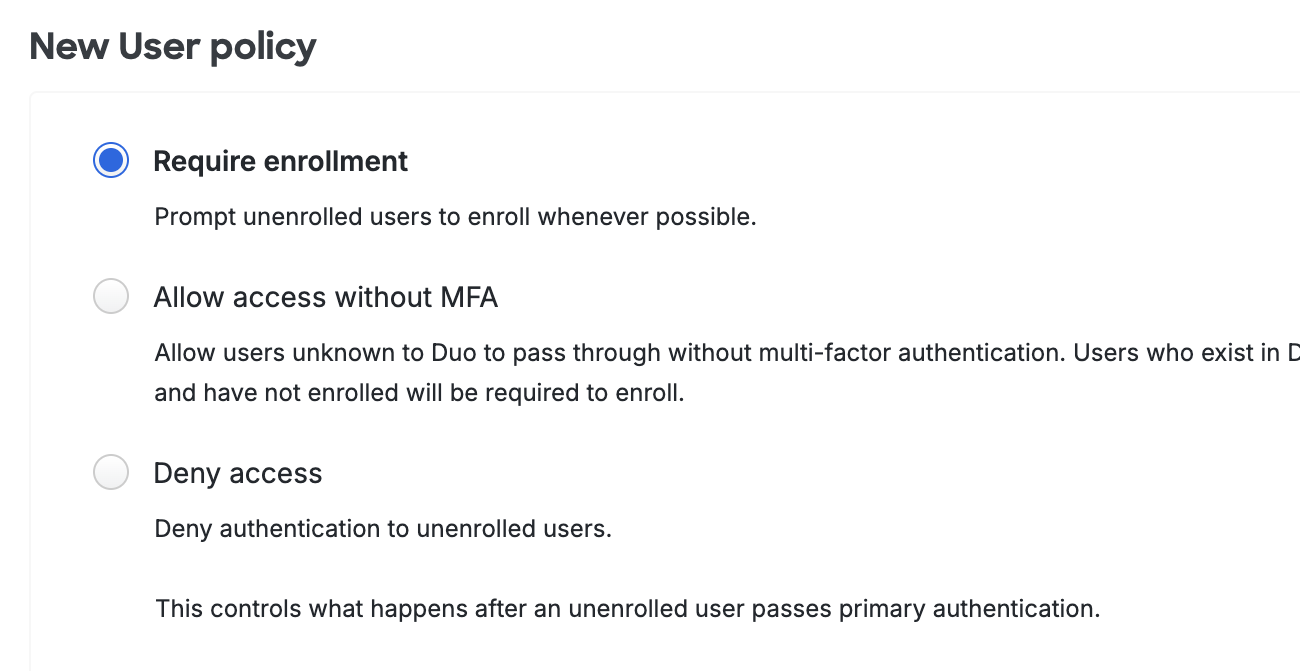
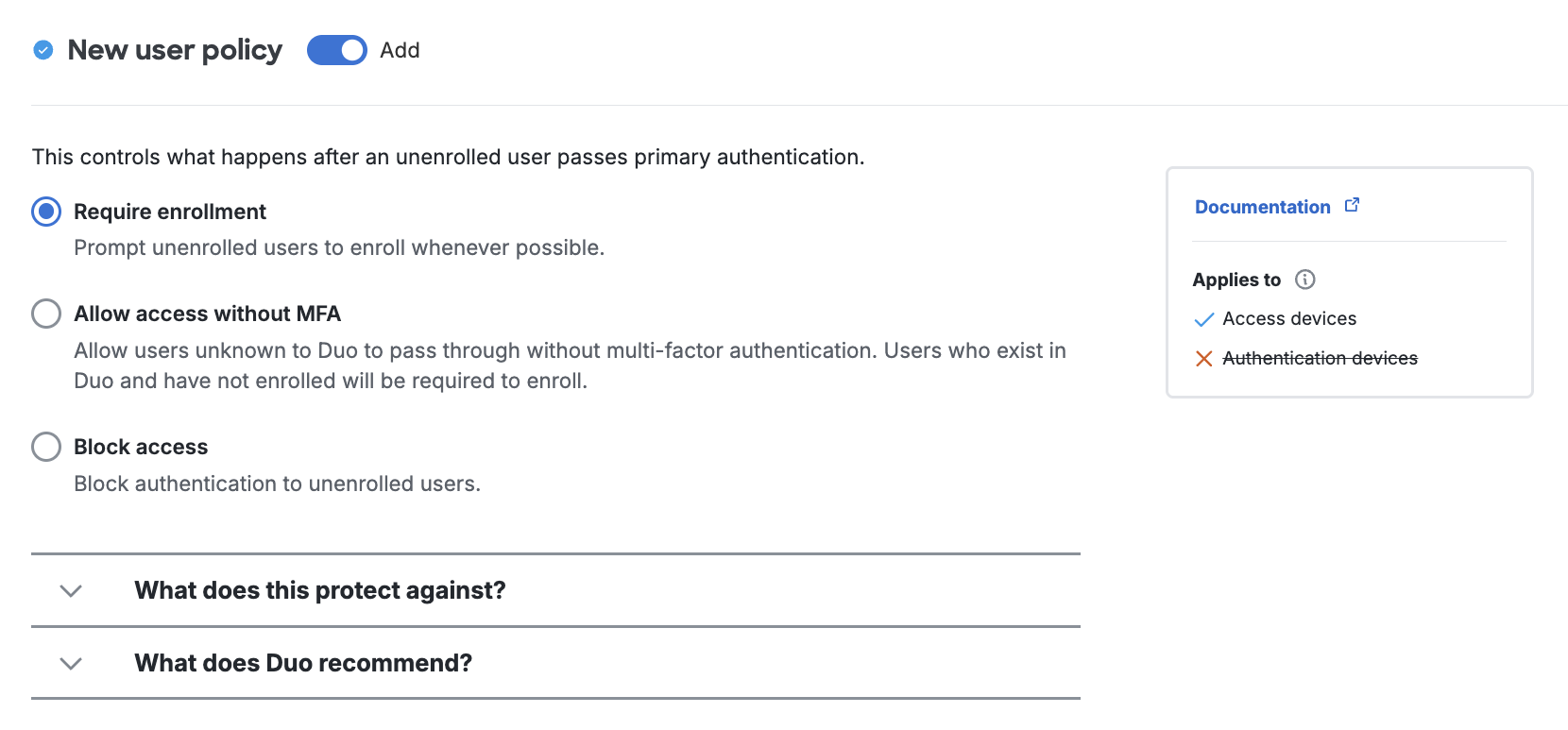
The new user policy controls authentication for unknown users, in other words, users not yet enrolled in Duo. In Duo, an enrolled user is someone who exists in the service and has at least one authentication device attached, which can be a phone, hardware token, etc. The new user policy can be one of the following:
-
Require enrollment: Users who are not enrolled in Duo see the inline self-enrollment setup process after entering their primary username and password. Users who are already enrolled in Duo are prompted to complete two-factor authentication. This is the default policy for new applications.
-
Allow access without MFA: Users who are already enrolled in Duo must use two-factor authentication. Users who do not exist in Duo are not prompted to complete enrollment and are granted access without two-factor authentication. Duo Premier, Duo Advantage, and Duo Essentials plan customers see events for users that access an application without two-factor authentication as a result of this setting in the Authentication Log.
-
Deny access or Block access: Access is denied to users not enrolled in Duo. Users must be enrolled before attempting authentication, by using one of the automatic enrollment options, bulk self-enrollment, or manual enrollment by a Duo administrator.
A new, unenrolled user may access an application when this setting allows access and user access for that application is restricted to selected permitted groups.
To change the new user policy, click the radio button next to the desired setting.
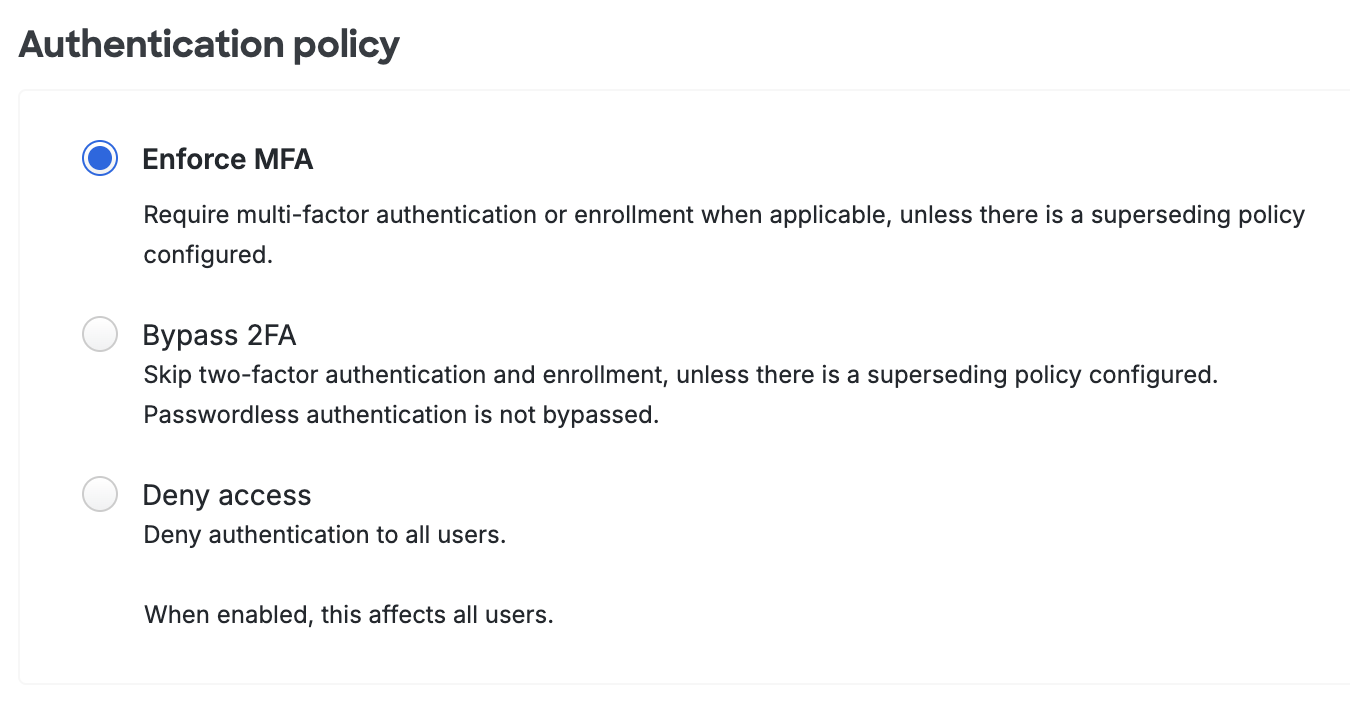
Authentication Policy
Available in: Duo Essentials, Duo Advantage, and Duo Premier
Configure this policy to change how both existing Duo users and unenrolled/new users access a Duo-protected application or to change access to selected applications. This overrides less-restrictive authentication policy settings configured at the global, application, or group level. More restrictive policy settings, such as a user location policy denying access to a specific country, still apply.
-
Enforce MFA: Two-factor authentication required unless another policy does not require it. This is the default.
-
Bypass 2FA or Skip MFA: Users may log in without completing two-factor authentication or enrollment unless another policy requires it.
-
Deny access or Block access: Blocks all users from authenticating.
Changing the authentication policy setting from the default prevents new users from completing inline self-enrollment while authenticating to applications. When set to "Bypass 2FA", users not enrolled in Duo have no opportunity for self-enrollment when accessing the application. If authentication to the application is blocked with the "Deny Access" setting, new users cannot self-enroll in that scenario either.
A new, unenrolled user may access an application when this setting permits bypass and user access for that application is restricted to selected permitted groups.
End users who receive enrollment links via email (like those sent by the directory sync process) may complete the Duo enrollment process via the emailed link regardless of the authentication policy setting.
As you deploy Duo throughout your organization you may need to let designated users access a certain application without Duo authentication, while requiring that they complete Duo 2FA when accessing any other protected application.
Accomplish this by first creating a Duo group (manually or via Directory Sync) containing those users.
Next, view the application which you want those group members to bypass Duo authentication in the Admin Panel. Click on Apply a policy to groups of users to create a new policy with the authentication policy set to Bypass 2FA, and then attach that new policy to your bypass group.
When the users in that Duo group access that application, they'll pass through to the application after successful verification of primary credentials. All other users accessing that application are subject to any other access policy settings applied to that application or in the global policy.
You can use the same process with the authentication policy set to Deny access to block users from accessing a selected application while still permitting them access to other Duo applications.
If you apply the authentication policy to an application as an application policy (instead of a group policy), then the configured bypass or deny access setting applies to all users of that application. Again, this overrides any other access policy set at the global level, and access to other Duo applications is unchanged.
Configuring the authentication policy within Duo's global policy affects all Duo applications and all users — whether the user is enrolled in Duo or not. If you set the authentication policy to deny in the global policy then no users can access any of your Duo-protected applications (unless another policy setting permits access). Conversely, if you set the authentication policy to allow access in the global policy, then all users can access any application without completing Duo two-factor authentication (unless another policy requires 2FA).
User Location
Available in: Duo Advantage and Duo Premier
The user location looks up the geographical origin of a user's access device and Duo Mobile authentication device based on the IP addresses reported by those devices, and then enforces rules based on the location. You can create rules here to enforce geoblocking for login requests based on the locations of both the access and authentication devices, or based on the location of the access device alone. You may also skip MFA for application access from specific locations.
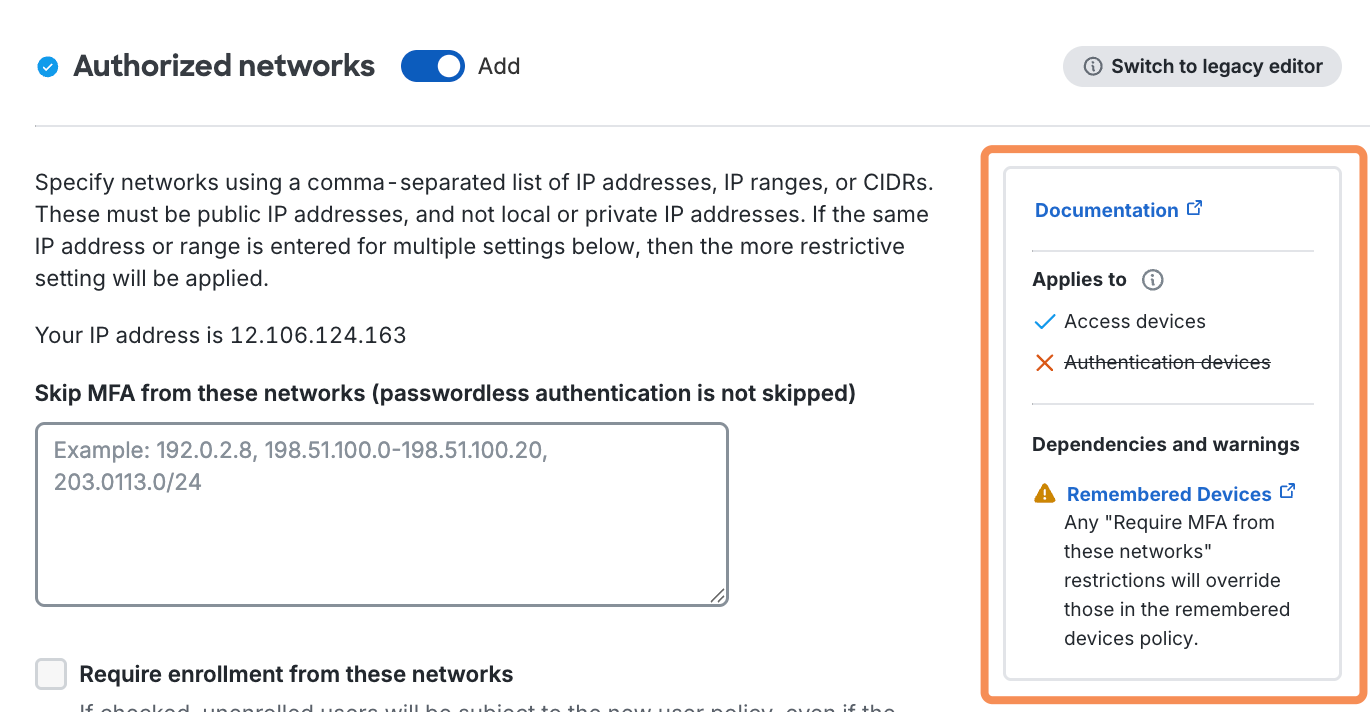
This policy setting overrides other access policies — like Authentication Policy, Authorized Networks, and Remembered Devices — when the setting applied here is more restrictive than the setting applied by those other policy options.
To change the user location policy, start typing in a country name to select it from the list, then change the drop-down to the desired setting for that country. The available settings are:
-
Don't change authentication requirements: Permits Duo authentication from the chosen country. This is the default policy setting for all locations. This is also the setting applied when an authentication has no location (i.e. the IP address of the access device is reported as 0.0.0.0, which cannot be geolocated).
-
Require 2FA or passwordless authentication even if it would normally be skipped: Always require two-factor or passwordless authentication for IP addresses originating from the selected country. This supersedes other effective policies that would permit access without 2FA or passwordless authentication.
-
Skip 2FA and allow access with only a password: Do not require Duo 2FA authentication for access requests from the named country. This setting has no effect for passwordless authentication.
-
Deny access: Prevents all Duo 2FA and passwordless authentication attempts from IP addresses originating from the specified country.
Click Add another rule to apply a different setting to a specific country or countries.
The "All other countries" settings apply when a country has no explicit rule settings applied.
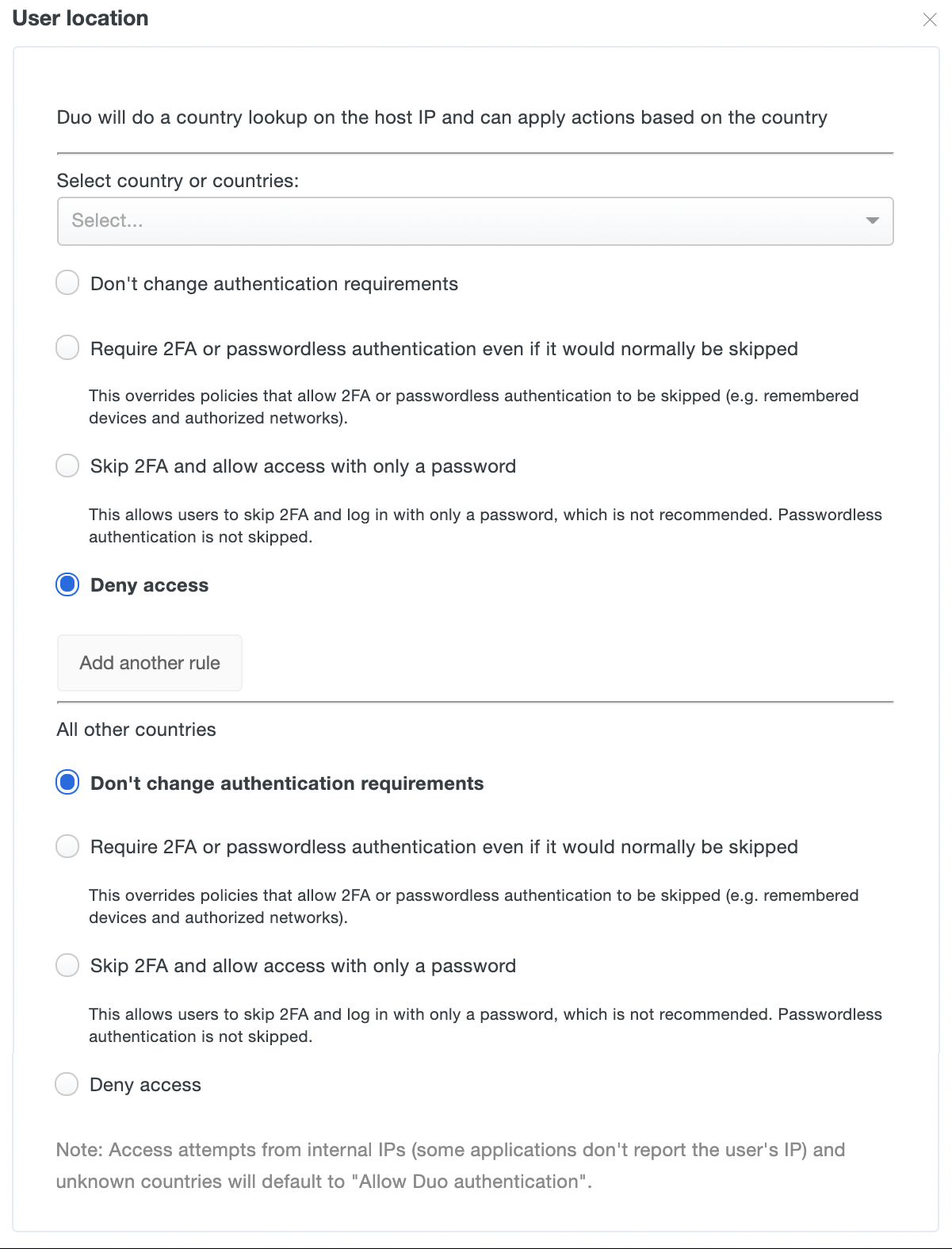
To add a user location policy rule for a specific country, start typing in a country name to select it from the list, then choose the desired setting for that country. You can add multiple countries to the same rule.
The available settings are:
-
Require MFA or passwordless authentication, even if it would normally be skipped: Always require two-factor or passwordless authentication for IP addresses originating from the selected country. This supersedes other effective policies that would permit access without 2FA or passwordless authentication.
-
Skip MFA and allow access with only a password: Do not require Duo 2FA authentication for access requests from the named country. This setting has no effect for passwordless authentication.
-
Allow access from selected countries and unknown locations: Permits application access and Duo authentication from the chosen country. This is the default policy setting for all locations. This is also the setting applied when an authentication has no location (i.e. the IP address of the access device is reported as 0.0.0.0, which cannot be geolocated).
-
Block access: Prevents all application access and Duo 2FA and passwordless authentication attempts from IP addresses originating from the specified country.
Click Add another rule to apply a different setting to a specific country or countries.
The "All other countries" settings apply when a country has no explicit rule settings applied.
A new user location policy will consider the locations of both the device accessing the protected application and the location of the Duo Mobile device used for authentication. To disregard the Duo Mobile device's location, enable the Only check access device IP option under "Advanced settings". Be aware that enabling this option reduces the effectiveness of user location blocking rules.
Expand User location data (last 30 days) in the policy editor for recent users' authentications by country to help you make location policy decisions, as well as authentications blocked by country rules you have already created.
Learn more about Duo Passwordless and how to enable passwordless authentication for your users in the Duo Passwordless documentation.
Devices Policy Settings
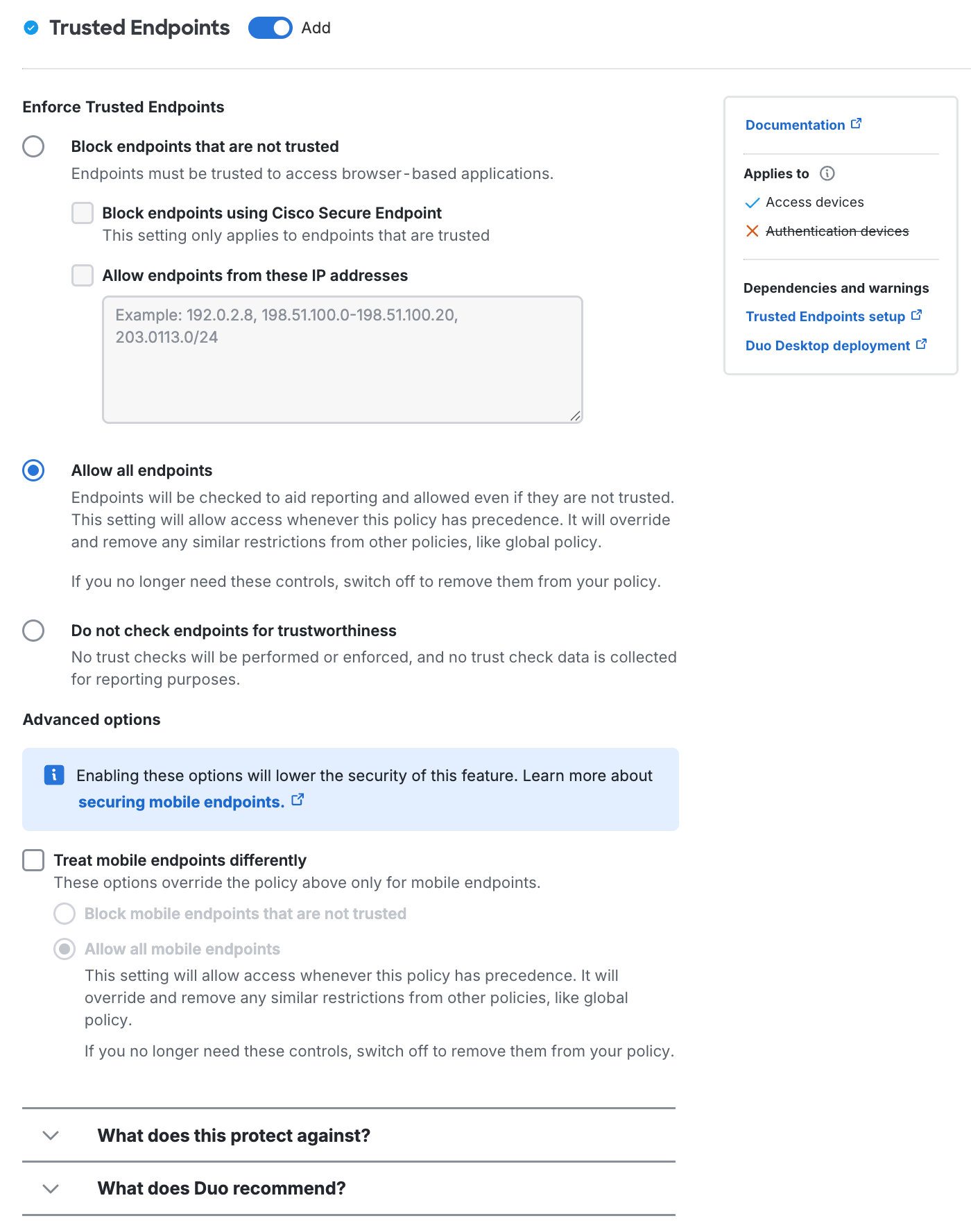
Trusted Endpoints
Certificate-based Trusted Endpoint verification reached end-of-life on October 7, 2024. Duo device certificates will no longer renew after October 2024. Migrate existing management integrations to solutions that verify endpoint status with Duo Mobile or Duo Desktop. Learn more about migration options in the Duo Trusted Endpoints Certificate Migration Guide.
Available in: Duo Essentials, Duo Advantage, and Duo Premier
Partially enforced for passwordless authentication
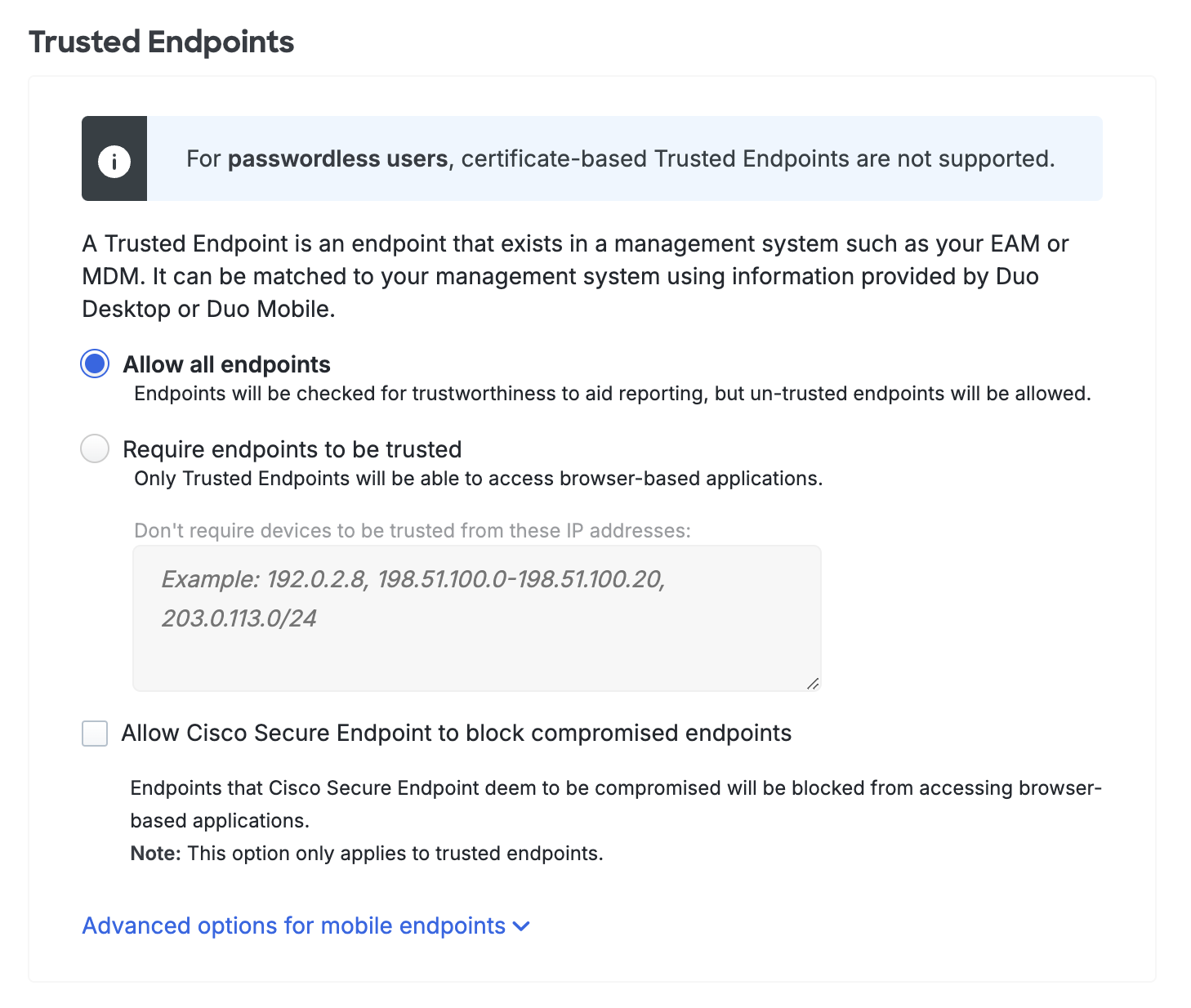
Duo's trusted endpoints feature determines whether an access device is managed by your organization or is an unmanaged "bring your own" or unknown device. When an application loads the Duo Prompt it checks for the presence of verification information from your endpoint management software, Duo Desktop, or Duo Mobile on that endpoint. You can use this policy to gain information about the devices used to access your Duo-protected web applications, and optionally restrict access from unmanaged endpoints.
Passwordless support for Trusted Endpoints device trust policy applies only to management systems that rely on Cisco Secure Endpoint verification, Duo Desktop trust verification, or Duo Mobile managed devices. Duo Passwordless does not support trusted device verification using certificates or Google Verified Access.
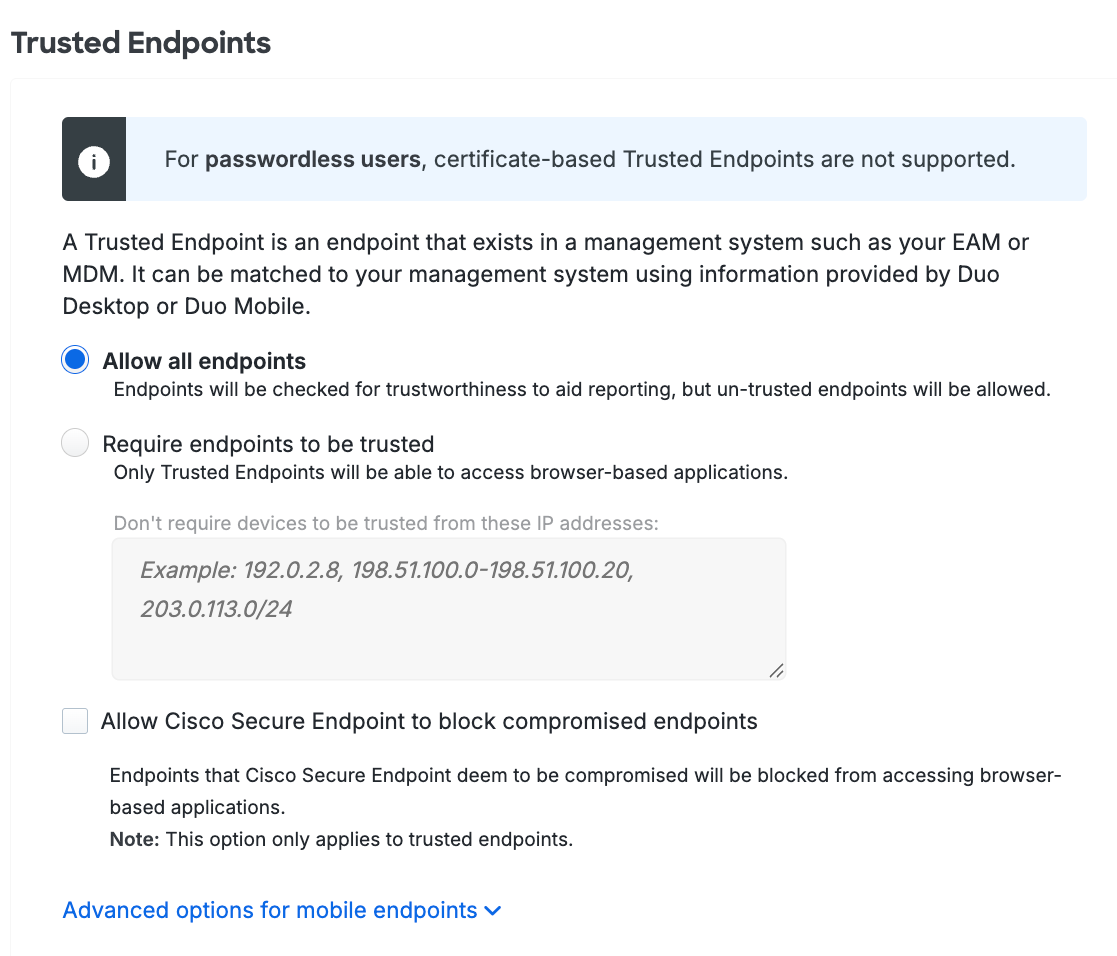
The primary endpoint policy options are:
-
Allow all endpoints: Duo checks the endpoint for validation of trusted device status from your endpoint management software, Duo Desktop, or Duo Mobile installed on the device, and records the endpoint's trusted status. No endpoints are blocked. This is the default.
-
Require endpoints to be trusted: Duo prevents access from endpoints that fail the endpoint management system, Duo Desktop, or Duo Mobile verification check.
- Don't require devices to be trusted from these IP addresses: Users attempting to access Duo-protected resources from these endpoints will bypass the trusted device check. Specify a block of IP addresses, IP ranges, or CIDRs as a comma-separated list.
-
Allow Cisco Secure Endpoint to block compromised endpoints: Duo verifies Windows and macOS endpoint status in Cisco Secure Endpoint and blocks access from endpoints which Cisco Secure Endpoint identifies as "compromised". Learn more about Duo and Cisco Secure Endpoint.
It's possible to apply different trusted endpoint policies to mobile devices than to computers. For example, you may want to track the status of application access by unmanaged or untrusted workstations without blocking access, while at the same time preventing application access from unmanaged or untrusted mobile endpoints.
If you'd like to enable this functionality then click on Advanced Options for Mobile Endpoints to expose these additional selections:
-
Allow all mobile endpoints: All mobile endpoints may access web-based applications. Duo checks the mobile endpoint for validation of trusted device status from an MDM or the Duo Mobile app installed on the device, and records the endpoint's trusted status.
-
Require mobile endpoints to be trusted: Duo prevents access from mobile endpoints that fail the MDM or Duo Mobile verification check.
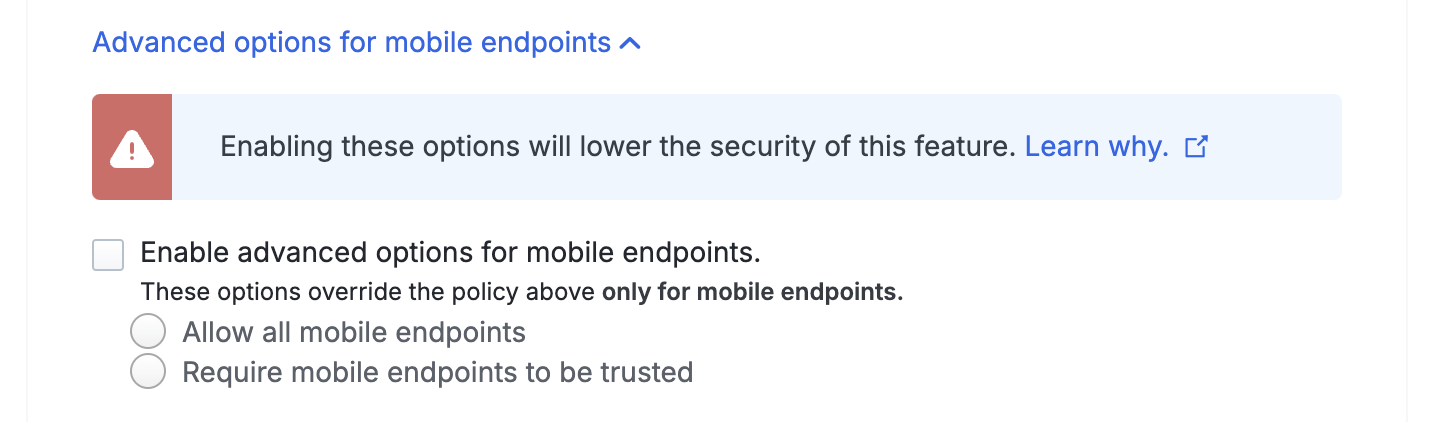
Changing the trusted mobile endpoint option could potentially make your overall trusted endpoints deployment less secure. Learn more about the security implications of enabling mobile endpoint options in your trusted endpoints policy.
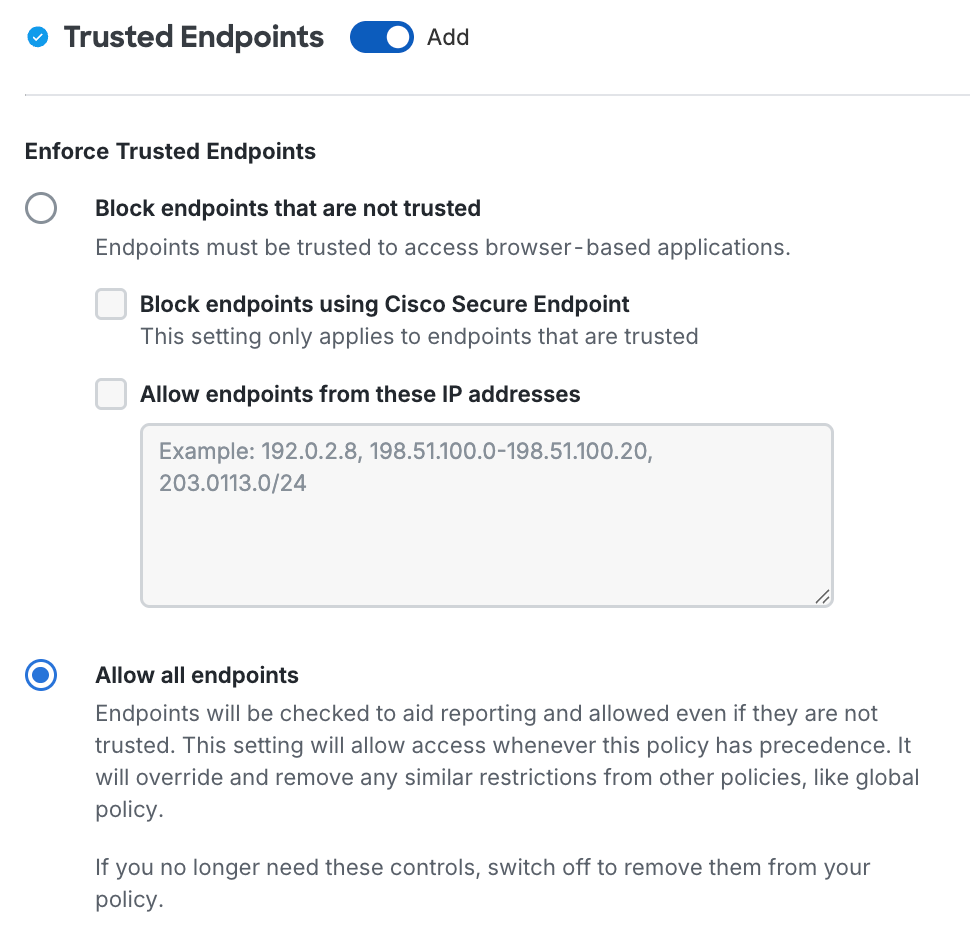
The primary endpoint policy options are:
-
Block endpoints that are not trusted: Duo prevents access from endpoints that fail the endpoint management system, Duo Desktop, or Duo Mobile verification check.
-
Block endpoints using Cisco Secure Endpoint: Duo verifies Windows and macOS endpoint status in Cisco Secure Endpoint and blocks access from endpoints which Cisco Secure Endpoint identifies as "compromised". Learn more about Duo and Cisco Secure Endpoint.
-
Allow endpoints from these IP addresses: Users attempting to access Duo-protected resources from these endpoints will bypass the trusted device check. Specify a block of IP addresses, IP ranges, or CIDRs as a comma-separated list.
-
-
Allow all endpoints: Duo checks the endpoint for validation of trusted device status from your endpoint management software, Duo Desktop, or Duo Mobile installed on the device, and records the endpoint's trusted status. No endpoints are blocked. This is the default.
-
Do not check endpoints for trustworthiness: Do not perform any trust checks or collect trust information for access devices. No endpoints are blocked.
It's possible to apply different trusted endpoint policies to mobile devices than to computers. For example, you may want to track the status of application access by unmanaged or untrusted workstations without blocking access, while at the same time preventing application access from unmanaged or untrusted mobile endpoints.
If you'd like to enable this functionality then enable Treat mobile endpoints differently under "Advanced options" to expose these additional selections:
-
Block mobile endpoints that are not trusted: Duo prevents access from mobile endpoints that fail the MDM or Duo Mobile verification check.
-
Allow all mobile endpoints: All mobile endpoints may access web-based applications. Duo checks the mobile endpoint for validation of trusted device status from an MDM or the Duo Mobile app installed on the device, and records the endpoint's trusted status.
Changing the trusted mobile endpoint option could potentially make your overall trusted endpoints deployment less secure. Learn more about the security implications of enabling mobile endpoint options in your trusted endpoints policy.
See our full Trusted Endpoints guide for more information and step-by-step deployment instructions.
Duo Desktop & Device Health
Available in: Duo Essentials, Duo Advantage, and Duo Premier
Duo Desktop & device health checks give organizations more control over which laptop and desktop devices can access protected applications based on the security posture of the device or presence of Duo Desktop on the endpoint. When users start first-time Duo enrollment or the first time users log in to an application protected by the web-based Duo Prompt, if the effective Duo Desktop policy requires the app then they must download and install Duo Desktop to proceed.
With Duo Desktop installed and device health checks configured, Duo blocks access if the device is unhealthy based on the Duo policy definition and informs the user of the reason the authentication was denied.
Some device health check options do not require Duo Desktop installed on the device. The check instead uses information reported by an external device data source, such as Chrome Enterprise browser. Any device health check options which require health information provided by Duo Desktop are noted. Duo Desktop is not available for Chrome OS. Device health checks for Chrome OS require the Chrome Enterprise browser data source.
Duo Desktop & device health policy options in Duo Advantage and Duo Premier
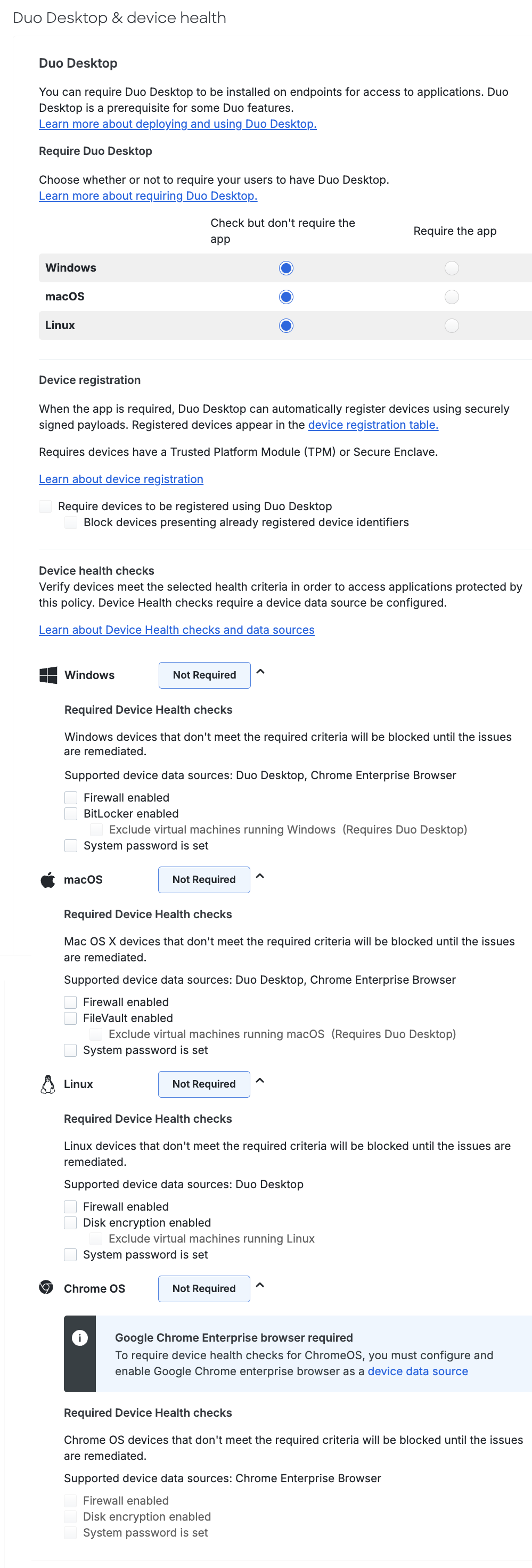
Duo Essentials policy options include requiring the Duo Desktop app and device registration, but no device health check options.
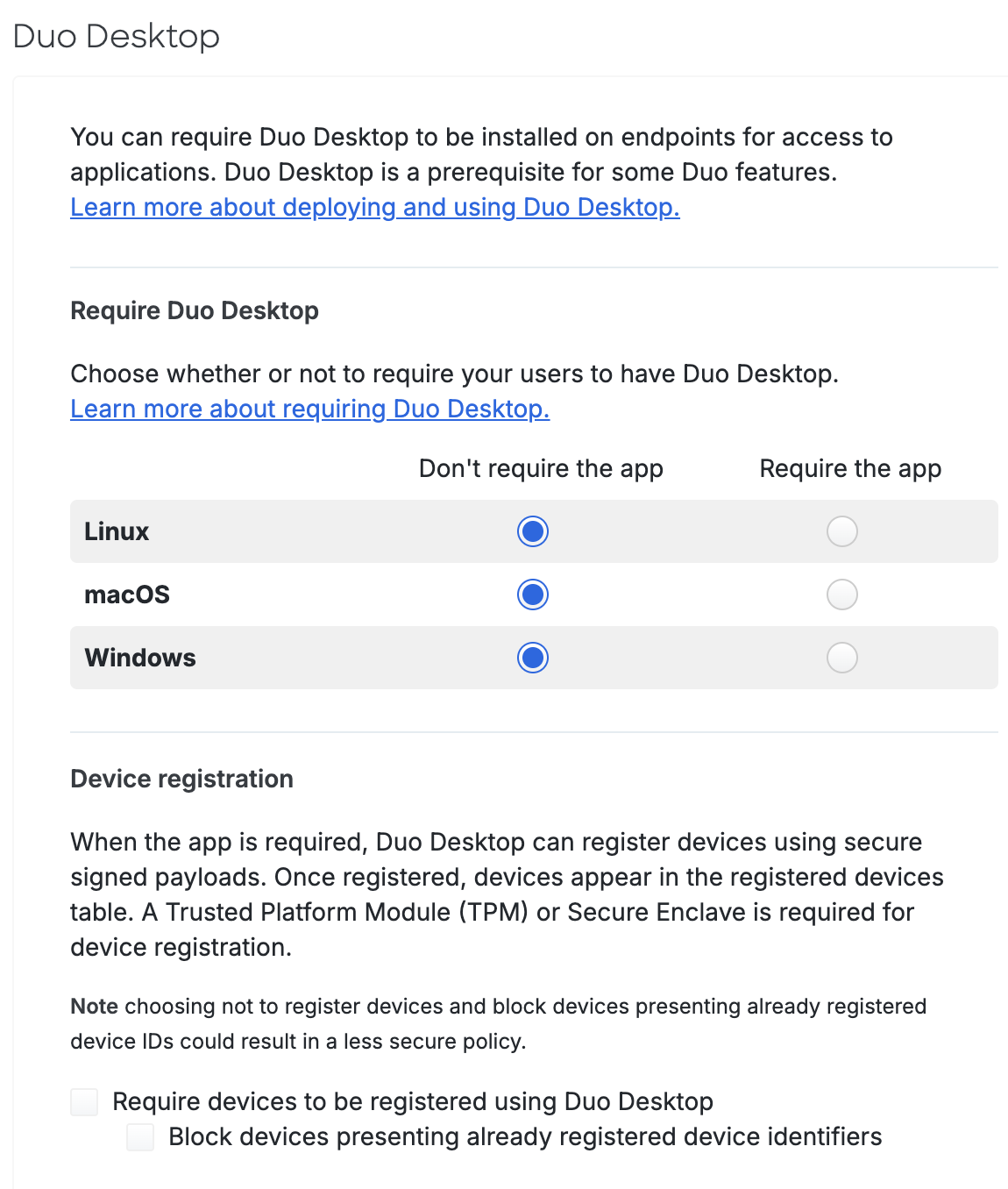
Duo Desktop policy options in Duo Essentials
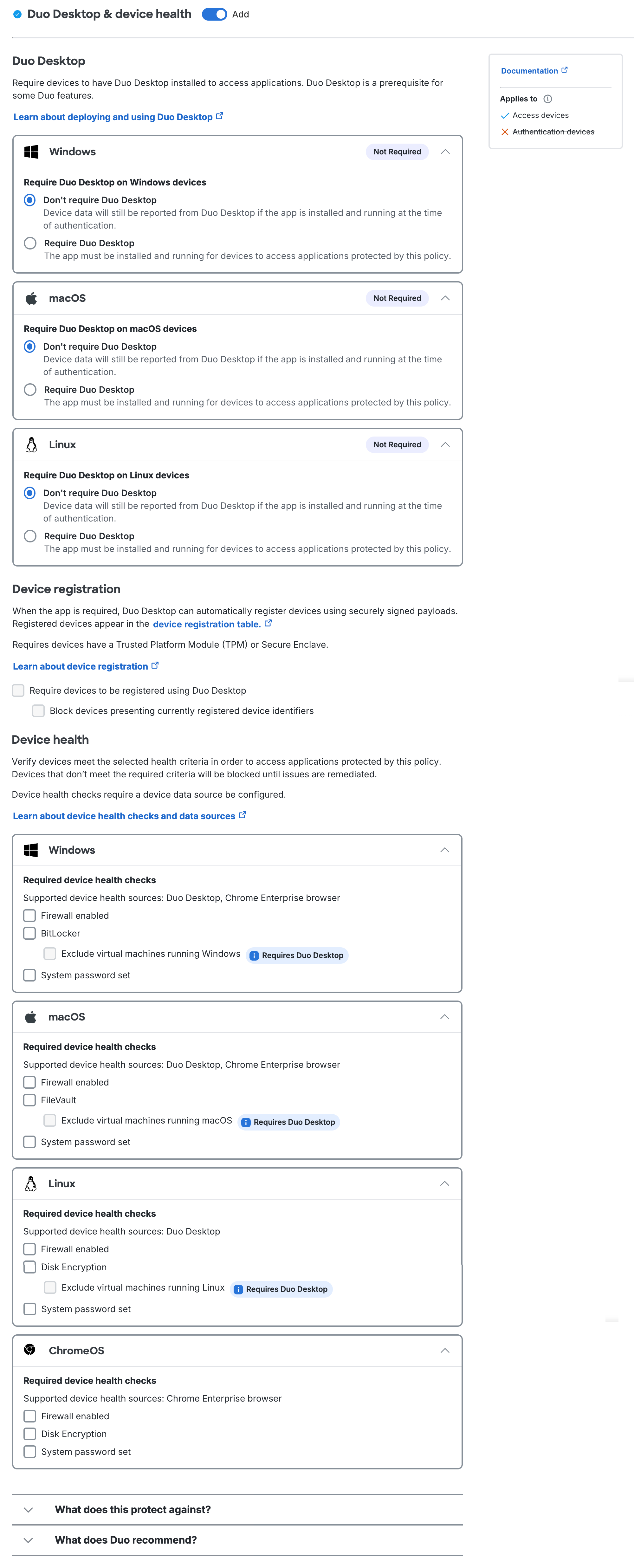
Duo Desktop & device health policy options in Duo Advantage and Duo Premier
Duo Essentials policy options include requiring the Duo Desktop app and device registration, but no device health check options.
Duo Desktop policy options in Duo Essentials
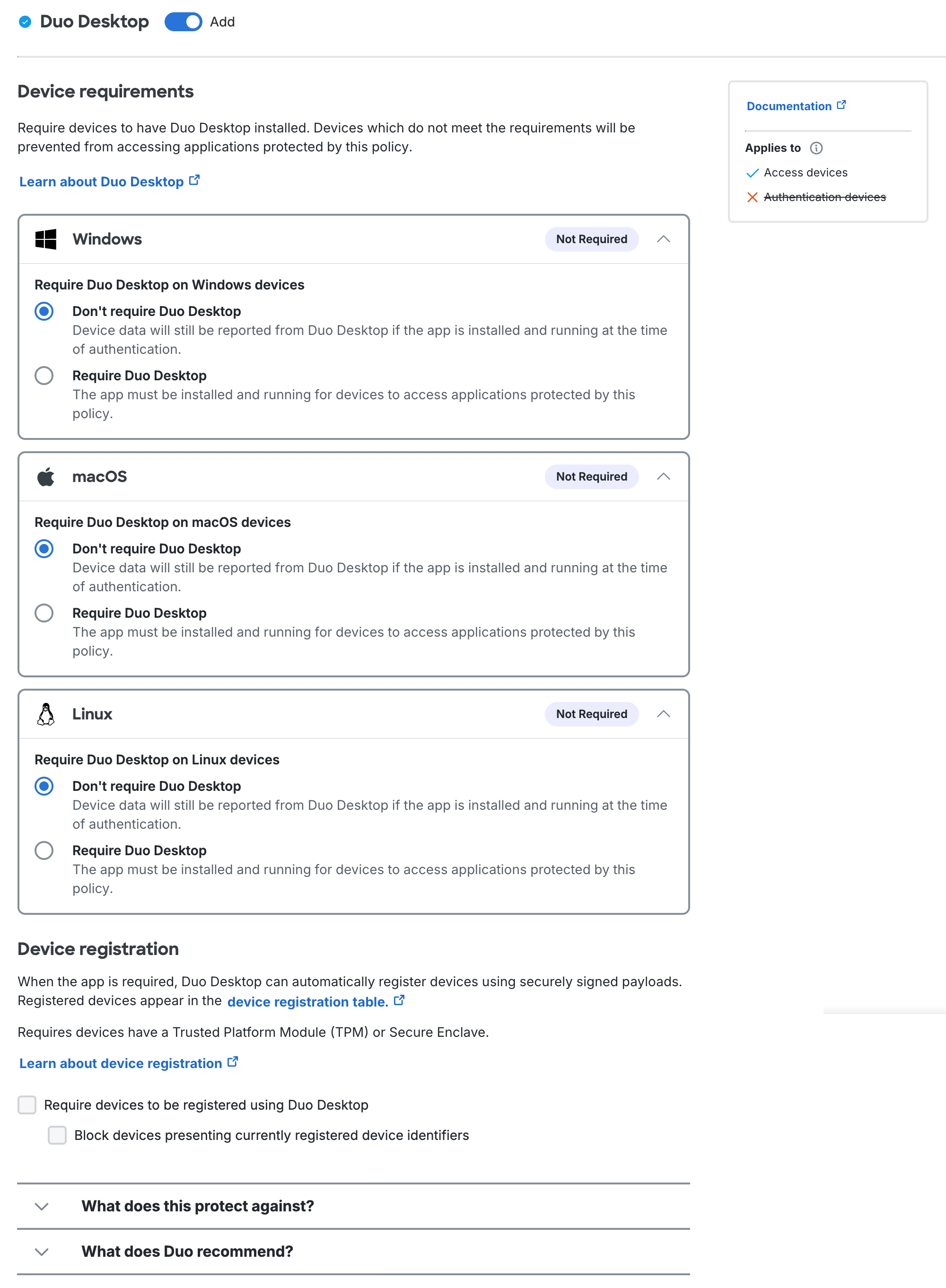
Within the Duo Desktop policy section you can configure whether to require Duo Desktop for application access, to require device registration using Duo Desktop from devices that meet hardware requirements, and which device health checks you want to enforce on your organization's endpoints.
Require Duo Desktop
Available in: Duo Essentials, Duo Advantage, and Duo Premier
These settings determine which operating systems require Duo Desktop installed for Duo-protected application access. For each operating system listed, make one of the following selections:
-
Don’t require the app or Don’t require Duo Desktop (Default for Duo Essentials in policy editor, and for all editions in policy maker):
With this option selected, the policy is not in effect and has no impact on end user access. End users are not prompted to install Duo Desktop when accessing a Duo-protected application. Data will be collected from Duo Desktop if present and running on the machine.
-
Check but don't require the app (Default for Duo Advantage and Duo Premier in policy editor, not present in policy maker):
With this option selected, end users are not prompted to install Duo Desktop when accessing a Duo-protected application. Data will be collected from Duo Desktop if present and running on the machine. Any applicable configured device health checks will be enforced if you have configured an external device data source, such as Chrome Enterprise browser. The policy options indicate which checks require Duo Desktop.
-
Require the app or Require Duo Desktop:
With this option selected, but none of the Device health checks options in the policy, having Duo Desktop installed and reporting information to Duo is required for access.
End users running devices that can install the app (Linux, macOS 11+, Windows 10 build 1803+, and Windows Server 2016+) see a link to download the app from the Duo authentication prompt when attempting to access a Duo-protected application associated with the policy if they do not already have the application installed. Devices that are capable of running the app but do not have it installed and running will be blocked from access.
The app will collect health information from the device, but Duo will not block the user from getting access if it does not pass the specific firewall, encryption, and password health checks. This means that the device will be able to access the application even if the device would not pass each health check.
Devices that cannot run the app, including older versions of Windows and macOS, mobile platforms, etc., will not be prompted to install the app and are effectively allowed to bypass the Duo Desktop policy.
Device Registration
Use the "Device registration" options in the Duo Desktop policy settings to register devices using signed payloads with Duo Desktop. Information collected during the registration process from a device with Trusted Platform Module (TPM) 2.0 or Secure Enclave is formatted and displayed with Endpoints information.
Device registration requires the following:
- Active two-factor authentication through browser-based applications using the Universal Prompt.
- Device registration does not occur if the user bypasses two-factor authentication for any reason, such as access from a network permitted by the authorized networks policy setting, if the user has an existing remembered devices session, or bypass status set at the individual or group level.
- Windows and Linux access devices with Trusted Platform Module (TPM) 2.0 or Mac access devices with Secure Enclave.
- Duo Desktop 6.0.0/6.0.0.0 or later installed on Windows and macOS clients and Duo Desktop 3.0.0 or later installed on Linux clients.
Chrome OS does not support Duo Desktop device registration.
Note: To enable device registration using Duo Desktop, first select Require the app in the Require Duo Desktop options for macOS, Windows, and/or Linux.
The primary device registration policy options are:
-
Require devices to be registered using Duo Desktop: Select this option to have payloads sent from Duo Desktop and evaluated against the policy controls to determine the device’s trust status. Devices that do not have TPM 2.0/Secure Enclave cannot complete registration and will be blocked.
The first time Duo Desktop sends a payload for a given device, it will be unsigned, and the device is sent through the automatic Duo Desktop registration.
-
Block devices presenting already registered device identifiers: Select this option to block devices that attempt to register but the device does not match the policy controls. For example, the device will be blocked:
-
If there is an existing Duo Desktop registration for the device.
-
If the payload is signed, and the stored signature does not match the one sent in the payload.
-
If the payload is signed, and the stored signature matches the one sent in the payload, but it is not the oldest known registration for that device.
When a device does not meet the security requirements of the device registration policies, the Admin Panel provides more information about why the user’s device was blocked.
To view and manage your registered devices, navigate to Devices → Duo Desktop Device Registration in the Admin Panel.
-
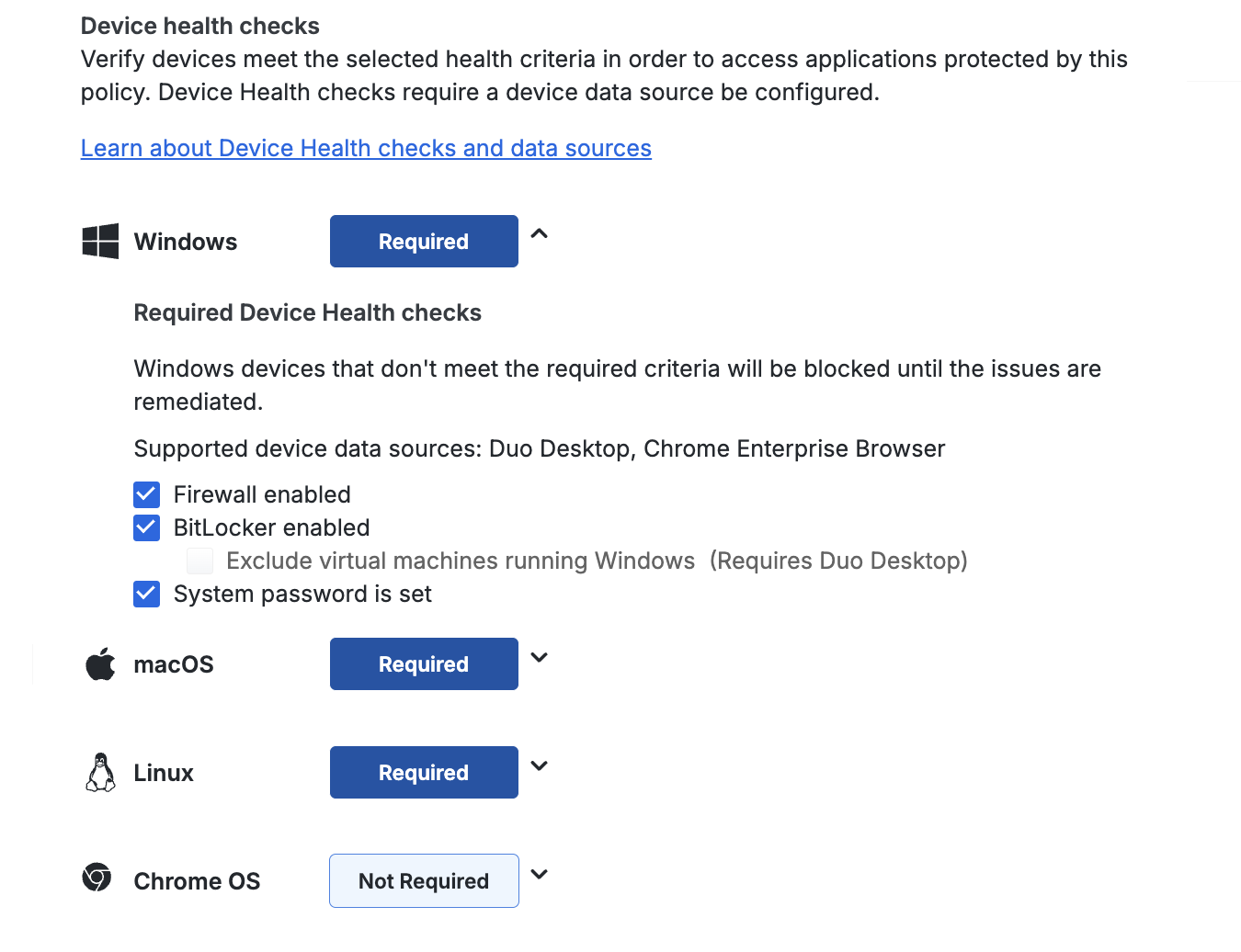
Device Health Checks
Available to Advantage and Premier plans. Device health checks can be performed with data collected by Duo Desktop or reported by an external device data source, such as Chrome Enterprise browser.
Configuring any of the device health check options that note they require Duo Desktop for an operating system needs the Require Duo Desktop option set to "Require the app" for the corresponding operating system.
With device health checks configured, users must either have Duo Desktop installed, running, and reporting information to Duo or be enrolled in the relevant external device data source, and the device must satisfy the specified health requirements for access.
End users running devices that can install the app (Linux, macOS 11+, Windows 10 build 1803+, and Windows Server 2016+) see a link to download the app from the Duo prompt when attempting to access a Duo-protected application associated with the policy if they do not already have the application installed. Devices that are capable of running the app but do not have it installed and running will be blocked from access if the policy requires the app.
Duo will allow or block access to the protected application based on the device health checks options selected.
The collapsed device health check view reflects the effective configuration:
- Not Required: No device health checks are configured for the operating system.
- Required: One or more device health checks are required for the operating system. Block access when devices don't comply with your selected options.
In the new policy editor the device health checks do not reflect whether the Duo Desktop app is required or not.
Devices that cannot run the app, including older versions of Windows and macOS, mobile platforms, etc., will not be prompted to install the app and are effectively allowed to bypass the Duo Desktop policy.
Note that the default "fail-open" Duo Desktop policy configuration allows you to enforce health checks for supported devices, while not blocking users who need to access an application using a non-supported device. You can optionally use Duo's Operating Systems policy to restrict other device types from accessing the application.
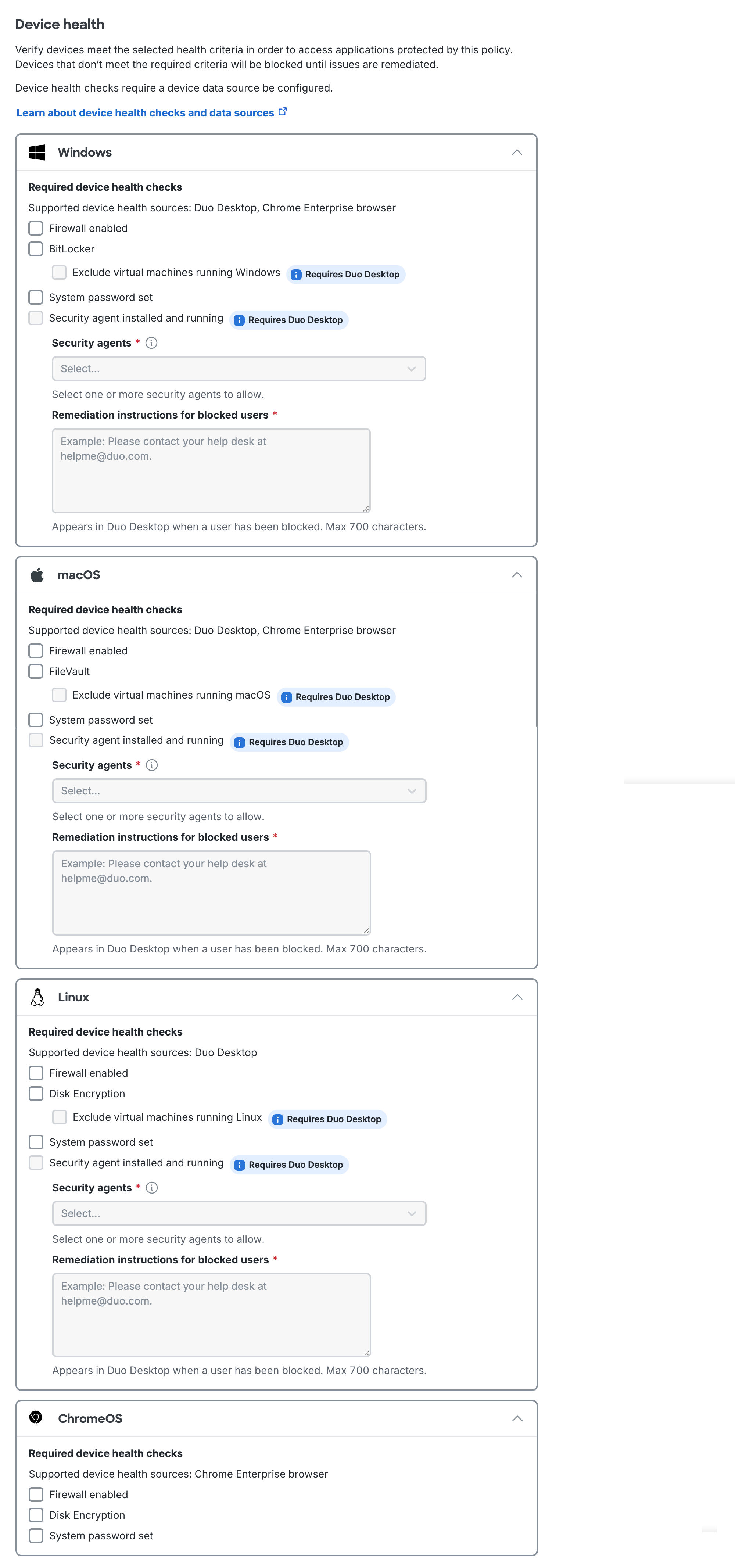
Device Health Check Options
Available in: Duo Advantage and Duo Premier
Block access to Duo-protected applications if devices don't comply with your selected device health check options. The checks can use any device data source, except as noted.
You can enforce the following health requirements for each OS:
- Firewall is disabled: Blocks access if the firewall is disabled on the endpoint
- Linux requires Duo Desktop. Chrome OS requires Chrome Enterprise browser.
- Disk encryption is disabled: Only for Linux endpoints. Blocks access if disk encryption is disabled on the Linux endpoint. Requires Duo Desktop.
- Exclude virtual machines running Linux: If Duo Desktop detects that it's running on a Linux virtual machine, disk encryption enforcement is skipped.
- FileVault is disabled: Only for macOS endpoints. Blocks access if FileVault is disabled on the macOS endpoint.
- Exclude virtual machines running macOS: If Duo Desktop detects that it's running on a macOS virtual machine, FileVault enforcement is skipped. Requires Duo Desktop.
- BitLocker is disabled: Only for Windows endpoints. Blocks access if BitLocker is disabled on the Windows endpoint.
- Exclude virtual machines running Windows: If Duo Desktop detects that it's running on a Windows virtual machine, BitLocker enforcement is skipped. Requires Duo Desktop.
- System password is not set: Blocks access if the system password is not set on the endpoint.
- Linux requires Duo Desktop. Chrome OS requires Chrome Enterprise browser.
- An endpoint security agent is not running: Only available for Duo Premier plan customers. See Security Agent Verification to learn more.
Duo Desktop & device health policy options in Duo Premier
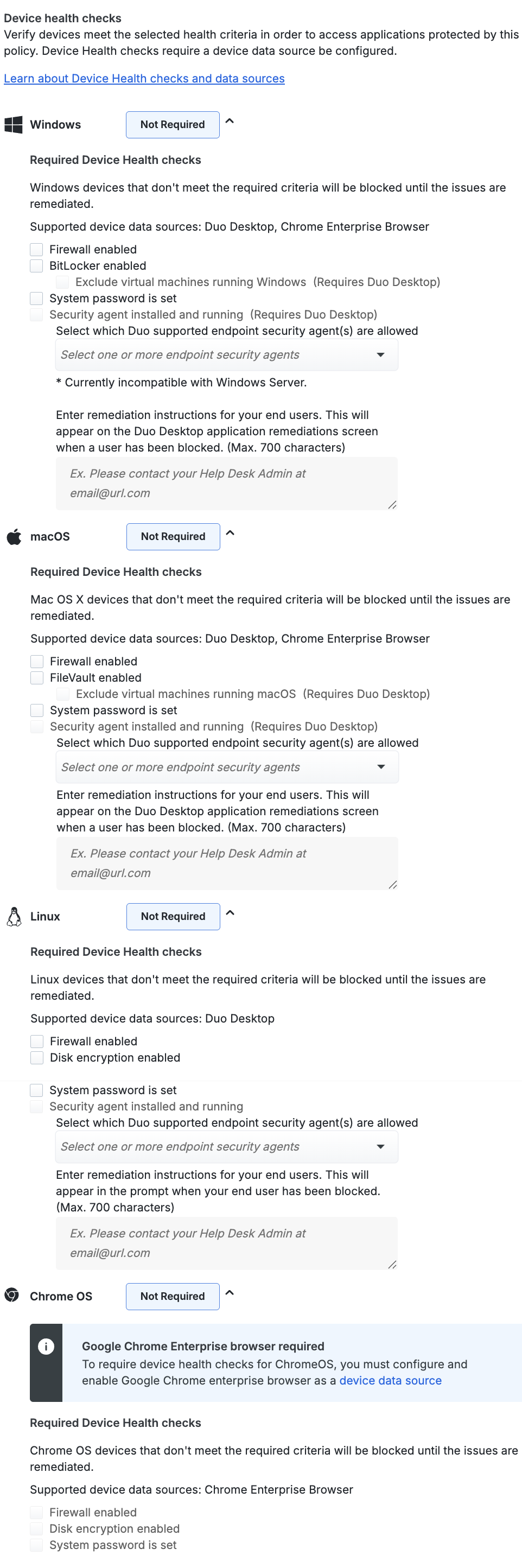
Security Agent Verification
Duo Premier plan customers can use Duo Desktop's antivirus/anti-malware agent device health checks to verify that endpoints have one of these supported security solutions listed below in place before accessing an application:
BitDefender Endpoint Security, Cisco Secure Endpoint (previously known as Cisco AMP for Endpoints), CrowdStrike Falcon Sensor, CylancePROTECT, Forcepoint One (only shown in the list for Windows and macOS), Microsoft Defender for Endpoint (only shown in the list for macOS), Trellix Endpoint Security (formerly known as McAfee Endpoint Security), Palo Alto Cortex XDR, Qualys Cloud Agent, SentinelOne, Sophos AV (only shown in the list for Windows and macOS), Sophos Home (only shown in the list for Windows and macOS), Symantec Endpoint Protection, Trend Micro Apex One (only shown in the list for Windows and macOS), VMWare Carbon Black Cloud, Windows Defender (only shown in the list for Windows)
All security agent checks for Windows, macOS, and Linux require Duo Desktop, with the Require the app option selected to activate the Security agent installed and running control.
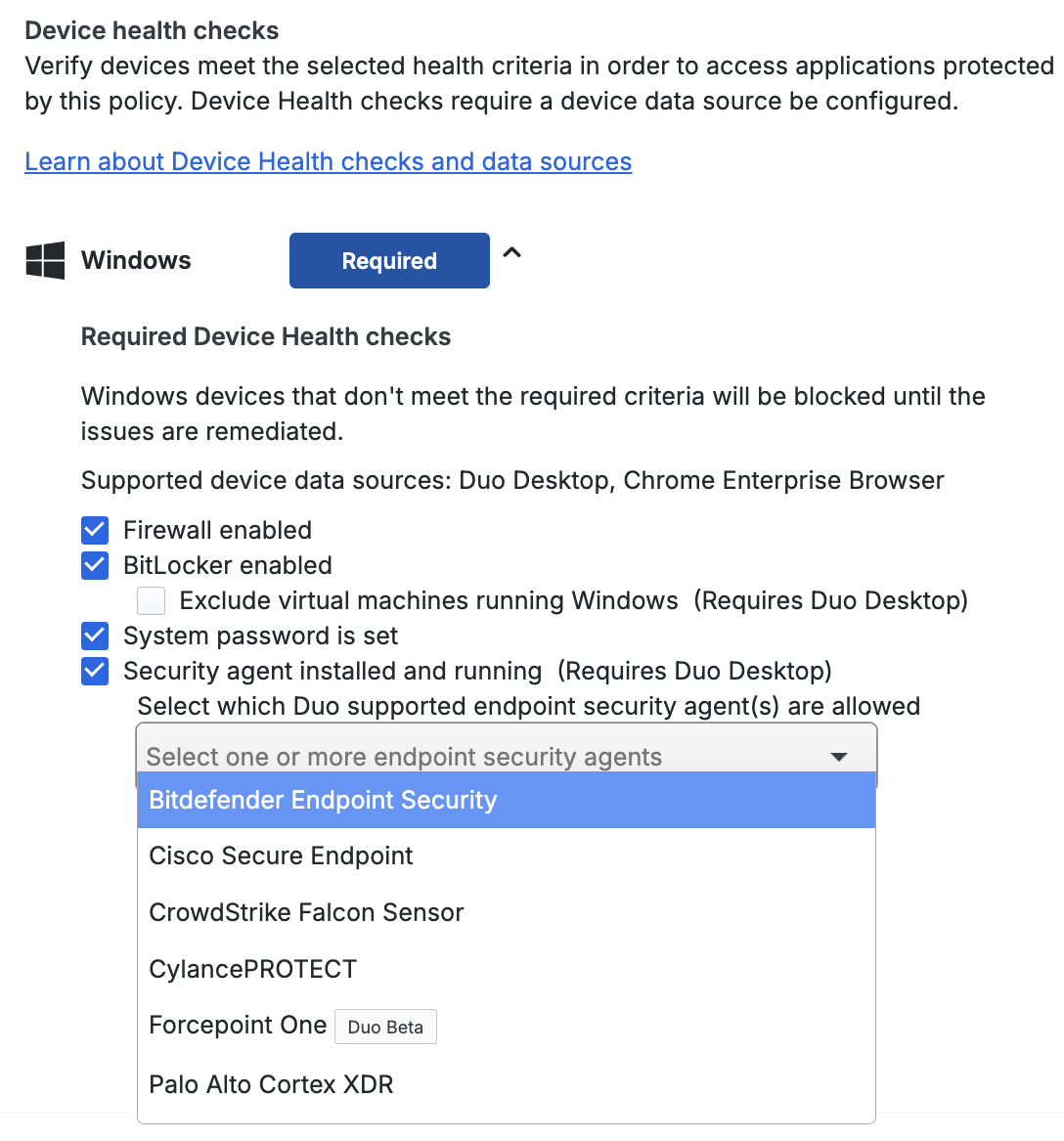
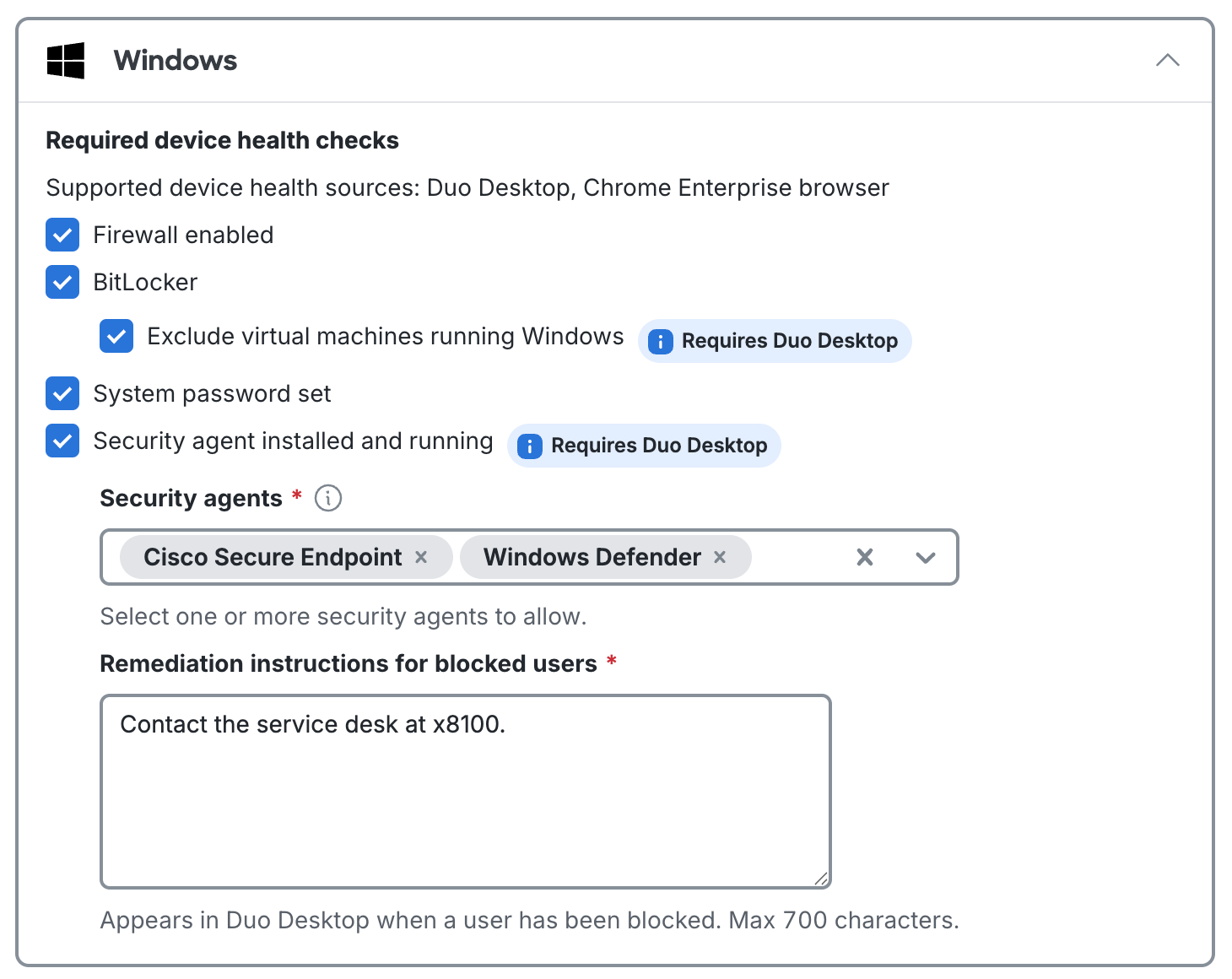
You can enforce the following health requirements for each OS:
-
Firewall enabled: Blocks access if the firewall is disabled on the endpoint
- Linux requires Duo Desktop. Chrome OS requires Chrome Enterprise browser.
-
BitLocker: Only for Windows endpoints. Blocks access if BitLocker is disabled on the Windows endpoint.
- Exclude virtual machines running Windows: If Duo Desktop detects that it's running on a Windows virtual machine, BitLocker enforcement is skipped. Requires Duo Desktop.
-
FileVault: Only for macOS endpoints. Blocks access if FileVault is disabled on the macOS endpoint.
- Exclude virtual machines running macOS: If Duo Desktop detects that it's running on a macOS virtual machine, FileVault enforcement is skipped. Requires Duo Desktop.
-
Disk encryption: Only for Linux endpoints. Blocks access if disk encryption is disabled on the Linux endpoint. Requires Duo Desktop.
- Exclude virtual machines running Linux: If Duo Desktop detects that it's running on a Linux virtual machine, disk encryption enforcement is skipped.
-
System password set: Blocks access if the system password is not set on the endpoint.
- Linux requires Duo Desktop. Chrome OS requires Chrome Enterprise browser.
-
Security agent installed and running: Only available for Duo Premier plan customers. See Security Agent Verification to learn more.
Duo Desktop & device health policy options in Duo Premier
Security Agent Verification
Duo Premier plan customers can use Duo Desktop's antivirus/anti-malware agent device health checks to verify that endpoints have one of these supported security solutions listed below in place before accessing an application:
BitDefender Endpoint Security, Cisco Secure Endpoint (previously known as Cisco AMP for Endpoints), CrowdStrike Falcon Sensor, CylancePROTECT, Forcepoint One (only shown in the list for Windows and macOS), Microsoft Defender for Endpoint (only shown in the list for macOS), Trellix Endpoint Security (formerly known as McAfee Endpoint Security), Palo Alto Cortex XDR, Qualys Cloud Agent, SentinelOne, Sophos AV (only shown in the list for Windows and macOS), Sophos Home (only shown in the list for Windows and macOS), Symantec Endpoint Protection, Trend Micro Apex One (only shown in the list for Windows and macOS), VMWare Carbon Black Cloud, Windows Defender (only shown in the list for Windows)
All security agent checks for Windows, macOS, and Linux require Duo Desktop, with the Require Duo Desktop option selected to activate the Security agent installed and running control.
Security agent verification is unavailable for Chrome OS.
See our full Duo Desktop guide for more information and step-by-step deployment instructions.
If you configure operating system version policy settings for Windows and macOS, consider deploying Duo Desktop to clients or enabling Duo Desktop installation during Duo enrollment to enhance OS version detection for those systems, even if you don't use the Duo Desktop policy options to verify security posture during authentication. Reliable detection and policy enforcement against Windows 11 requires Duo Desktop.
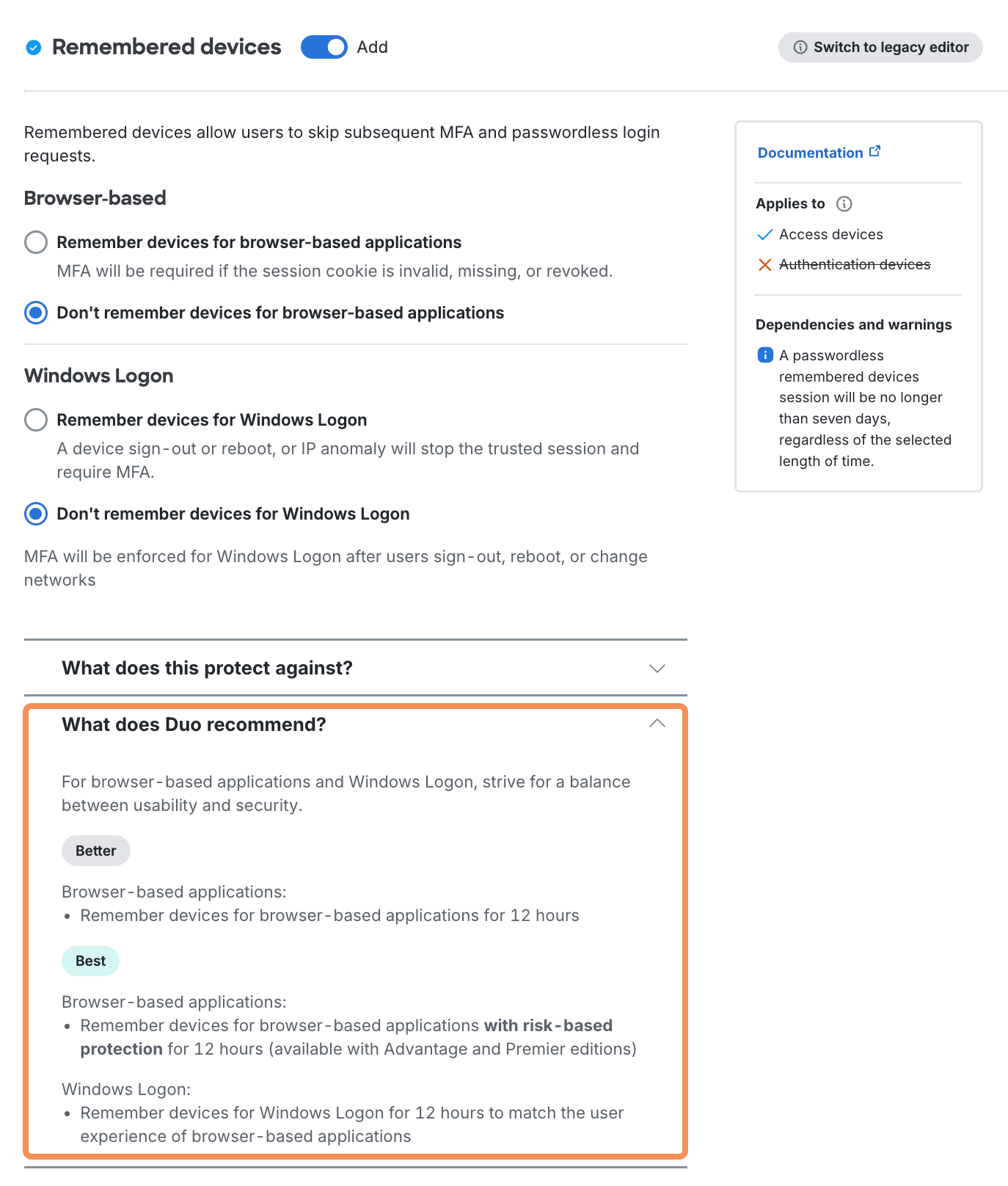
Remembered Devices
Available in: Duo Essentials, Duo Advantage, and Duo Premier
- Remembered devices is currently not supported for Universal Prompt with Trusted Endpoints when accessing protected applications from a mobile device.
- The maximum duration for a Passwordless remembered devices session is seven days (168 hours), regardless of the configuration in the Duo Admin Panel.
- Endpoint checks for trust status, security posture, etc. still occur during a remembered device login session.
- Duo Desktop authentication cannot be used as a factor for remembered devices. Even if a remembered devices policy is applied, Duo Desktop authentication will not start a remembered devices session, and users will need to authenticate with Duo Desktop each time.
Duo's remembered devices feature is similar to the "remember my computer" or "keep me logged in" options familiar to users from primary authentication to websites and applications.
With the remembered devices feature enabled, users of the Duo traditional prompt and Duo Authentication for Windows Logon see a "Remember me" option, and users of Duo Universal Prompt see "Is this your device?". When users select this option during Duo authentication, they will not be challenged for Duo authentication when they log in again from that device for a set period of time.
Disabling a user invalidates existing remembered device sessions. Disabling the remembered devices policy setting and then enabling it again will not invalidate a user's remembered device sessions.
You can enable remembered devices separately for web applications or Duo Authentication for Windows Logon, or for both in a single policy with distinct session lengths. If you plan to enable Duo Passwordless be aware that the remembered devices policy options apply to both passwordless and password plus 2FA application logins.
Duo Essentials Policy Options
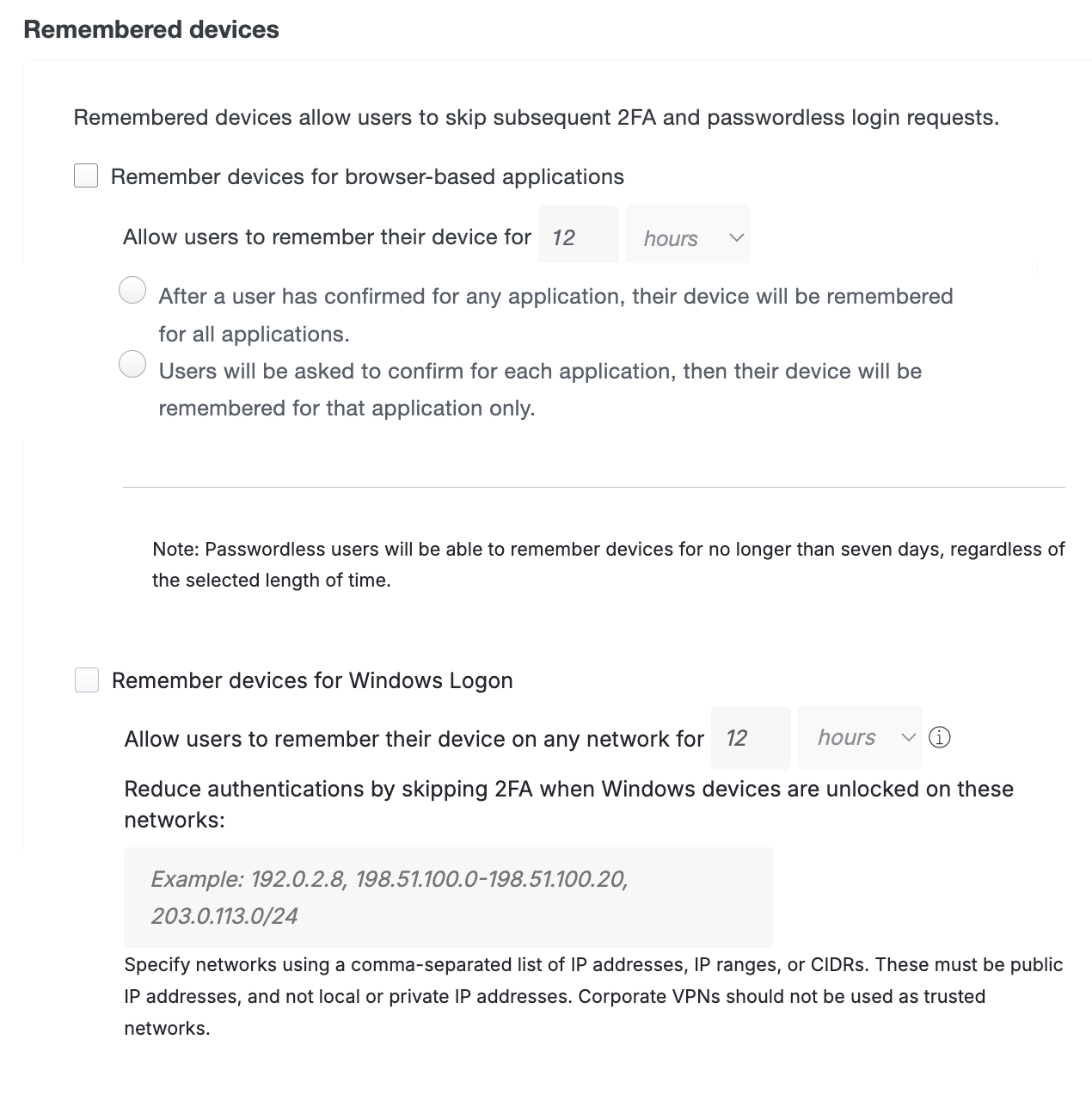
The Remember devices for browser-based applications setting works with applications that show the Duo Prompt in a browser.
-
Allow users to remember their device for nn: This enables traditional remembered devices. Default setting: off. Enter the desired number of days or hours — up to 365 days — for the setting and then choose one of these options:
-
After a user has confirmed for any application, their device will be remembered for all applications.: When a user checks the "Remember me" box on the traditional Duo Prompt or opts to remember this browser on your device on the Universal Prompt, it creates a trusted session for that user, client browser, and endpoint after successful Duo authentication. Duo won't prompt for authentication again for the duration specified if a user logs into that or any other web applications assigned a remembered device policy with this same option selected when the trusted session is still valid and the authenticator used to create the session is also permitted for the additional application.
This is especially helpful for users of Duo Single Sign-On. In this scenario, you would create a policy with remembered devices for all applications and then apply that same policy to each Duo-protected SAML application for which you don't want additional 2FA prompts. When a user logs into one of the protected SAML apps with that policy, like Google Workspace, and chooses to remember that device, the user isn't prompted for Duo access again when accessing other SAML apps via Duo Single Sign-On which also allow remembered devices for all applications in their effective policy.
In practice, we recommend configuring your remembered devices policy for browser-based applications at the global policy level, and then creating application and group level policies without remembered devices to override an existing trusted login session for those sensitive or restricted-access web applications where you want your users to perform Duo authentication again.
If a user has started a remembered device session for any browser-based application and you delete or remove any device from that user from the Admin Panel, the session will be revoked and the user will have to perform two-factor authentication again the next time they try to log into a browser-based application with that remembered devices policy.
-
Users will be asked to confirm for each application, then their device will be remembered for that application only.: When a user opts in to remembering their browser in an application, then it only applies to that individual Duo-protected service or application. Subsequent access of the same application will not require 2FA after a user checks the "Remember me" box on the traditional Duo Prompt or opts to remember this browser on your device on the Universal Prompt, but if a user accesses a different application protected by Duo then the user will have to approve a Duo login request again for those other applications.
-
The Remember devices for Windows Logon setting works with Duo Authentication for Windows Logon version 4.2.0 and later. When enabling remembered devices for local Windows logons, enter the desired number of days or hours — up to 365 days — for the Allow users to remember their device for setting. Default setting: off.
Client network changes, such as moving between WiFi networks, invalidate a Windows logon remembered devices session. You can allow persistent remembered devices sessions across trusted networks by entering network IPs, IP ranges, or CIDRs under Reduce authentications by skipping 2FA when Windows devices are unlocked on these networks. Duo Authentication for Windows Logon 5.2.0 or later will not invalidate a remembered devices session as long as the client is authenticating from a network you specify here.
-
This policy setting only affects "Microsoft RDP" Duo applications. If you configure this setting in your global policy, or assign it to any application types other than Microsoft RDP, it has no effect on other application types and users will not see the remembered device option during Duo authentication from those other applications.
-
Additionally, remembered devices settings do not apply to remote access Windows logins over RDP; the "Remember me" option shown for local console logins won't be present at RDP login. If you want to bypass Duo authentication for RDP connections, consider applying an Authorized Networks policy to the application.
-
When a user logs into Windows at the local workstation or server console and checks the "Remember me" box during Duo authentication, it creates a trusted session for that user on that host with that IP address after successful Duo authentication. Duo won't prompt for authentication again when the user locks and unlocks the workstation, or for credentialed UAC elevation by that user, for the duration specified in the policy setting.
-
Duo Authentication for Windows Logon invalidates the local trusted session on that Windows system before it expires if the user logs out of Windows or reboots, if the user cancels a remembered authentication in process, if the user authenticates with offline access for Windows logon, or if the network state of the system changed from the network state at session creation and the new network isn't allowed to continue the remembered device session.
-
Administrators may revoke use of trusted Duo sessions by disabling or unassigning a remembered devices policy for Windows Logon from a Microsoft RDP application, or by deleting the registry entry for the user session from the Windows client. Learn more about this in the Windows Logon FAQ.
Learn more about remembered devices for Windows Logon in the application documentation.
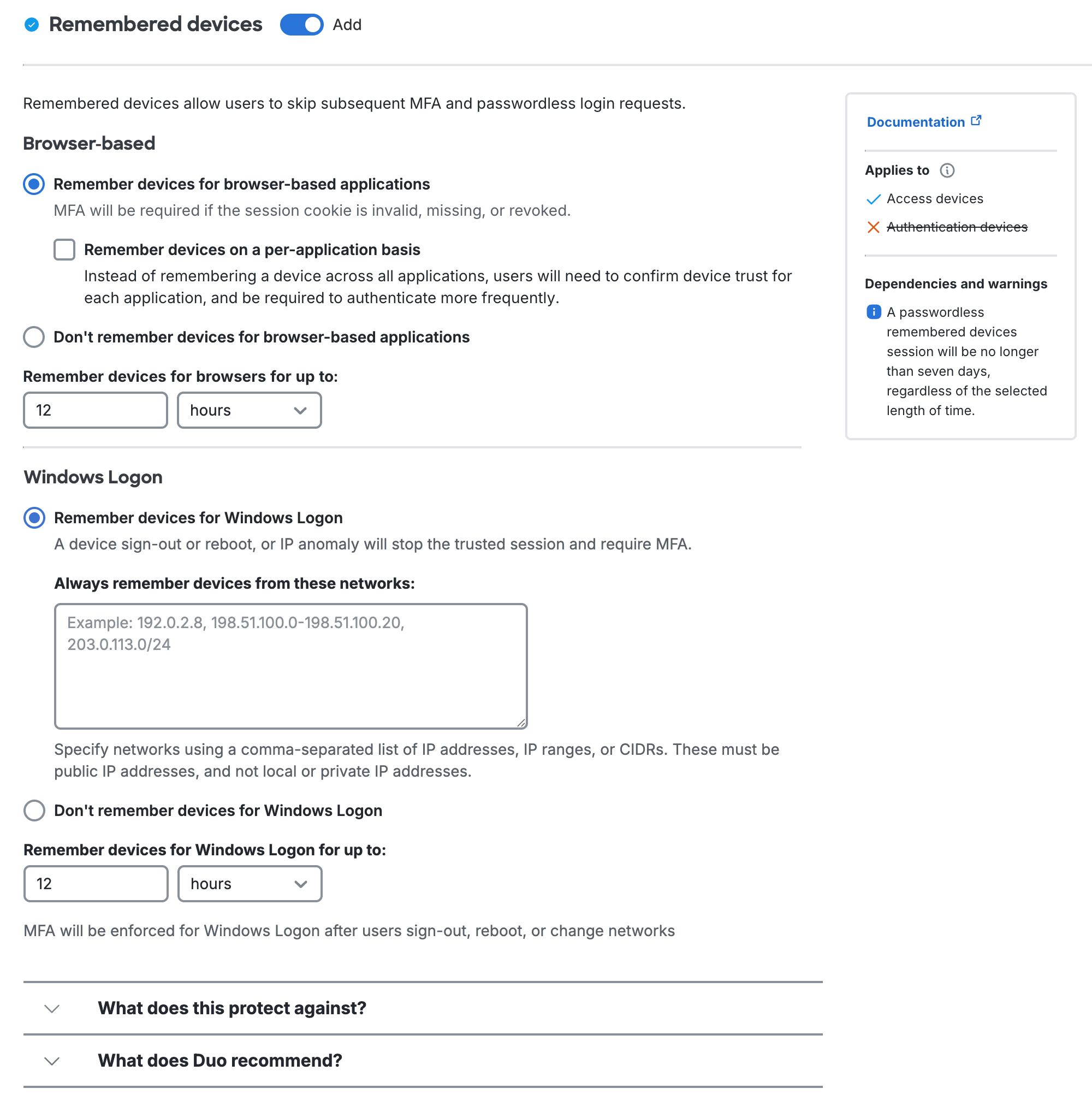
Browser-based
The "Browser-based" settings work with applications that show the Duo Prompt in a browser. In practice, we recommend configuring your remembered devices policy for browser-based applications at the global policy level, and then creating application and group level policies without remembered devices to override an existing trusted login session for those sensitive or restricted-access web applications where you want your users to perform Duo authentication again.
If a user has started a remembered device session for any browser-based application and you delete or remove any device from that user from the Admin Panel, the session will be revoked and the user will have to perform two-factor authentication again the next time they try to log into a browser-based application with that remembered devices policy.
-
Remember devices for browser-based applications: When a user checks the "Remember me" box on the traditional Duo Prompt or opts to remember this browser on your device on the Universal Prompt, it creates a trusted session for that user, client browser, and endpoint after successful Duo authentication. Duo won't prompt for authentication again for the duration specified if a user logs into that or any other web applications assigned a remembered device policy with this same option selected when the trusted session is still valid and the authenticator used to create the session is also permitted for the additional application.
- Remember devices on a per-application basis: When a user opts in to remembering their browser in an application, then it only applies to that individual Duo-protected service or application. Subsequent access of the same application will not require 2FA after a user checks the "Remember me" box on the traditional Duo Prompt or opts to remember this browser on your device on the Universal Prompt, but if a user accesses a different application protected by Duo then the user will have to approve a Duo login request again for those other applications.
-
Don't remember devices for browser-based applications: Users must complete MFA or passwordless for every login.
-
Remember devices for browsers for up to:: Enter the desired number of days or hours — up to 365 days — for the maximum remembered devices session with "Remember devices for browser-based application" selected.
Windows Logon
The "Windows Logon" settings work with Duo Authentication for Windows Logon version 4.2.0 and later. This policy setting only affects "Microsoft RDP" Duo applications. If you configure this setting in your global policy, or assign it to any application types other than "Microsoft RDP", it has no effect on those other application types and users will not see the remembered device option during Duo authentication from those other applications.
Additionally, remembered devices settings do not apply to remote access Windows logins over RDP; the "Remember me" option shown for local console logins won't be present at RDP login. If you want to bypass Duo authentication for RDP connections, consider applying an Authorized Networks policy to the application.
-
Remember devices for Windows Logon: When a user logs into Windows at the local workstation or server console and checks the "Remember me" box during Duo authentication, it creates a trusted session for that user on that host with that IP address after successful Duo authentication. Duo won't prompt for authentication again when the user locks and unlocks the workstation, or for credentialed UAC elevation by that user, for the duration specified in the policy setting.
-
Don't remember devices for Windows Logon: Users must complete MFA or passwordless for every login.
-
Remember devices for Windows Logon for up to:: Enter the desired number of days or hours — up to 365 days — for the maximum remembered devices session with "Remember devices for Windows Logon" selected.
Client network changes, such as moving between WiFi networks, invalidate a Windows logon remembered devices session. You can allow persistent remembered devices sessions across trusted networks by entering network IPs, IP ranges, or CIDRs under Always remember devices from these networks. Duo Authentication for Windows Logon 5.2.0 or later will not invalidate a remembered devices session as long as the client is authenticating from a network you specify here.
Duo Authentication for Windows Logon invalidates the local trusted session on that Windows system before it expires if the user logs out of Windows or reboots, if the user cancels a remembered authentication in process, if the user authenticates with offline access for Windows logon, or if the network state of the system changed from the network state at session creation.
Administrators may revoke use of trusted Duo sessions by disabling or unassigning a remembered devices policy for Windows Logon from a Microsoft RDP application, or by deleting the registry entry for the user session from the Windows client. Learn more about this in the Windows Logon FAQ.
Learn more about remembered devices for Windows Logon in the application documentation.
Duo Advantage and Premier Policy Options
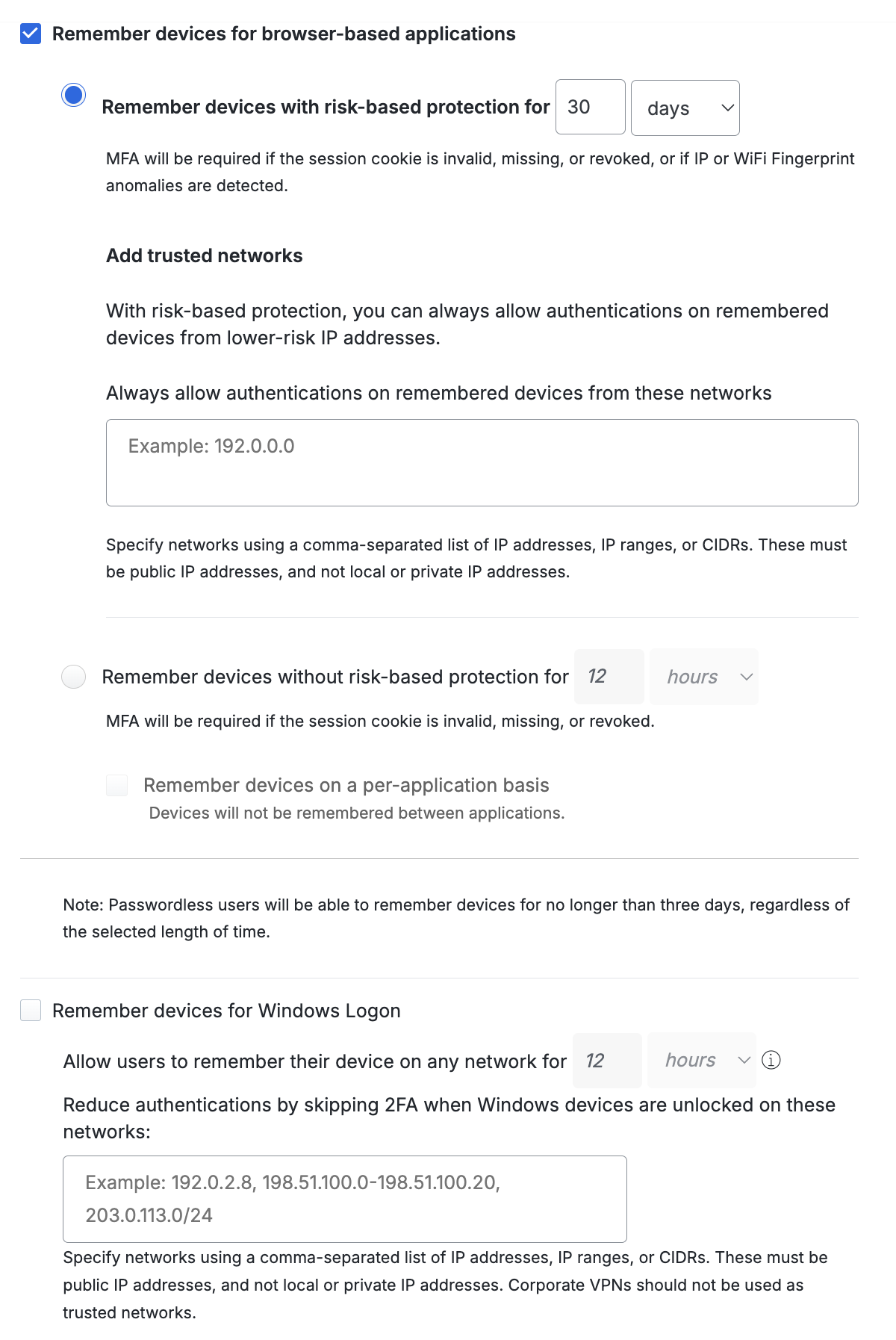
The Remember devices for browser-based applications setting works with applications that show the Duo Prompt in a browser. Choose between Risk-Based Remembered Devices or traditional remembered devices, where the user opts-in during authentication. Risk-Based Remembered Devices is enabled by default for Duo Advantage and Duo Premier customers.
-
Remember devices with risk-based protection for _nn_days: This setting applies Risk-Based Remembered Devices, which analyzes user authentications for IP and device patterns and either suppresses additional two-factor authentication prompts after the initial login for the duration defined (default: 30 days), or prompts for two-factor authentication before the defined duration expires if anomalous access is detected. Default setting: enabled.
See our full Risk-Based Authentication documentation for more information and step-by-step deployment instructions.
-
You can define low-risk network IPs and ranges under Add trusted networks.
-
Remember devices without risk-based protection for _nn_hours: This enables traditional remembered devices. Default setting: off. Enter the desired number of days or hours — up to 365 days — for the setting and then choose:
- Remember devices on a per-application basis When a user opts in to remembering their browser in an application, then it only applies to that individual Duo-protected service or application. Subsequent access of the same application will not require 2FA after a user checks the "Remember me" box on the traditional Duo Prompt or opts to remember this browser on your device on the Universal Prompt, but if a user accesses a different application protected by Duo then the user will have to approve a Duo login request again for those other applications.
The Remember devices for Windows Logon setting works with Duo Authentication for Windows Logon version 4.2.0 and later. When enabling remembered devices for local Windows logons, enter the desired number of days or hours — up to 365 days — for the Allow users to remember their device for setting. Default setting: off.
Client network changes, such as moving between WiFi networks, invalidate a Windows logon remembered devices session. You can allow persistent remembered devices sessions across trusted networks by entering network IPs, IP ranges, or CIDRs under Reduce authentications by skipping 2FA when Windows devices are unlocked on these networks. Duo Authentication for Windows Logon 5.2.0 or later will not invalidate a remembered devices session as long as the client is authenticating from a network you specify here.
-
This policy setting only affects "Microsoft RDP" Duo applications. If you configure this setting in your global policy, or assign it to any application types other than Microsoft RDP, it has no effect on other application types and users will not see the remembered device option during Duo authentication from those other applications.
-
Additionally, remembered devices settings do not apply to remote access Windows logins over RDP; the "Remember me" option shown for local console logins won't be present at RDP login. If you want to bypass Duo authentication for RDP connections, consider applying an Authorized Networks policy to the application.
-
When a user logs into Windows at the local workstation or server console and checks the "Remember me" box during Duo authentication, it creates a trusted session for that user on that host with that IP address after successful Duo authentication. Duo won't prompt for authentication again when the user locks and unlocks the workstation, or for credentialed UAC elevation by that user, for the duration specified in the policy setting.
-
Duo Authentication for Windows Logon invalidates the local trusted session on that Windows system before it expires if the user logs out of Windows or reboots, if the user cancels a remembered authentication in process, if the user authenticates with offline access for Windows logon, or if the network state of the system changed from the network state at session creation.
-
Administrators may revoke use of trusted Duo sessions by disabling or unassigning a remembered devices policy for Windows Logon from a Microsoft RDP application, or by deleting the registry entry for the user session from the Windows client. Learn more about this in the Windows Logon FAQ.
Learn more about remembered devices for Windows Logon in the application documentation.
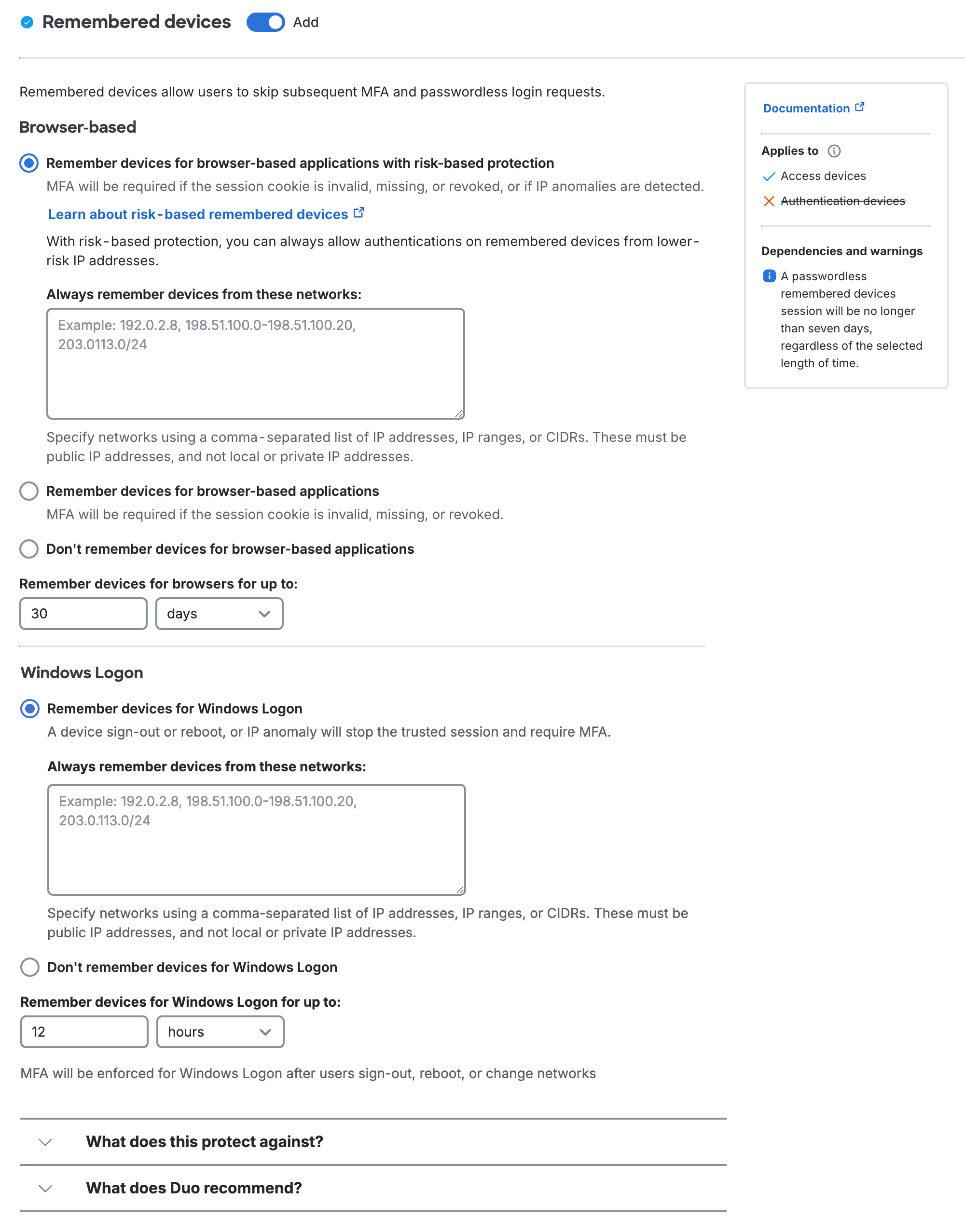
Browser-based
The "Browser-based" settings work with applications that show the Duo Prompt in a browser. In practice, we recommend configuring your remembered devices policy for browser-based applications at the global policy level, and then creating application and group level policies without remembered devices to override an existing trusted login session for those sensitive or restricted-access web applications where you want your users to perform Duo authentication again.
If a user has started a remembered device session for any browser-based application and you delete or remove any device from that user from the Admin Panel, the session will be revoked and the user will have to perform two-factor authentication again the next time they try to log into a browser-based application with that remembered devices policy.
-
Remember devices for browser-based applications with risk-based protection: This setting applies Risk-Based Remembered Devices, which analyzes user authentications for IP and device patterns and either suppresses additional two-factor authentication prompts after the initial login for the duration defined (default: 30 days), or prompts for two-factor authentication before the defined duration expires if anomalous access is detected. Default setting: enabled.
See our full Risk-Based Authentication documentation for more information and step-by-step deployment instructions.
-
You can define low-risk network IPs and ranges under Add trusted networks.
-
Remember devices without risk-based protection for _nn_hours: This enables traditional remembered devices. Default setting: off. Enter the desired number of days or hours — up to 365 days — for the setting and then choose:
- Remember devices on a per-application basis When a user opts in to remembering their browser in an application, then it only applies to that individual Duo-protected service or application. Subsequent access of the same application will not require 2FA after a user checks the "Remember me" box on the traditional Duo Prompt or opts to remember this browser on your device on the Universal Prompt, but if a user accesses a different application protected by Duo then the user will have to approve a Duo login request again for those other applications.
-
Don't remember devices for browser-based applications: Users must complete MFA or passwordless for every login.
-
Remember devices for browsers for up to:: Enter the desired number of days or hours — up to 365 days — for the maximum remembered devices session with "Remember devices for browser-based application" selected.
Windows Logon
The "Windows Logon" settings work with Duo Authentication for Windows Logon version 4.2.0 and later. This policy setting only affects "Microsoft RDP" Duo applications. If you configure this setting in your global policy, or assign it to any application types other than Microsoft RDP, it has no effect on other application types and users will not see the remembered device option during Duo authentication from those other applications.
Additionally, remembered devices settings do not apply to remote access Windows logins over RDP; the "Remember me" option shown for local console logins won't be present at RDP login. If you want to bypass Duo authentication for RDP connections, consider applying an Authorized Networks policy to the application.
-
Remember devices for Windows Logon: When a user logs into Windows at the local workstation or server console and checks the "Remember me" box during Duo authentication, it creates a trusted session for that user on that host with that IP address after successful Duo authentication. Duo won't prompt for authentication again when the user locks and unlocks the workstation, or for credentialed UAC elevation by that user, for the duration specified in the policy setting.
-
Don't remember devices for Windows Logon: Users must complete MFA or passwordless for every login.
-
Remember devices for Windows Logon for up to:: Enter the desired number of days or hours — up to 365 days — for the maximum remembered devices session with "Remember devices for Windows Logon" selected.
Client network changes, such as moving between WiFi networks, invalidate a Windows logon remembered devices session. You can allow persistent remembered devices sessions across trusted networks by entering network IPs, IP ranges, or CIDRs under Always remember devices from these networks. Duo Authentication for Windows Logon 5.2.0 or later will not invalidate a remembered devices session as long as the client is authenticating from a network you specify here.
Duo Authentication for Windows Logon invalidates the local trusted session on that Windows system before it expires if the user logs out of Windows or reboots, if the user cancels a remembered authentication in process, if the user authenticates with offline access for Windows logon, or if the network state of the system changed from the network state at session creation.
Administrators may revoke use of trusted Duo sessions by disabling or unassigning a remembered devices policy for Windows Logon from a Microsoft RDP application, or by deleting the registry entry for the user session from the Windows client. Learn more about this in the Windows Logon FAQ.
Learn more about remembered devices for Windows Logon in the application documentation.
Operating Systems
Available in: Duo Advantage and Duo Premier
Operating systems policies apply to:
-
Which operating systems and versions are allowed to access your applications when protected by Duo's browser-based authentication prompt, while also encouraging users running older operating systems to update to the latest version.
-
Which mobile OS platforms and versions may be used with Duo Mobile to approve two-factor authentication requests or generate passcodes for authentication. When you block a given mobile operating system, then that restriction applies to use of Duo Mobile to authenticate to all Duo-protected applications, not just those that use Duo's browser prompt, and prevents enrollment of Duo Mobile for any device with that OS. See Mobile Platforms to learn more about operating system policy for mobile platforms.
You may block access from all versions of any of the OS platforms listed in the policy editor: Android, BlackBerry, Chrome OS, iOS, Linux, macOS, Windows, and Windows Phone.
The default settings do not allow access, authentication, or enrollment from browsers on BlackBerry devices and Windows Phones. All other Duo-supported operating systems and mobile platforms are allowed with no warnings.
Duo offers more granular options for the Android, iOS, Chrome OS, macOS, and Windows operating systems, like warning on or blocking access below a certain version, warning the user that they need to update to an approved version instead of blocking access outright, and setting a grace period for warning or blocking a user after a version becomes outdated.
- Duo only considers numbered operating system releases when making policy evaluations. Security updates that do not increment the OS version cannot be detected or blocked by Duo's operating systems policy.
- Duo generally defines the "latest" version as the most recently released available OS version or build, and defines "up-to-date" and "supported" as the most recent patch release for a given OS version or build.
- "End-of-life" indicates that the software vendor no longer releases security updates for that version.
Scroll down in the policy editor to see all OS options.
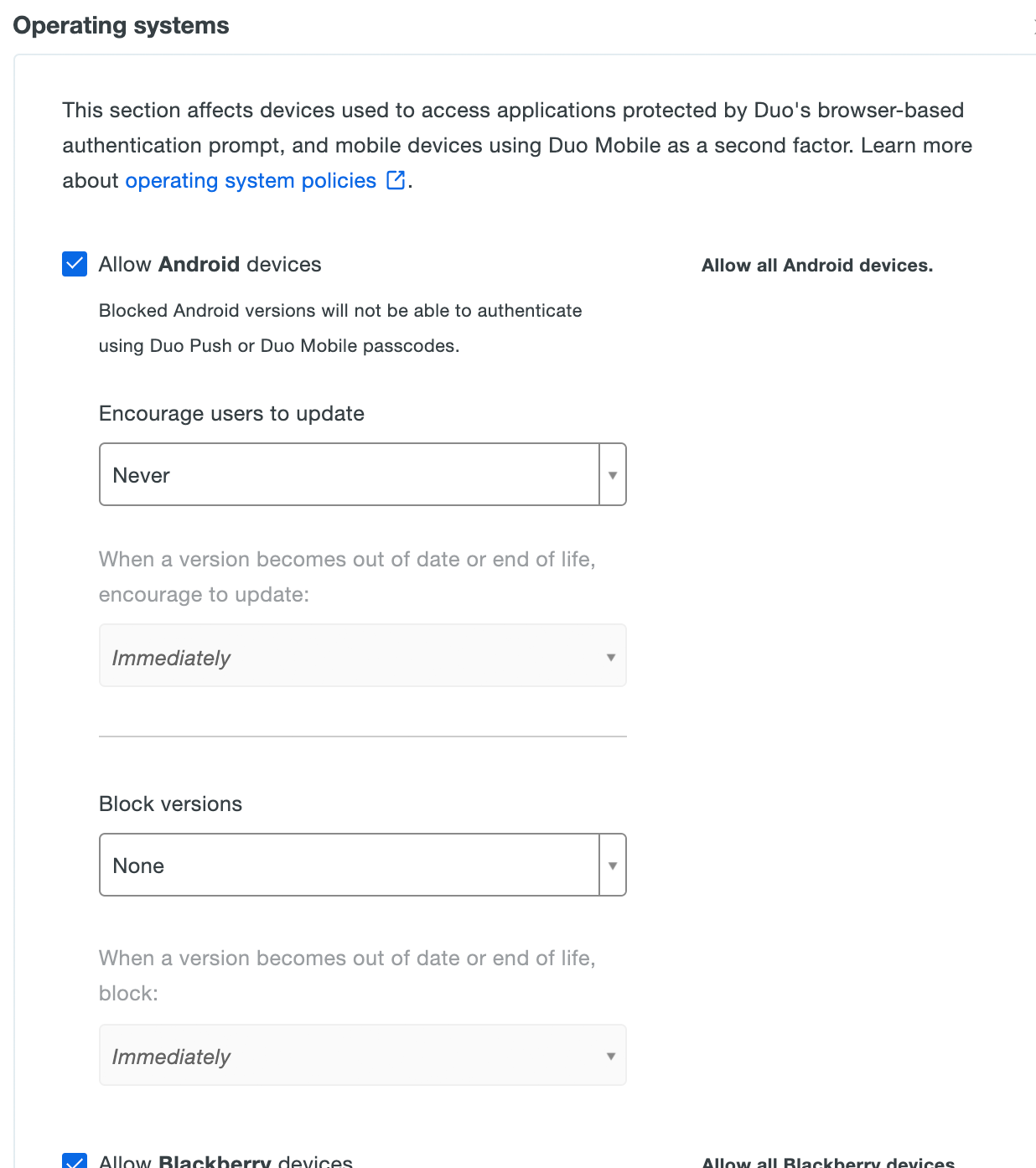
Expand the sections in the policy editor to see all OS options. All major operating system families are allowed by default, along with Linux and unrecognized operating systems (under "Other Devices"), with no out-of-date warnings or blocked versions.
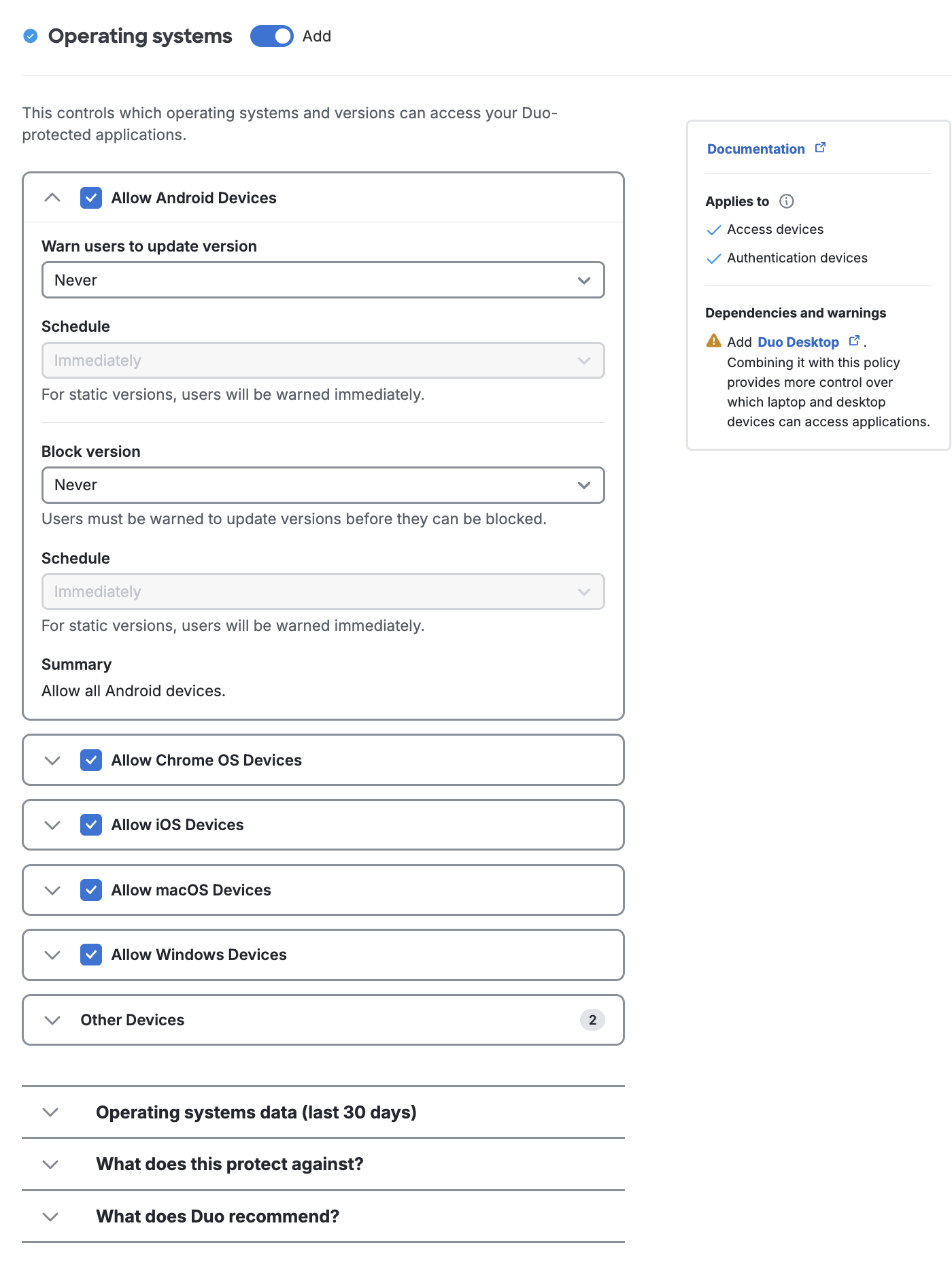
Check the OS Specific Version Data section of this document for additional details about how Duo determines the "up-to-date" or "end-of-life" status for a given operating system.
Encourage Users to Update While Still Permitting Access
Enable the Encourage users to update option by picking your minimum allowable OS version from the drop-down selector. This affects access to applications from computers and mobile devices by showing a message in the online Duo prompt recommending they update their operating system. You can choose to select a specific version, or let Duo determine the most recent available up-to-date or end-of-life version.
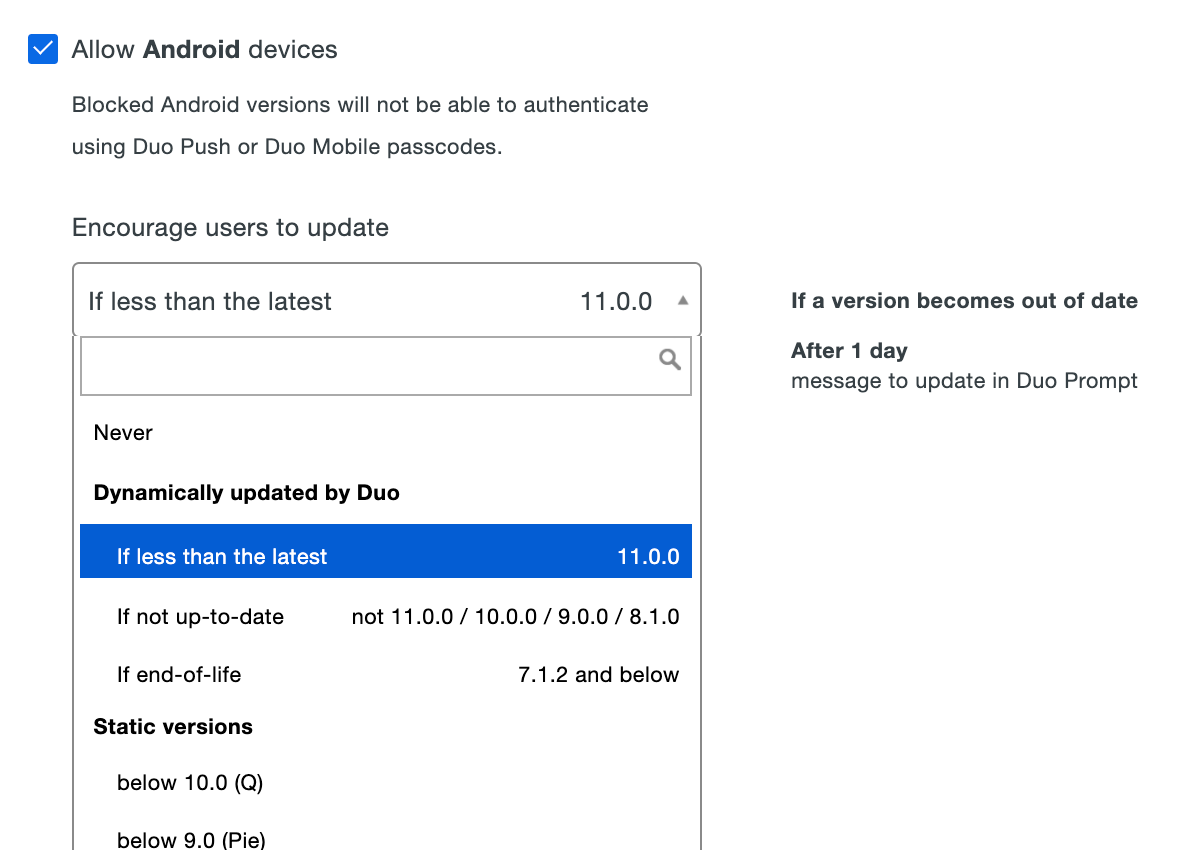
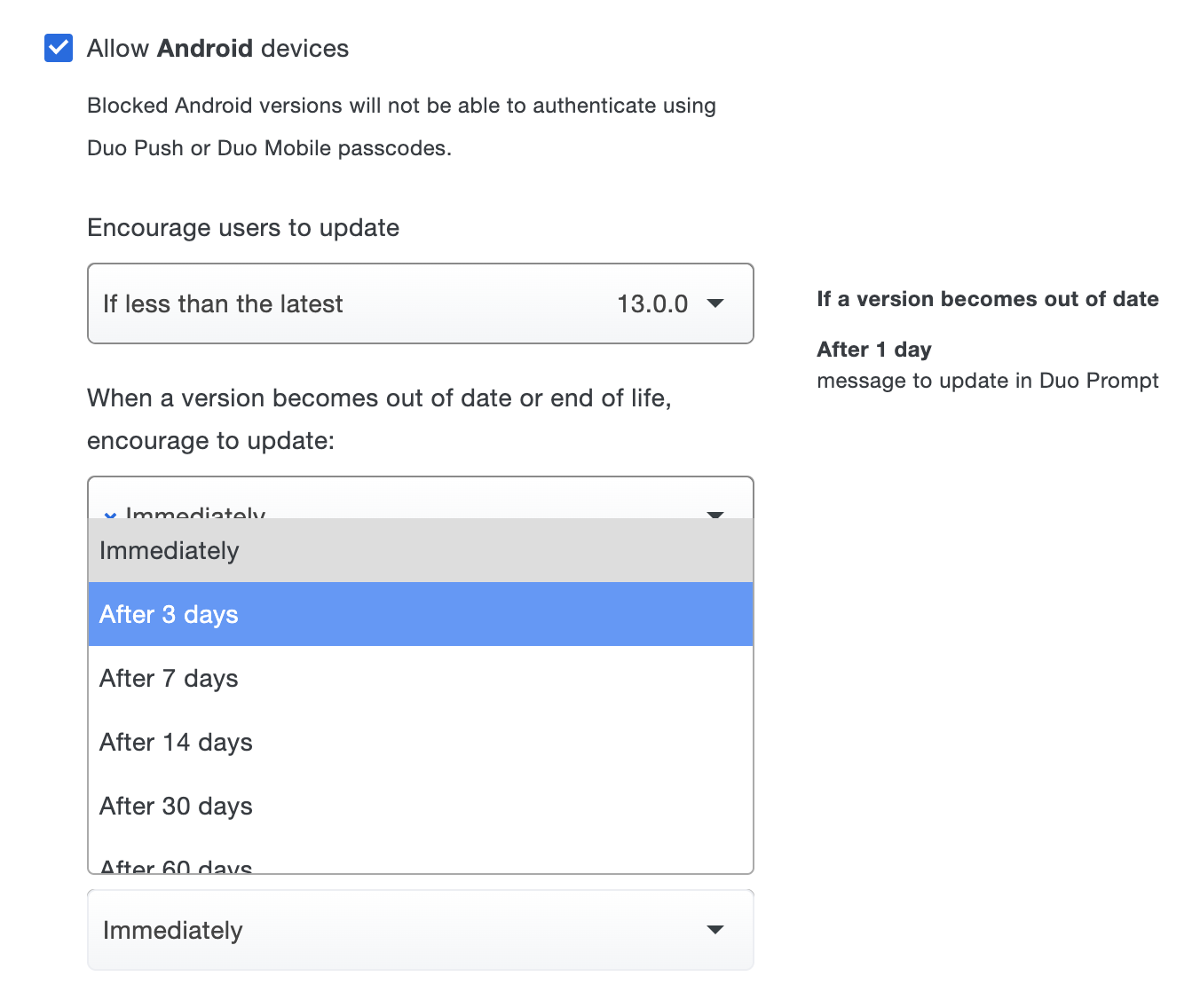
After choosing the OS version, select a grace period from the When a version becomes out of date or end of life, encourage to update choices. Setting this to "Immediately" means users see the warning as soon as their current version is lower than the version you selected. You can delay the Duo warning for up to 365 days. Look to the right of your selection to see a summary of your new policy setting.
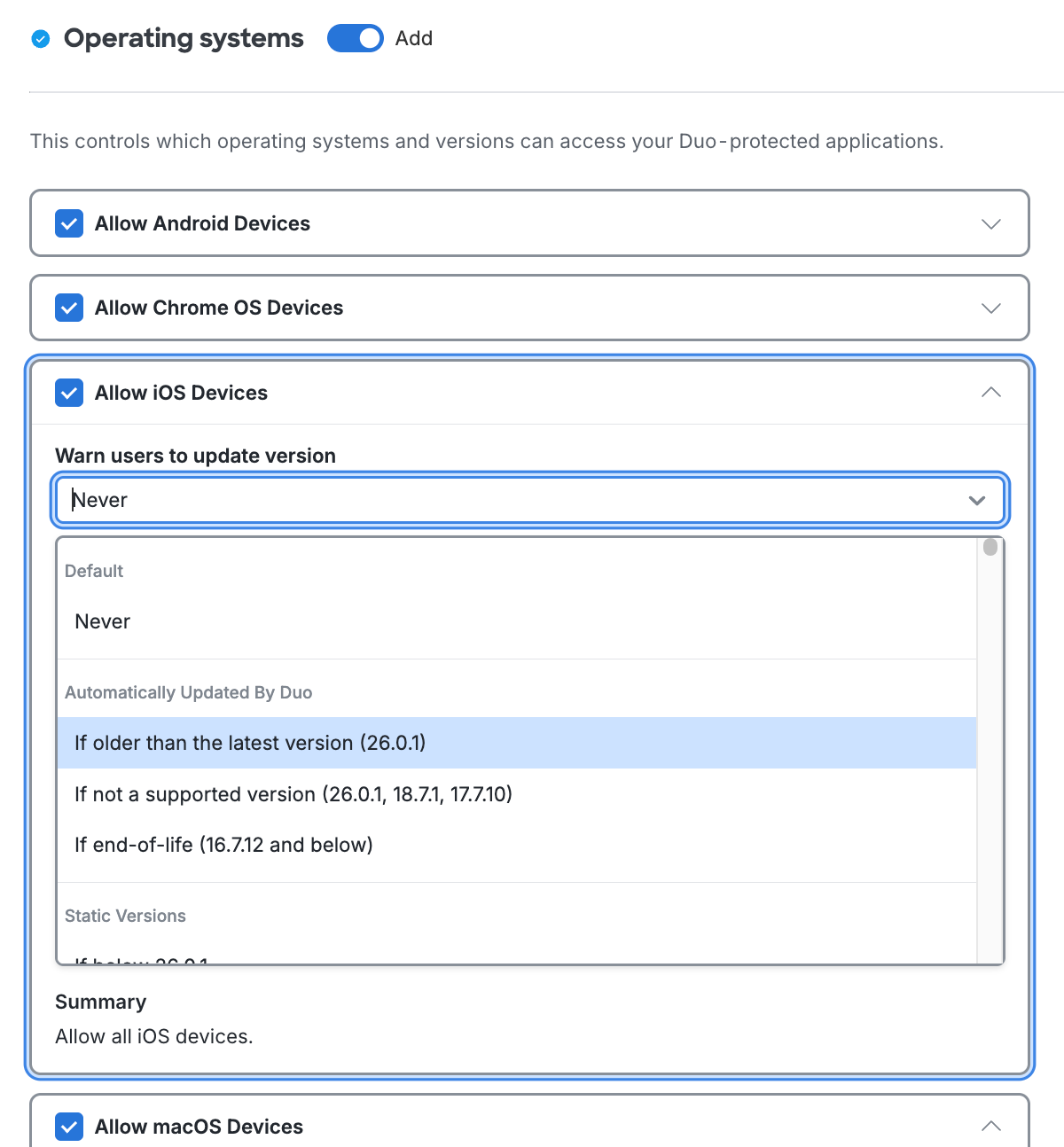
To allow users access to applications while encouraging them to update their OS, expand a given operating system section change the Warn users to update version option from "Never" to your minimum permitted version. This affects access to applications from computers and mobile devices by showing a message in the online Duo prompt recommending they update their operating system. You can choose to select a specific version, or let Duo determine the latest, supported by the vendor with patches, or end-of-life version to allow without a warning.
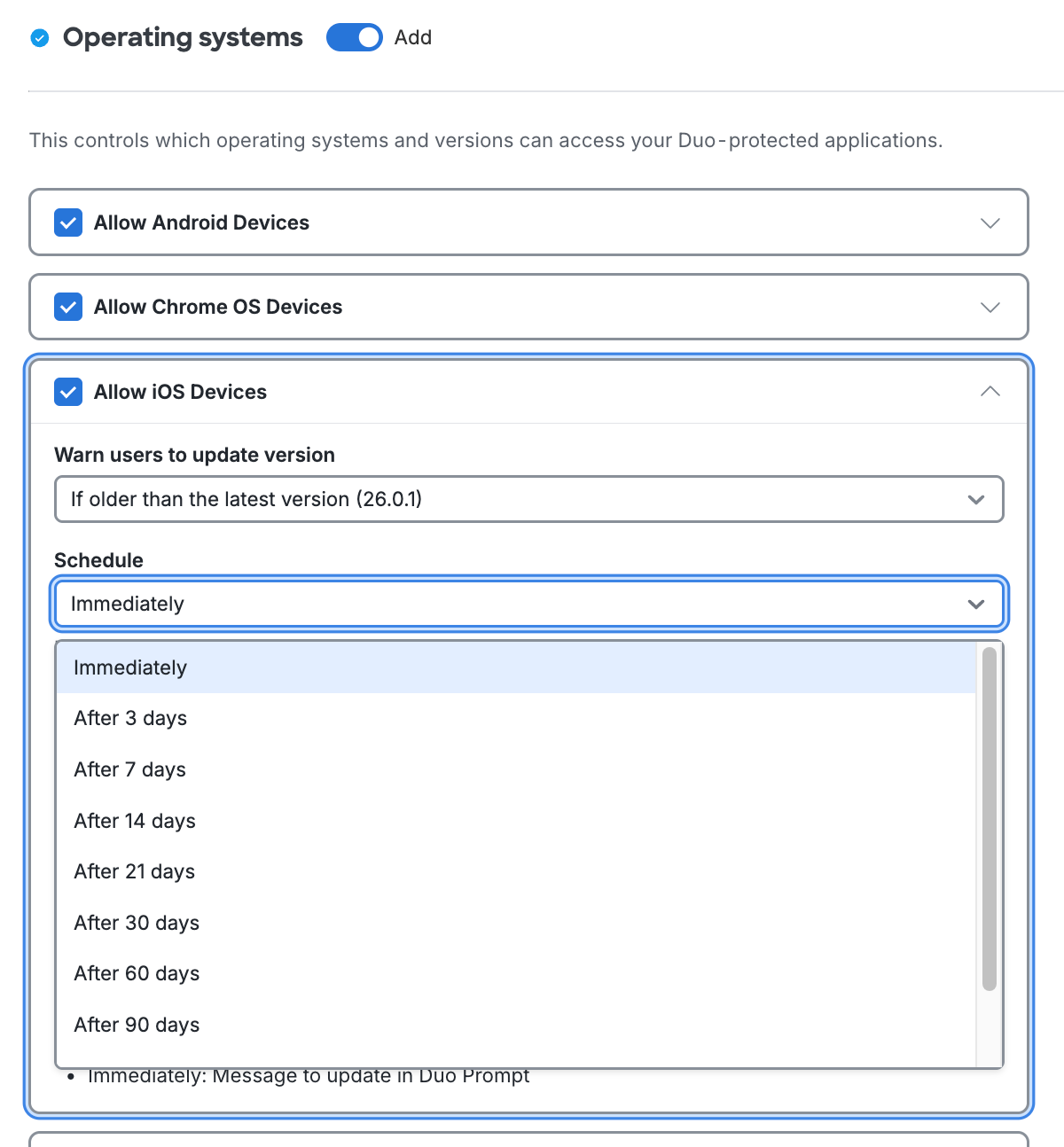
After choosing the OS version, select a grace period from the Schedule choices. Setting this to "Immediately" means users see the warning as soon as their current version is lower than the version you selected. You can delay the Duo warning for up to 365 days. Review the summary of your policy selections underneath the configurable options.
Expand Operating systems data (last 30 days) in the policy editor for recent users' operating system information to help you make OS policy decisions.
Once configured, Duo shows a notification during authentication or enrollment to your users informing them that they should update when accessing your Duo-protected resource from a device running an operating system version older than your selection.
This policy setting has no effect on use of mobile devices for completing Duo authentication. No operating system version warning will be shown to users when they access an application from a computer browser and use an iOS or Android device with an OS version older than your allowed version selection for Duo Push approvals or to generate a passcode.
Universal Prompt Example Scenario
You choose to warn macOS users not running the latest version to consider updating their systems immediately.
A user accessing your application from a Mac a few updates behind the latest sees a message in the Universal Prompt indicating their operating system is out of date.
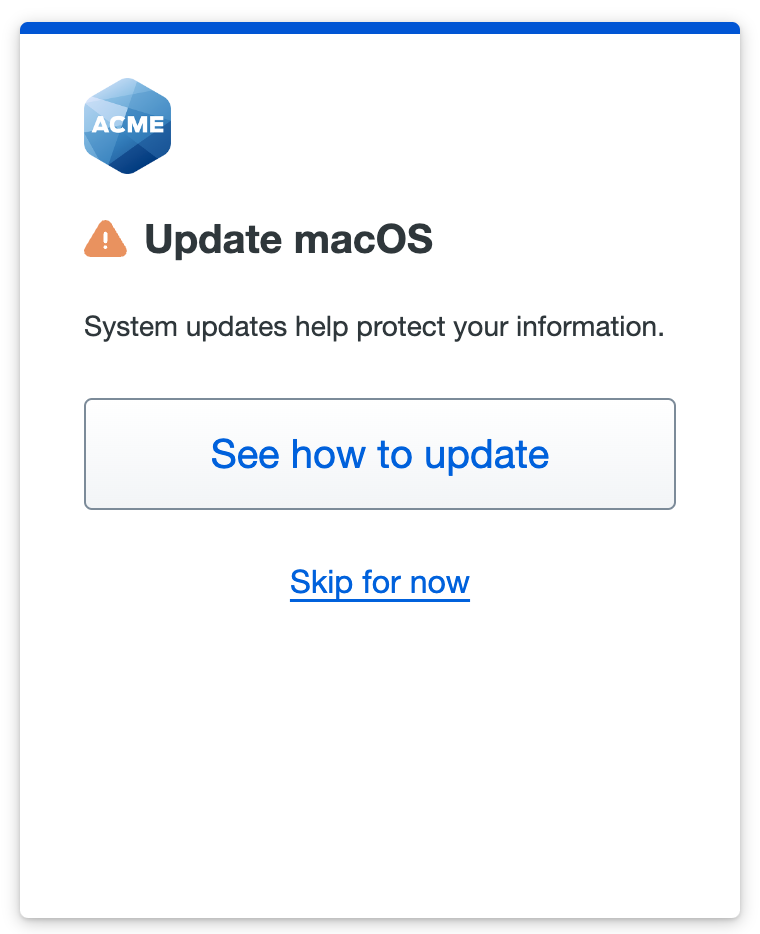
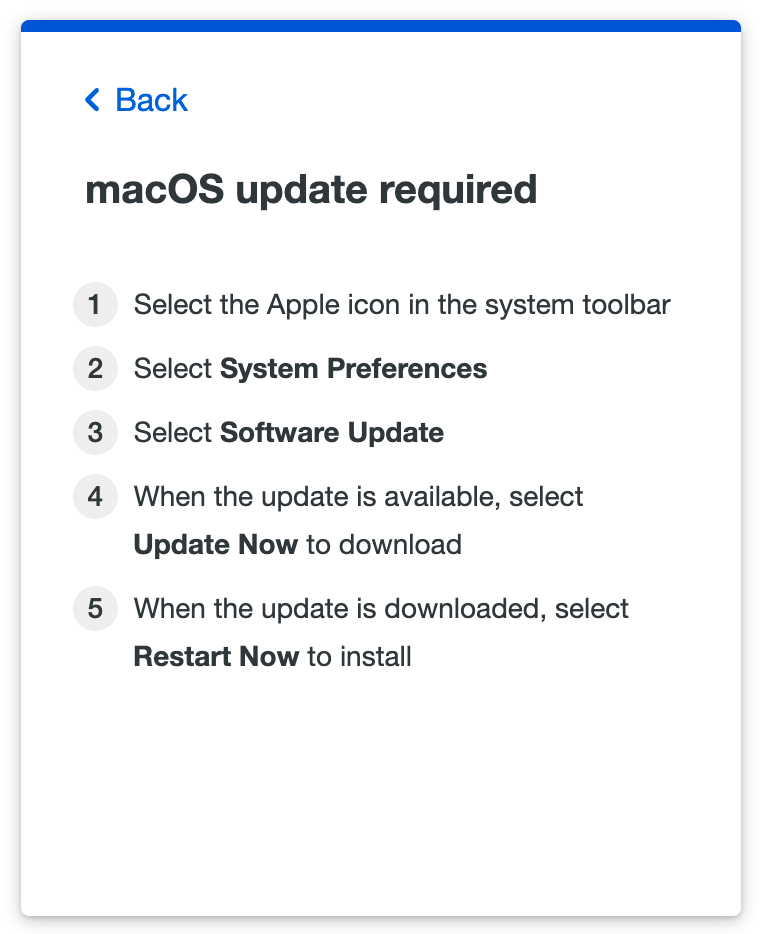
Users can click Skip for now to continue to the application, or click See how to update to view instructions for their operating system.
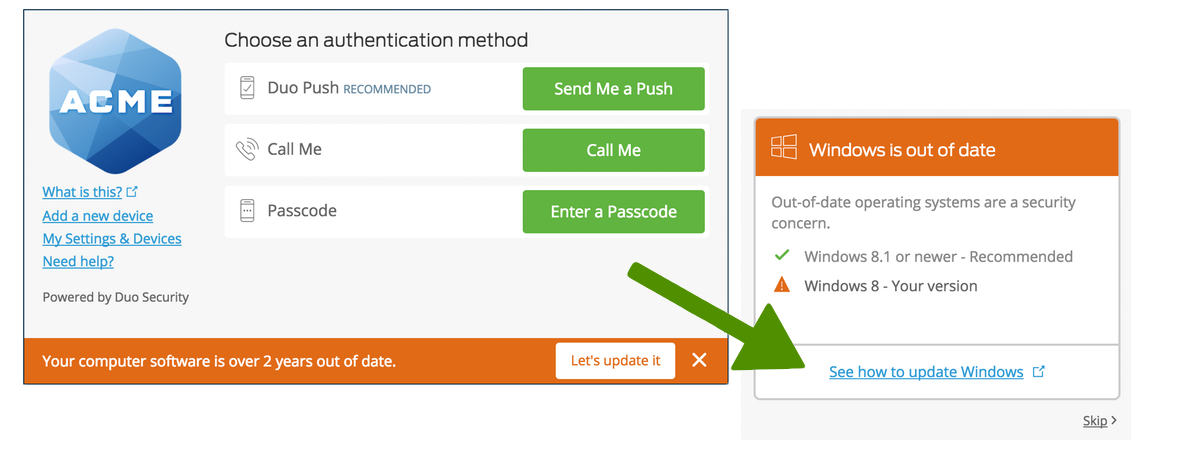
Traditional Prompt Example Scenario
You choose to warn Windows users to update versions older than 8.1 to consider updating their systems immediately.
A user accessing your application from a Windows 8 PC sees a warning at the bottom of the traditional Duo Prompt. Clicking "Let's update it" provides the user with information on how to update the operating system. Users can proceed past the warning by clicking "Skip".
Block Access from Outdated Versions
This policy setting affects use of mobile devices for both accessing applications with a mobile device browser and for authenticating with Duo Mobile push requests or passcodes. See the Mobile Platforms section of this document for more information.
Restrict application access to only the versions you've allowed by making a selection in the Block versions option for an OS, along with a corresponding grace period for blocking. Blocking any operating system version(s) prevents users from completing authentication or new user enrollment from that disallowed OS (or OS version).
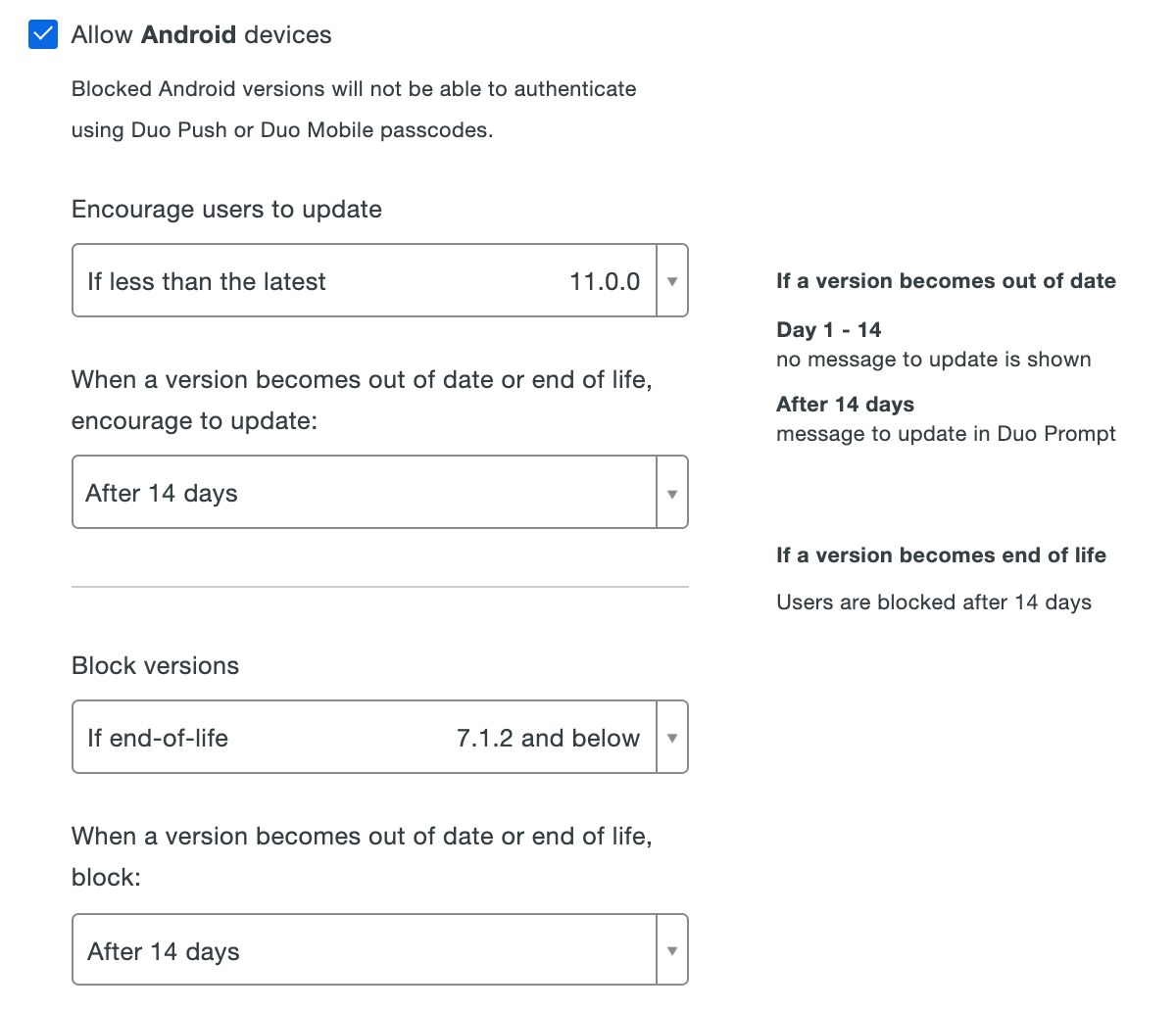
Restrict application access to only the versions you've allowed by making a selection in the Block version option for an OS, along with a corresponding Schedule selection for when to start blocking. Blocking any operating system version(s) prevents users from completing authentication or new user enrollment from that disallowed OS (or OS version).
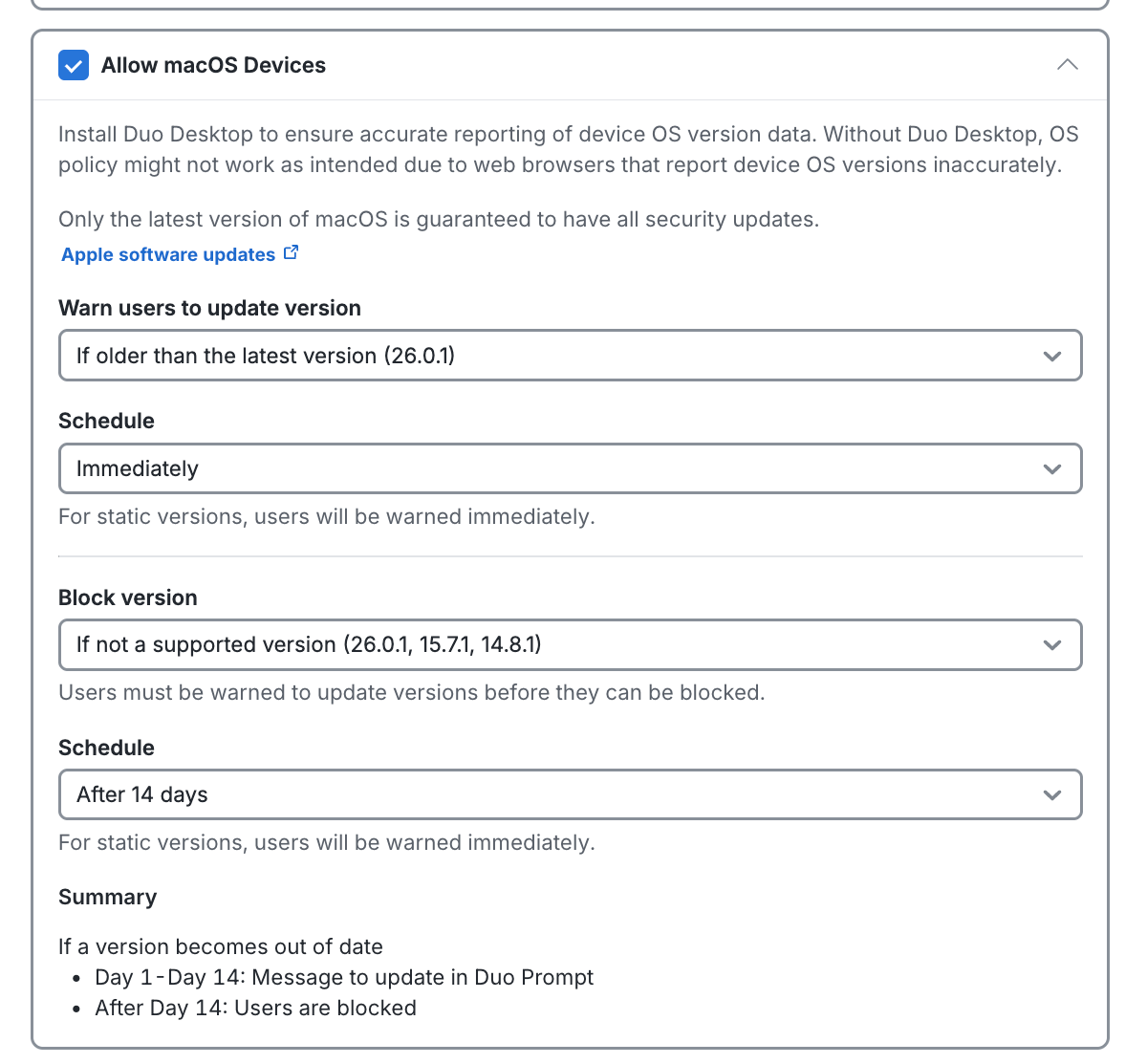
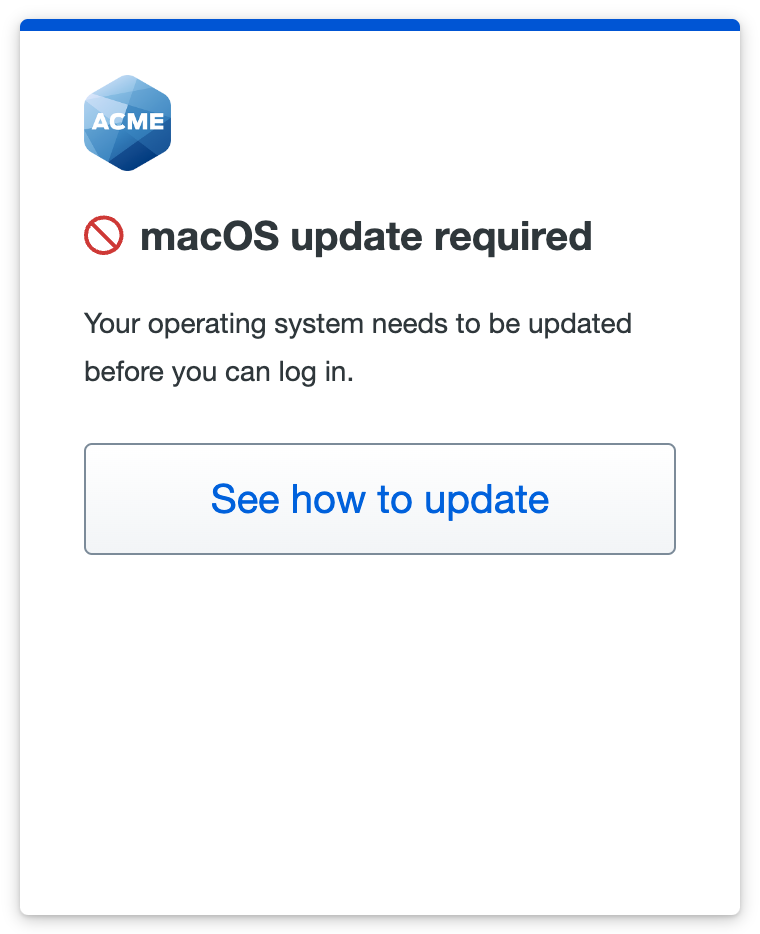
Universal Prompt Example Scenario
You choose to block macOS versions "If less than the latest", which prevents authentication or enrollment for any user trying to access your application from a computer not running the latest version of macOS.
Choosing to block an out-of-date macOS version with a warning grace period gives users a countdown in the out-of-date warning letting them know when they will be required to update their endpoint to continue accessing the application.

If the user doesn't update their operating system by the end of the warning period, or if you chose to immediately block access from the user's OS version, the Universal Prompt denies application access with the update instructions available from the prompt.
Traditional Prompt Example Scenario
You choose to block users with Windows versions "below 8.1", which prevents authentication or enrollment for any user trying to access your application from a Windows 8 computer. A user accessing your application from a Windows 8 PC can't proceed past the out-of-date software notification.
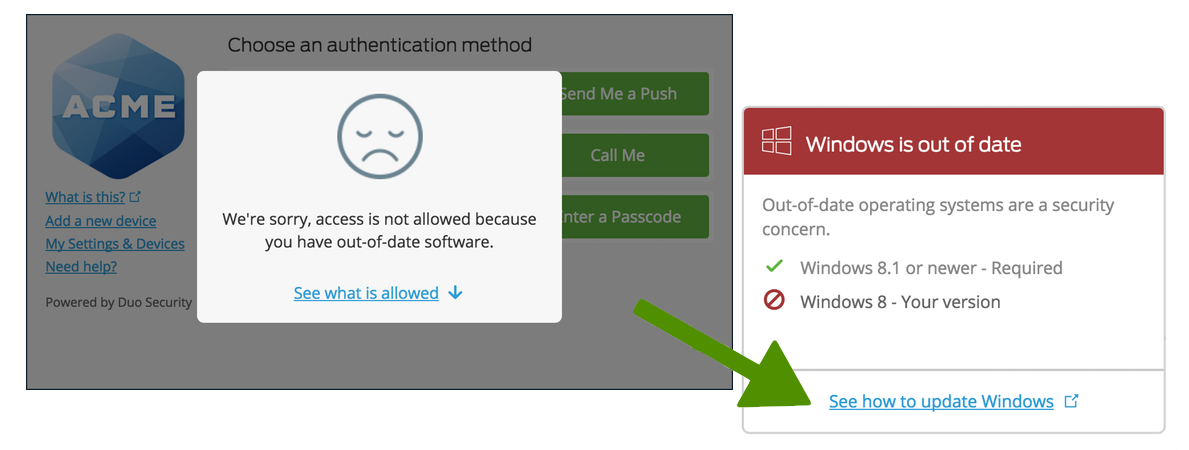
Block Access and Authentication from an Operating System
Uncheck the "Allow" option for an operating system to prevent access and authentication entirely, i.e. if you uncheck Allow Windows Devices in the policy editor, then users accessing your application from any version of Windows are blocked. They can click See what is allowed for information about the operating systems you permit or block.
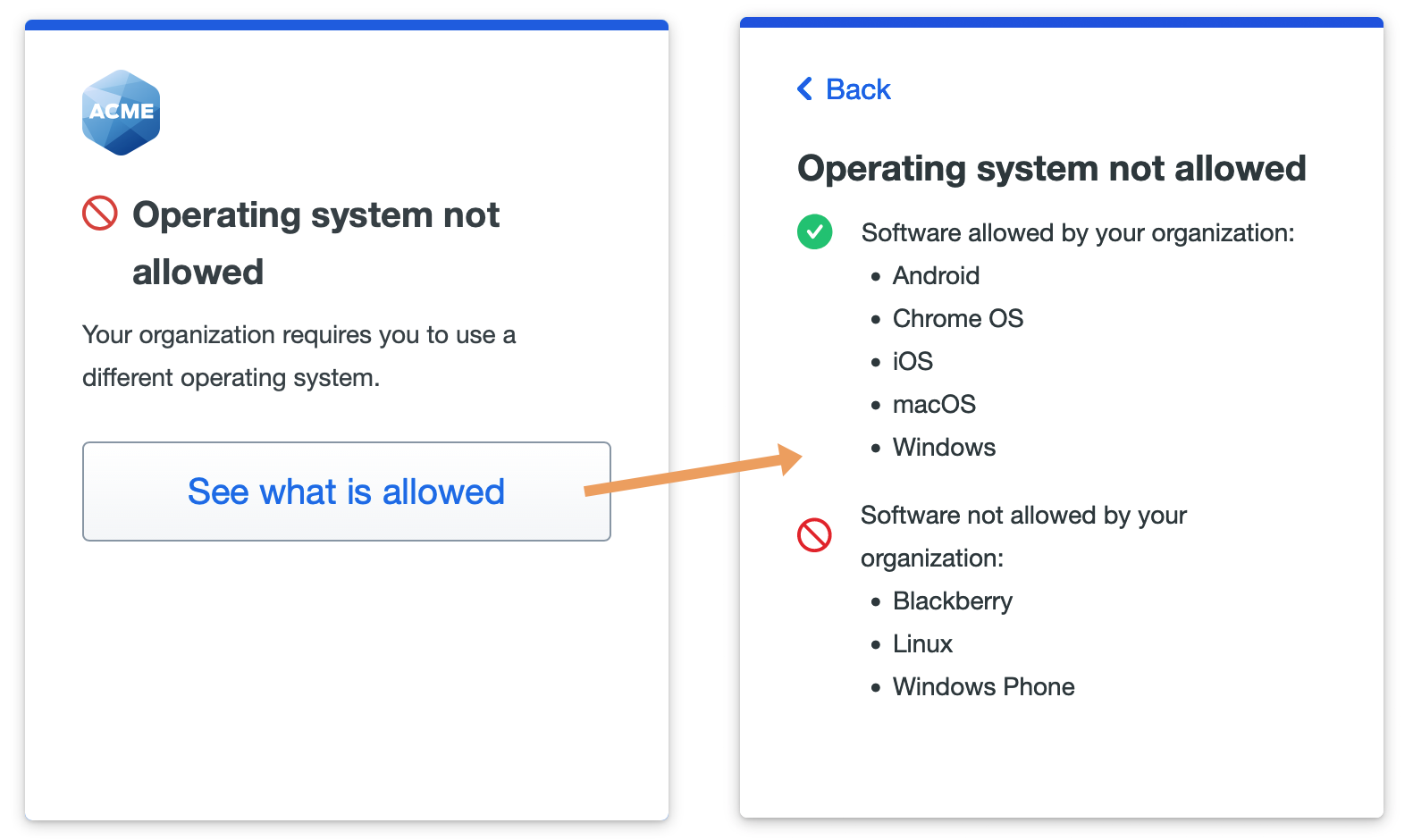
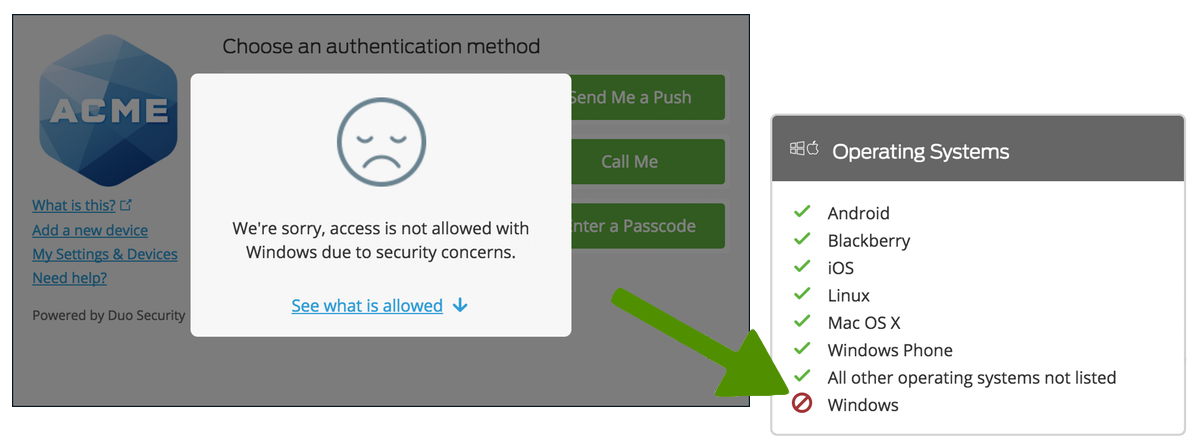
This policy setting affects use of mobile devices for both accessing applications with a mobile device browser and for authenticating with Duo Mobile push requests or passcodes. See the Mobile Platforms section of this document for more information.
Mobile Platforms
The Android and iOS mobile platforms can also be restricted to a minimum allowed version or blocked entirely via the operating system policy options.
Blocking a mobile operating system, or any version of a mobile OS platform, e.g. iOS or Android has the following effects:
- Restricts use of the mobile device to access Duo-protected resources that feature the browser-based traditional Duo Prompt or Universal Prompt on those OS platforms or versions.
- Prevents use of Duo Mobile to approve Duo Push requests or generate usable passcodes to complete two-factor authentication for any Duo-protected application on devices running the restricted OS.
The Encourage users to update or Warn users to update version policy options will not show a warning message in the online Duo prompt for mobile devices completing Duo authentication. iOS or Android devices with an OS version older than your allowed version selection will see a message in Duo Mobile recommending they update to the latest version after approving a Duo Push.
If you were to block iOS versions "below 15.0" then any users with Apple devices running iOS 14.x or lower can no longer access Duo-protected applications from mobile Safari, nor can they approve Duo Push request or use Duo Mobile passcodes from those devices to authenticate to any Duo-protected application, whether it's accessed via browser or not. If a user has other additional activated devices running a different mobile platform, the functionality of the other devices is not affected.
Universal Prompt Example Scenario
You choose to block any iOS versions less than or older than the latest version, which prevents authentication for any user trying to access your application from any mobile device not running the latest version of iOS. This also blocks any out-of-date iOS device from approving two-factor authentication requests or generating passcodes for authentication.
Choosing to block an out-of-date iOS version with a warning grace period shows users a warning message in Duo Mobile after a Duo Push is approved, recommending that they update their iOS.
If the user doesn't update their mobile operating system by the end of the warning period, or if you chose to immediately block access from the user's OS version, the Universal Prompt denies application access with the update instructions available from the prompt.
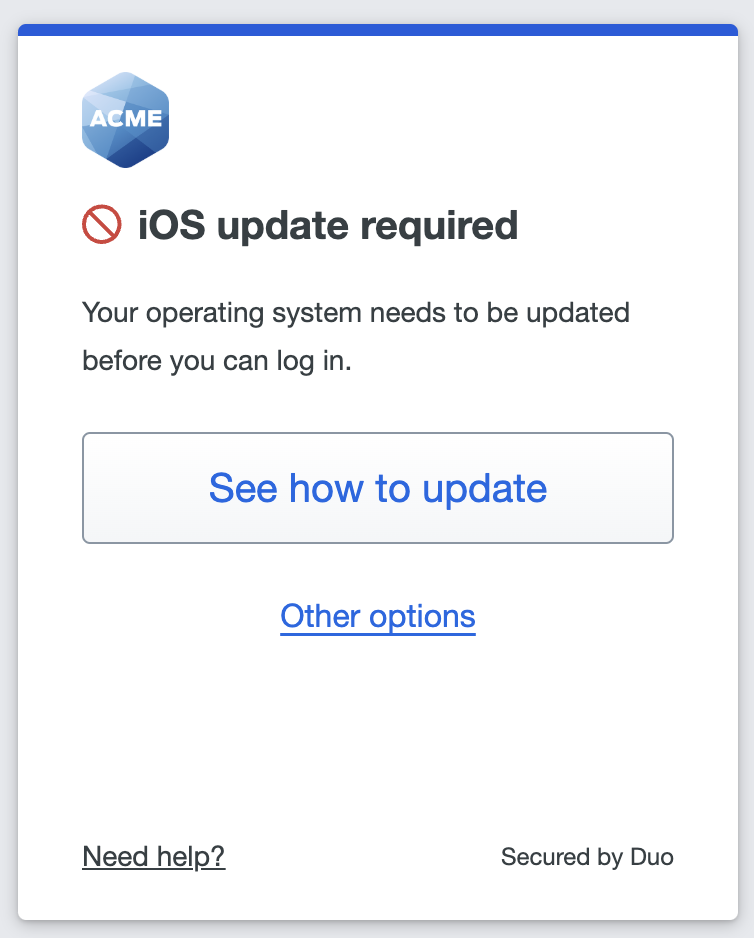
Traditional Prompt Example Scenario
When a mobile device operating system or version is restricted users see a message indicating the mobile version or platform can't be used to complete authentication in the browser-based traditional Duo Prompt.
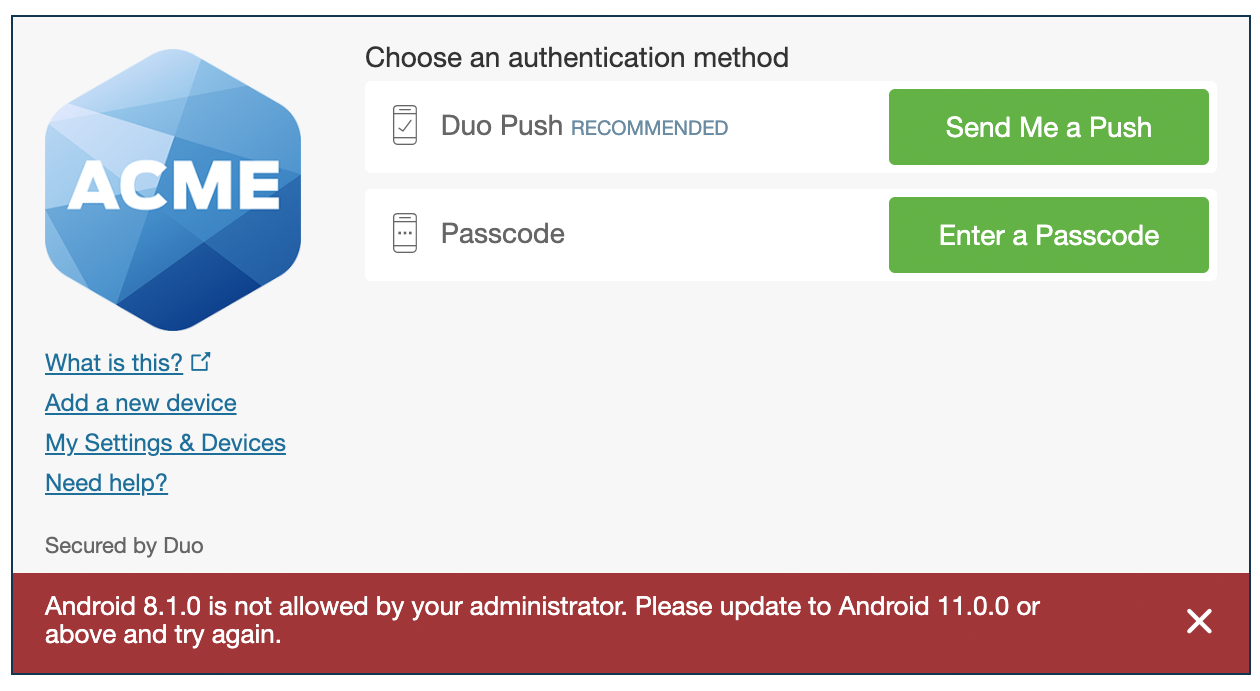
Duo Mobile notifies the user that the mobile platform or version is not allowed when attempting to approve the Duo Push request as well.
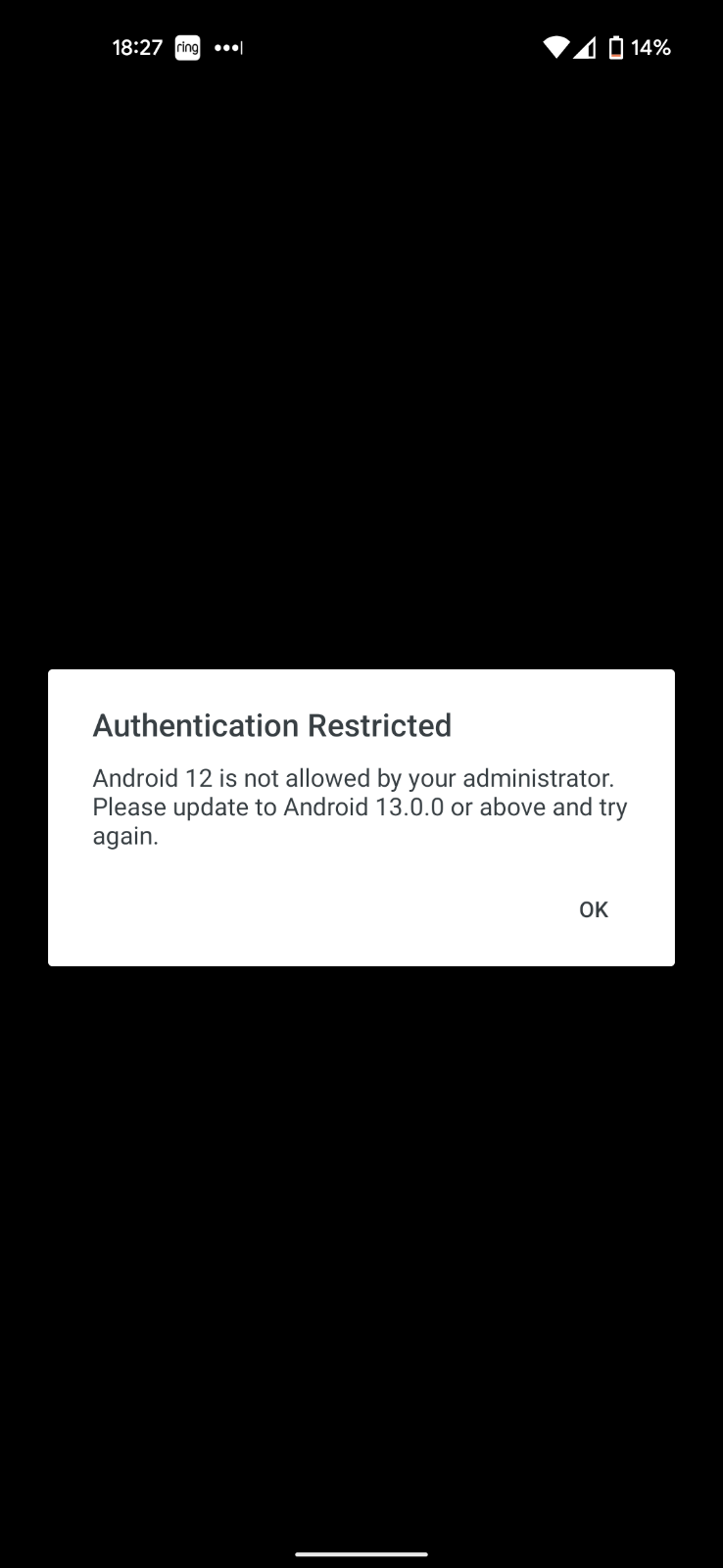
Passcodes from a hardware token or received via SMS are allowed, as are phone call authentications, but entering a passcode generated by Duo Mobile on any device running the restricted platform results in an error stating that platform is not permitted.
As an example scenario, if you disallow Android devices then your iOS users continue to receive and approve Duo Push requests, and can also authenticate with SMS passcodes, application passcodes, hardware tokens, or over the phone. Your Android users can only use SMS passcodes to authenticate, approve a login via phone call, or use a hardware token passcode. If you wanted to completely prevent any use of Android phones to approve authentications, you'd also need to disable the "Phone callback" and "SMS passcodes" options in the Authentication Methods policy setting. Keep in mind that disabling phone and SMS authentication affects authentication for all users, no matter what mobile OS they use.
OS Specific Version Data
These operating system sections and tables detail the state of our version data for the five major OS platforms as of June 9th, 2021. This data maps to the operating system policy options as follows:
-
The current version for an OS platform whose status in the tables below is "Current" satisfies the If less than the latest policy option. All other versions are considered out of date.
-
The current version for an OS platform whose status in the tables below is "Current" or "Supported" satisfies the If not up to date policy option for macOS and Android, and all other versions are considered out of date.
All versions for an OS platform whose status in the tables below is "End of Life" (EOL) fall in scope for the If end of life policy option. Note that out-of-date versions for "Current" or "Supported" status products pass this policy as they aren't considered end of life.
Android Version Information
| Release Name | Base Version | Current Version | Status | Date Marked EOL |
|---|---|---|---|---|
| Android 16 | 16 | 16.0.0 | Current | n/a |
| Android 15 | 15 | 15.0.0 | Supported | n/a |
| Android 14 | 14 | 14.0.0 | Supported | n/a |
| Android 13 | 13 | 13.0.0 | Supported | n/a |
| Android 12 | 12 | 12.1.0 | End of Life | 2025-MAY-29 |
| Android 11 | 11 | 11.0.0 | End of Life | 2024-MAR-27 |
| Android 10 | 10 | 10.0.0 | End of Life | 2023-NOV-14 |
| Android 9 | 9 | 9.0.0 | End of Life | 2022-MAY-04 |
| Android 8 | 8 | 8.1.0 | End of Life | 2022-MAY-04 |
| Android 7 | 7 | 7.1.2 | End of Life | 2020-SEP-28 |
| < 7 | n/a | n/a | End of Life | n/a |
Duo's end-of-life determination for Android is that versions that still receive security patches are considered supported. However, Duo does not check for the presence of security patches on Android devices.
Versions no longer receiving security patches are considered end of life.
Chrome OS Version Information
See the Chrome OS Release Notes for the latest release version.
Chrome OS policy supports the “If less than latest” dynamic option and static versioning enforcement. When determining the latest version Duo will not take the device model into account. Duo will select the current version that is available on a large majority of devices.
Duo supports the Stable, Beta, Dev, LTS, and LTC Chrome OS release tracks. When a version is present in multiple release tracks, Duo will use the least restrictive version to calculate if a device is out of date.
iOS Version Information
| Release Name | Base Version | Current Version | Status | Date Marked EOL |
|---|---|---|---|---|
| iOS 26 | 26 | 26.3 | Current | n/a |
| iOS 18 | 18 | 18.7.5 | Supported * | N/A |
| iOS 17 | 17 | 17.7.10 | End of Life | 2025-NOV-03 |
| iOS 16 | 16 | 16.7.11 | End of Life | 2024-SEP-16 |
| iOS 15 | 15 | 15.8.4 | End of Life | 2024-SEP-16 |
| iOS 14 | 14 | 14.8.1 | End of Life | 2022-JAN-25 |
| iOS 13 | 13 | 13.7 | End of Life | 2020-SEP-25 |
| Older iOS Releases | < 12 | n/a | End of Life | n/a |
* We expect to mark iOS 18 as end of life in 2026 if Apple releases no further updates.
Duo bases the end-of-life determination for iOS on Apple's historical update patterns. Historically, we considered only the most recent iOS version supported, but this has changed. Apple began providing security patches for older releases, starting with iOS 14 and iOS 15. This means our end-of-life determination is no longer solely based on the release of a new iOS version. We now consider an iOS version end-of-life when Apple no longer releases security updates to that version when they release security updates for newer versions.
Enforcement of policies that specify Apple Rapid Security Response (RSR) update versions require Duo Mobile activated for Duo Push on the iOS device to accurately report the OS version. Browsers do not report the RSR portion of the OS version and Duo's operating systems policy will not block those authentications.
macOS Version Information
| Release Name | Base Version | Current Version | Status | Date Marked EOL |
|---|---|---|---|---|
| Tahoe | 26 | 26.3 | Current | n/a |
| Sequoia | 15 | 15.7.4 | Supported | n/a |
| Sonoma | 14 | 14.8.4 | Supported | n/a |
| Ventura | 13 | 13.7.8 | End of Life | 2025-SEP-15 |
| Monterey | 12 | 12.7.6 | End of Life | 2024-SEP-16 |
| Big Sur | 11 | 11.7.10 | End of Life | 2023-OCT-26 |
| Catalina | 10.15 | 10.15.7 | End of Life | 2022-DEC-12 |
| Mojave | 10.14 | 10.14.6 | End of Life | 2021-OCT-25 |
| High Sierra | 10.13 | 10.13.6 | End of Life | 2020-DEC-14 |
| Older Mac Releases | < 10.13 | n/a | End of Life | n/a |
Duo bases the end-of-life determination for macOS on Apple's historical update patterns. Our end-of-life determination is no longer solely based on the release of a new macOS version. We consider a macOS version end-of-life when Apple no longer releases security updates to that version when they release security updates for newer versions.
As of macOS 11, up-to-date versions of major browsers (Safari, Chrome, Firefox, and Edge) have frozen the OS version reported via the browser user agent string as 10.15.6, 10.15.7, or 10.16, impacting the ability to detect whether macOS 11 and later is truly up to date when relying only on information reported to Duo by the browser.
Duo does not block user access from endpoints that report the frozen 10.15.x macOS version in the browser user agent string, as the macOS software on those endpoints may actually be a later, up-to-date version.
Duo Desktop detects and reports the actual macOS version, enabling reliable OS version verification during Duo authentication. Duo recommends using Duo Desktop on macOS 11 or newer clients to enable accurate macOS version checking, blocking, and reporting, especially if you choose to apply a Duo operating systems policy with the "If less than the latest" option selected, or pick a static version of 11.0 or greater.
Enforcement of policies that specify Apple Rapid Security Response (RSR) update versions also require the macOS endpoint to have Duo Desktop installed to accurately report the OS version. Browsers do not report the RSR portion of the OS version and Duo's operating systems policy will not block those authentications.
Learn more about how Duo Desktop enables granular operating system policy for macOS in the Duo Desktop documentation.
Windows Version Information
| Build Name | Base Version | Current Version | Status | Date Marked EOL |
|---|---|---|---|---|
| Windows 11 26H1 | 10.0.28000 | 10.0.28000.1575 | Current | n/a |
| Windows 11 25H2 | 10.0.26200 | 10.0.26200.7840 | Current | n/a |
| Windows 11 24H2 | 10.0.26100 | 10.0.26100.7840 | Current | n/a |
| Windows 11 23H2 | 10.0.22631 | 10.0.22631.6649 | Current | n/a |
| Windows 11 22H2 | 10.0.22621 | 10.0.22621.6060 | End of Life | 2025-OCT-14 |
| Windows 11 21H2 | 10.0.22000 | 10.0.22000.3260 | End of Life | 2024-OCT-08 |
| Windows 10 22H2 (ESU) | 10.0.19045 | 10.0.19045.6937 | Current | n/a |
| Windows 10 22H2 | 10.0.19045 | 10.0.19045.6456 | End of Life | 2025-OCT-14 |
| Windows 10 21H2 | 10.0.19044 | 10.0.19044.5011 | End of Life | 2024-JUN-11 |
| Windows 10 21H1 | 10.0.19043 | 10.0.19043.2364 | End of Life | 2022-DEC-13 |
| Windows 10 20H2 | 10.0.19042 | 10.0.19042.2965 | End of Life | 2022-JUN-14 |
| Windows 10 2004 | 10.0.19041 | 10.0.19041.1415 | End of Life | 2022-JAN-11 |
| Windows 10 1909 | 10.0.18363 | 10.0.18363.2274 | End of Life | 2021-JUN-08 |
| Older Windows 10 Builds | < 10.0.18363 | n/a | End of Life | n/a |
| Windows 8.1 | 6.3.9200 | 6.3.9600 | End of Life | 2023-FEB-06 |
| Windows 8 | 6.2 | n/a | End of Life | 2016-JAN-12 |
| Windows 7 | 6.1 | n/a | End of Life | 2020-FEB-11 |
| Older Windows Releases | < 7 | n/a | End of Life | n/a |
As of the Windows 10 end of life by Microsoft on October 14, 2025, only Windows 10 Extended Security Updates (ESU) build versions remain "current" in Duo operating systems policy. If you have not obtained ESU coverage for your Windows 10 clients and want them to continue accessing Duo-protected resources then you should avoid setting your Windows policy to block the 22H2 19045.6456 release.
Duo’s end-of-life determination for Windows 10 and Windows 11 builds relies on the date that Microsoft marks that build as end of life for Windows Enterprise and Education editions. For Windows 10 20H2 and earlier versions of Windows 10, Duo’s end-of-life determination was based the date that Microsoft marked a build as end of life for Windows 10 Home and Professional editions.
For Windows operating systems before Windows 10, the Duo end-of-life determination matches Microsoft's stated "Extended End Date" for that version.
- Windows 8.1 supported until January 10, 2023; will be marked end of life on February 6. 2023.
- Windows 8 supported until January 12, 2016
- Windows 7 supported until January 14, 2020
Refer to the Lifecycle FAQ for Windows for more details.
A browser user agent provides a limited amount of information about Windows 10 and 11 versions. As of Windows 11, up-to-date versions of major browsers (Chrome, Firefox, and Edge) have frozen the OS version reported via the browser user agent string as Windows 10, impacting the ability to detect whether Windows 11 and later is truly up to date when relying only on information reported to Duo by the browser.
Duo does not block user access from endpoints that report the frozen Windows 10 version in the browser user agent string, as the Windows software on those endpoints may actually be a later, up-to-date version.
Duo Desktop detects and reports the actual Windows build version and the security patch version, enabling reliable OS version verification during Duo authentication. Duo recommends using Duo Desktop on Windows 10 and 11 clients to enable accurate Windows version checking, blocking, and reporting for specific Windows versions, especially if you choose to apply a Duo operating systems policy with the "If less than the latest" option selected, or pick a static version of Windows 11 or greater.
The warn and block OS version policy options do not apply to Windows Server, as it has its own versioning system. If Duo Desktop detects that it's running on a Windows Server, it skips OS version policy enforcement.
Learn more about how Duo Desktop enables granular operating system policy for Windows in the Duo Desktop documentation.
Browsers
Available in: Duo Advantage and Duo Premier
Enable this feature to inform your users when their web browser is out of date and optionally block access to your Duo-protected resources from clients with older browser versions or an entire browser family.
The default setting allows all versions of all browsers and warns users as soon as their installed version of one of the browsers listed by name in the policy options is out of date (0 days). Users authenticating via the Duo Prompt see a notification when a web browser version used is older than the current release version.
This policy supports Chrome, Chrome Mobile, Edge, Edge Chromium Mobile, Firefox, Firefox Mobile, Internet Explorer, Mobile Safari, and Safari. While you can block access from other browsers not listed by name with the All other browsers option, the out-of-date warning and blocking functionality only applies to the named browsers.
Use the drop-down to extend a grace period of 3 days to 1 year before users will start seeing out-of-date warnings while accessing Duo-protected applications from that browser. Instructions for updating or a link to the browser vendor's website are provided if applicable.
You may also choose to block user access when web browsers are out of date and specify a grace period during which users may continue to authenticate with older versions (0 days to 1 year after the current release). This grace period must be longer than the warning grace period so users have time to update their browsers before being blocked. If both the warning and block grace periods are set to 0 days, users have no opportunity to update their browsers as they will be blocked immediately once their browser is out of date.
This policy supports Chrome, Chrome Mobile, Edge, Edge Chromium Mobile, Firefox, Firefox Mobile, Internet Explorer, Mobile Safari, and Safari. While you can block access from other browsers not listed by name with the Other browsers option, the out-of-date warning and blocking functionality only applies to the named browsers.
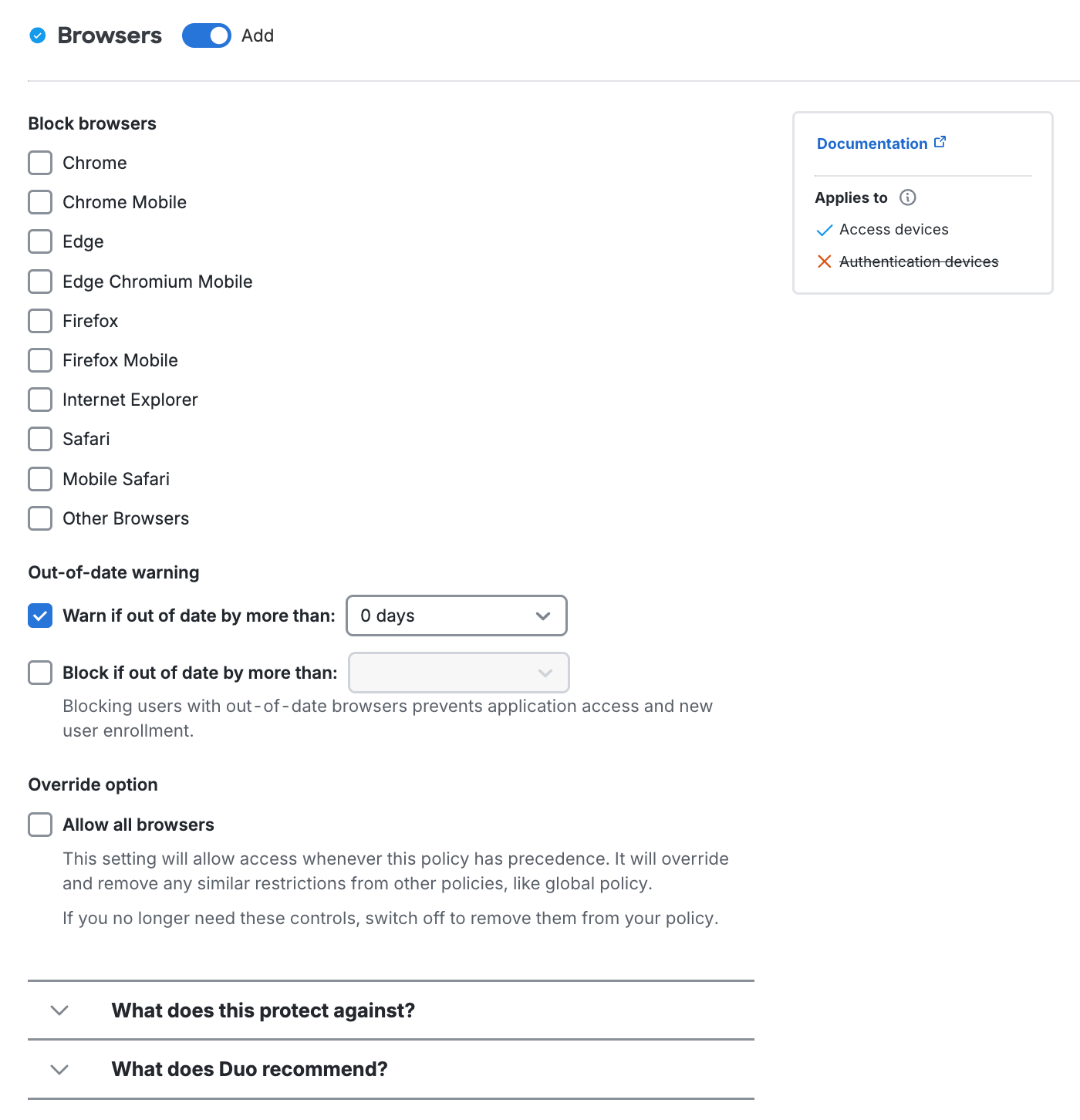
Users will see the browser warning immediately as soon as a newer browser version becomes available. Use the Warn if out of date by more than drop-down to extend a grace period of 3 days to 1 year before users will start seeing out-of-date warnings while accessing Duo-protected applications from that browser. Instructions for updating or a link to the browser vendor's website are provided if applicable.
You may also choose to block user access when web browsers are out of date with the Block if out of date by more than option and specify a grace period during which users may continue to authenticate with older versions (0 days to 1 year after the current release). This grace period must be longer than the warning grace period so users have time to update their browsers before being blocked. If both the warning and block grace periods are set to 0 days, users would have no opportunity to update their browsers as they would be blocked immediately once their browser is out of date.
Use the "Override option" Allow all browsers setting if you want users subject to this policy to always be able to authenticate from any version of any browser, regardless of other browser policy settings in the user's effective policy stack.
When a user accesses an application from an out-of-date browser, they'll see a suggestion to update. Instructions for updating or a link to the browser vendor's website are provided if applicable.
If you have only opted to warn users, they may skip the software update and complete authentication. The out-of-date notification continues appearing during authentication attempts until the end user updates to the current version.
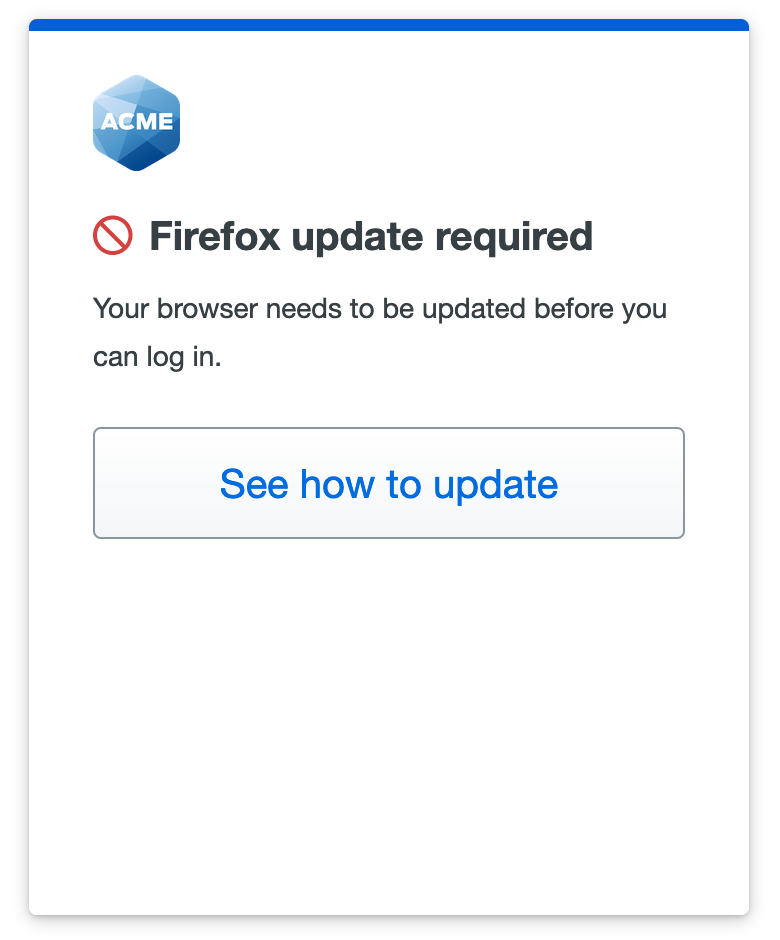
If you set your policy to block access from out-of-date browsers, users can skip past the software update warning up until the end of the grace period you specified in the policy.
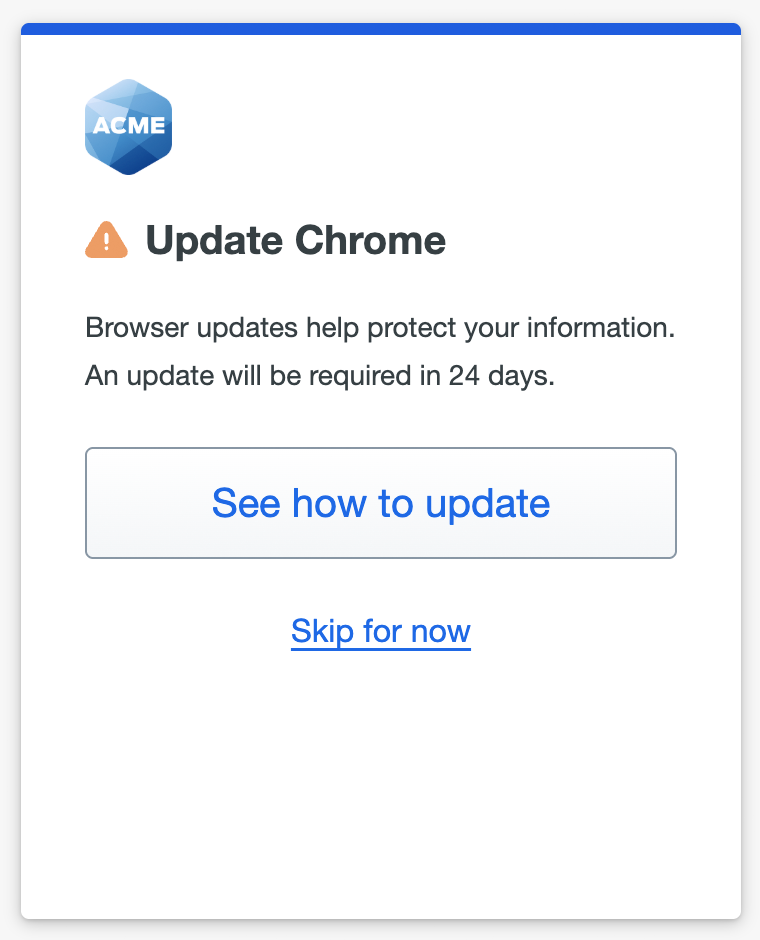
After that, users may not continue to Duo new user enrollment and authentication. Only updating the browser to a current version permits a user to complete Duo authentication or enrollment.
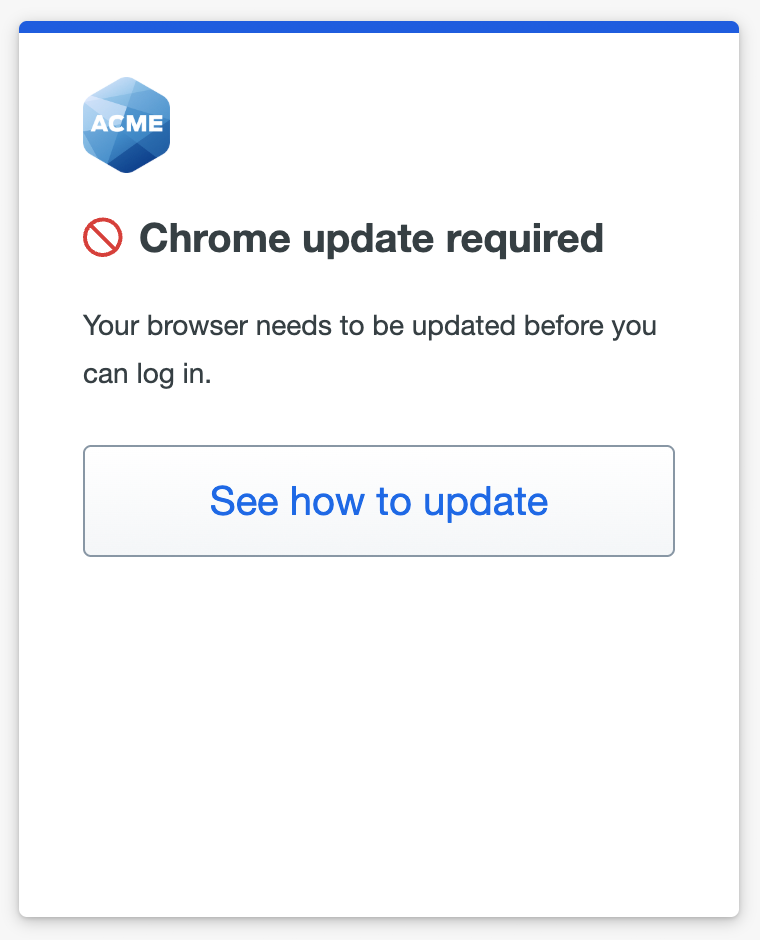
When you restrict user access from certain web browsers completely by blocking it in the policy setting, affected users can click See what is allowed in the block message to review the list of browsers permitted by your policy.
See Software Update in the user guide for more information.
Plugins
Available in: Duo Advantage and Duo Premier
Not enforced for passwordless authentication
Enable this feature to inform your users when selected plugins are out of date or block access to your Duo-protected resources from clients with outdated plugins (or block a plugin entirely). The default setting blocks all versions of Flash plugins and warns users when their Java plugin is out of date.
When the "Warn users" option is enabled, users authenticating via the Duo Prompt see a notification when the selected plugins are older than the current release version. If you have only selected to notify users of the outdated software, they may skip the software update and complete authentication. The software update notification continues appearing during authentication attempts until the end user updates the affected plugin.
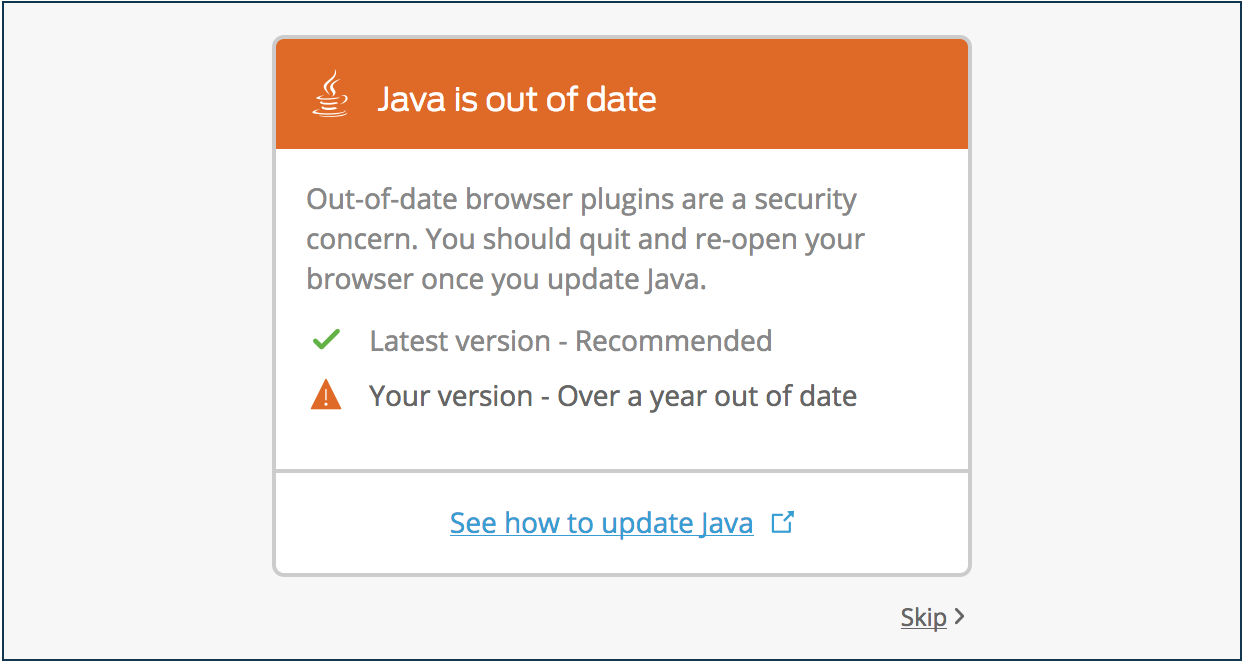
You may also choose to block user access when plugins are out of date and specify a grace period during which users may continue to authenticate with older versions (0 days to one year after the current release).
If you set your policy to block access from out of date plugins, users can skip past the software update warning up until the end of the grace period you specified in the policy. After that, users may not continue to Duo new user enrollment and authentication. Only updating the affected plugins permits a user to complete Duo authentication or enrollment.
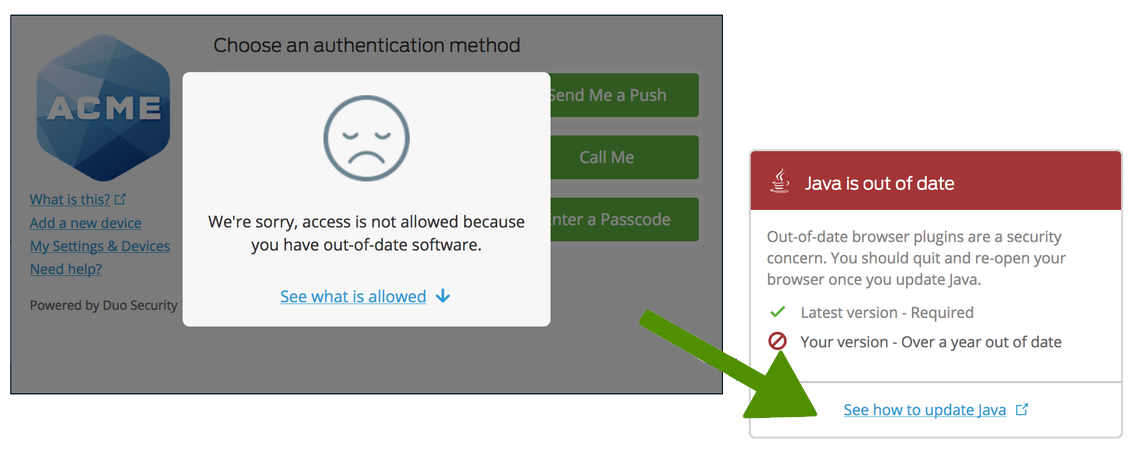
Restrict user access with certain plugins completely by selecting "Block all versions".
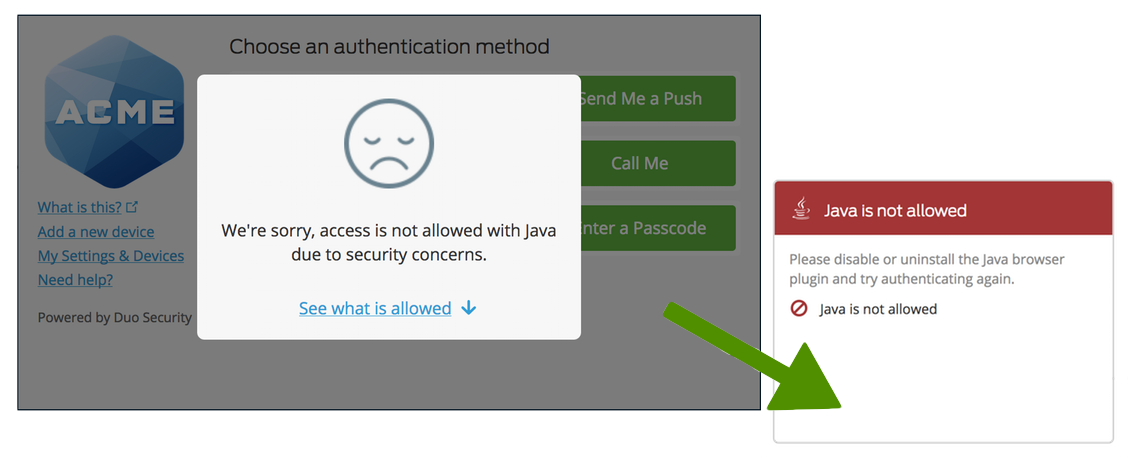
Configure software notifications for either or all of the following plugins:
-
Flash: Checks whether or not the browser uses the Flash plugin. Adobe ended support for Flash on December 31, 2020, and began blocking Flash content from running in Flash Player on January 12, 2021. With Flash at its end-of-life (EOL), version updates are no longer possible. Therefore, the Duo policy options no longer check for the latest version, and only offer the options to allow or block all versions of Flash.
Customers who configured a Flash plugin policy that checks for out-of-date versions prior to the Flash EOL still see those settings when viewing or editing those existing policies, but should be aware that the end of update availability means that all versions are considered out of date.
Duo recommends that all customers set the Flash plugin policy to Block all versions.
-
Java: Checks the version of the Java plugin used by the current browser and notifies the user if it is out of date. A link is provided to the Oracle Java download site.
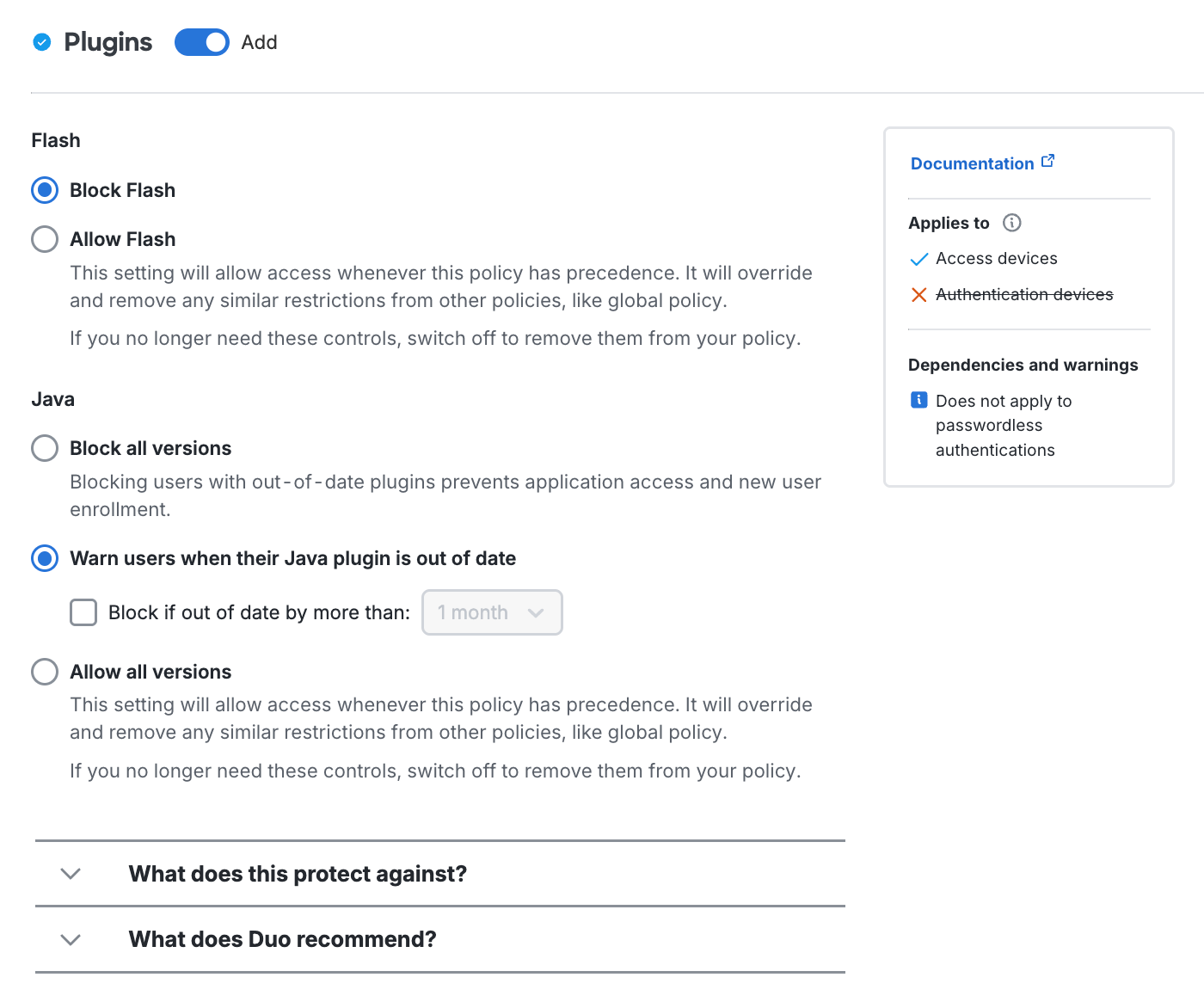
Configure this policy setting for these plugins:
-
Flash: Checks whether or not the browser uses the Flash plugin. Adobe ended support for Flash on December 31, 2020, and began blocking Flash content from running in Flash Player on January 12, 2021. With Flash at its end-of-life (EOL), version updates are no longer possible. Therefore, the Duo policy options no longer check for the latest version, and only offer the options to Block Flash (default) or Allow Flash.
-
Java: Checks the version of the Java plugin used by the current browser and notifies the user if it is out of date. A link is provided to the Oracle Java download site.
With Warn users when their Java plugin is out of date enabled, users authenticating via the Duo Prompt see a notification when the selected plugins are older than the current release version. If you have only selected to notify users of the outdated software, they may skip the software update and complete authentication. The software update notification continues appearing during authentication attempts until the end user updates the affected plugin.

You may also enable Block if out of date by more than and specify a grace period during which users may continue to authenticate with older versions (0 days to one year after the current release).
If you set your policy to block access from out of date plugins, users can skip past the software update warning up until the end of the grace period you specified in the policy. After that, users may not continue to Duo new user enrollment and authentication. Only updating the affected plugins permits a user to complete Duo authentication or enrollment.

Restrict user access from browsers with Java enabled completely by selecting Block all versions.

See Software Update in the user guide for more information.
Networks Policy Settings
Authorized Networks
Available in: Duo Essentials, Duo Advantage, and Duo Premier
Partially enforced for passwordless authentication
Define global or application 2FA policies for different networks with Duo's authorized networks policy. Essentials customers can minimize Duo prompts for specific networks, while Advantage and Premier customers have additional options to require Duo authentication or block access entirely on a per network basis. The default settings apply no per-network restrictions or allowances.
The authorized policy options are:
-
Allow access without 2FA from these networks: Users accessing Duo-protected resources from these networks skip Duo secondary authentication. Specify a block of IP addresses, IP ranges, or CIDRs as a comma-separated list. If you have enabled Duo Passwordless for your organization the description of this setting mentions this has no effect on passwordless authentication.
By default, Duo prompts users to enroll when logging in from an authorized network when the new user policy is set to require enrollment. To prevent unenrolled users from receiving the Duo enrollment prompt when connecting from an authorized network, uncheck the Require enrollment from these networks setting.
-
Require 2FA from these networks: Users accessing Duo-protected resources from these networks must always complete Duo secondary authentication, even when another policy that permits bypassing Duo applies. Specify a block of IP addresses, IP ranges, or CIDRs as a comma-separated list. This overrides remembered device trust.
Note that the setting is Require MFA from these networks when passwordless is enabled.
-
Deny access from these networks -
- Deny access from any other network not specified above: Use this option to block user access from any network not configured in the "allow access" or "require 2FA" options. At least one network must be defined for 2FA bypass or enforcement to enable this setting.
- Deny access from these networks: Users attempting to access Duo-protected resources from these networks will be blocked. Specify a block of IP addresses, IP ranges, or CIDRs as a comma-separated list. This overrides the “allow access” and “require 2FA” options.
WARNINGEnabling the deny access option blocks access from Duo applications that don't report client IP! This prevents connections for any Duo application that shows the client IP as 0.0.0.0. Before configuring the setting please review your authentication logs in the Admin Panel to verify your Duo-protected applications report the client IP.
If there is any overlap between the network segments or IP addresses defined in the "allow access", "require 2FA", and "deny access" options, then the more restrictive policy setting applies.
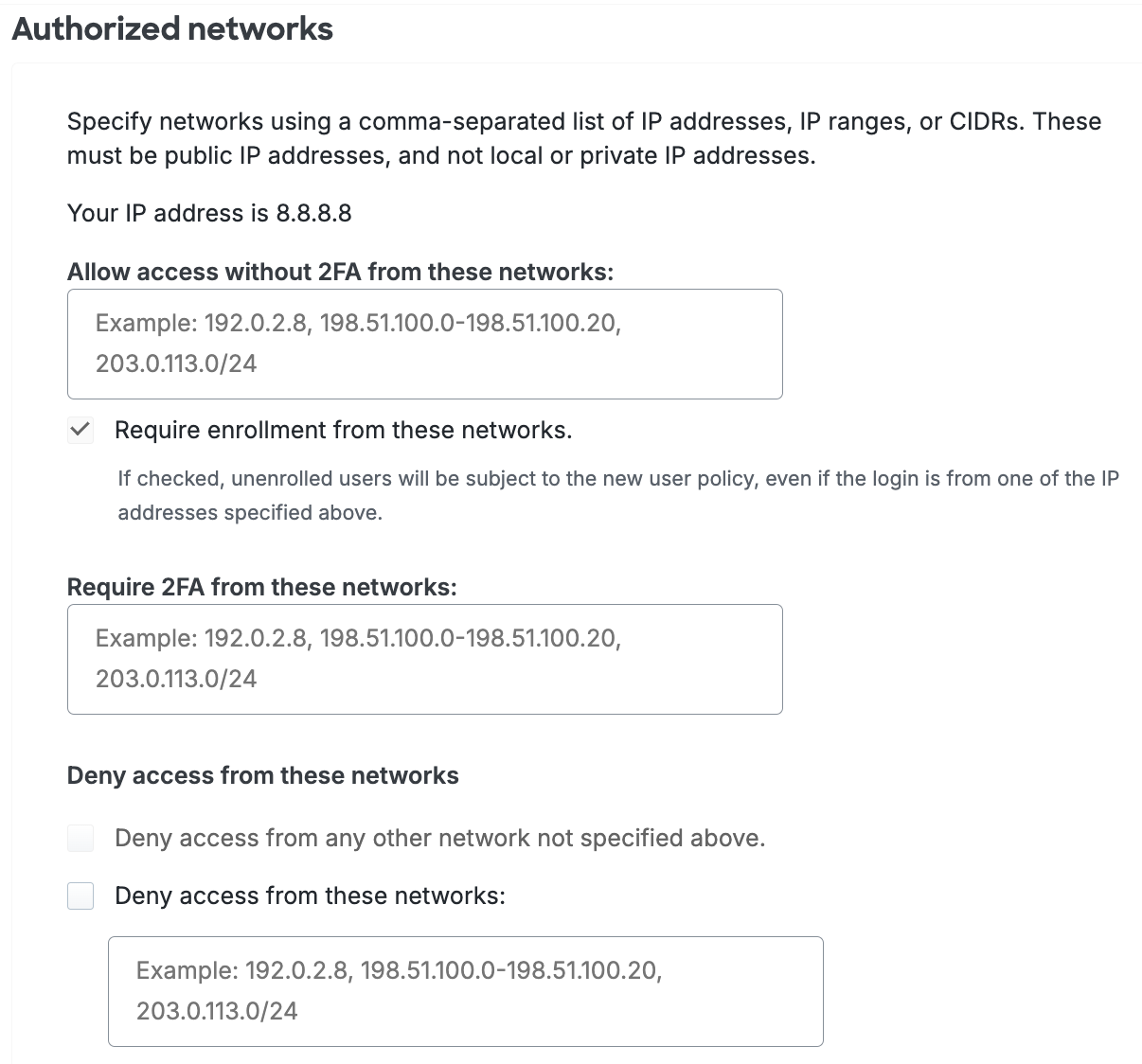
The Duo Essentials plan authorized networks policy only permits specifying a network to bypass Duo Essentials for regular (not passwordless) authentication, and does not include the require or deny options.
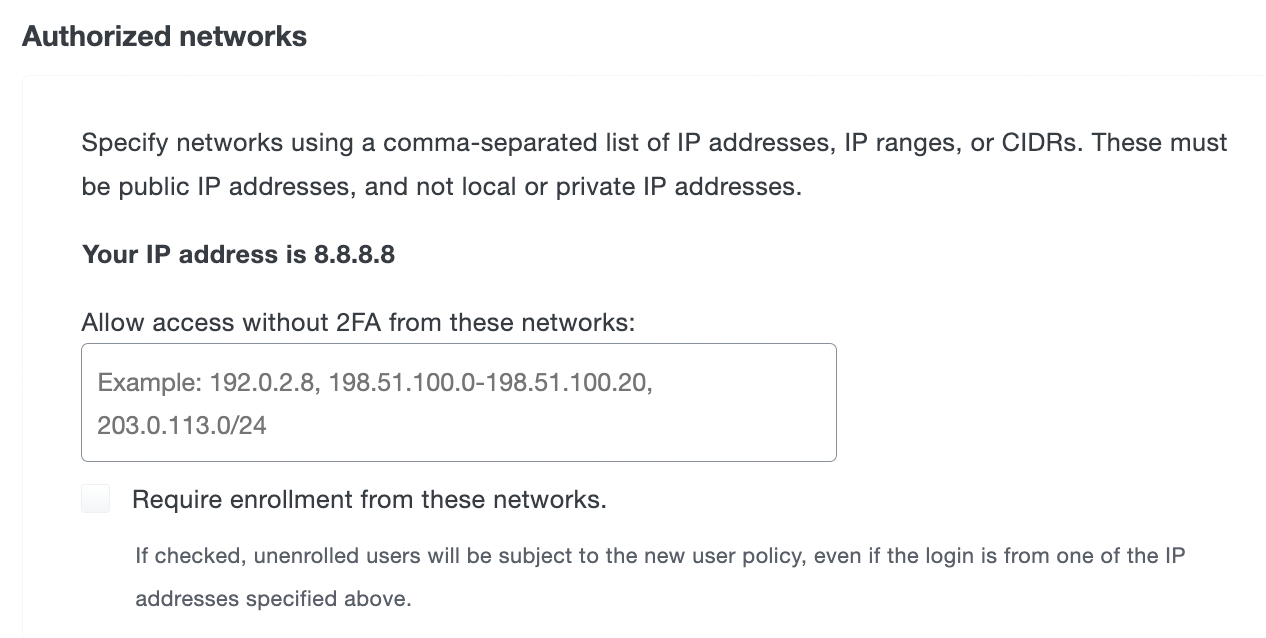
-
Skip MFA from these networks (passwordless authentication is not skipped): Users accessing Duo-protected resources from these networks bypass Duo secondary authentication. Specify a block of IP addresses, IP ranges, or CIDRs as a comma-separated list.
New, unenrolled users connecting from an authorized network will not be required to complete Duo enrollment when the new user policy is set to require enrollment unless you enable the Require enrollment from these networks option.
-
Require MFA from these networks every time, even if it would normally be skipped: Users accessing Duo-protected resources from these networks must always complete Duo secondary authentication, even when another policy that permits bypassing Duo applies. Specify a block of IP addresses, IP ranges, or CIDRs as a comma-separated list. This overrides remembered device trust.
-
Block access from these networks -
- Block access from any other network not specified above: Use this option to deny user access from any network not configured in the "allow access" or "require MFA" options. At least one network must be defined for 2FA bypass or enforcement to enable this setting.
- Block access from these networks: Denies access to Duo-protected resources for users on these networks. Specify a block of IP addresses, IP ranges, or CIDRs as a comma-separated list. This overrides the “skip MFA” and “require MFA” options.
WARNINGEnabling the "block access" options prevent access from Duo applications that don't report client IP! This prevents connections for any Duo application that shows the client IP as 0.0.0.0. Before configuring the setting please review your authentication logs in the Admin Panel to verify your Duo-protected applications report the client IP.
-
Allow access from all networks: Enable this to create a custom policy that will override any other effective policies implementing IP restrictions when placed higher in the stack.
If there is any overlap between the network segments or IP addresses defined in the "skip MFA", "require MFA", and "block access" options, then the more restrictive policy setting applies.
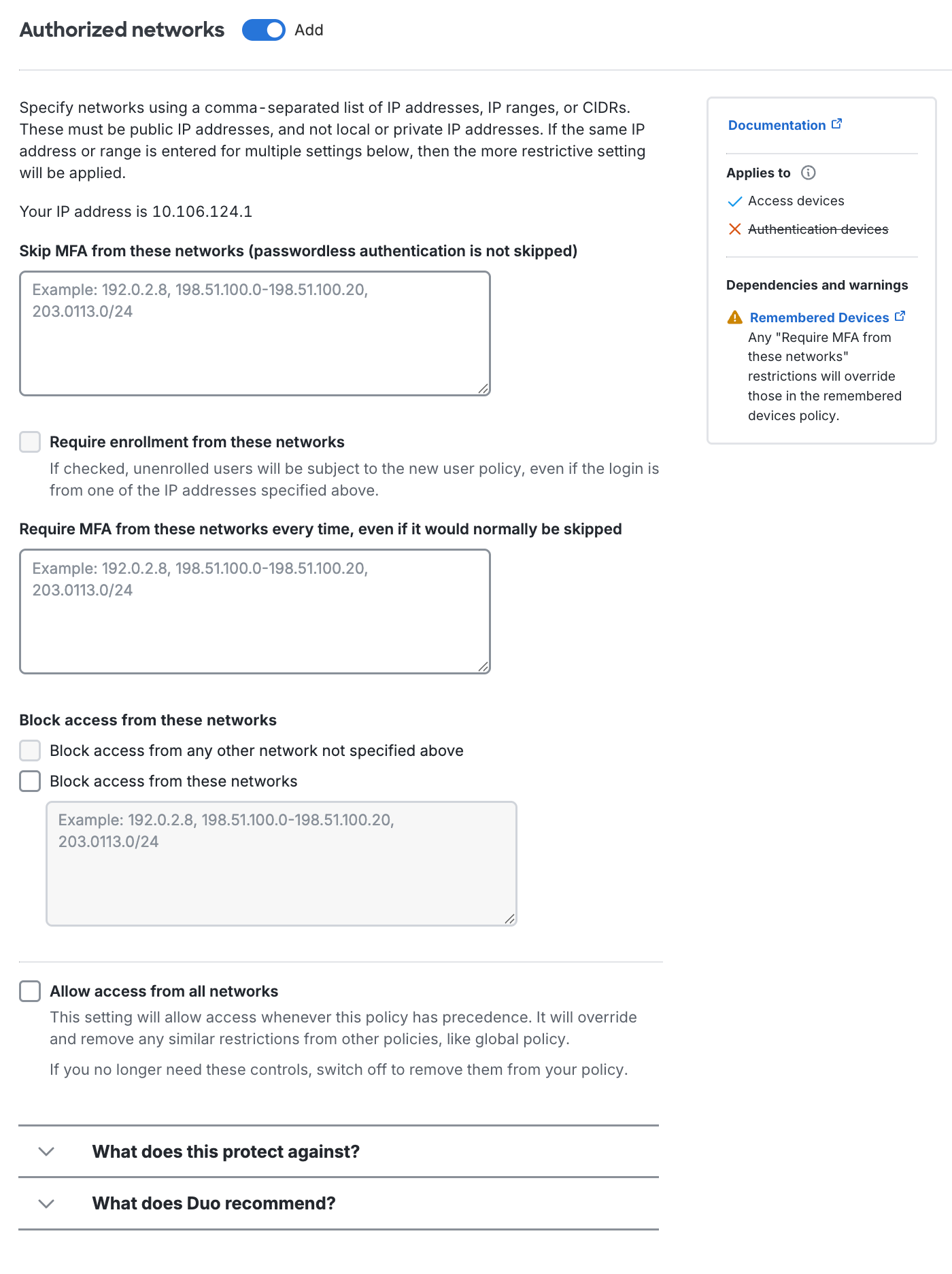
The Duo Essentials plan authorized networks policy only permits specifying a network to bypass Duo Essentials for regular (not passwordless) authentication or allowing access from all networks, and does not include the "require MFA" or "block access" options.
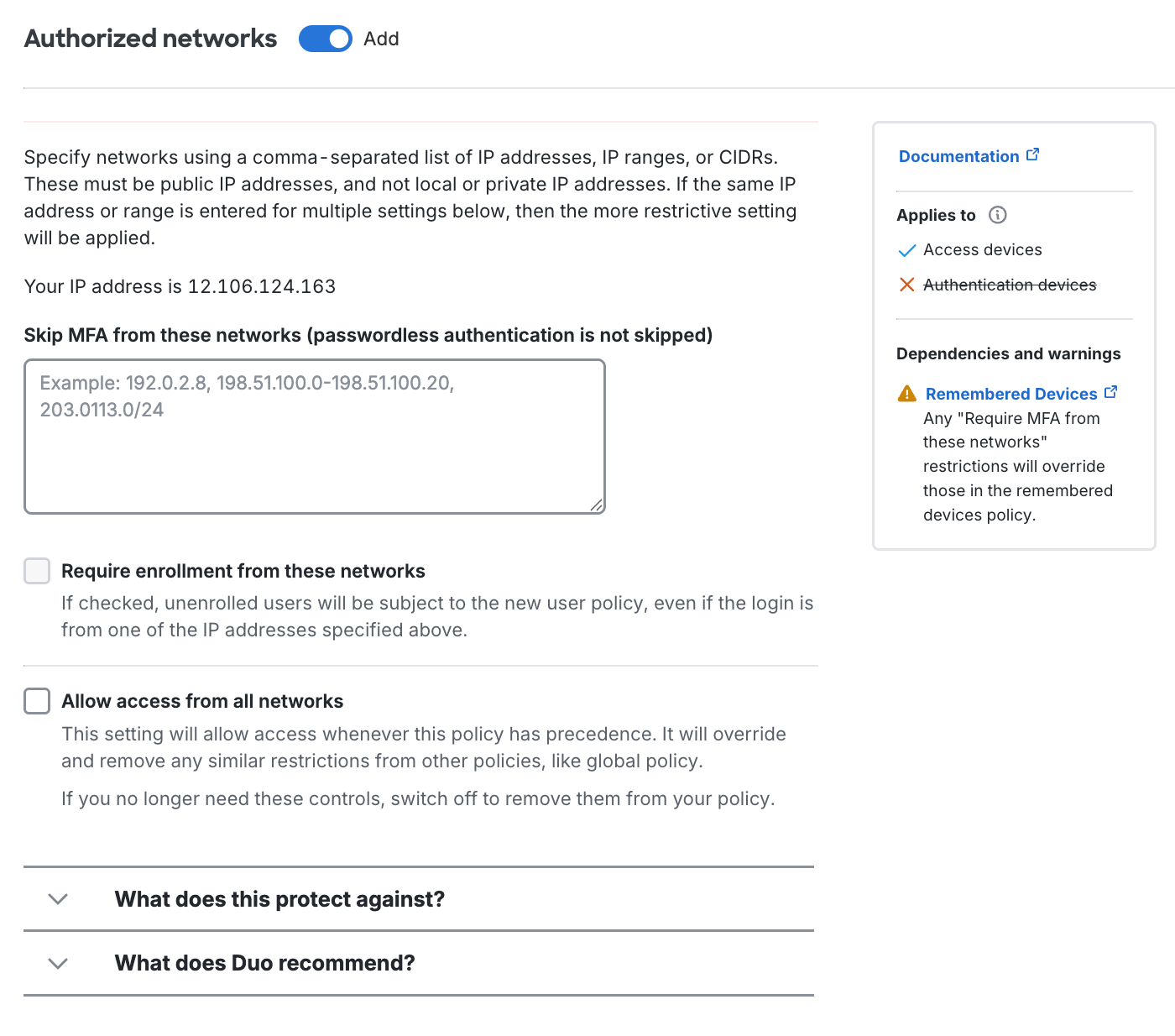
Anonymous Networks
Available in: Duo Advantage and Duo Premier
Duo can help you monitor and optionally prevent application access and MFA attempts originating from known anonymous IP addresses, such as those provided by Tor and I2P, HTTP/HTTPS proxies, or anonymous VPNs. The anonymous networks policy applies to both password + MFA and passwordless authentication. The available settings are:
-
Don’t change authentication requirements: Permits Duo two-factor authentication and bypass or passwordless authentication from anonymous IP addresses. This is the default policy setting.
-
Require 2FA or passwordless authentication even if it would normally be skipped: Always require two-factor authentication or passwordless authentication for requests from anonymous IP addresses. This supersedes other effective policies that would permit access without 2FA or passwordless authentication.
-
Deny access: Prevents all Duo authentication attempts from anonymous IP addresses.
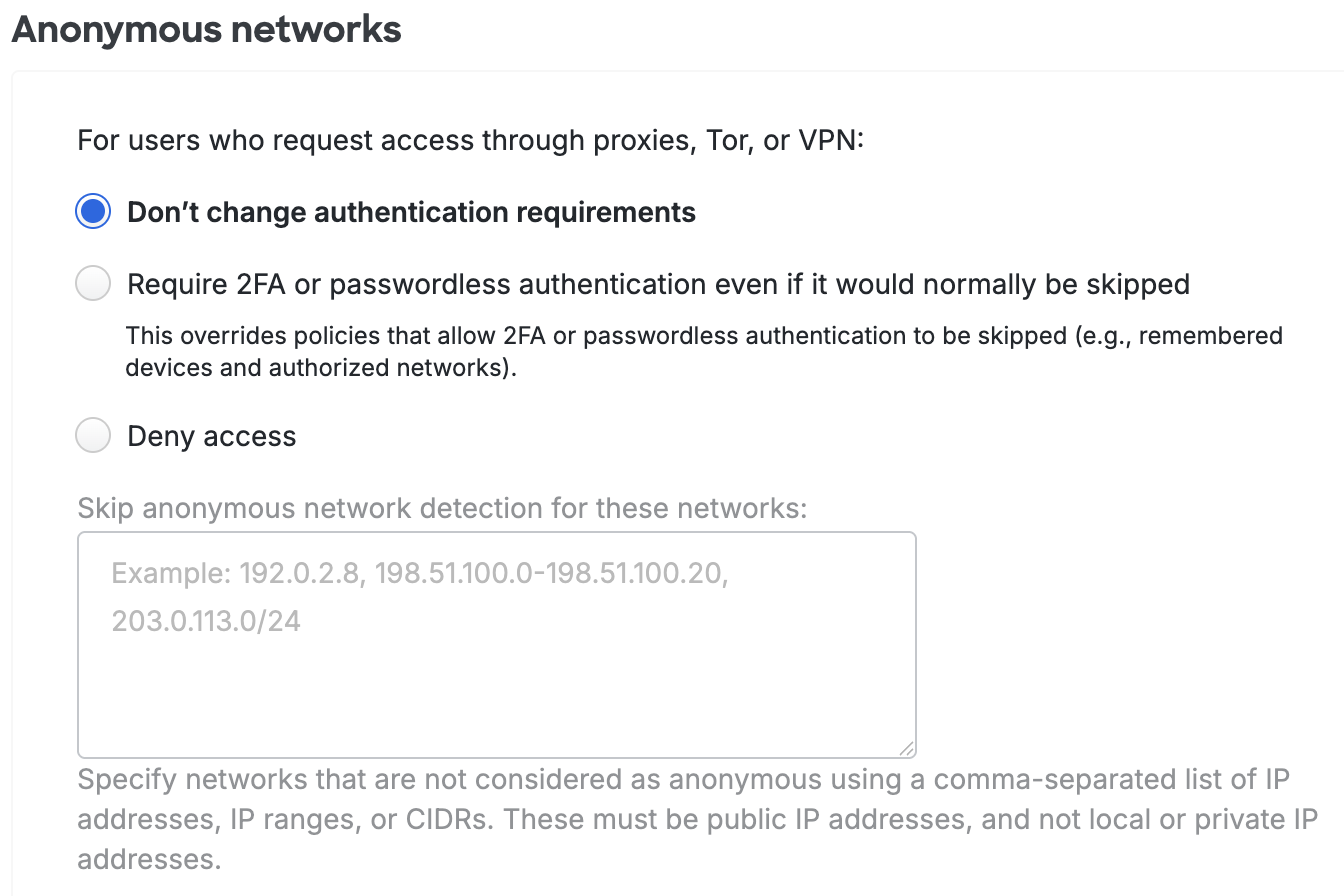
If you select Deny Access or Require 2FA or passwordless authentication even if it would normally be skipped, you can specify networks that are not considered as anonymous and allow access by entering a comma-separated list of IP Addresses, IP ranges, or CIDRs in the Skip anonymous network detection for these networks: field. These must be public IP addresses, and not local or private addresses.
Learn more about Duo Passwordless and how to enable passwordless authentication for your users in the Duo Passwordless documentation.
-
Require MFA or passwordless authentication every time, even if it would normally be skipped: Always require two-factor authentication or passwordless authentication for requests from anonymous IP addresses. This supersedes other effective policies that would permit access without 2FA or passwordless authentication.
-
Block access: Prevents all Duo authentication attempts from anonymous IP addresses.
-
Allow access from anonymous networks: Permits Duo two-factor authentication and bypass or passwordless authentication from anonymous IP addresses. This is the default policy setting.
A new anonymous networks policy will consider the IP address of both the device accessing the protected application and the IP address of the Duo Mobile device used for authentication. To disregard the Duo Mobile device's network, enable the Only check access device IP option under "Advanced settings". Be aware that enabling this option reduces the effectiveness of anonymous network blocking rules.
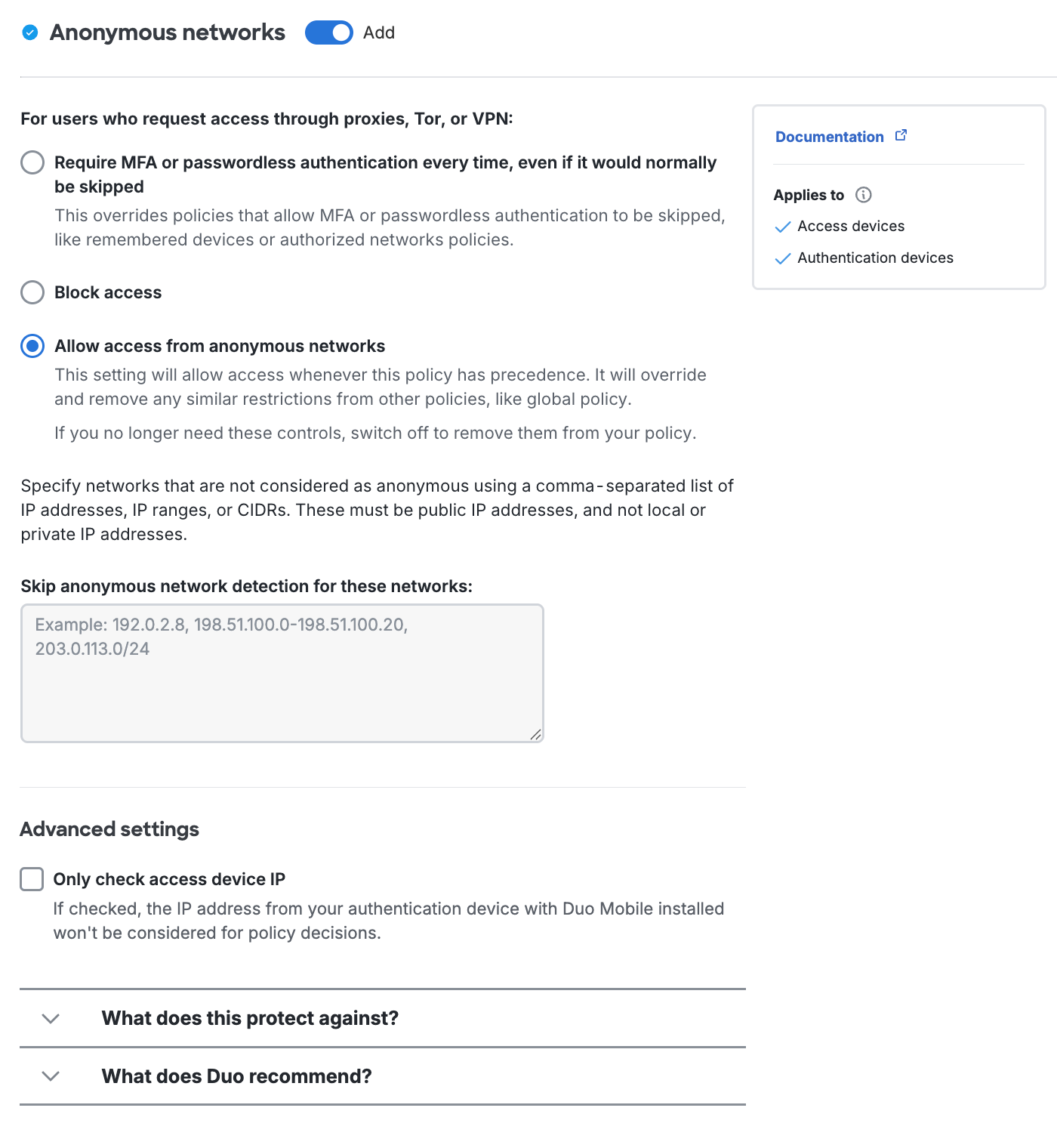
If you select the "require MFA" or "block" options, you can specify networks Duo will not consider anonymous and allow access from by entering a comma-separated list of IP Addresses, IP ranges, or CIDRs in the Skip anonymous network detection for these networks: field. These must be public IP addresses, and not local or private addresses.
Learn more about Duo Passwordless and how to enable passwordless authentication for your users in the Duo Passwordless documentation.
Authenticators Policy Settings
Risk-Based Factor Selection
Available in: Duo Advantage and Duo Premier
Duo’s Risk-Based Authentication automatically detects and mitigates commonly known attack patterns and high-risk anomalies to provide a higher level of security without compromising end-user experience.
The Risk-based Factor Selection policy setting enables detection and analysis of authentication requests and adaptively enforces the most-secure factors in order to highlight risk as well as adapt its understanding of normal user behavior.
Duo Risk-Based Factor Selection works with existing authentication methods policy for web-based applications that show the Duo Universal Prompt and for the Duo Auth API application (meaning any client app that uses the named "Duo Auth API" application). When we identify a risky logon attempt for a user we restrict the authentication methods allowed for that user until they successfully authenticate with one of the permitted secure factors.
The default setting enables Risk-Based Factor Selection with a six-character verification code.
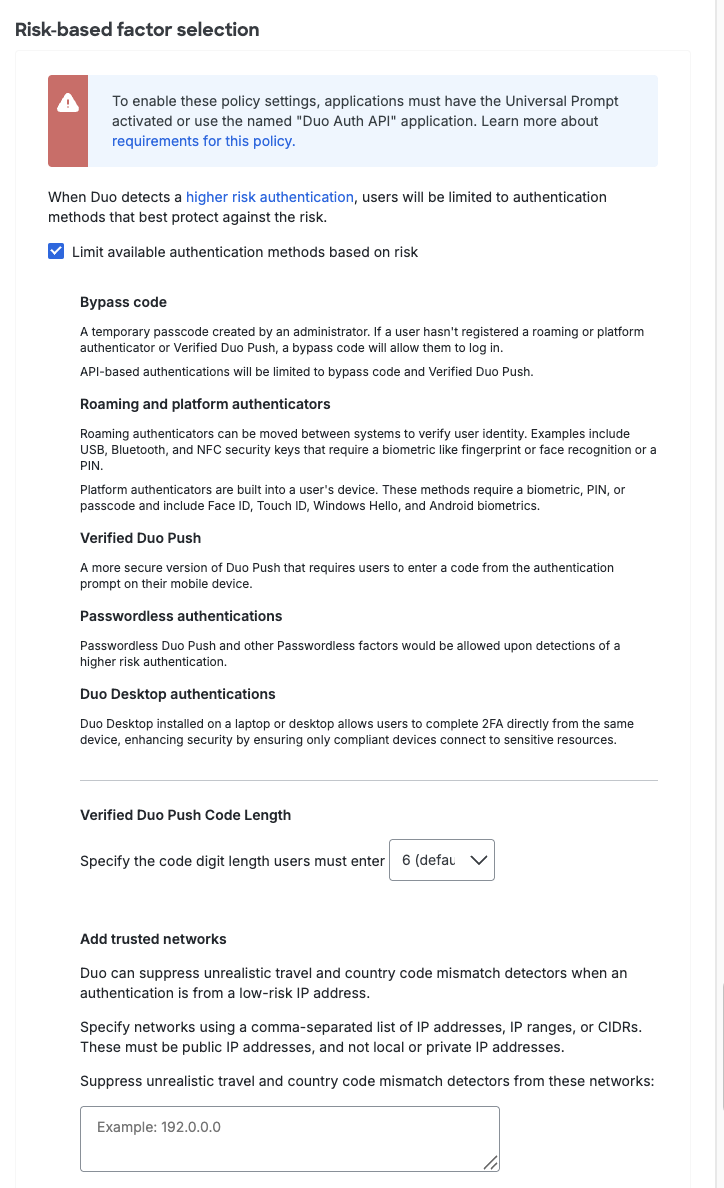
Expand Risk-based factor selection data (last 30 days) in the policy editor for recent users' restricted authentications to help you make risk-based factor selection policy decisions.
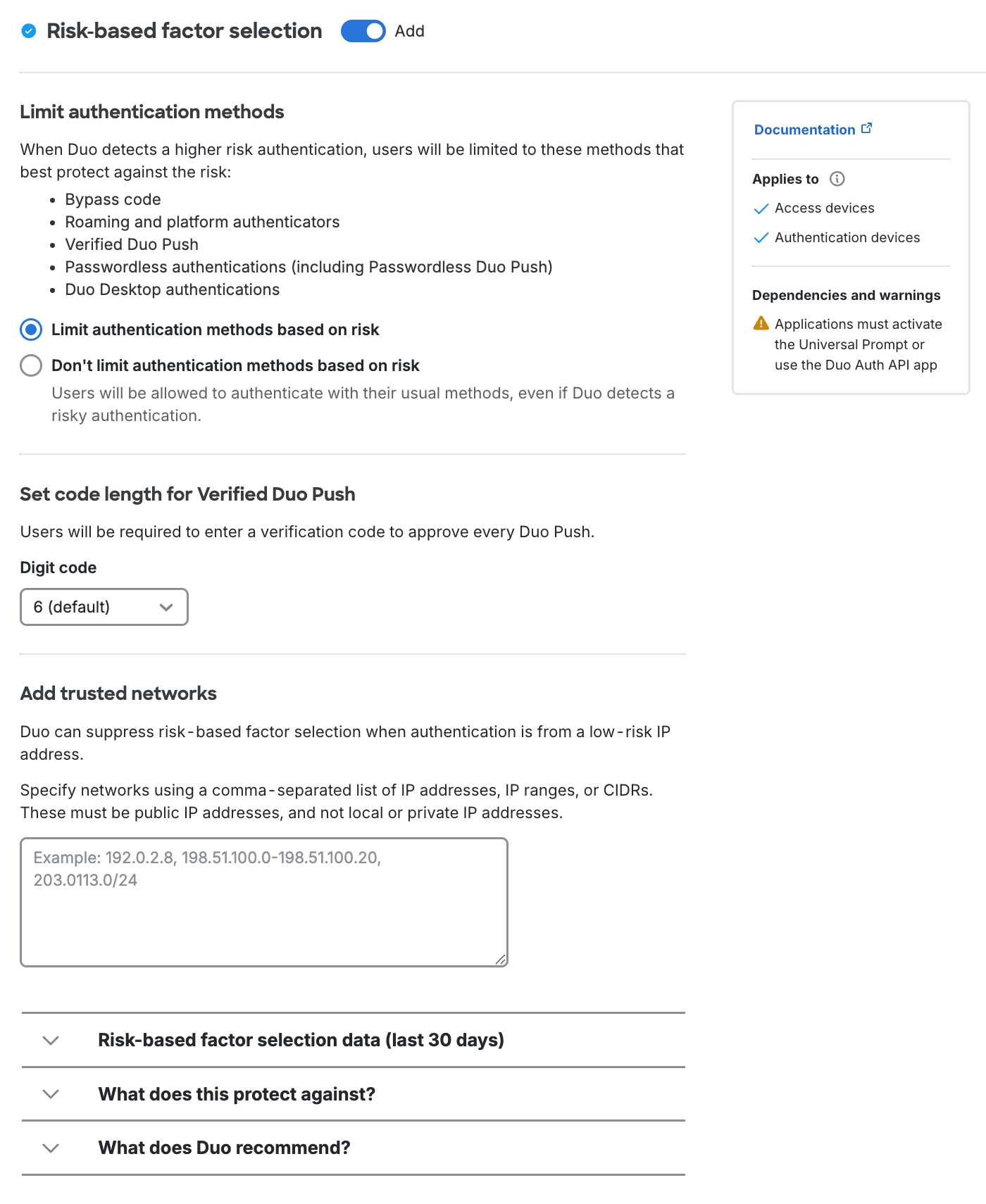
See our full Risk-Based Authentication documentation for more information and step-by-step deployment instructions.
Authentication Methods
Available in: Duo Essentials, Duo Advantage, and Duo Premier
Duo offers a variety of ways that users can receive their second authentication factor: one-tap authentication with a WebAuthn passkey or Duo Push, a passcode sent via SMS, an automated voice call, and so on (see our detailed explanation of all authentication methods). Unless otherwise noted, all authentication methods options are available to Duo Essentials, Duo Advantage, and Duo Premier editions, including those for Duo Passwordless and verified Duo Push.
Phone calls and SMS passcode text messages consume telephony credits. Check the rate card to see the credit costs for users in different locations.
If you disallow an authentication method in a policy, this also prevents self-enrollment of that method. You can create a custom policy for the self-service portal to allow users to enroll different authentication methods than the ones used to authenticate to the application.
Be aware that if you enable the Risk-based factor selection policy option, this may block some of the authentication methods you allow here for use in a higher-risk authentication scenario. See the full Risk-Based Factor Selection documentation to learn which authentication methods will be permitted or blocked.
2FA Authentication methods policy options:
-
Platform authenticator (WebAuthn): Users interact with the methods integrated into their device hardware and operating system, like the Touch ID fingerprint reader on a Mac, to authenticate. Default setting: enabled for Touch ID, Face ID, Windows Hello, and Android biometric.
-
Roaming authenticator (WebAuthn): Users tap an FIDO2-compliant WebAuthn security key to authenticate. Default setting: enabled for USB, Bluetooth or NFC security keys.
-
Require user verification with PIN or biometric. With this option enabled users must perform the extra step of PIN or biometric verification as supported by their security key model in both the Universal Prompt and the traditional Duo Prompt. The Duo device enrollment process prompts users to set a PIN or configure biometrics if it hasn't already been done for that security key. Default setting: off.
Users who registered a compatible security key before this policy setting was enabled may need to remove and re-register their security key to add user verification support. Please see article 8091 in the Duo Knowledge Base for more details about the effects of enabling this policy setting.
This option blocks use of roaming authenticators which do not support FIDO2 user verification, so if any of your users have older security keys you should either exclude them from effective policies requiring user verification, allow an alternative authentication method available to those users in the effective policy, or issue them updated security keys that do support user verification.
-
-
Duo Push: Duo's service sends an authentication request to the Duo Mobile iOS or Android app for the user to approve or deny. Default setting: enabled.
-
Require a Verified Duo Push: Users can approve a Duo Push by entering a numeric code or through proximity verification, depending on the application being accessed.
Note: If a user's browser does not meet the requirements for the Universal Prompt and therefore falls back to traditional Duo Prompt, Verified Duo Push authentication is not enforced for that user login attempt because Verified Duo Push is not supported in the traditional Duo Prompt. Ensure your users have access to supported, up-to-date browsers to avoid this fallback scenario.
Default settings:
- For Duo Essentials customers, "Require users to enter a verification code" is enabled and set to 3 digits.
- For Duo Advantage and Duo Premier customers, all Verified Duo Push options are off.
Verified Duo Push options:
-
Require users to enter a verification code - Users must enter a numeric code in the Duo Universal Prompt, in Duo Authentication for Windows Logon 4.3.16 and later, and in the UI of an Auth API client application before approving the Duo Push request. No effect if you apply this selection to applications that do not show the Duo Universal Prompt, Duo Authentication for Windows Logon version 4.3.1 or earlier, or Auth API applications with clients not updated to support verification codes.
-
Autofill the verification code with Bluetooth - Users have the option to automatically fill their verification codes with Bluetooth if their mobile device is near their access device. Only available for Duo applications which feature the Duo Universal Prompt.
-
Require proximity verification with Bluetooth - Users must have their mobile device near their access device to approve the Duo Push request. Only available for Duo applications which feature the Duo Universal Prompt. Users will need to choose a different authentication method to log in if you apply this selection to applications that do not show the Duo Universal Prompt.
-
-
Duo Desktop authentication: Duo's service sends an authentication request for the user to approve or deny to the Duo Desktop application installed on the computer accessing the Duo Universal Prompt application. Default setting: off.
-
Duo Mobile passcodes: Users authenticate with a passcode generated in the Duo Mobile app. Default setting: off.
-
SMS passcodes: Users receive a text message with a Duo passcode that they use to authenticate. Default setting: enabled.
Duo attempts to send the SMS passcode once. If you would like Duo to retry sending the passcode text upon encountering a messaging error then enable the Automatically send a new passcode up to 3 times if delivery fails. option. -
Phone callback: Users receive a phone call from Duo and press a digit to approve the login request. Default setting: off.
-
Hardware tokens: Users enter passcodes generated by a physical device issued by your organization. Default setting: enabled.
-
Bypass code: Users enter a numeric bypass code generated by a Duo administrator. This is useful when no other previously-registered authentication methods are available. Default setting: enabled.
If you choose to enable phone calls as an authentication method, consider applying some additional policy controls (such as restricting User Location to your expected countries) or reducing your max credits per action telephony setting to only the credit amount needed for phone calls to your users' expected locations to avoid telephony misuse, especially if you've enabled the self-service portal for any of your applications.
WebAuthn security keys and passkeys can be used with the browser-based Duo Prompt when accessing applications. Please refer to Passkey Browser Support to see the minimum browser versions supported.
To restrict or allow authentication methods, just choose from the available options.
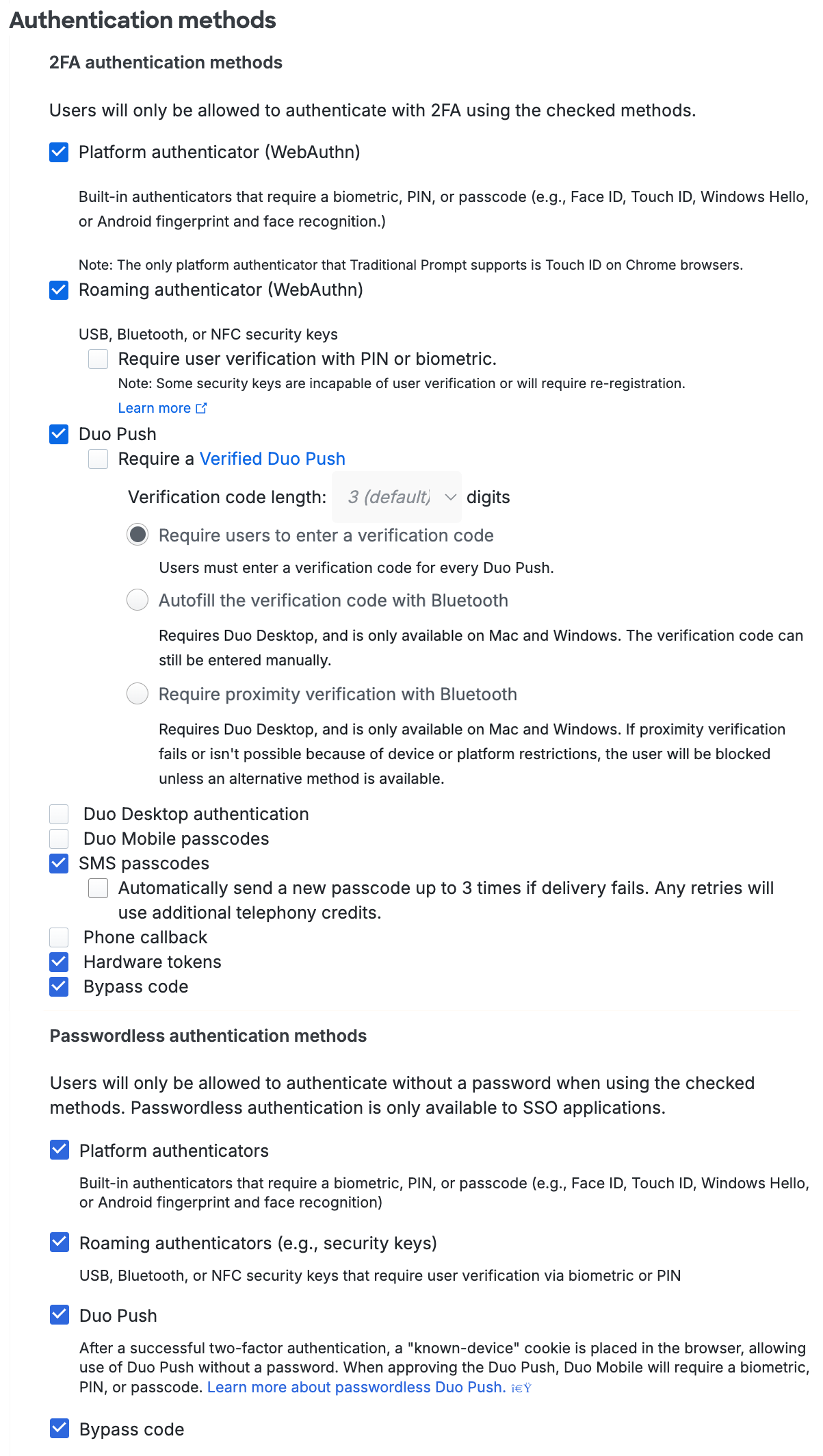
Passwordless Authentication Methods
Duo Passwordless has separate authentication methods policy settings for passwordless authentication methods. Customers who sign up in June 2025 or later will have the passwordless methods enabled in the Global Policy by default, as well as in any new custom policies created. If you started your Duo account before June 2025, then the passwordless authentication methods won't be enabled in an existing policy until you enable them. If you create a new policy or revert your Global Policy to default settings, all passwordless authentication methods will be enabled by default in those policies.
Enabling any of the passwordless methods in a policy permits use of passwordless authentication for any Duo Single Sign-On application subject to that policy. The passwordless authentication methods settings have no effect for non-SSO applications, as those applications do not support passwordless logins today.
The authentication method options for passwordless logins are:
-
Platform Authenticators: This enables end-user authentication using biometric sensors built into their devices, such as Touch ID or Face ID on Apple devices, Windows Hello on Windows 10 and 11 systems, or Android biometrics. Enabling platform authenticators prompts just those users with compatible access devices to register a passwordless authenticator when they log in.
-
Roaming Authenticators: This enables end-user authentication using FIDO2-compliant WebAuthn security keys, like those from Yubico or Feitian. Enabling roaming authenticators prompts all users to register a passwordless authenticator whenever they log in.
-
Duo Push: This enables end-user authentication by approval of a login request pushed to Duo Mobile on a user's Android or iOS device. Duo Push authentication for Duo Passwordless is enabled via a browser cookie for the specific browser used to log in to a protected application from a given access device. When the user approves a Duo Push request for passwordless login, they must perform biometric or PIN/passcode verification while they approve the login request. Users may also need to enter a verification code into Duo mobile to complete the passwordless Duo Push login depending on the known and trusted status of the browser used.
-
Bypass code: Users enter a numeric bypass code generated by a Duo administrator. This is useful when no other previously-registered passwordless authentication methods are available. Default setting: enabled.
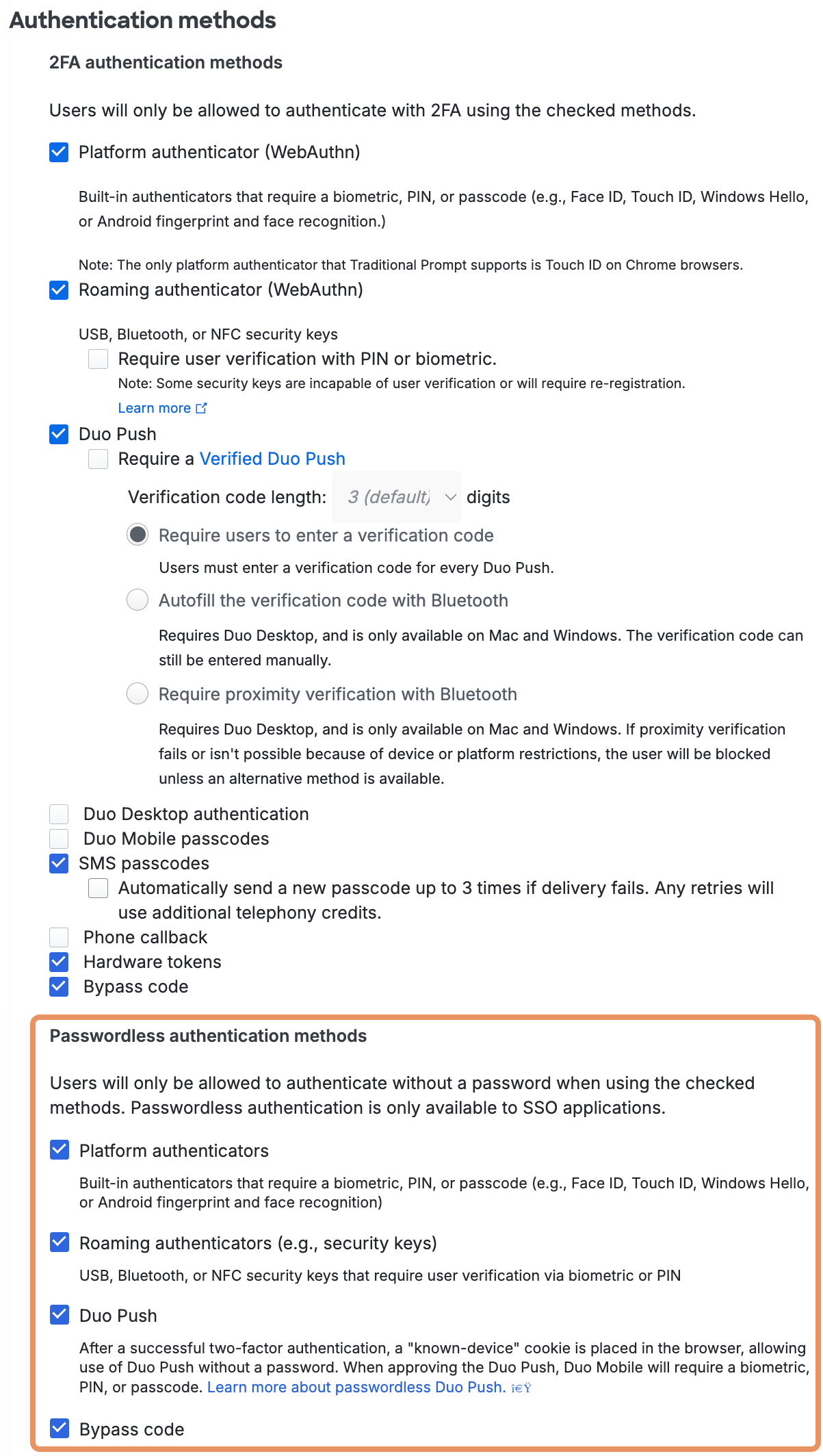
Learn more about Duo Passwordless and passwordless authentication for your users in the Duo Passwordless documentation.
Duo's recommended secure authentication methods are highlighted in the policy editor. Expand Authentication methods data (last 30 days) at the bottom of the policy editor for methods used by recent users' authentications to help you make authentication method policy decisions.
Second-factor authentication (2FA) policy options:
-
Platform authenticator (passkey / WebAuthn): Users interact with the methods integrated into their device hardware and operating system, like the Touch ID fingerprint reader on a Mac, to authenticate. Default setting: enabled for Touch ID, Face ID, Windows Hello, and Android biometric.
-
Roaming authenticator (passkey / WebAuthn): Users tap an FIDO2-compliant WebAuthn security key to authenticate. Default setting: enabled for USB, Bluetooth or NFC security keys.
-
Require user verification with a PIN or biometric. With this option enabled users must perform the extra step of PIN or biometric verification as supported by their security key model in both the Universal Prompt and the traditional Duo Prompt. The Duo device enrollment process prompts users to set a PIN or configure biometrics if it hasn't already been done for that security key. Default setting: off.
Users who registered a compatible security key before this policy setting was enabled may need to remove and re-register their security key to add user verification support. Please see article 8091 in the Duo Knowledge Base for more details about the effects of enabling this policy setting.
This option blocks use of roaming authenticators which do not support FIDO2 user verification, so if any of your users have older security keys you should either exclude them from effective policies requiring user verification, allow an alternative authentication method available to those users in the effective policy, or issue them updated security keys that do support user verification.
-
-
Duo Mobile Push: Duo's service sends an authentication request to the Duo Mobile iOS or Android app for the user to approve or deny. Default setting: enabled.
-
Require a Verified Duo Push: Users can approve a Duo Push by entering a numeric code or through proximity verification, depending on the application being accessed.
Note: If a user's browser does not meet the requirements for the Universal Prompt and therefore falls back to traditional Duo Prompt, Verified Duo Push authentication is not enforced for that user login attempt because Verified Duo Push is not supported in the traditional Duo Prompt. Ensure your users have access to supported, up-to-date browsers to avoid this fallback scenario.
Default settings:
- For Duo Essentials customers, "Require users to enter a verification code" is enabled and set to 3 digits.
- For Duo Advantage and Duo Premier customers, all Verified Duo Push options are off.
Verified Duo Push options:
-
Require users to enter a verification code - Users must enter a numeric code in the Duo Universal Prompt, in Duo Authentication for Windows Logon 4.3.16 and later, and in the UI of an Auth API client application before approving the Duo Push request. No effect if you apply this selection to applications that do not show the Duo Universal Prompt, Duo Authentication for Windows Logon version 4.3.1 or earlier, or Auth API applications with clients not updated to support verification codes.
-
Autofill the verification code with Bluetooth when possible - Users have the option to automatically fill their verification codes with Bluetooth if their mobile device is near their access device. Only available for Duo applications which feature the Duo Universal Prompt.
-
Require proximity verification with Bluetooth - Users must have their mobile device near their access device to approve the Duo Push request. Only available for Duo applications which feature the Duo Universal Prompt. Users will need to choose a different authentication method to log in if you apply this selection to applications that do not show the Duo Universal Prompt.
-
-
Duo Desktop authentication: Duo's service sends an authentication request for the user to approve or deny to the Duo Desktop application installed on the computer accessing the Duo Universal Prompt application. Default setting: off.
-
Duo Mobile passcode: Users authenticate with a passcode generated in the Duo Mobile app. Default setting: off.
-
SMS passcode: Users receive a text message with a Duo passcode that they use to authenticate. Default setting: enabled. We recommend disabling SMS if not needed.
Duo attempts to send the SMS passcode once. If you would like Duo to retry sending the passcode text up to three times upon encountering a messaging error then enable the Send new passcodes when delivery fails option. -
Phone callback: Users receive a phone call from Duo and press a digit to approve the login request. Default setting: off.
-
Hardware tokens: Users enter passcodes generated by a physical device issued by your organization. Default setting: enabled.
-
Bypass code: Users enter a numeric bypass code generated by a Duo administrator. This is useful when no other previously-registered authentication methods are available. Default setting: enabled.
If you choose to enable phone calls as an authentication method, consider applying some additional policy controls (such as restricting User Location to your expected countries) or reducing your max credits per action telephony setting to only the credit amount needed for phone calls to your users' expected locations to avoid telephony misuse, especially if you've enabled the self-service portal for any of your applications.
WebAuthn security keys and passkeys can be used with the browser-based Duo Prompt when accessing applications. Please refer to Passkey Browser Support to see the minimum browser versions supported.
Passwordless authentication in SSO policy options:
Duo Passwordless has separate authentication methods policy settings for passwordless authentication methods available when logging into Duo SSO applications. Customers who sign up in June 2025 or later will have the passwordless methods enabled in the Global Policy by default, as well as in any new custom policies created. If you started your Duo account before June 2025, then the passwordless authentication methods won't be enabled in an existing policy until you enable them. If you create a new policy or revert your Global Policy to default settings, all passwordless authentication methods will be enabled by default in those policies.
Enabling any of the passwordless methods in a policy permits use of passwordless authentication for any Duo Single Sign-On application subject to that policy. The passwordless authentication methods settings have no effect for non-SSO applications, as those applications do not support passwordless logins today.
The authentication method options for passwordless logins in SSO are:
-
Platform authenticator (passkey / WebAuthn): This enables end-user authentication using biometric sensors built into their devices, such as Touch ID or Face ID on Apple devices, Windows Hello on Windows 10 and 11 systems, or Android biometrics. Enabling platform authenticators prompts just those users with compatible access devices to register a passwordless authenticator when they log in.
-
Roaming authenticator (passkey / WebAuthn): This enables end-user authentication using FIDO2-compliant WebAuthn security keys, like those from Yubico or Feitian. Enabling roaming authenticators prompts all users to register a passwordless authenticator whenever they log in.
-
Duo Mobile Push: This enables end-user authentication by approval of a login request pushed to Duo Mobile on a user's Android or iOS device. Duo Push authentication for Duo Passwordless is enabled via a browser cookie for the specific browser used to log in to a protected application from a given access device. When the user approves a Duo Push request for passwordless login, they must perform biometric or PIN/passcode verification while they approve the login request. Users may also need to enter a verification code into Duo mobile to complete the passwordless Duo Push login depending on the known and trusted status of the browser used.
-
Bypass code: Users enter a numeric bypass code generated by a Duo administrator. This is useful when no other previously-registered passwordless authentication methods are available. Default setting: enabled.
Learn more about Duo Passwordless and passwordless authentication for your users in the Duo Passwordless documentation.
To restrict or allow authentication methods, just choose from the available options.
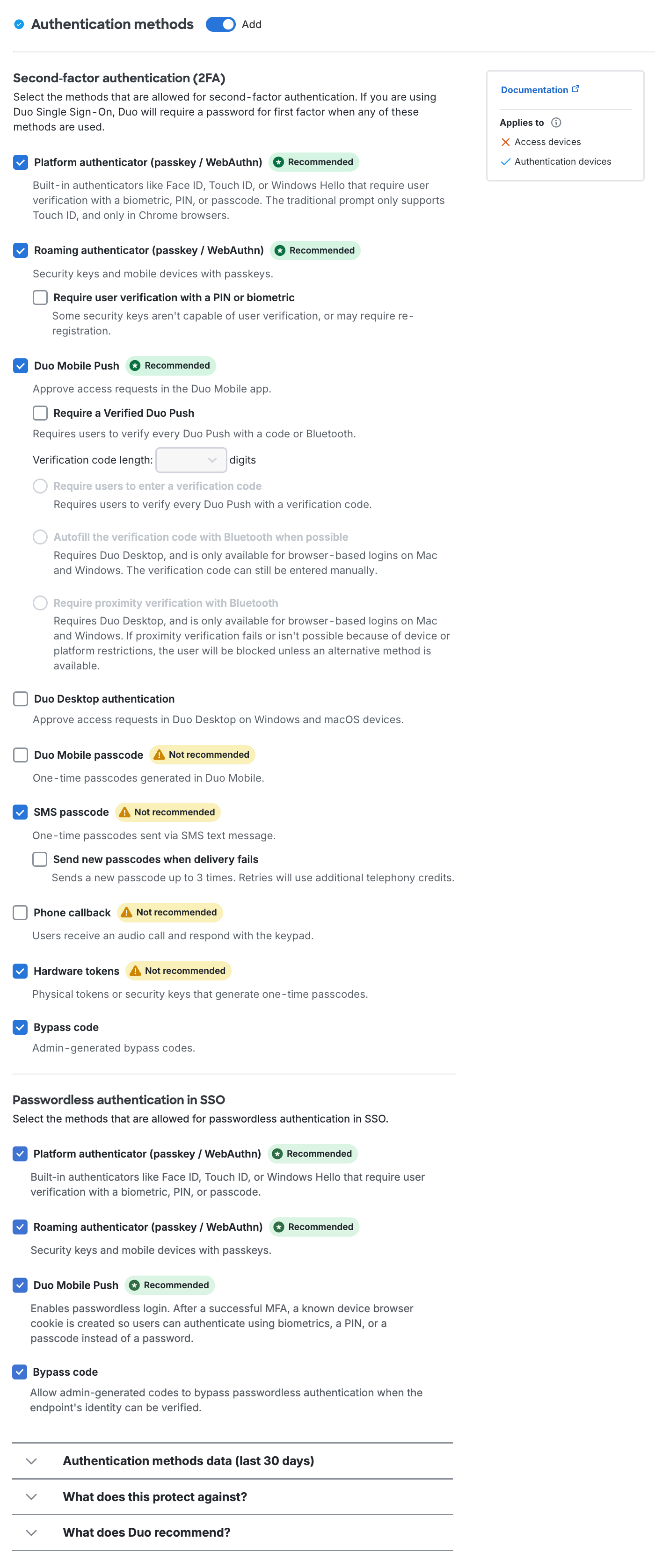
For example, when "Phone callback" is deselected then phone call no longer appears as an option in the traditional Duo Prompt. A user could still opt to send an SMS passcode after clicking Enter a Passcode.
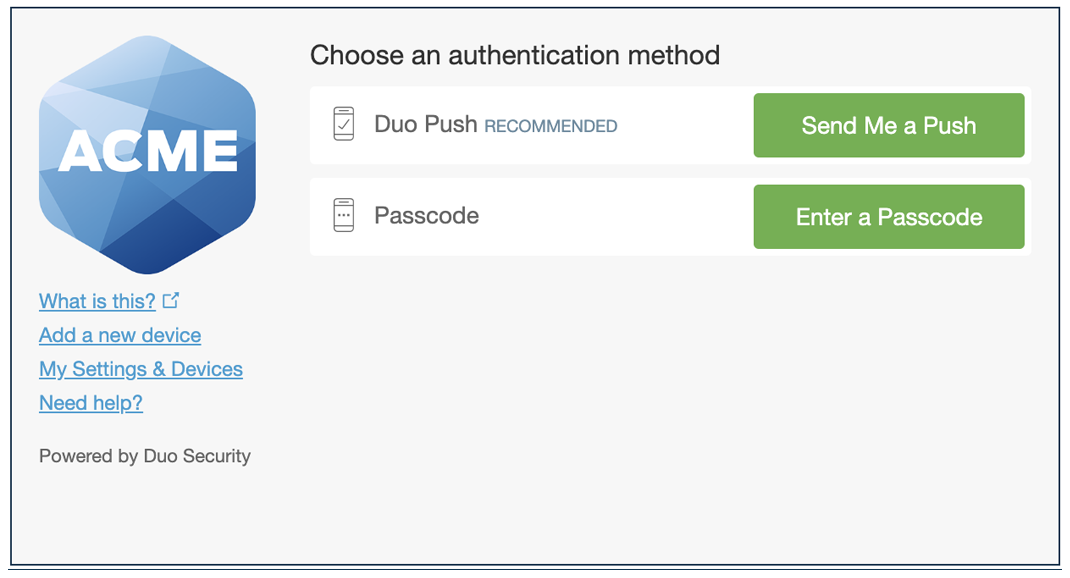
In the Duo Universal Prompt, phone call isn't in the list of available login options. Sending a passcode to the phone via text message remains available.
If all methods are deselected, then only bypass codes may be used to authenticate.
Note: If Duo Push is disabled but Duo Mobile passcode is enabled then user will be able to use Duo Mobile to generate a one-time passcode (much as they might with a hardware token). You can prevent users from using the app to generate one-time passcodes by not enabling the Duo Mobile passcodes authentication method.
If you permit use of WebAuthn authentication methods in the traditional Duo Prompt, Duo recommends configuring allowed hostnames for your protected applications before onboarding your end-users.
The Duo Universal Prompt has built-in protection from unauthorized domains so this setting does not apply.
Verified Duo Push
The verification code option for Duo Push provides additional security against push harassment and fatigue attacks by asking the user to enter a verification code while approving a Duo Push authentication request. It also provides improved fraud reporting from end users by directing them toward the fraud report option in Duo Mobile when they receive unexpected Duo Push login requests.
Users will see a numeric code three to six digits in length (based on your preference) in the Duo prompt when you have push verification enabled in the effective policy for these supported applications. They must enter this code into Duo Mobile to approve the Duo Push request on their authentication device. This ensures users cannot accidentally approve login requests when they aren't actively logging in to the application.
Verified Duo Push Login Experience in Universal Prompt and Duo Mobile
Verified Duo Push in the Duo Windows Prompt
Enable numeric code verification for Duo Push by selecting the Require a Verified Duo Push and Require users to enter a verification code options shown under the Duo Mobile Push authentication method. When enabling this option you may select a verification code length from three to six digits (default: 3).
Verified Duo Push requires:
- A supported Duo application:
- Applications that show the Duo Universal Prompt.
- Duo Authentication for Windows Logon v4.3.16 and later.
- Duo Unix v2.2.0 and later.
- An Auth API client application updated to support Duo Verified Push.
- A supported version of Duo Mobile installed and activated on their mobile device:
- Duo Mobile 4.16.0 or later on Android 8 or later.
- Duo Mobile 4.17.0 or later on iOS 16 or later.
Users with an older version of Duo Mobile receive a Duo Push request without the code entry field. When they try to approve then the login fails and they see a message instructing them to update their software. If your users can't update their devices then make sure you allow another authentication method which they can use instead.
Verified Duo Push has no effect in the traditional Duo Prompt. Duo Authentication for Windows Logon 4.3.1 and earlier, Duo for macOS, or Duo's other non-browser applications like RADIUS or LDAP applications that use Duo Authentication Proxy, Duo Unix, etc.
In addition, trusted endpoint verification of iOS and Android devices with Duo Mobile uses the standard Duo Push approval process and will not prompt for a Duo Push verification code.
The Authentication Log shows when a verification code was used to approve a Duo push request, when an incorrect code was entered, and when a user denied the push request as a mistake or fraud. If the response indicated the login request was suspicious, Duo sends an email notification to the administrators specified in the Alert email global setting.
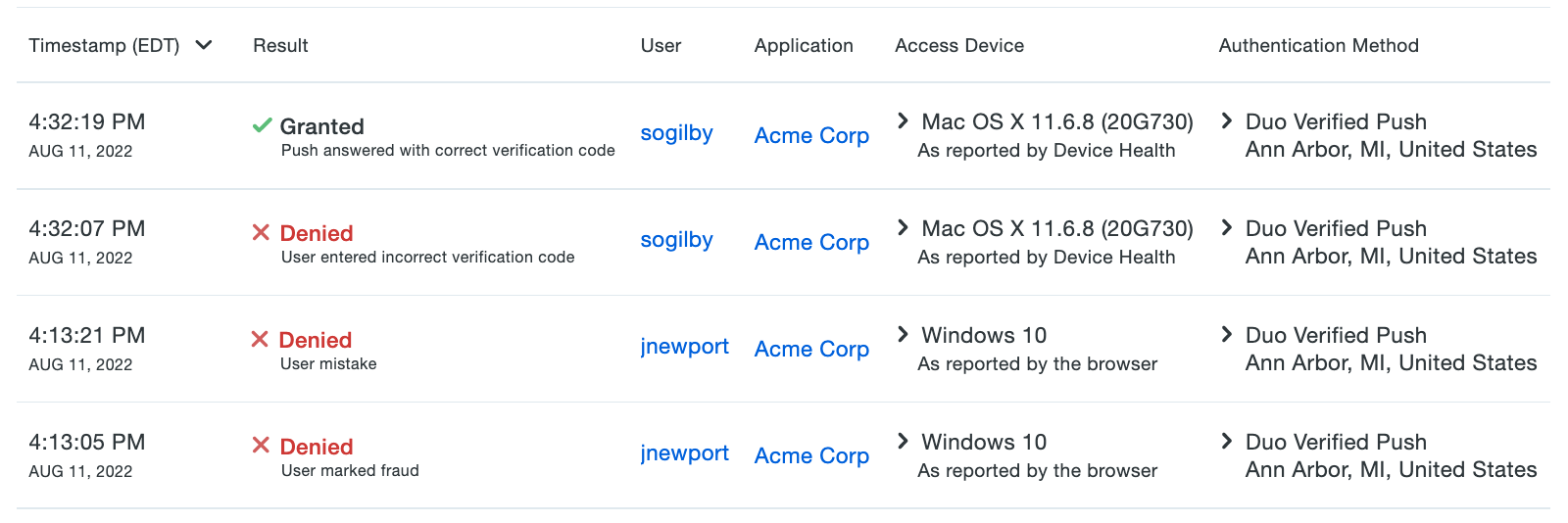
Verified Duo Push with Bluetooth Autofill
Verified Duo Push with Bluetooth autofill utilizes Bluetooth Low Energy (BLE) technology to automatically fill in the verification code in Duo Mobile during a Verified Duo Push from a Duo Universal Prompt application. It requires Duo Desktop to be installed and the user to be near their access device for the Bluetooth connection to automatically transmit the verification code.
Users need to allow Bluetooth for Duo Desktop on the access device and Duo Mobile on the device used to approve login requests in order to experience the code being automatically filled. If users don’t allow Bluetooth on both devices, they will continue to log in by manually entering the code shown in the prompt. We do not prompt for Bluetooth permissions for a regular Duo Push.
If you have applied a risk-based factor selection policy, users will be asked to grant Bluetooth permissions on both Duo Mobile and Duo Desktop during a step-up Verified Duo Push authentication. If they deny or skip allowing permissions, they can continue logging in after manually entering the code for the Verified Duo Push.
The Authentication Log shows "Push answered with Bluetooth" when Bluetooth was used to autofill a verification code.
Verified Duo Push with Bluetooth autofill does not work with applications that show the traditional Duo Prompt, Duo Authentication for Windows Logon, Duo Authentication for macOS, or Duo's other non-browser applications like RADIUS or LDAP applications that use Duo Authentication Proxy, Duo Unix, etc.
Verified Duo Push with Bluetooth autofill requires:
- Supported Duo applications which feature the Duo Universal Prompt.
- Mobile devices running Android 12+ or iOS 16+.
- Duo Mobile 4.72.0 or later installed on Android and iOS devices.
- Access devices running macOS 11+ or Windows 10 build 1803+.
- Duo Desktop 6.13.0/6.13.0.0 or later installed on Windows and macOS clients.
- Bluetooth v4.0 and later enabled on Windows, macOS, and mobile devices.
- Supported Bluetooth adapters tested by Duo (only required for computers that don't have Bluetooth built-in):
- Avantree DG45 Bluetooth USB adapter
- Ugreen CM656 Bluetooth adapter
- TP Link UP500
- Other Bluetooth adapter models not tested by Duo may work.
- Supported Bluetooth adapters tested by Duo (only required for computers that don't have Bluetooth built-in):
- Edit your global policy or apply a custom group or application policy with these policy settings:
- Require Duo Desktop: Selected for macOS and/or Windows.
- Authentication methods: Enable Autofill the verification code with Bluetooth when possible.
See the full Verified Duo Push with Bluetooth autofill experience in the Duo User Guide for iOS and Android.
Duo Mobile Proximity Verification
Duo Mobile proximity verification utilizes Bluetooth Low Energy (BLE) technology to verify a user's mobile device is near their access device during authentication to a Duo Universal Prompt application. It requires Duo Desktop to be installed on the user's macOS or Windows access device.
Users need to allow Bluetooth for both Duo Desktop on the access device and Duo Mobile on the device used to approve login requests. If users don’t allow Bluetooth on both devices, they will need to choose a different authentication method to log in.
If you have applied a risk-based factor selection policy, users will be asked to grant Bluetooth permissions on both Duo Mobile and Duo Desktop during a step-up Verified Duo Push authentication. If a user denies or skips allowing permissions, they will need to choose a different step-up authentication method to log in.
The Authentication Log shows "Push answered with Bluetooth" when proximity verification is used.
Duo Mobile Proximity Verification does not work with applications that show the traditional Duo Prompt, Duo Authentication for Windows Logon, Duo Authentication for macOS, or Duo's other non-browser applications like RADIUS or LDAP applications that use Duo Authentication Proxy, Duo Unix, etc.
Duo Mobile proximity verification requires:
- Supported Duo applications which feature the Duo Universal Prompt.
- Mobile devices running Android 12+ or iOS 16+.
- Duo Mobile 4.81.0 or later installed on Android and iOS devices.
- Access devices running macOS 11+ or Windows 10 build 1803+.
- Duo Desktop 6.13.0/6.13.0.0 or later installed on Windows and macOS clients.
- Bluetooth v4.0 and later enabled on Windows, macOS, and mobile devices.
- Supported Bluetooth adapters tested by Duo (only required for computers that don't have Bluetooth built-in):
- Avantree DG45 Bluetooth USB adapter
- Ugreen CM656 Bluetooth adapter
- TP Link UP500
- Other Bluetooth adapter models not tested by Duo may work.
- Supported Bluetooth adapters tested by Duo (only required for computers that don't have Bluetooth built-in):
- Edit your global policy or apply a custom group or application policy with these policy settings:
- Require Duo Desktop: Selected for macOS and/or Windows.
- Authentication methods: Enable Require proximity verification with Bluetooth.
See the full Duo Mobile proximity verification experience in the Duo User Guide for iOS and Android.
Duo Mobile App
Available in: Duo Advantage and Duo Premier
The Duo Mobile smartphone app is an essential part of most organizations' Duo deployment. This policy controls which versions of Duo Mobile on iOS and Android are allowed to access your Duo-protected applications while also encouraging users running older versions to update to the latest version.
Encouraging users to update Duo Mobile will show users that they need to update to an approved version instead of blocking access outright. When you block a given Duo Mobile version, then that restriction applies to use of Duo Mobile to authenticate to all Duo-protected applications, not just those that use Duo's browser prompt.
You can choose a minimum allowed version of Duo Mobile. Any versions of Duo Mobile older than that selected won't allow users to approve Duo Push requests or generate passcodes for authentication. You can set a grace period for warning or blocking a user after a version becomes outdated.
Duo defines the "latest" version as the most recently released Duo Mobile version available on iOS or Android. You can see the latest version of Duo Mobile in the policy editor.
Third-party accounts on Duo Mobile are not affected by this policy.
The default setting blocks authentication with Duo Push or app-generated passcodes from Duo Mobile versions less than 3.8.0 with no warning notification to the user.
For customers who signed up before August 2024, your previous Duo Mobile app policy selection will carry over:
- If you had it set to Require up-to-date security patches for Duo Mobile, the policy blocks authentication with Duo Push or app-generated passcodes from Duo Mobile versions less than 3.8.0 with no warning notification to the user.
- If you had it set to Don't require up-to-date security patches for Duo Mobile, all versions of Duo Mobile are allowed with no warnings.
Encourage Users to Update While Still Permitting Access
Enable the Encourage users to update option by picking your minimum allowable Duo Mobile version from the drop-down selector. You can choose to select a specific version, or let Duo determine the most recent available version.
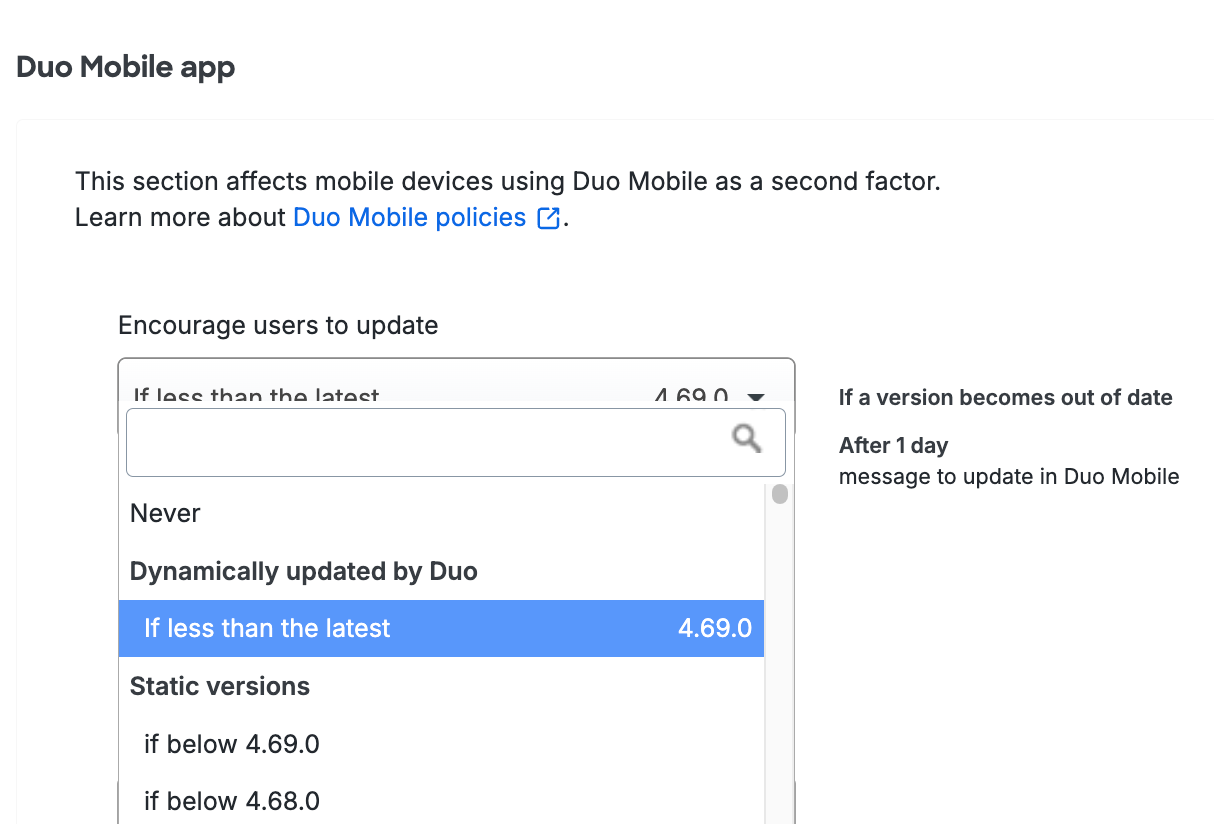
If you select a specific Duo Mobile version, the grace period is set to "Immediately" and users see the warning in Duo Mobile during their next authentication if their Duo Mobile version is lower than the version you selected.
If you select the If less than the latest version, you can select a grace period from the When a version becomes out of date or end of life, encourage to update choices. Setting this to "Immediately" means users see the warning in Duo Mobile during their next authentication if their Duo Mobile version is lower than the version you selected. You can delay the Duo warning for up to 365 days. Look to the right of your selection to see a summary of your new policy setting.
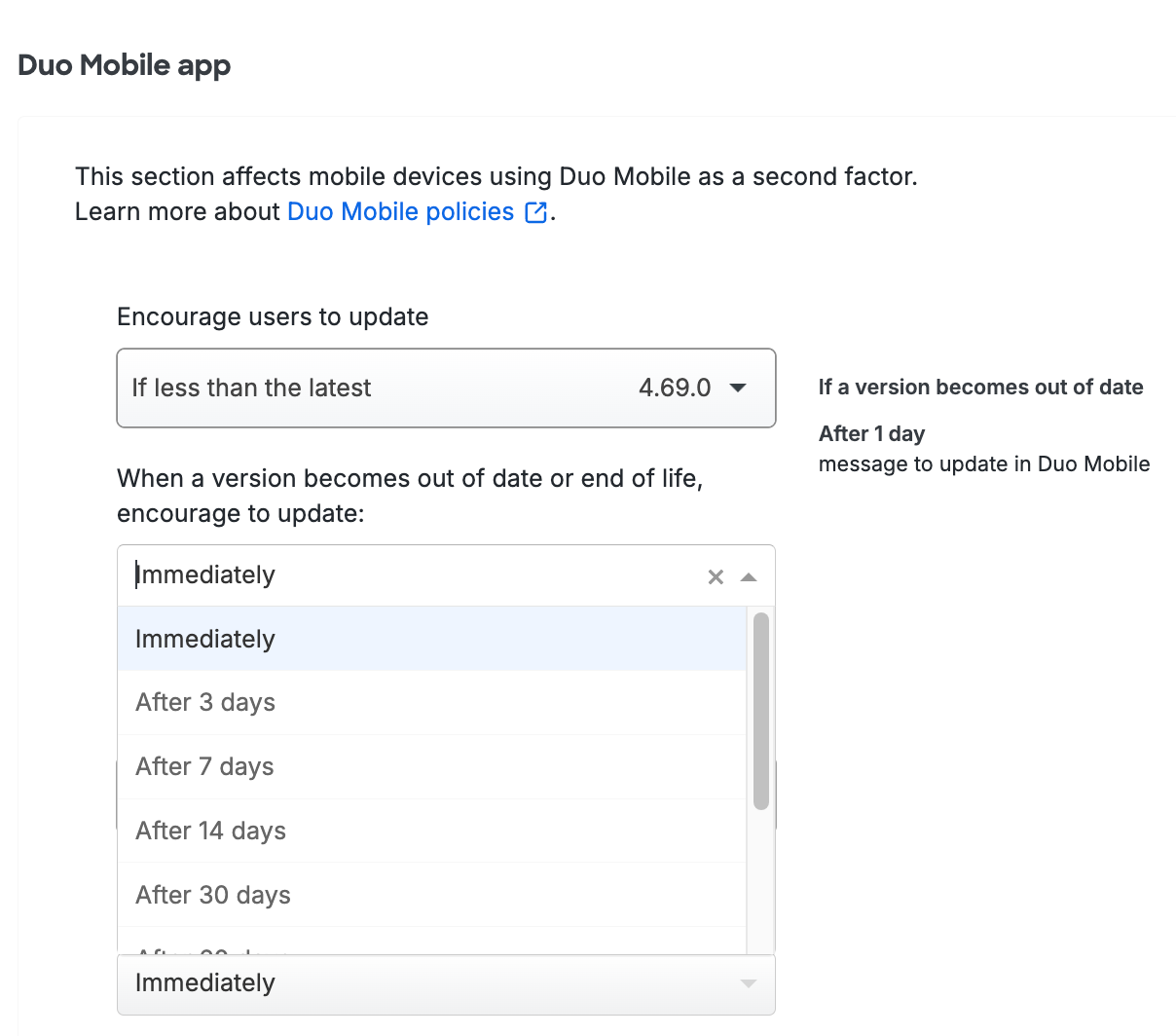
Once configured, Duo shows a notification in Duo Mobile during authentication to your users informing them that they should update if their device is running a Duo Mobile version older than your selection.
Enable the Warn users to update version option by picking your minimum allowable Duo Mobile version from the drop-down selector. You can choose to select a specific version, or let Duo determine the most recent available version.
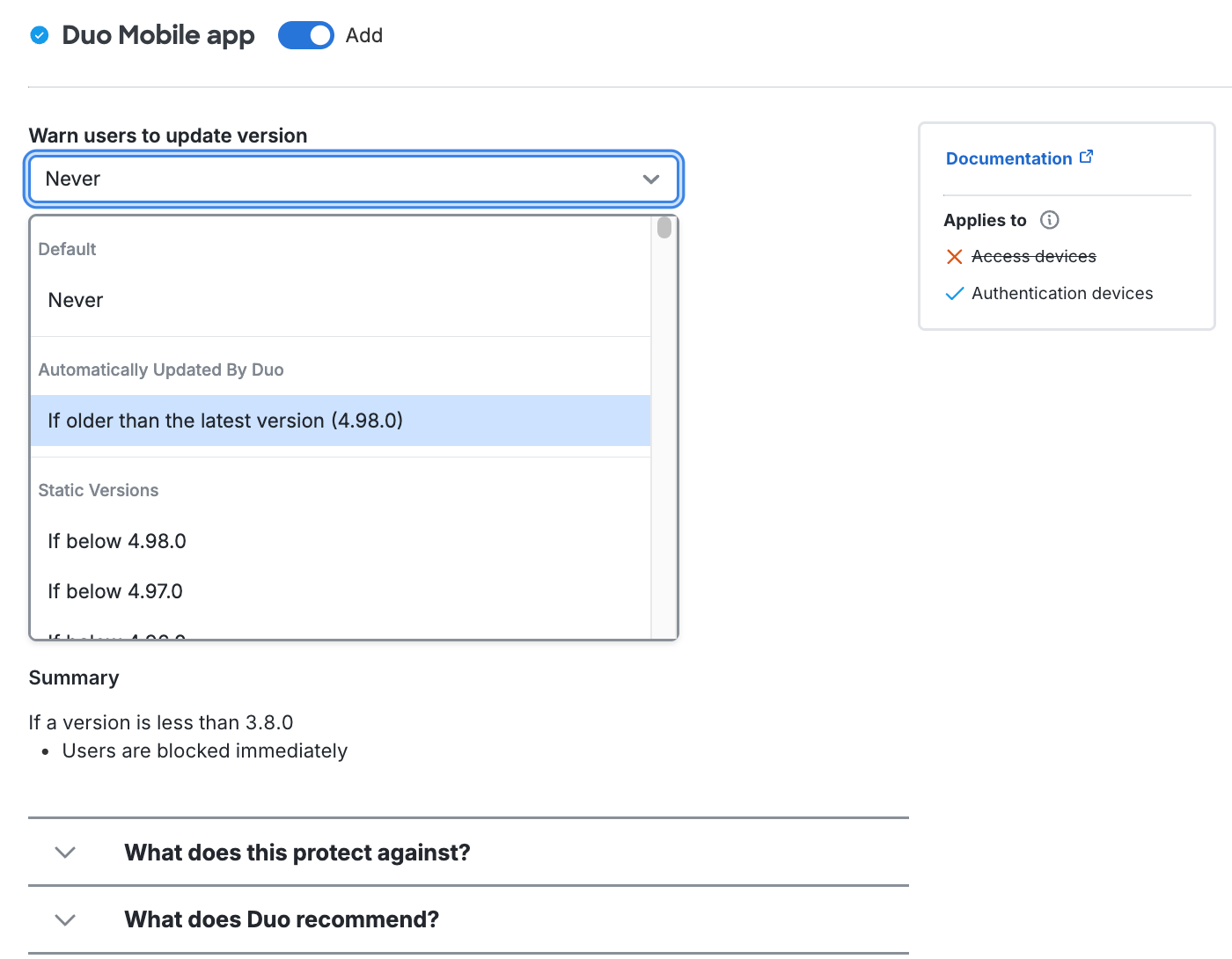
If you select a specific Duo Mobile version, users immediately see the warning in Duo Mobile during their next authentication if their Duo Mobile version is lower than the version you selected.
If you select the If older than the latest version, you can select a grace period from the Schedule choices. Setting this to "Immediately" means users see the warning in Duo Mobile during their next authentication if their Duo Mobile version is lower than the version you selected. You can delay the Duo warning for up to 365 days. Review the summary of your policy selections underneath the configurable options.
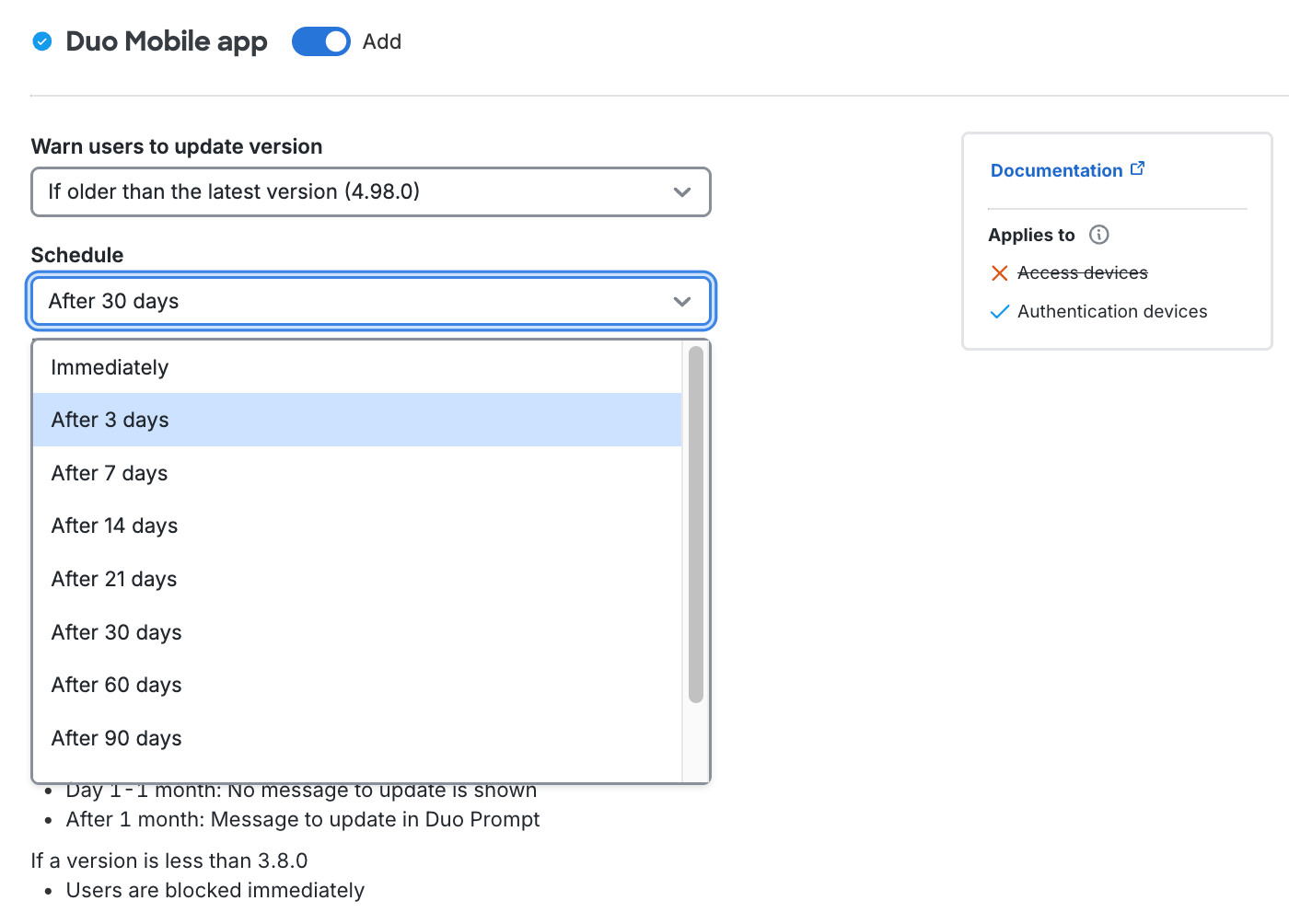
Once configured, Duo shows a notification in Duo Mobile during authentication to your users informing them that they should update if their device is running a Duo Mobile version older than your selection.
Example Scenario
You may choose to encourage users to update if they are not running the latest Duo Mobile release and to start encouraging them "Immediately". A user authenticating with an older version of Duo Mobile sees a message in Duo Mobile indicating their version is out of date.
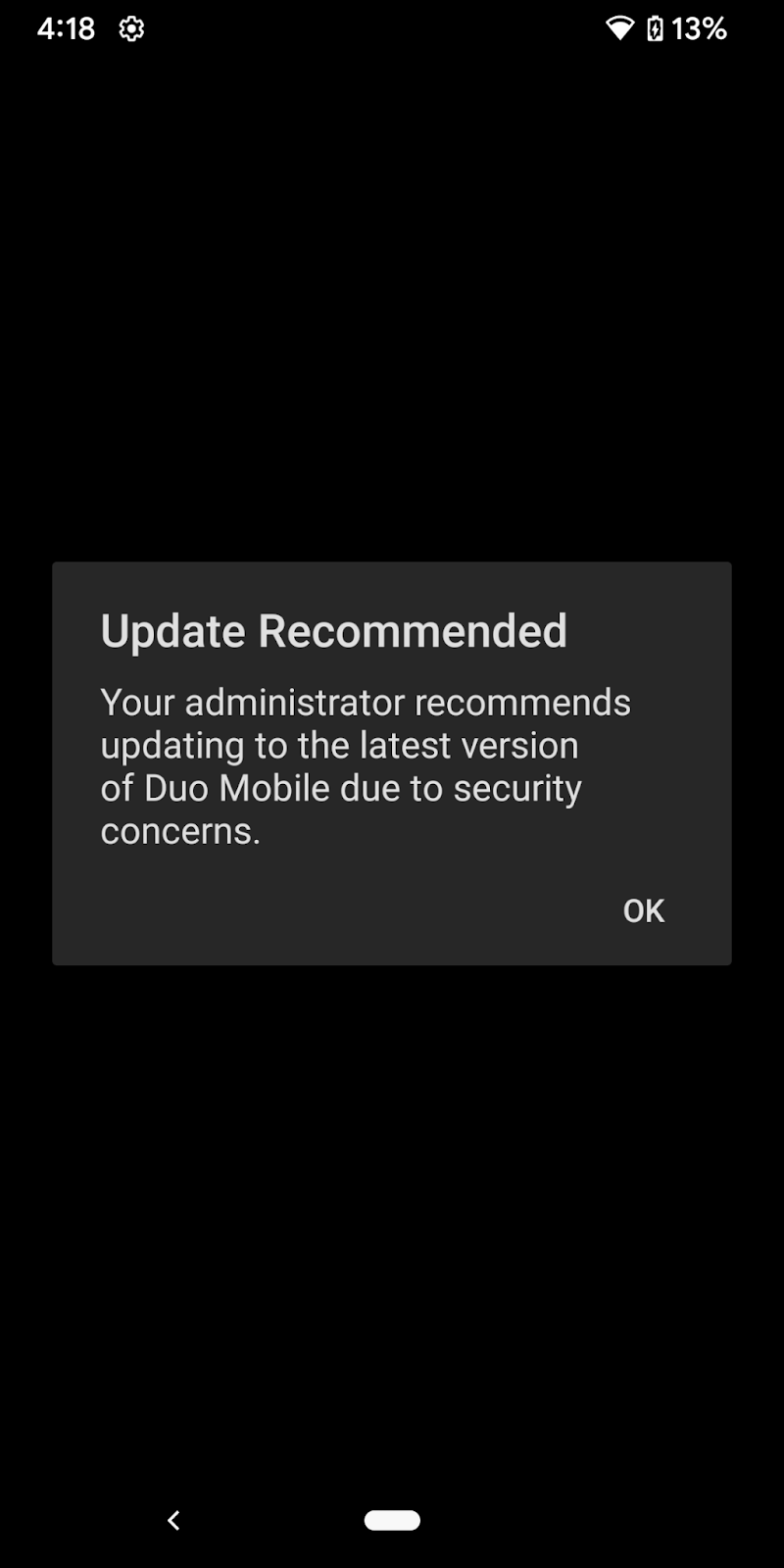
Block Access from Older Versions
Restrict application access to only the versions you've allowed by making a selection in the Block versions option, along with a corresponding grace period for blocking. Blocking any version prevents users from approving Duo Push requests or generating passcodes for authentication with any older versions of Duo Mobile.
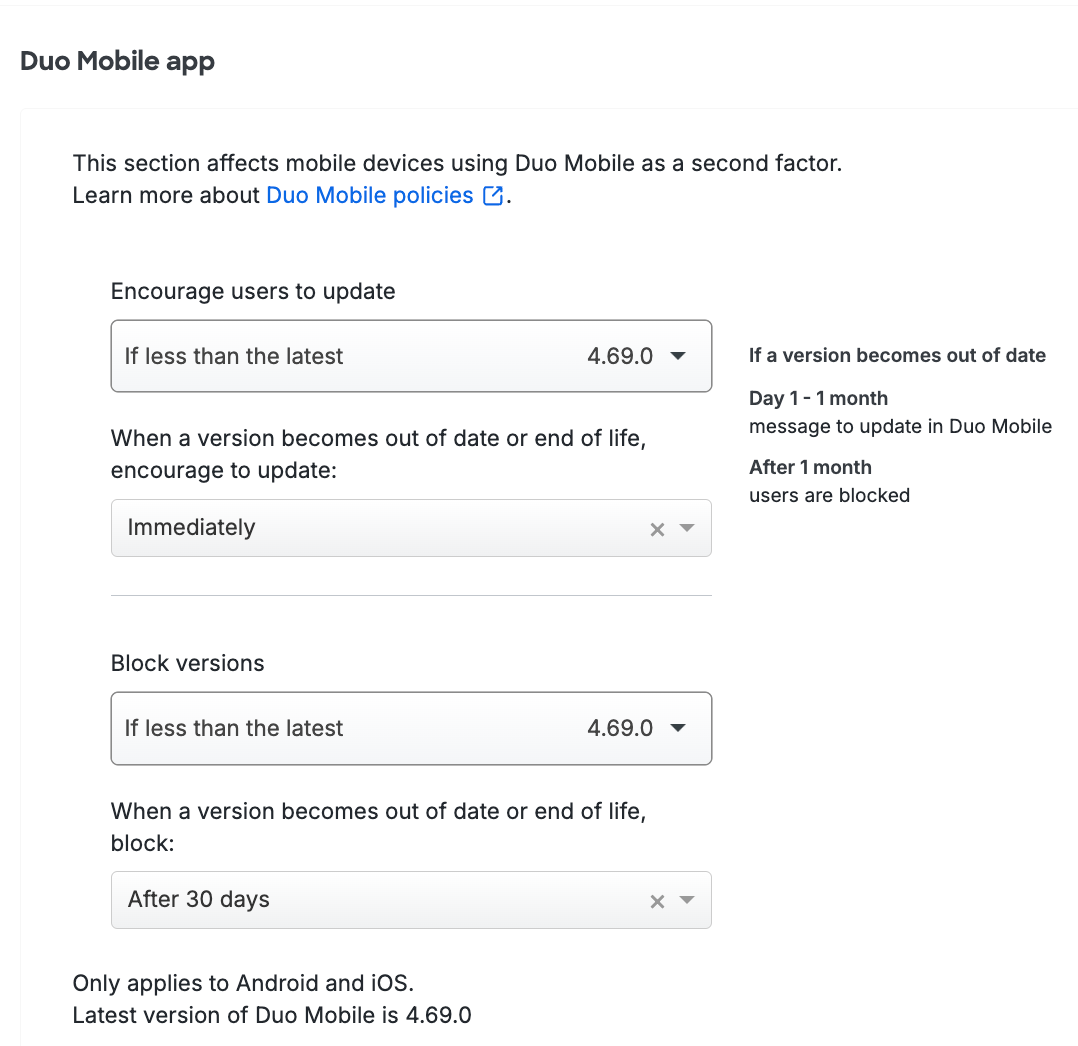
Restrict application access to only the versions you've allowed by making a selection in the Block version option, along with a corresponding scheduled grace period for blocking. Blocking any version prevents users from approving Duo Push requests or generating passcodes for authentication with any older versions of Duo Mobile.
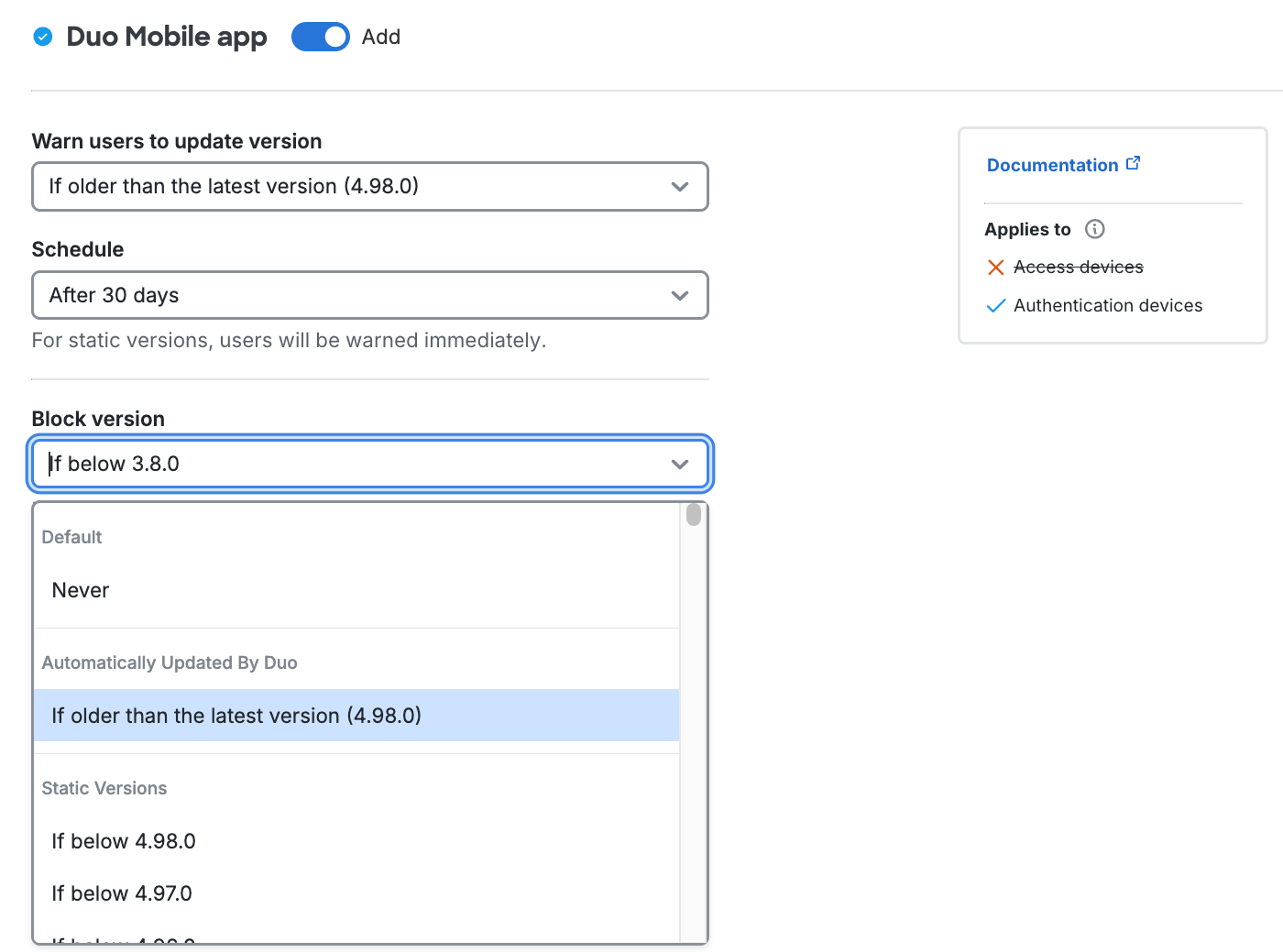
Example Scenario
You may choose to block Duo Mobile versions older than the latest release. This prevents authentication for any user trying to access your application with Duo Push or Duo Mobile passcodes not running the latest version of Duo Mobile.
If the user doesn't update Duo Mobile by the end of the scheduled warning period, or if you chose to immediately block access, the Universal Prompt denies application access.
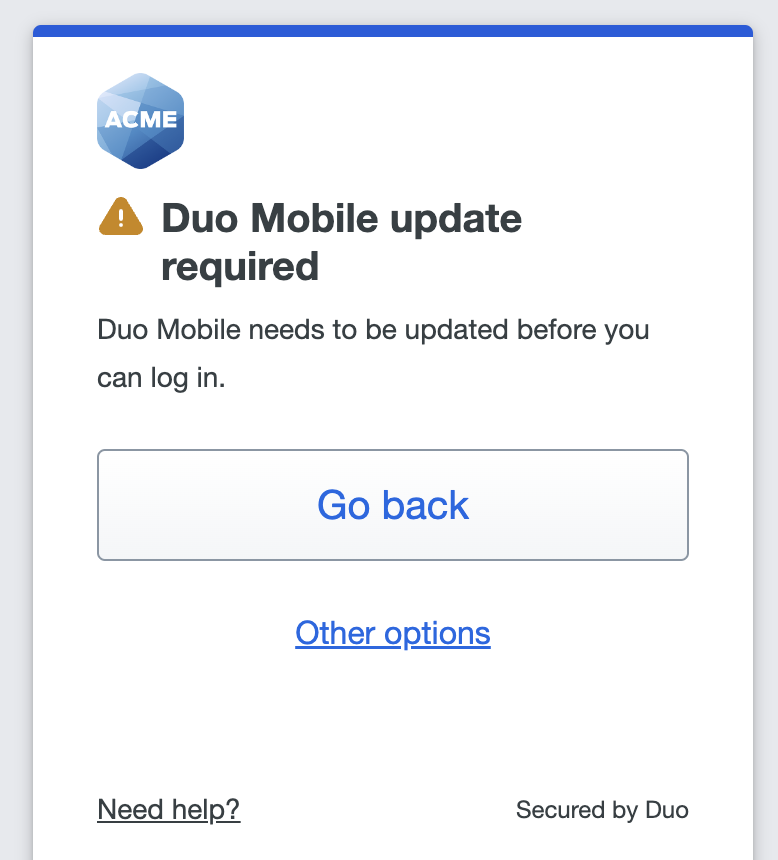
Duo Mobile will also show a notification that the app is out of date and that authentication is restricted.
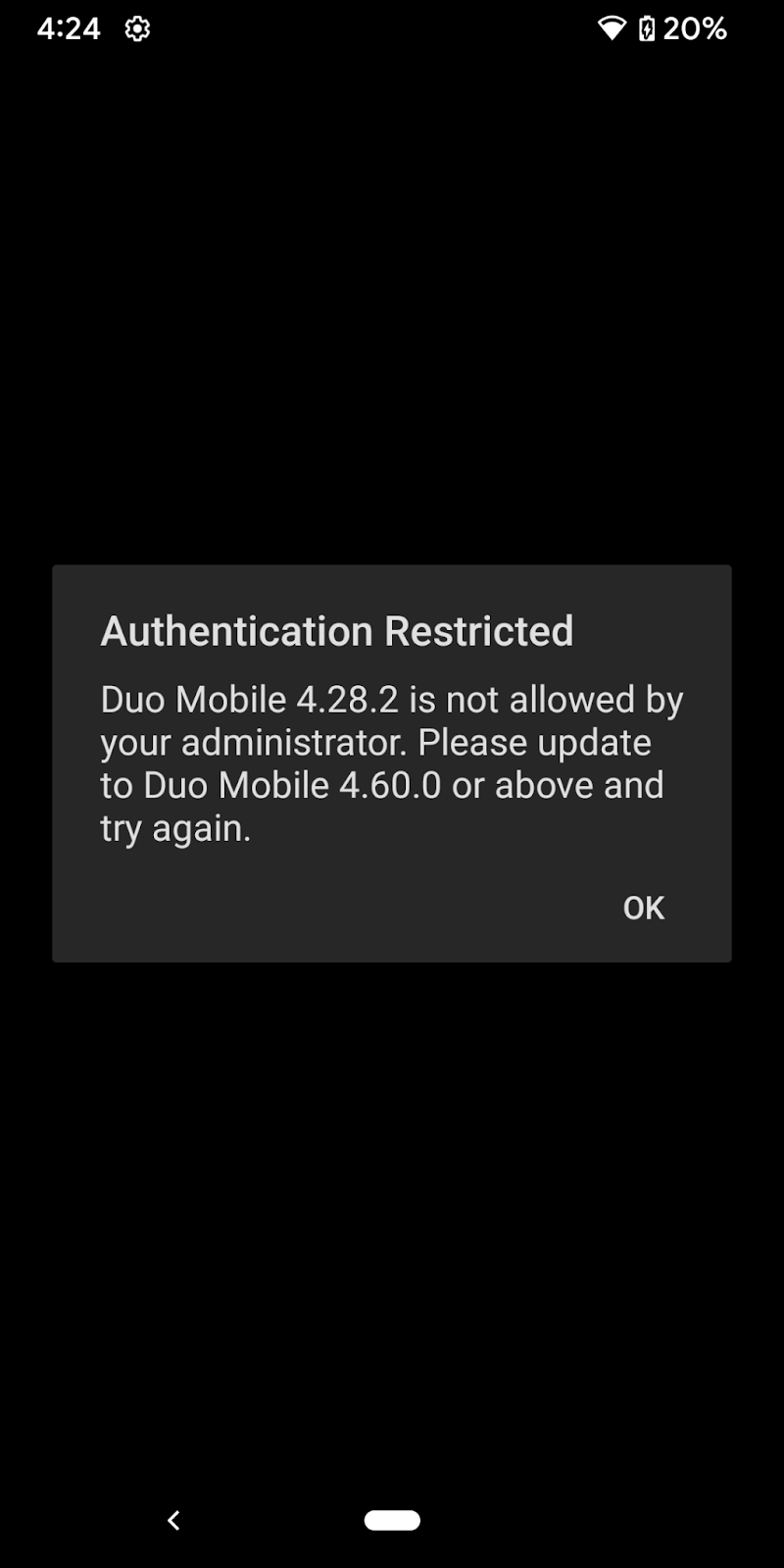
To see more ways to manage Duo Mobile, see the Duo Mobile App section on the global Settings page.
Tampered Devices
Available in: Duo Advantage and Duo Premier
It is possible to gain privileged access to the operating system of a mobile device. This is known as "rooting" on Android, and "jailbreaking" on iOS. Tampered, rooted, and jailbroken devices may be considered a security risk because they are more vulnerable to exploit by malware and malicious apps.
Duo can verify whether a device is rooted or jailbroken and prevent authentication from those devices. Duo performs jailbreak detection on iOS and, in addition to checking for rooted access on Android, also utilizes Google's Play Integrity device attestation (as of Duo Mobile version 4.40.0) to identify tampered-with Android devices. Android devices running Duo Mobile versions older than 4.40.0 stopped reporting tampered status when Google discontinued the SafetyNet service in June 2024.
You can prevent Duo authentication approvals from tampered-with or rooted Android and jailbroken iOS devices by enabling the Don't allow authentication from tampered devices policy setting. This setting has no effect on other mobile platforms.
The default setting does not allow authentications from tampered iOS and Android devices.
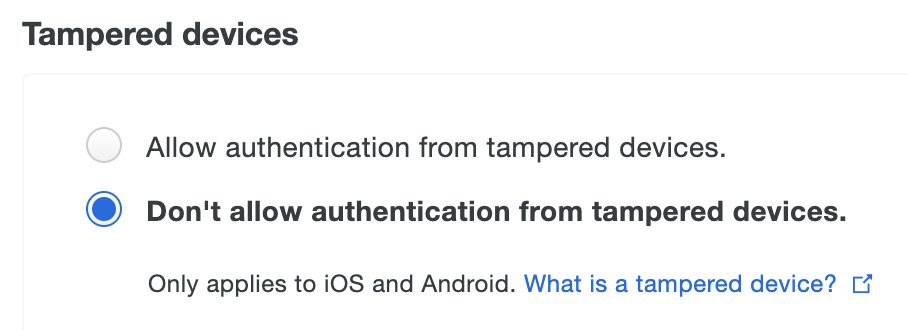
The default setting Block authentication from tampered devices does not allow authentications from tampered iOS and Android devices.
You can allow Duo authentication approvals from tampered-with or rooted Android and jailbroken iOS devices by enabling the Allow authentication from tampered devices policy setting. This setting has no effect on other mobile platforms.
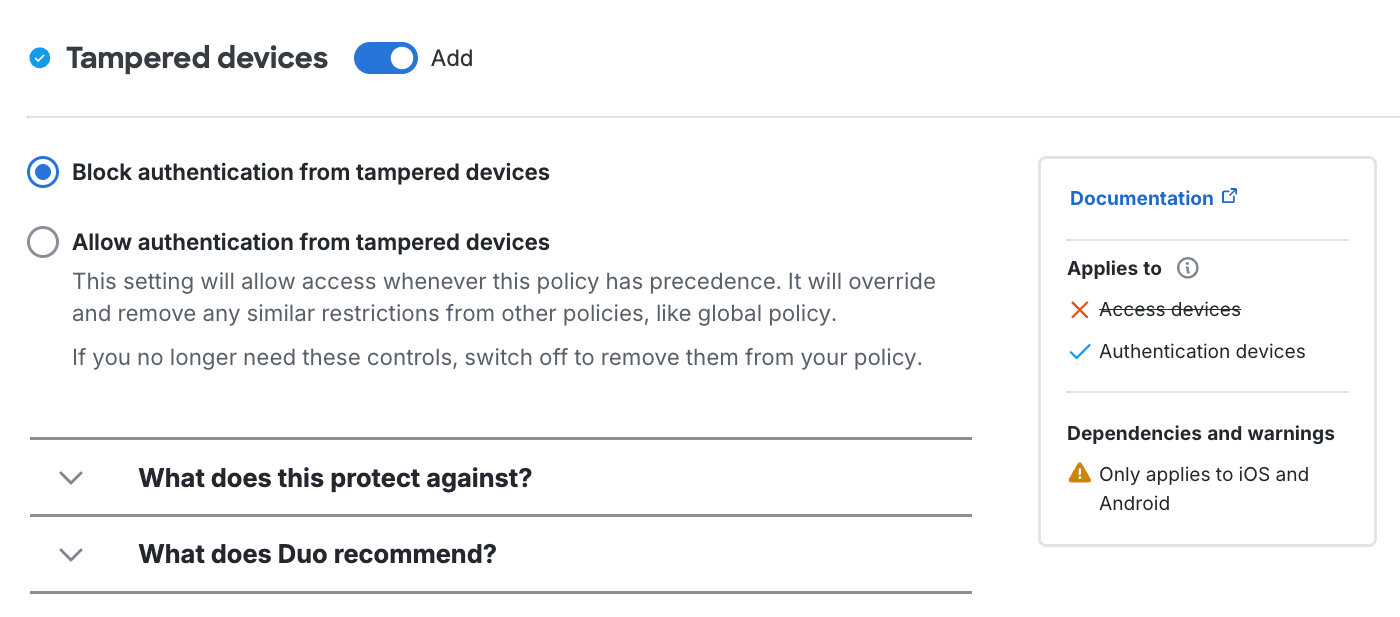
Screen Lock
Available in: Duo Advantage and Duo Premier
Enabling screen lock with passcode on iOS or with PIN on Android secures devices by requiring input of a numeric code when turning on your device or unlocking the screen. If the screen is locked when a Duo Mobile push authentication request is received, then the screen must be unlocked before approving the authentication request.
Require your users to set a PIN or passcode on their devices by enabling the Don't allow authentication from devices without a screen lock option in the "Screen Lock" policy. With this option enabled, users must have screen lock enabled on their devices to approve Duo Push authentication requests or log in with a passcode generated by the Duo Mobile app. Users may still approve phone call login requests and use SMS passcodes texted to a device without screen lock. If you wanted to completely prevent authentications from phones without screen lock configured, you'd also need to disable the "Phone callback" and "SMS passcodes" options in the Authentication Methods policy setting.
This setting applies to all supported Android versions (2.2 and up). For iOS devices, this setting is only enforced on version 8 and higher. Devices running iOS 7 and lower can still authenticate without enabling screen lock. To ensure that Apple devices used to authenticate comply with the screen lock requirement, you may change the Operating Systems policy for iOS to "Block users if their version is below 8.0".
The default setting requires that screen lock be enabled to approve a Duo authentication request received via push or use a Duo Mobile generated passcode.
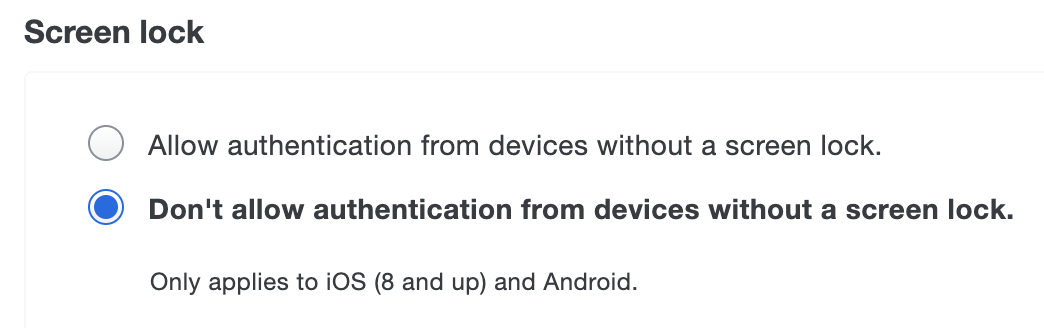
The default Block authentication from devices without a screen lock setting requires that your users to set a PIN or passcode on their devices. With this option enabled, without screen lock enabled on their devices cannot approve Duo Push authentication requests or log in with a passcode generated by the Duo Mobile app.
This setting applies to all supported Android versions (2.2 and up). For iOS devices, this setting is only enforced on version 8 and higher. Devices running iOS 7 and lower can still authenticate without enabling screen lock. To ensure that Apple devices used to authenticate comply with the screen lock requirement, you may change the Operating Systems policy for iOS to "Block users if their version is below 8.0".
Select Allow authentication from devices without a screen lock if you don't want to require that devices used to approve a Duo authentication request received via push or generate Duo Mobile generated passcode have screen lock enabled.
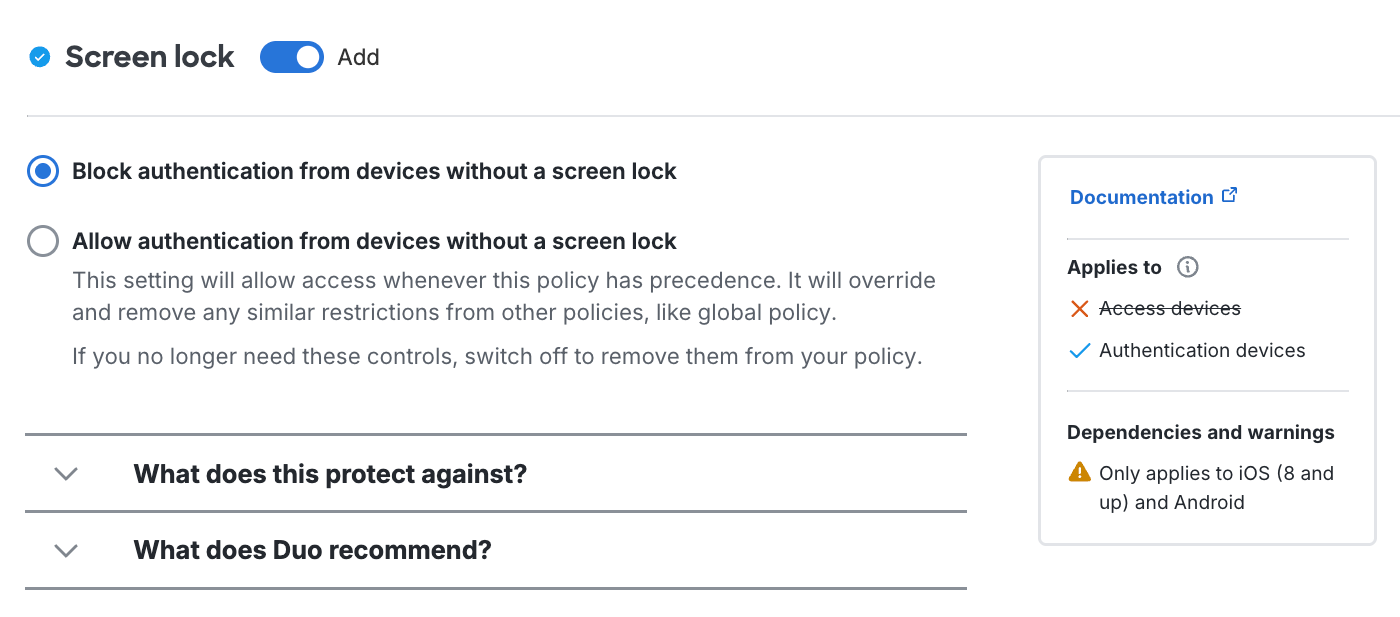
Users may still approve phone call login requests and use SMS passcodes texted to a device without screen lock. If you wanted to completely prevent authentications from phones without screen lock configured, you'd also need to disable the Phone callback and SMS passcode options in the Authentication methods policy settings.
Full-Disk Encryption
Available in: Duo Advantage and Duo Premier
Disk encryption protects device data from unauthorized access. Booting an encrypted device requires entering a passcode or PIN at device boot. Apple devices automatically encrypt the filesystem, but on Android devices encryption is enabled by the end user separately after enabling screen lock.
Prevent Duo authentication from Android devices without disk encryption by enabling the Don't allow authentication from devices without full-disk encryption option in the "Full-Disk Encryption" settings. Note that a PIN is required at startup in order for a device's status to show as encrypted.
The default setting does not require full-disk encryption to approve a Duo authentication request from an Android device. This setting has no effect on iOS.
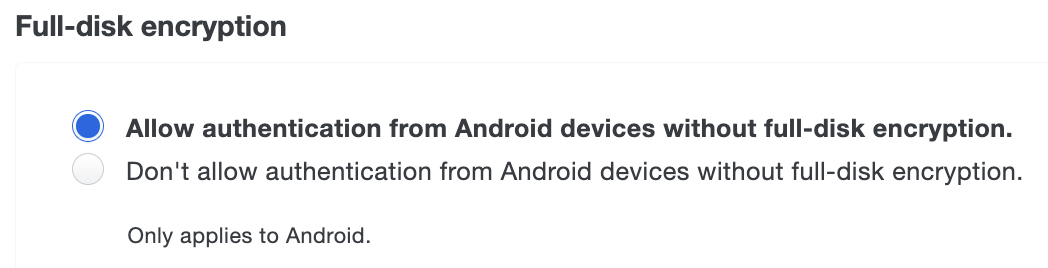
Prevent Duo authentication from Android devices without disk encryption by enabling the Block authentication from Android devices without full-disk encryption option in the "Full-Disk Encryption" settings. Note that a PIN is required at startup in order for a device's status to show as encrypted.
The default setting Allow authentication from Android devices without full-disk encryption does not require full-disk encryption to approve a Duo authentication request from an Android device. This setting has no effect on iOS.
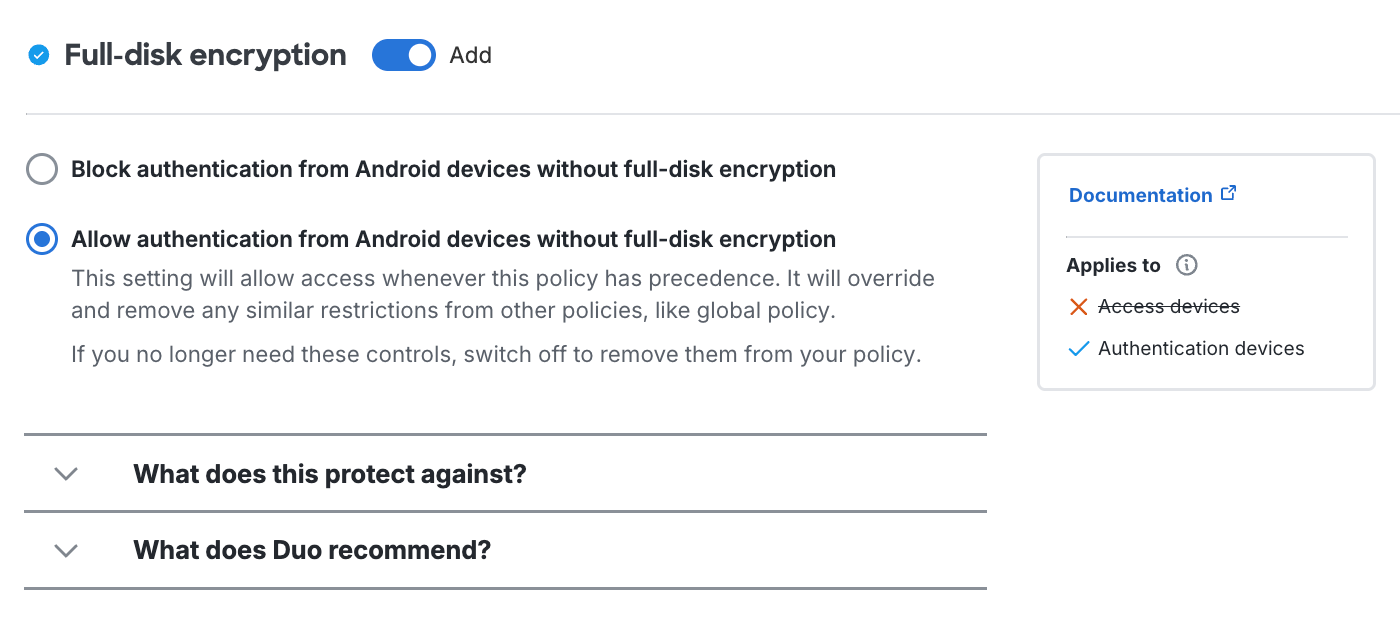
Mobile Device Biometrics
Available in: Duo Advantage and Duo Premier
Biometric identity verification, like Apple's Touch ID and Face ID or Android Fingerprint, makes two-factor authentication even more secure.
In the policy editor, select the Require additional biometric verification option to require biometric approval for Duo Push from supported devices. Use of Duo Mobile generated or SMS passcodes remains unaffected, as well as authentication via phone call.
Fingerprint and Touch ID authentication requires Duo Mobile app versions 3.7 or above for iOS and version 3.10 or above for Android and minimum OS versions iOS 8 or Android 5.0 Lollipop. Face ID requires iOS 11 and Duo Mobile 3.19. Devices running earlier versions of Duo Mobile, iOS, and Android can not authenticate without biometric verification when you enable this policy setting.
Requiring biometric verification changes the Duo Push workflow. Users may no longer approve an authentication request from the app notification. Tapping the Duo notification opens the Duo Mobile app. After you tap "Approve" on the authentication request, scan your enrolled finger at the Touch ID or Android PIN prompt or perform Face ID verification to confirm the authentication approval. If you are unable to authenticate with a biometric factor you can fall back to your device's passcode.
You can disable fall back to passcodes by selecting Don't allow device passcode as a fallback when biometric verification fails. For this setting, fingerprint and Touch ID authentication requires Duo Mobile version 4.51.0 or above and minimum OS versions iOS 8 or Android 10.0. Face ID requires iOS 11 and Duo Mobile version 4.51.0 or above. Devices running older versions of Duo Mobile, iOS, or Android cannot authenticate without biometric verification when this policy setting is enabled.
The default setting does not require any biometric verification to approve a Duo Push authentication request from any device. All Duo Mobile, Android, and iOS versions may authenticate (subject to any other version restriction policy settings you may configure).
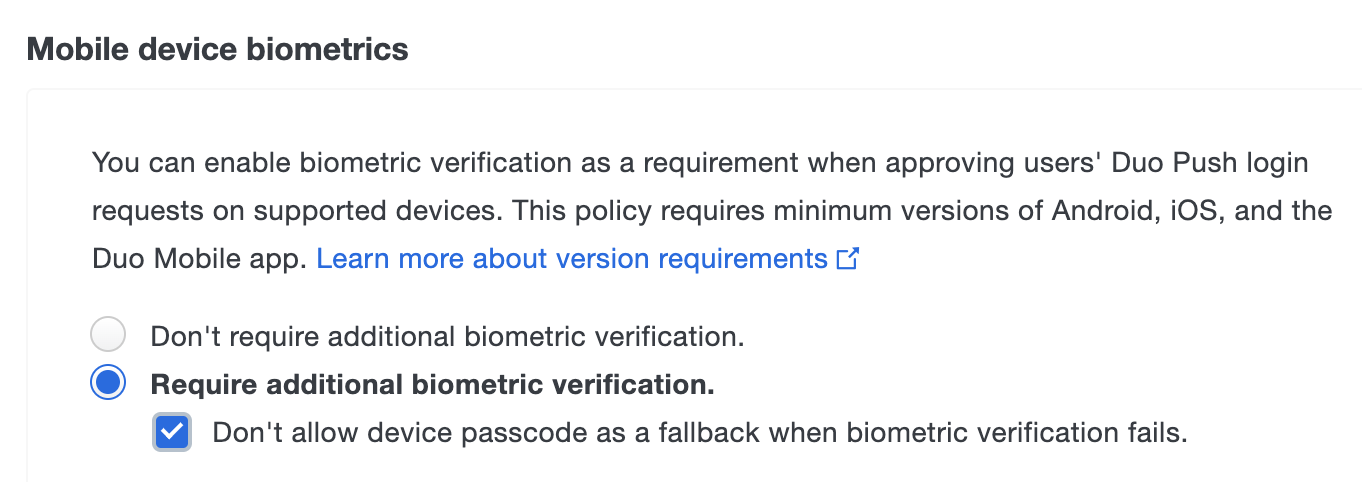
In the policy editor, select the Require additional biometric verification option to require biometric approval for Duo Push from supported devices. Use of Duo Mobile generated or SMS passcodes remains unaffected, as well as authentication via phone call.
Fingerprint and Touch ID authentication requires Duo Mobile app versions 3.7 or above for iOS and version 3.10 or above for Android and minimum OS versions iOS 8 or Android 5.0 Lollipop. Face ID requires iOS 11 and Duo Mobile 3.19. Devices running earlier versions of Duo Mobile, iOS, and Android can not authenticate without biometric verification when you enable this policy setting.
Requiring biometric verification changes the Duo Push workflow. Users may no longer approve an authentication request from the app notification. Tapping the Duo notification opens the Duo Mobile app. After you tap "Approve" on the authentication request, scan your enrolled finger at the Touch ID or Android PIN prompt or perform Face ID verification to confirm the authentication approval. If you are unable to authenticate with a biometric factor you can fall back to your device's passcode.
You can disable fall back to passcodes by selecting Block device passcode as a fallback when biometric verification fails. For this setting, fingerprint and Touch ID authentication requires Duo Mobile version 4.51.0 or above and minimum OS versions iOS 8 or Android 10.0. Face ID requires iOS 11 and Duo Mobile version 4.51.0 or above. Devices running older versions of Duo Mobile, iOS, or Android cannot authenticate without biometric verification when this policy setting is enabled.
The default setting Don't require additional biometric verification does not require any biometric verification to approve a Duo Push authentication request from any device. All Duo Mobile, Android, and iOS versions may authenticate (subject to any other version restriction policy settings you may configure).
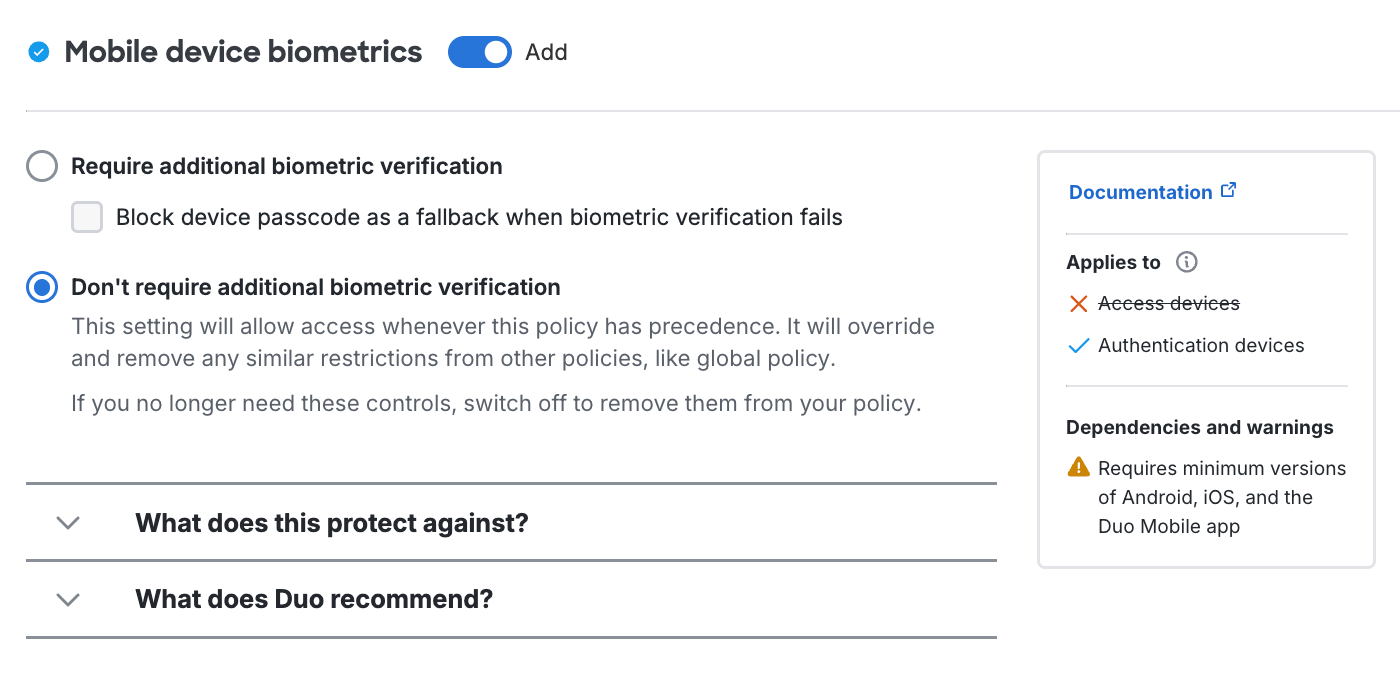
More Information
Please refer to the Duo Policy Guide for supplemental information about constructing effective custom policies and assigning them to your Duo applications and users.
Please also refer to the Duo Admin API for information about using the Policies Admin API endpoint to programmatically create policies, modify policy settings, and attach policies to applications and groups.
Troubleshooting
Need some help? Try searching our Knowledge Base articles or Community discussions. For further assistance, contact Support.